Skip to main content
- PRODUCTSAgentic SOC Platform OverviewUnifies threat intelligence, security data, and agentic AI into a single platform, enabling SOC and CTI teams to collaborate seamlessly. Teams gain context and AI-guided workflows to detect hidden threats, prioritize high-risk incidents, and respond faster.Agentic SOC Platform OverviewAgentic SOC Platform OverviewProducts
- Unified Security Data LakeComplete visibility, AI-guided insights, and unified workflows to detect, investigate, and respond at machine speed.Unified Security Data LakeUnified Security Data Lake
- ThreatStream Next-GenThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.ThreatStream Next-GenThreatStream Next-Gen
- Agentic AIAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Agentic AIAgentic AI
Use Cases- ComplianceAll-in-one ETL, SIEM, XDR, UEBA, and SOAR for blazing fast threat detection, investigation, and response.ComplianceCompliance
- Threat DetectionThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.Threat DetectionThreat Detection
- Investigation and ResponseAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Investigation and ResponseInvestigation and Response
- Threat HuntingAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Threat HuntingThreat Hunting
- Threat AnalysisAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Threat AnalysisThreat Analysis
- Intelligence DistributionAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Intelligence DistributionIntelligence Distribution
Capabilities- Threat Intelligence (TIP)All-in-one ETL, SIEM, XDR, UEBA, and SOAR for blazing fast threat detection, investigation, and response.Threat Intelligence (TIP)Threat Intelligence (TIP)
- SIEMThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.SIEMSIEM
- Agentic AIAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Agentic AIAgentic AI
- SOARAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.SOARSOAR
- XDRAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.XDRXDR
- USE CASESUnified Security Data lake
- ComplianceAll-in-one ETL, SIEM, XDR, UEBA, and SOAR for blazing fast threat detection, investigation, and response.ComplianceCompliance
- Threat DetectionThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.Threat DetectionThreat Detection
- Investigation and ResponseAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Investigation and ResponseInvestigation and Response
- Threat HuntingAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Threat HuntingThreat Hunting
ThreatStream Next-Gen- Threat DetectionThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.Threat DetectionThreat Detection
- Investigation and ResponseAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Investigation and ResponseInvestigation and Response
- Threat HuntingAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Threat HuntingThreat Hunting
- Threat AnalysisAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Threat AnalysisThreat Analysis
- Intelligence DistributionAdvanced AI and natural language processing to simplify and speed up analysis so you can stop threats in their tracks.Intelligence DistributionIntelligence Distribution
Agentic AI- Reason and ActAll-in-one ETL, SIEM, XDR, UEBA, and SOAR for blazing fast threat detection, investigation, and response.Reason and ActReason and Act
- Model Context ProtocolThe industry’s leading threat intelligence platform (TIP) that provides curated access to the world’s largest repository of curated threat intelligence.Model Context ProtocolModel Context Protocol
- MarketplaceThe Anomali MarketplaceA unique cybersecurity marketplace providing instant access to a growing catalog of threat intelligence providers, integration partners, and threat analysis tools.The Anomali MarketplaceThe Anomali Marketplace
- Threat Intelligence FeedsTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Threat Intelligence FeedsThreat Intelligence Feeds
- Threat Analysis Tools and EnrichmentsGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.Threat Analysis Tools and EnrichmentsThreat Analysis Tools and Enrichments
- Security System PartnersTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Security System PartnersSecurity System Partners
- SDKsGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.SDKsSDKs
- RESOURCESExplore ResourcesDive into the latest cybersecurity and threat intelligence news, tips, and insights through our library of articles, webinars, datasheets, industry reports, case studies, and more.Explore ResourcesExplore ResourcesSIEM OptimizationOptimize SIEM with an intelligence-native approach built for speed, scale, and action.Explore
- BlogTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.BlogBlog
- Case StudiesTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Case StudiesCase Studies
- GlossaryTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.GlossaryGlossary
Engage- WebinarsTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.WebinarsWebinars
- EventsTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.EventsEvents
- Demos and VideosTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Demos and VideosDemos and Videos
Learn- What is a Threat Intelligence Platform (TIP)?Trial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.What is a Threat Intelligence Platform (TIP)?What is a Threat Intelligence Platform (TIP)?
- What is MITRE ATT&CK?Gain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.What is MITRE ATT&CK?What is MITRE ATT&CK?
- What is Threat Intelligence?Gain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.What is Threat Intelligence?What is Threat Intelligence?
- What are STIX/TAXII?Gain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.What are STIX/TAXII?What are STIX/TAXII?
- What is Security Analytics?Gain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.What is Security Analytics?What is Security Analytics?
- CompanyAbout AnomaliAnomali delivers the first Intelligence-Native Agentic SOC Platform, unifying a fully-featured-security data lake, threat intelligence, and agentic AI into a single modern experience. The platform accelerates detection, investigation, and response, delivering earlier insights, faster action, and scalable modernization across any environment.About AnomaliAbout Anomali
- Press RoomTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Press RoomPress Room
- Gartner ReviewsGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.Gartner ReviewsGartner Reviews
- AwardsGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.AwardsAwards
- LeadershipTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.LeadershipLeadership
- CareersGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.CareersCareers
- Contact UsGain the tools to pivot quickly from one piece of information to look up other sources of data to get a complete picture of a threat – all one click away.Contact UsContact Us
- PartnersPartners OverviewAnomali is dedicated to fostering strong partnerships, ensuring shared success and growth through collaborative innovation and mutual support.Partners OverviewPartners Overview
- Partner DirectoryTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Partner DirectoryPartner Directory
- Channel PartnersTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Channel PartnersChannel Partners
- MSSPTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.MSSPMSSP
- Technology Alliance PartnersTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Technology Alliance PartnersTechnology Alliance Partners
- Threat Intel SharingTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Threat Intel SharingThreat Intel Sharing
- Partner PortalTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Partner PortalPartner Portal
- Deal RegistrationTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Deal RegistrationDeal Registration
- Become a Channel PartnerTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Become a Channel PartnerBecome a Channel Partner
- Become a MSSPTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Become a MSSPBecome a MSSP
- Become a Technology Alliance PartnerTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Become a Technology Alliance PartnerBecome a Technology Alliance Partner
- Become a Threat Intel Sharing PartnerTrial and purchase threat intelligence feeds from Anomali partners – find the right intelligence for your organization, industry, geography, and more.Become a Threat Intel Sharing PartnerBecome a Threat Intel Sharing Partner
KEY CAPABILITIES
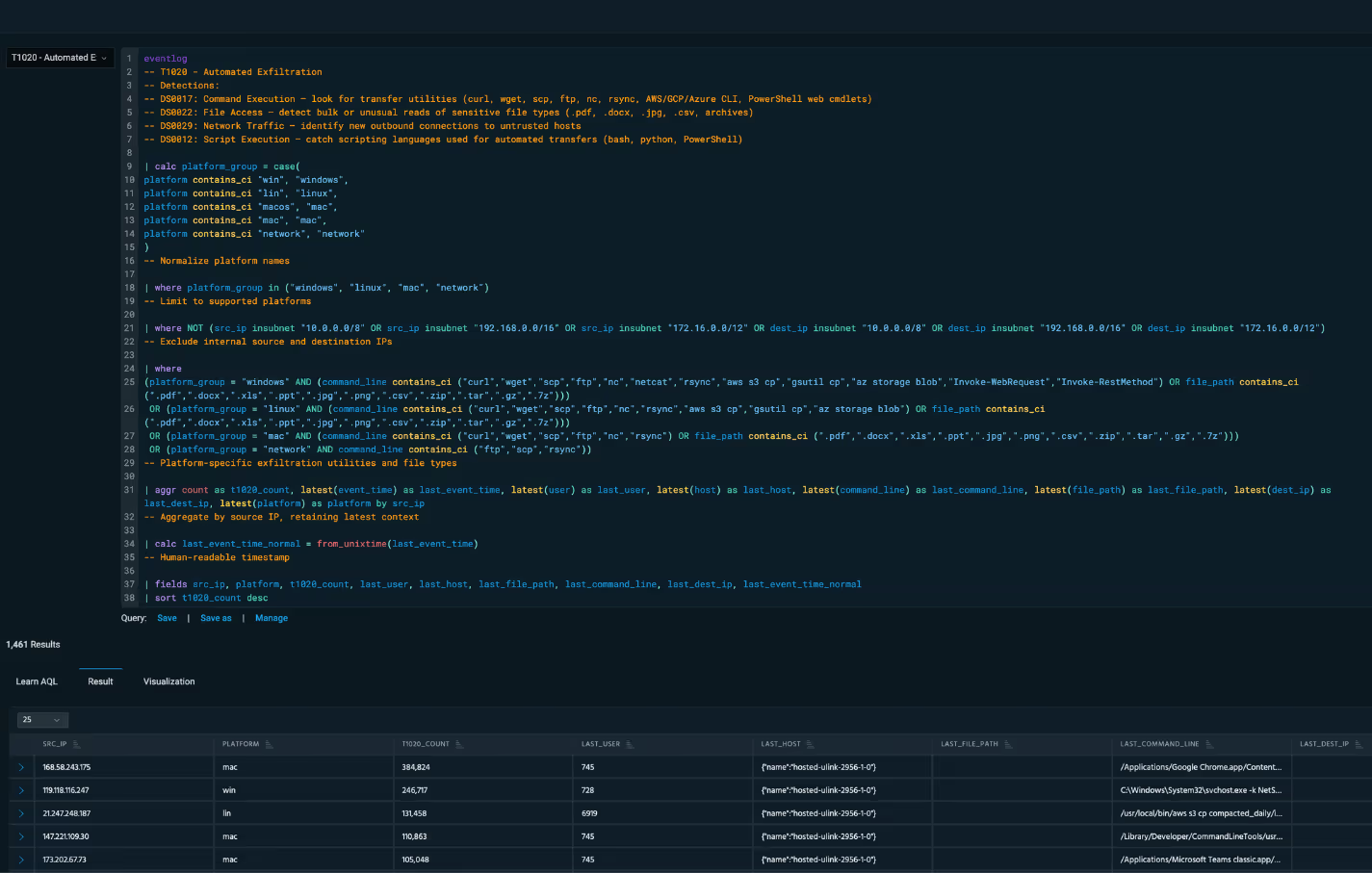
AI-Powered Detection
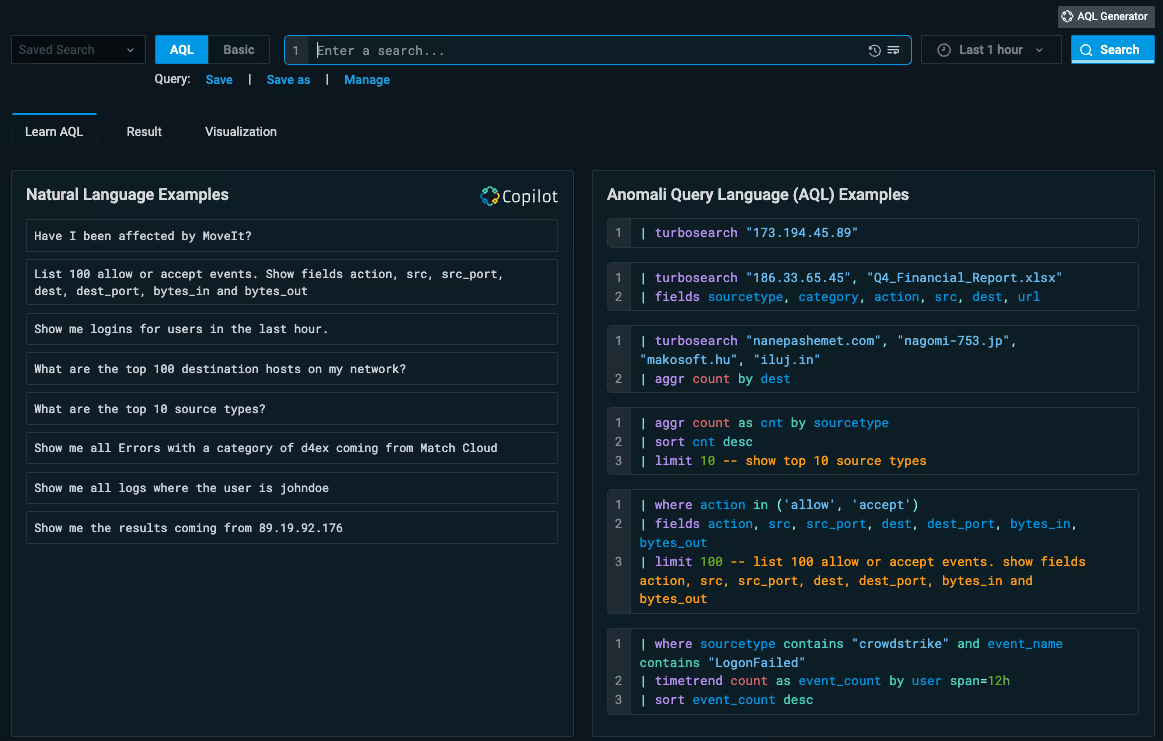
NLP Querying
Automated Investigation
Total Visibility
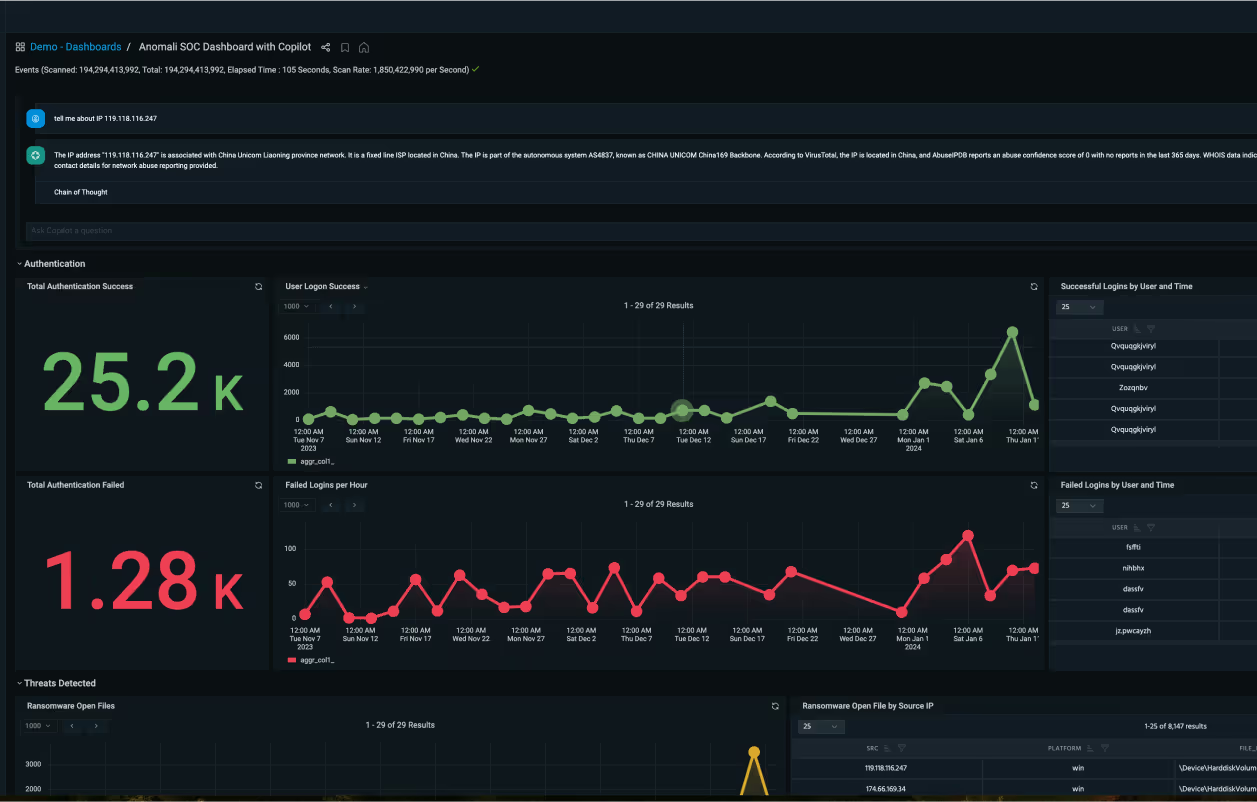
Copilot
Empower your analysts with the speed and simplicity of AI. Anomali Copilot AI uses natural language and advanced threat intelligence to supercharge detection, investigation, and response.
ASK ANOMALI COPILOT
Type in your query below...
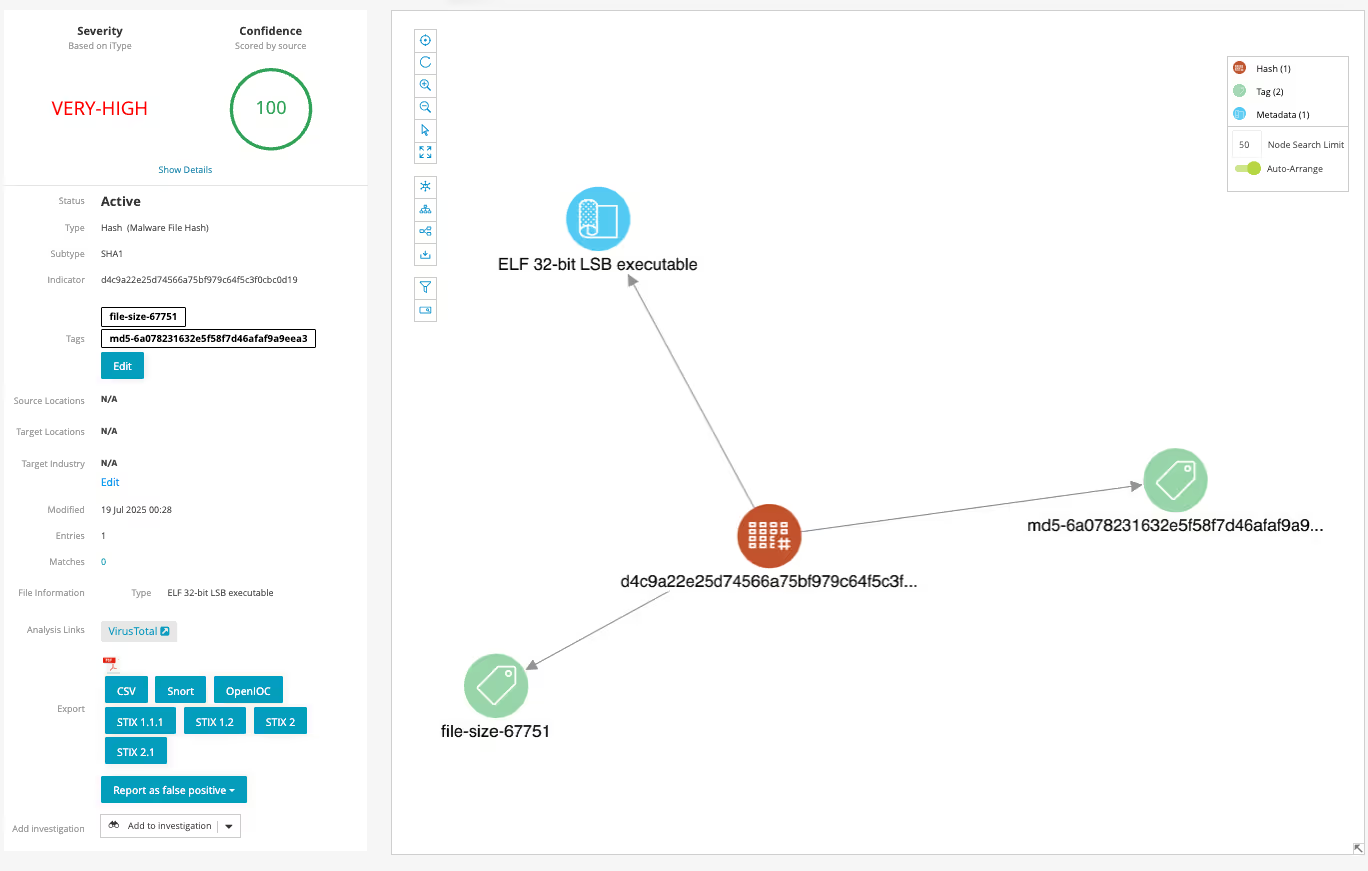
The ToolShell SharePoint exploit primarily targets the CVE-2025-53770 vulnerability in on-premises Microsoft SharePoint Server, allowing for remote code execution. The key attack vectors include:1. Exploiting the CVE-2025-53770 vulnerability, which is a critical remote code execution (RCE) vulnerability caused by the deserialization of untrusted data in SharePoint Server.2. Targeting the "/layouts/15/ToolPane.aspx" endpoint on the SharePoint server and using a specially crafted HTTP request with a unique "Referer" header to bypass authentication.3. Uploading a malicious .aspx file named "spinstall0.aspx" as a web shell to execute .NET commands and extract the SharePoint instance's machineKey configuration.4. Using the extracted machineKey and validationKey to forge valid and signed __VIEWSTATE payloads for unauthenticated remote code execution.Additionally, SharePoint could potentially be abused for ingress tool transfer and user enumeration, but specific details on these vectors are not provided in the threat model documents.
Strengthen Threat Detection, Investigation, and Response with AI
As cyber threats grow in complexity, traditional security methods struggle to keep up. Our guide, AI-Powered Threat Detection, Investigation, and Response (TDIR), explores how security teams can detect threats faster, streamline investigations, and automate response actions with the help of AI.


“The time it takes to analyze a threat has gone down from 30 minutes to just a few minutes, time that adds up over the course of investigating many malicious IPs every week. There has been a substantial decrease in terms of meantime-to-know.”
Arindam Bose
Senior Vice President & Security Officer, Bank of Hope

“Before Anomali, we had tons of information without context. We had to look through thousands of alerts quickly just to see what stood out and then react to those. Anomali enabled us to spend less time dealing with noise, and more time focusing on critical issues.”
Devin Ertel
CISO, Blackhawk Network Holdings

“We leverage market-leading tools to give our company a competitive advantage and our 24/7 SOC a leg up on bad actors. With Anomali, we improve on both of these goals. By adding intelligence, we achieve a high level of certainty that enhances prioritization of the most serious threats our customers face, while improving our mitigation decisions.”
Grant Leonard
Co-Founder, Castra

“As one of the prominent banks in the United Arab Emirates, we manage assets and transactions for thousands of customers. One of our main commitments to our customers is security and we achieve this through solid partnerships with industry experts such as Anomali. By bringing in industry experts, we expect to gain advanced levels of security that will help us to further heighten our defenses and intercept any possible exploitation by cybercriminals.”
K.S. Ramakrishnan
Chief Risk Officer, RAKBANK

“To counter today’s adversaries, organizations must optimize their security operations. Anomali has both a strong leadership team and proven technology and expertise to transform how organizations protect their assets against today’s most challenging cyber threats.”
Nidal Othman
MEA CEO & Head of Vendor Management, Infinigate Group

“Anomali elevates security efficacy, reducing costs significantly with automated processes at the heart of everything. The Anomali platform powered by the largest global repository of threat intelligence is a game-changer in the industry.”
Wendy O'Keeffe
EVP & Managing Director, Nextgen Asia
Latest from Anomali
Anomali Cyber Watch: React and Next.js RCE Vulnerabilities, "Evil Twin" Wifi Networks, Record 29.7 Tbps DDoS Attack, and More
Anomali Cyber Watch: React and Next.js RCE Vulnerabilities, "Evil Twin" Wifi Networks, Record 29.7 Tbps DDoS Attack, and More