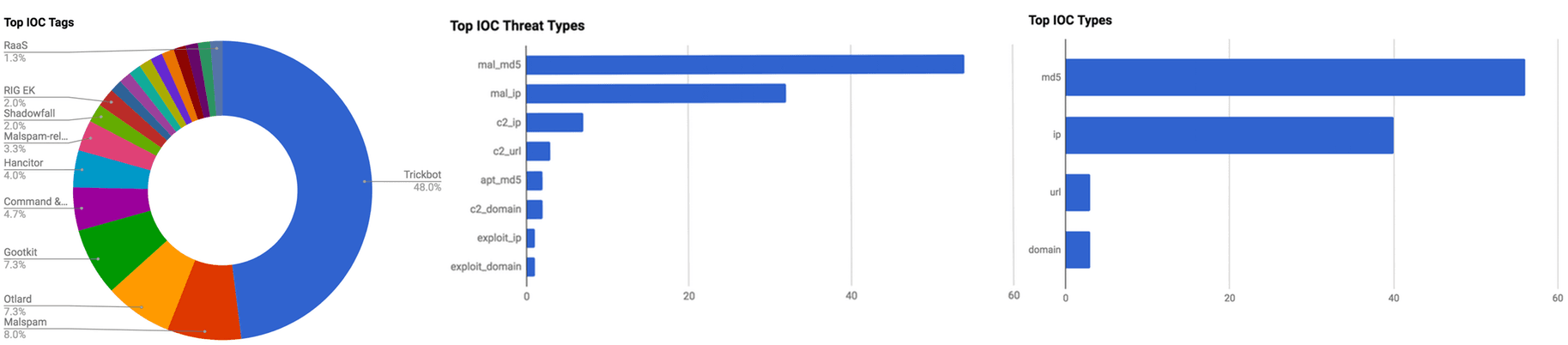

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
Ex-Admin Deletes All Customer Data and Wipes Servers of Dutch Hosting Provider (June 9, 2017)
The Dutch hosting provider, Verelox experienced a significant breach after a former IT administrator deleted all of their customer data. The former employee also wiped most of the company’s servers. The company is asking all of their customers to reset their passwords. At the time of this writing, it is unknown if Verelox will be able to retrieve the deleted customer data.
Recommendation: Ensure that your server is always running the most current software version. Additionally, maintaining secure passwords for RDP and other remote access systems is paramount, and passwords should be changed on a frequent basis. Intrusion detection systems and intrusion prevention systems can also assist in identifying and preventing attacks against your company's network. Furthermore, always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). Furthermore, maintaining comprehensive backups files is important to help ensure the security of important customer data.
Tags: Breach
MacRansom: Offered as Ransomware-as-a-Service (June 9, 2017)
A Ransomware-as-a-Service (RaaS) has been discovered to be targeting macOS users, according to Fortinet researchers. The malware, called "MacRansom," is being offered by actors who claim to be engineers at Yahoo and Facebook in what appears to be attempts to add trust for potential buyers. MacRansom is advertised to be capable of infecting users by moving the malware to a USB drive and then running the program.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: RaaS, MacRansom
Mouse Over, Macro: Spam Run in Europe Uses Hover Action to Deliver Banking Trojan (June 9, 2017)
A new malspam campaign has been identified to be distributing the banking trojan called Gootkit (Otlard), according to Trend Micro researchers. Gootkit was first discovered in 2012 and is capable of multiple forms of malicious activity such as browser manipulation, credential theft, network traffic monitoring, and remote access capability. In this campaign, some of the spam emails are financially themed with subject lines such as "Fee," and "Purchase Orders" that request the recipient to open the attachment. If opened, a hyperlink will try to open if the user hovers over the text that requests that macros be enabled in order to properly view the document.
Recommendation: Malspam is a constant threat used by malicious actors who are consistently changing the themes of the messages to trick unsuspecting recipients. Anti-spam and antivirus application provided from trusted vendors should be employed in addition to educating your employees to identify such attempts. Additionally, Microsoft Office will not ask a user to leave a protected view mode to view the content of the document.
Tags: Malspam, Banking trojan
Hancitor Malspam (Dropbox-Themed) (June 8, 2017)
A malspam campaign has been identified to be impersonating the file sharing software, Dropbox. The content of the email purports that a payment invoice has been shared and requests the recipient to view the file to identify any potential "questions" about the document. If the attachment is opened, it requests that "Enable editing" be clicked which, if done, will begin the infection process of the Hancitor malware. The Hancitor malware is capable of downloading additional malware to steal information from the compromised machine.
Recommendation: Educate your employees on the risks of opening attachments from unknown senders. Anti-spam and antivirus applications provided from trusted vendors should also be employed. Emails that are received from unknown senders should be carefully avoided, and attachments from such senders should not be opened. Additionally, Microsoft Office will not ask a user to leave a protected view mode to view the content of the document.
Tags: Malspam, Dropbox-themed
CertLock Trojan Blocks Security Programs by Disallowing Their Certificates (June 8, 2017)
Researchers have discovered a new malware campaign that is capable of preventing antivirus programs from running on the infected machines. The malware, dubbed "CertLock," is being distributed by threat actors by concealing it in program bundles such as miners. CertLock prevents antivirus software from running by adding the vendors digital certificate to a revoked certificate list. Once the antivirus software is blocked, actors would be able to download additional malware.
Recommendation: This story depicts the dangers of downloading free program bundles. The appeal of free, potentially useful software can cause some users to become infected with malware after downloading it themselves. Software should only be downloaded from trusted and verified sources.
Tags: Malware, CertLock
Russian Hackers Target Montenegro as Country Joins NATO (June 7, 2017)
Montenegro has officially joined the North Atlantic Treaty Organization (NATO), amid pressure from Russia to do otherwise. Researchers believe that the Russian-linked threat group, APT28, is targeting Montenegro government officials with NATO-themed spearphishing emails in response. The spearphishing emails have been identified to exploit Adobe Flash vulnerabilities.
Recommendation: This story represents potential threats and attacks that can arise based on current political geopolitical developments. Therefore, awareness of tension between countries and governments can potentially grant some insight as to where attacks may originate. It is crucial that server software be kept up-to-date with the most current versions and that all external facing assets are carefully monitored and scanned for unusual activity and vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Spearphishing
TrickBot's Bag of Tricks (June 6, 2017)
Threat Intelligence Analyst, Bart Parys, has recently released new information regarding the TrickBot banking trojan. At the time of this writing, TrickBot's Multi-Purpose Internet Mail Extensions (MIME) data is similar to the Dyre banking trojan. Additionally, TrickBot also has the ability for Dynamic Link Library (DLL) injection to a web browser in order to perform web injection. TrickBot is also capable of generating a Domain Generation Algorithm (DGA) to direct users to a website that impersonates legitimate banking websites to steal financial information.
Recommendation: Malware authors are always innovating new methods of communicating back to the control servers. Always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). Multi-factor authentication should be also be used when performing financial tasks.
Tags: Malware, Trickbot
Turla's Watering Hole Campaign: An Updated Firefox Extension Abusing Instagram (June 6, 2017)
ESET researchers have discovered that the Advanced Persistent Threat (APT) group "Turla" is engaged in a new watering hole campaign. The group is known to compromise websites, typically associated with government embassies, in order to redirect visitors to Turla watering hole C2s. It was also discovered in February 2017 that Turla was distributing malicious Word document attachments via spear phishing emails that dropped a Firefox web browser extension. The group has now resumed this form of malicious activity. The extension is called "HTML5 Encoding 0.3.7" and functions as a backdoor. It will steal information and then send it back to a C2 via a URL that is generated in Instagram comments.
Recommendation: Spear phishing emails represent a significant security risk because the sending email will often appear legitimate to the target; sometimes a target company email is compromised and used for such emails. Education is the best defense, inform your employees on what to expect for information requests from their managers and colleagues. Employees should also be aware of whom to contact when they suspect they are the target of a possible spear phishing attack. Additionally, emails could be signed with cryptographic signatures in order for employees to properly identify legitimate information requests.
Tags: APT, Turla
Malicious Android Ads Leading to Drive By Downloads (June 5, 2017)
Zscaler researchers have identified a new malvertising campaign that is targeting Android users. This campaign is installing a malicious application onto the user's device that visits certain website forums called "Ks Clean." The application poses as an Android cleaner application that, upon the automatic download, presents the user with a screen that forces the user to accept an "Update" by clicking "OK." Once clicked, the application will request administrator rights, which then must be Installed and then Activated. If the rights are granted, the application is capable of a variety of different capabilities such as accessing external storage locations, downloading files, and stealing device information, among others.
Recommendation: Your company should have appropriate anti-virus, anti-spam, and policies in place that will prevent your employees from visiting potentially malicious websites. Education is also a great mitigation technique that can assist your company in awareness of the risks posed by visiting less reputable online locations. Additionally, automatic downloads should be disabled in Android web browsers.
Tags: Malvertising, Android
Shadowfall (June 5, 2017)
RSA researchers, in collaboration with other researchers and organizations, have published their findings regarding analysis of the RIG Exploit Kit. The researchers discovered that a significant portion of RIG's infrastructure from February 21 and March 20, 2017 was created via domain shadowing. Domain shadowing is a "technique in which attackers steal domain account credentials from their owners for the purpose of creating subdomains directed at malicious servers." The primary method used to direct users to RIG is being conducted by compromising legitimate websites.
Recommendation: Exploit kits have become one of the most common types of crimeware currently available to the less than sophisticated threat actor. The kits, put together by skilled actors, are then sold to criminal groups as easily deployable exploitation frameworks. The best protection from exploit kits is through employee education in combination with keeping web browsing software (including extensions such as flash and java) up to date at all times, as well as operating system software. Users should be educated on how to browse the web as safely as possible, and to report any suspicious symptoms observed on their devices to IT/secops immediately. In the case of a compromise by RIG, the infected system must be wiped and reformatted.
Tags: RIG EK
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
RIG exploit kit Tool Tip
The RIG exploit kit is a framework used to exploit client side vulnerabilities in web browsers. The RIG exploit kit takes advantage of vulnerabilities in Internet Explorer, Adobe flash, Java and Microsoft Silverlight. The RIG exploit kit was first observed in early 2014. The RIG exploit kit's objective is to upload malicious code to the target system. The RIG exploit kit is known to distribute ransomware, spambots and backdoors. Victims are redirected to the RIG exploit kit with a landing page coming from malvertising or compromised sites.
Tags: RIG, exploitkit
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



