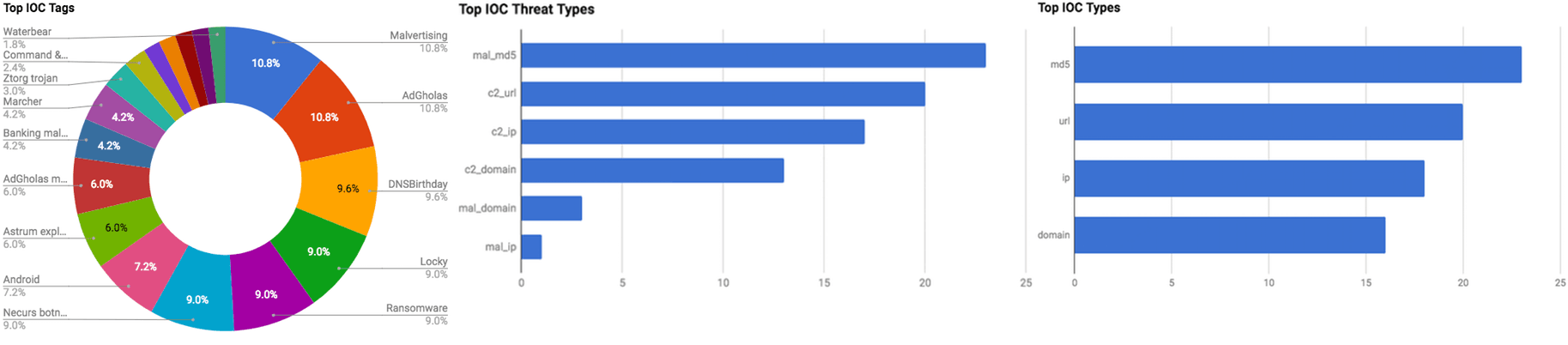

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
SamSam Ransomware Now Demands $33,000 from Victims (June 26, 2017)
AlienVault researchers have observed an increase in distribution of the "SamSam" ransomware. Additionally, the actors behind the campaign are demanding and increasing amount of funds for the decryption key. The malware is typically installed by exploiting an unpatched server vulnerability, according to researchers. Recently, threat actors have been demanding 1.7 Bitcoin (approximately $4,600 USD) for the decryption key for one machine. If multiple machines are infected, threat actors are demanding 6 Bitcoin (approximately $16,400 USD) to decrypt half of the machines, and 12 Bitcoin (approximately $32,800 USD) to decrypt all of the machines.
Recommendation: Always run antivirus and endpoint protection software to assist in preventing ransomware infection. Maintain secure backups of all your important files to avoid the need to consider payment for the decryption key. Emails received from unknown sources should be carefully avoided, and attachments and links should not be followed or opened. Your company should sustain policies to consistently check for new system security patches. In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: SamSam, Ransomware
Birthday Reminder Looks Benign but the Devil's In the Details: Hook DNS, Serves Dodgy Ads (June 23, 2017)
ESET researchers have discovered a "Birthday Reminder" application for Windows operating systems that has some hidden malicious features. The malware contained in the application, dubbed "DNSBirthday," can hook into DNS requests to inject advertisements into web pages. The malware loads multiple modules onto the infected machine, one of which is capable of gathering information about machine that is sent to a C2 before delivering advertisement payloads.
Recommendation: All applications should be carefully researched prior to installing on a personal or work machine. Additionally, all applications, especially free versions, should only be downloaded from trusted vendors.
Tags: DNSBirthday, Malicious application
New Android Marcher Variant Posing as Adobe Flash Player Update (June 22, 2017)
The banking malware called, "Marcher," has been observed being distributed via fake Adobe Flash Player updates, according to Zscaler researchers. If a device installs the fake update, the malware hides icon and will proceed to perform web injection overlays attacks. The overlays impersonate legitimate banking applications and will gather the data that is inputted by the user and send it to a C2.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Marcher, Mobile malware, Android
Following the Trail of BlackTech's Cyber Espionage Campaigns (June 22, 2017)
According to Trend Micro researchers, a cyber espionage threat group called, "BlackTech," has been discovered to be attacking targets located in East Asia. The group appears to have been active since at least 2010 and has primarily targeted Taiwan, however, Hong Kong and Japan have also been targeted. Additionally, researchers have discovered connections between BlackTech operations and other information theft campaigns codenamed PLEAD, Shrouded Crossbow, and Waterbear; this appears to indicate that the same group is behind the campaigns.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of phishing, how to identify such attempts.
Tags: APT, BlackTech, Cyber espionage
Player 1 Limps Back Into the Ring - Hello Again, Locky! (June 21, 2017)
The malspam botnet, "Necurs," has been observed switching back to distributing "Locky" ransomware and away from previous "Jaff" ransomware distribution, according to Talos researchers. The spam emails claim that an attached .zip file contains information for a previously placed order. The Locky ransomware is contained in a .exe file that is encapsulated within two compressed .zip archives.
Recommendation: All employees should be educated on the risks of malspam, and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided. Furthermore, it is paramount to have a comprehensive and tested backup solution in place. If a reproducible backup is not available, there may a decryptor available that can assist in retrieving encrypted files.
Tags: Locky, Necurs, Malspam
Honda Halts Japan Car Plant After WannaCry Hits Computer (June 21, 2017)
The Honda Motor Company has stated that its Sayama manufacturing plant was affected by the "WannaCry" ransomware on June 19, 2017. The company reported that it shut down all manufacturing in the Sayama plant for the entire day while they underwent mitigation procedures to contain and remove the malware.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. If a reproducible backup is not available, there may a decryptor available that can assist in retrieving encrypted files.
Tags: WannaCry, Breach
Ztorg: From Rooting to SMS (June 20, 2017)
Two malicious applications were discovered in the Google Play Store that were downloaded in total more than 60,000 times, according to Kaspersky researchers. One of the applications, called "Magic Browser," was downloaded approximately 50,000 times and the other, called "Noise Detector," was downloaded approximately 10,000 times. Both applications contain malicious code that is similar to the "Ztorg" malware family. Ztorg is capable of receiving remote commands that can allow it to steal money from an infected device's account, among other features.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Ztorg, Mobile malware
AdGholas Malvertising Campaign Employs Astrum Exploit Kit (June 20, 2017)
TrendMicro researchers have discovered a new "AdGholas" malvertising campaign that is using the "Astrum" exploit kit to deliver malware. Researchers identified 262,163 separate events that involved AdGholas C2's with the traffic coming largely from the U.S. and Japan. While no specific malware payloads were identified, the traffic did appear to coincide with ransomware attacks in the U.K.
Recommendation: Malvertising and exploit kits, in general, are being developed and improved constantly by cybercriminals, therefore keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: AdGholas, Malvertising
Minimalist Alina POS Variant Starts Using SSL (June 19, 2017)
A new variant of the Point-of-Sale (POS) malware called "Alina" has been discovered, according to SpiderLabs researchers. The malware was first identified in the wild in late 2012, and in this variant the threat actors have removed some features in favor of a Secure Socket Layer (SLL) tunnel. In this manner, Alina is able to add another layer of encryption in addition to obfuscating the stolen credit card data using a legacy XOR scheme.
Recommendation: Customer-facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats, and important network infrastructure should be segregated. In the case of infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: Alina, POS malware
The RNC Files: Inside the Largest US Voter Data Leak (June 19, 2017)
UpGuard's Cyber Risk Team discovered an Amazon S3 Bucket that was misconfigured in a way that allowed public access. The cloud server was owned by U.S. Republican National Committee employed data firm, "Deep Root Analytics," and contained Personally Identifiable Information (PII) belonging to approximately 198 million American voters. UpGuard discovered the database on June 12, 2017, and subsequently informed federal authorities; the cloud server was secured from public access on June 19, 2017. The data consisted of date of birth, full name, home address, phone numbers, voter registration details, and other unspecified "modeled" data regarding ethnicity and religion.
Recommendation: It is crucial for your company to verify that access control is configured correctly prior to adding any sensitive data. As this story portrays, misconfigured databases has the potential to cause significant harm to individuals and a company's reputation.
Tags: Misconfigured database, Data leak
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



