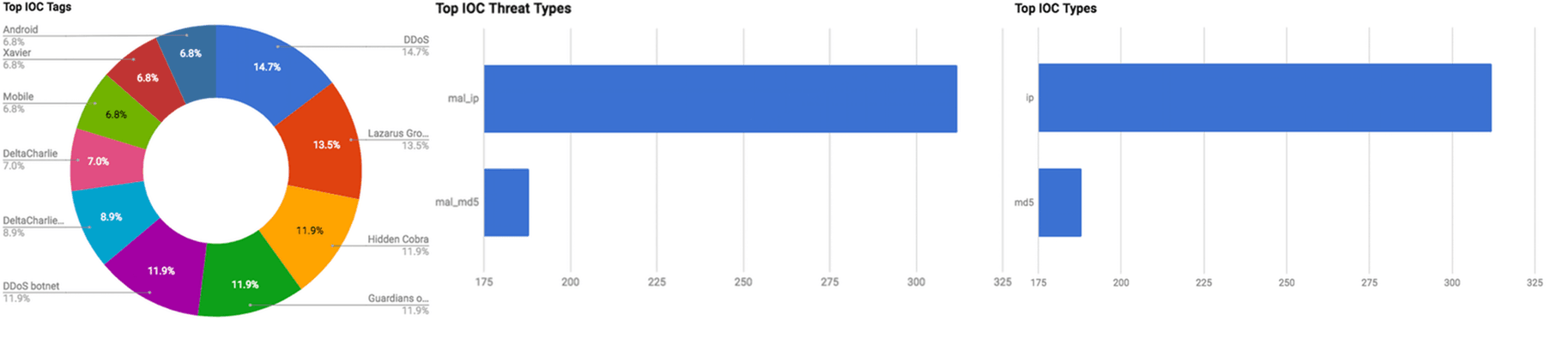

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
Erebus Resurfaces as Linux Ransomware (June 19, 2017)
The web hosting company, "Nayana," was recently infected with a ransomware family called "Erebus," according to a statement made by the company. The ransomware infected approximately 153 Linux servers and over 3,400 websites hosted by the company. The infection occurred on June 10, 2017, and the threat actors demanded a payment of 550 Bitcoins (approximately $1.62 million USD at the time). On June 19, 2017 The company stated that they had negotiated the payment to 397.6 Bitcoins (approximately $1.01 million USD) to be paid in installments.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Ransomware, Infection
Credit Card Breach at Buckle Stores (June 17, 2017)
The clothes retailer, "The Buckle Inc.," has released a statement in which they confirmed that some of their locations were infected with credit card stealing malware. Additionally, the company stated that the malware appeared to have been present on Point-of-Sale (POS) systems between October 28, 2016 and April 14, 2017. At the time of this writing, it is unknown how many individuals may have had their credit card data stolen.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of infection, the affected networks should be repopulated. Customers should also be notified and potentially offered fraud protection to avoid negative media coverage and reputation
Tags: POS, Credit card theft
Hacker "His Royal Gingerness" Jailed for Cyber-Attack on UK Hospital, Airport (June 16, 2017)
Daniel Devereux, known online as "His Royal Gingerness," has been sentenced to 32 weeks in prison for unauthorized access to websites owned by Norfolk and Norwich University Hospitals, and Norwich International Airport. Devereux used SQL injection attacks against said websites that made them inaccessible. Norwich Airport's website was down for three days and the damage was so severe that the management team decided to rebuild the entire website from scratch.
Recommendation: Properly sanitize user provided data to prevent injection attacks. Using prepared statements and stored procedures, implementing escape schemes, properly limiting privileged accounts, and using input validation are also different steps you can take to better protect your company from SQL injections attacks.
Tags: Cybercriminal, Compromised website
FIN10: Anatomy of a Cyber Extortion Operation (June 16, 2017)
According to FireEye researchers, the threat group called "FIN10" has been observed to be conducting extortion campaigns against Canadian casinos and mining companies. In the emails identified that have been sent to said entities, the group is claiming that they have stolen sensitive data and will make the information public unless a ransom is paid. The campaigns have primarily taken place between 2013 and 2016 and in some instances the stolen data was available in online locations. While some initial infection points are unknown, researchers did discover that in at least two instances spear phishing emails with malicious attachments were used.
Recommendation: Spear phishing emails represent a significant security risk because the sending email will often appear legitimate to the target; sometimes a target company email is compromised and used for such emails. Education is the best defense, inform your employees on what to expect for information requests from their managers and colleagues. Employees should also be aware of whom to contact when they suspect they are the target of a possible spear phishing attack.
Tags: APT, Extortion campaign, Data theft
SMILE – New PayPal Phish Has Victims Sending Them a Selfie (June 15, 2017)
A new PayPal-themed phishing campaign has been identified in which threat actors attempt to direct recipients to compromised websites that ask for PayPal credentials, according to PhishMe researchers. The emails claim that activity has been discovered in the recipient's PayPal account and instructs the recipient to follow a link to "recover" their account. The link leads to a legitimate website that has been compromised by an actor called "Mr.Dr3awe." If the link is followed, the phishing kit that has been implanted in the compromised website requests that the individual take a picture of themselves with a form of identification and credit card next to their face.
Recommendation: The impersonation of legitimate services continues to be an effective phishing tactic to steal Personally Identifiable Information (PII). All employees should be informed of the threat phishing poses, how to identify such attempts, and inform the appropriate personnel when they are identified.
Tags: Phishing, PayPal-themed
Nigerian BEC Scams Hit 500 Companies in 50 Countries (June 15, 2017)
Kaspersky researchers have discovered an increase in Business Email Compromise (BEC) conducted by Nigerian threat actors. Researchers discovered that within the past several months approximately 500 companies, largely located in the industrial and transportation sector, have been targeted with phishing emails. The emails purport that banking details are incorrect, or that an unknown payment has been made and requests that the recipient open an .RTF attachment to correct the details. The attachments have been identified to contain malicious macros, Microsoft Word exploits, or OLE objects that download information stealing malware.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified. Furthermore, maintain policies regarding what kind of requests and information your employees can expect to receive from colleagues, clients, and management.
Tags: Cybercriminal, BEC
DHS and FBI Publish Details on DeltaCharlie, North Korea's DDoS Botnet (June 14, 2017)
The U.S. Computer Emergency Response Team (CERT) and Federal Bureau of Investigation (FBI) have released a report discussing the malware family called "DeltaCharlie." The malware is believed to be used by the Democratic Republic of North Korea (DPRK) to create its own Distributed Denial-of-Service (DDoS) botnet. Researchers believe, via studying the IP addresses reported by US-CERT and the FBI, that DeltaCharlie is the third botnet created by the threat group called "HIDDEN COBRA" (Guardians of Peace, Lazarus Group).
Recommendation: Denial of service attacks can potentially cost your company loss in revenue because severe attacks can shut down online services for extended periods of time. With the leak of the Mirai botnet source code in October, the availability for threat actors to compromise vulnerable devices, and purchase DDoS for hire is a continually evolving threat. Mitigation technique can vary depending on the specifics of the attack. For example, in the case of BlackNurse, which can disrupt enterprise firewalls, ICMP type 3 traffic should be block, or at least rate limited.
Tags: DDoS botnet, Hidden Cobra
Analyzing Xavier: An Information-Stealing Ad Library on Android (June 13, 2017)
Approximately 800 applications in the Google Play Store have been discovered to contain an information stealing malware dubbed "Xavier," according to Trend Micro researchers (Google has since removed the malicious applications). Additionally, researchers found that the malicious applications had been downloaded "millions of times" and that the malicious ad library is also present in a variety of pre-installed Android applications.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, Malicious application
FIN7 Hitting Restaurants With Fileless Malware (June 13, 2017)
Morphisec Lab researchers have discovered that the financially motivated threat group called "FIN7" is targeting U.S. restaurants in a new phishing campaign. The phishing emails are being distributed with a RTF Word document attachment. If the document is opened and the recipient double clicks on an image of an envelope, and then clicks "OK" the infection process will begin. FIN7's objective is to install a backdoor on the restaurant's network in order to steal financial data.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified. Furthermore, maintain policies regarding what kind of requests and information your employees can expect to receive from colleagues and management.
Tags: APT, Phishing, Data theft
New "Matrix Banker" Trojan Targets Latin America (June 12, 2017)
A new banking trojan has been identified to be actively targeting financial institutions in Mexico and Peru, according to Arbor Networks researchers. The malware is being distributed when a user visits a malicious website, and is capable of injecting a Dynamic Link Library (DLL) into a web browser to conduct Man-in-the-Browser (MitB) attacks. Matrix Banker will perform a web injection, when an infected machine attempts to visit a banking website, that impersonates the legitimate website. The primary objective of the malware is to steal banking credentials. Researchers note that the malware appears to be under active development.
Recommendation: Your company should have appropriate antivirus, anti-spam, and policies in place that will prevent your employees from visiting potentially malicious websites. Education is also a great mitigation technique that can assist your company in awareness of the risks posed by visiting less reputable online locations.
Tags: Malicious websites, Banking trojan
Hacker "Sagade" Extradited to the US for the Role in Scareware Scheme (June 12, 2017)
Peter Sahurovs, a cybercriminal with the alias "Sagade," has been extradited to the U.S. for purchasing advertising space that was then used to show malicious advertisements. The malvertising campaign reportedly allowed Sagade and his accomplice to earn approximately $2 million USD in illicit revenue. The advertisements were, at first, legitimate, but were later identified to redirect users to malicious servers that downloaded malware onto the visiting machine. The malware would then display pop-ups that claimed that the machine had been infected with a virus and implored users to purchase a fake antivirus program.
Recommendation: Users should be cautious when clicking on advertisements because as this story portrays, malicious advertisements can sometimes appear on legitimate online locations. If the advertised product is appealing, it would be safer to search for the product on the authentic websites of the company who is selling the product, or other trusted online shopping locations.
Tags: Cybercriminal, Malicious advertisements
GameStop Confirms Payment Card Breach (June 12, 2017)
GameStop, the video games and electronics retailer, has confirmed a breach of its website (GameStop[.]com) and has begun reaching out to affected customers. On April 7, 2017, investigative reporter Brian Krebs first reported that the website may have been compromised. At that time the company had only confirmed that they had launched an investigation into the matter. GameStop stated that certain online transactions that took place between August 10, 2016 and February 9, 2017 resulted in payment card data being stolen for some online transactions.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of POS infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: POS, Credit card theft
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



