Anomali Limo – Free Intelligence Feeds
Use Anomali Limo to get the latest Anomali updates and cybersecurity news straight to your inbox from a variety of sources such as Anomali Labs research and more.
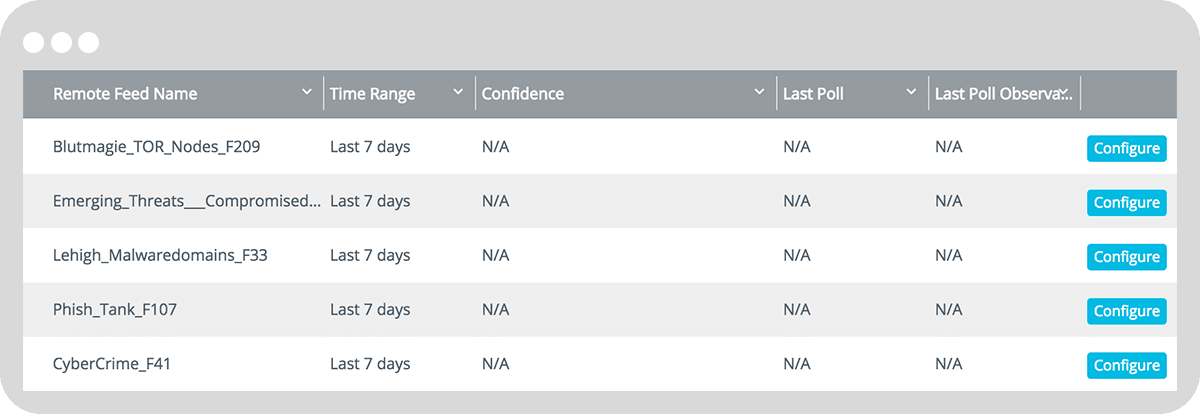

<p>If today’s threat landscape were a road, it would be marred with all kinds of obstacles- potholes of malware, a flat tire of phishing emails, and maybe even a stolen car/computer through a botnet. It’s treacherous to navigate- particularly if you don’t have a mature security program. Even the smallest of organization stands to benefit from threat intelligence though, and a lack of expertise, time, or budget shouldn’t exclude them from improved security.</p><p>That’s why we’ve created <a href="https://www.anomali.com/community/limo">Limo</a>, a free TAXII service made up of a variety of threat intelligence feeds. Anomali’s Limo service provides a luxurious and smooth ride through this threat landscape- luxurious in the quality of information, and smooth in how simple it is to set up.</p><p>The information for these feeds is harvested from a variety of sources such as Anomali Labs research, our Modern Honey Net, open source feeds, and more. These feeds are fully STIX/TAXII compliant, making it easy to collect and share. These feeds are also updated regularly to provide users with the most relevant threat information.</p><p>Here’s where the comparison to a limousine service ends though. Accessing Limo is far easier a process than its real-life counterpart, and completely free. For Anomali STAXX users, Limo is preconfigured so that all data and preferences remain the same and intelligence from Limo’s feeds is available to be used immediately.</p><p>Anomali Limo isn’t as exclusive as a real-life limo either. If you’d like to use another TAXII client, you can configure it to point towards <a href="https://limo.anomali.com/api/v1/taxii/taxii-discovery-service/" target="_blank">https://limo.anomali.com/api/v1/taxii/taxii-discovery-service/</a> and use guest/guest as the username and password.</p><div style="padding:20px 20px 30px 20px;margin-bottom:30px;background:#cfe6f5;-webkit-border-radius:8px;-moz-border-radius:8px;border-radius:8px;"><div class="row"><div class="col-xs-12 col-sm-4 center"><a href="https://www.anomali.com/community/staxx"><img alt="Cybersecurity Talent Shortage Infographic" src="https://cdn.filestackcontent.com/DhTGansTsaYTh8LofrSY" style="margin-bottom: 10px; width: 300px;"/></a></div><div class="col-xs-12 col-sm-8"><h4 class="nobottommargin"><a href="https://www.anomali.com/community/staxx">Get STAXX Free</a></h4><p style="margin-bottom:20px;">The simplest way to buckle in for a deluxe threat intelligence experience.</p><p class="nobottommargin"><a href="https://www.anomali.com/community/staxx">DOWNLOAD NOW</a></p></div></div></div><p>If you have any other questions about Limo, STAXX, or other Anomali products, join the conversation on the <a href="https://forum.anomali.com" target="_blank">Anomali Forum</a>.</p>
FEATURED RESOURCES

Anomali Cyber Watch
When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest

Anomali Cyber Watch


