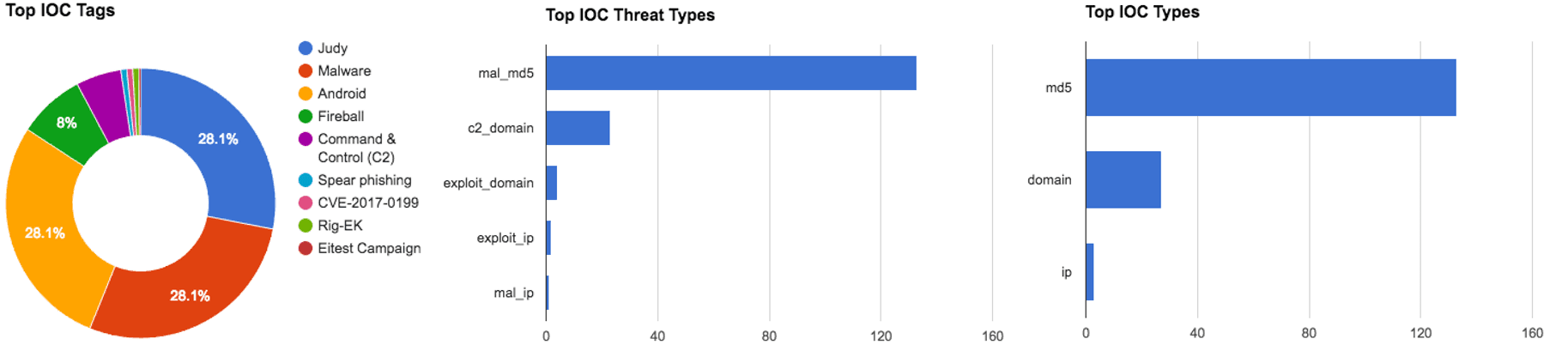

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
RoughTed Malvertising Operation Leads to "RELST" Domains and RIG EK (June 5, 2017)
Researchers have discovered a new malvertising campaign, dubbed "RELST," that appears to be connected to the "RoughTed" malvertising campaign. Malicious scripts were identified on websites associated with streaming. Additionally, some of the websites attempt to redirect users to the RIG Exploit Kit to download information stealing malware. Other related domains attempt to trick users into downloading a "missing ArialText" format. Another domain claims that the user's webcam has been compromised, and requests the user to download a file to view the photos that have been stolen.
Recommendation: Malvertising and exploit kits in general are being developed and improved constantly by cybercriminals, so keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: Malvertising, Exploit Kit
Fireball – The Chinese Malware of 250 Million Computers Infected (June 1, 2017)
Check Point researchers have identified a new campaign that uses a unique malware dubbed "Fireball," that infects machines by compromising web browsers. Researchers believe that approximately 250 million machines have been infected. Additionally, Check Point researchers believe that the digital marketing agency "Rafotech" is behind this campaign. The malware is believed to be distributed by bundling it with other Rafotech products and other free software distributors. Fireball is capable of taking over a user’s web browser as well as downloading files, hijacking and manipulating web-traffic to generate advertising revenue, and running code on the infected machine.
Recommendation: Free applications should be regarded with the utmost scrutiny before they are downloaded because as this story depicts, free software can sometimes come with security risks. Additionally, keeping track of the applications used by your company is important because unknown applications discovered on machines may indicate an infection. The same method should also be applied to web browser add-ons.
Tags: Malware campaign
OneLogin: Breach Exposed Ability to Decrypt Data (June 1, 2017)
OneLogin, the online service that allows users to manage login credentials to multiple websites and applications, has experienced a breach. Currently unknown actors were able to gain access to customer data in the U.S. region. Additionally, OneLogin stated that the cybercriminals also accessed information that would allow them to decrypt encrypted user data.
Recommendation: OneLogin has release several steps it suggests all customers take. This includes generating new API keys and OAuth tokens (OAuth being a system for logging into accounts), creating new security certificates as well as credentials, recycling any secrets stored in OneLogin's Secure Notes feature, and having end-users update their passwords, amongst others.
Tags: Breach
Credit Card Breach at Kmart Stores. Again (May 31, 2017)
Members of the financial industry have recently reached out to security researcher Brian Krebs with concerns that a breach had occurred at Kmart stores. Kmart's parent company, Sears Holdings, was asked about a potential breach. In their response they confirmed that "a security incident involving unauthorized credit card activity following certain customer purchases" had occurred. Sears Holdings stated that some credit card numbers have been compromised but no Personally Identifiable Information (PII) was stolen. The company did not mention the amount of Kmart stores that were compromised or how long malware was present on their payment systems.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: Breach, Credit card theft
Vulnerability Affecting 1,000+ Apps Is Exposing Terabytes of Data (May 31, 2017)
A new backend data exposure vulnerability dubbed "HospitalGown" has been discovered to affect more than 1,000 mobile applications, according to Appthority researchers. The applications affected by HospitalGown are connecting to unsecured services such as Elasticsearch and MySQL leaving significant amounts of data vulnerable to theft. The exposed data consists of corporate profile information such as email addresses, phone numbers, and VPN PINs, in addition to other forms of Personally Identifiable Information (PII), location, passwords, and travel and payment details.
Recommendation: It is important to configure database settings because default configurations are not always secure. Actors can use services like Shodan scans to index everything that uses IPv4 to connect to the internet, thus making secure configurations paramount to the security of the server.
Tags: Vulnerability, Data theft
Motorcycle Gang Busted for Hacking and Stealing Over 150 Jeep Wranglers (May 31, 2017)
The U.S. Federal Bureau of Investigation (FBI) has arrested members of Tijuana, Mexico-based motorcycle gang for the theft of over 150 Jeep Wranglers in Southern California. Members of the group would first identify the Vehicle Identification Number (VIN) of a Jeep Wrangler and pass it off to their leader via Facebook. Then another member would access a proprietary database that contained replacement key codes for Jeep Wrangler models. The code would then be used to create a key for the Jeep that would then be stolen by the gang.
Recommendation: Databases should not be directly accessible over or connected to the internet. For web applications that are accessing database data, make sure all user supplied data is sanitized to prevent SQL injections.
Tags: Cybercrime, Theft
Eitest Campaign Pushing Tech Support Scams, RIG EK, Hoeflertext Popups (May 30, 2017)
Researchers have discovered a new "Eitest" campaign that attempts to execute different malicious activity based on the web browser visiting a compromised website. Actors behind this campaign first compromise legitimate websites. The compromised websites have been observed distributing tech support scams and redirecting users to the RIG Exploit Kit to download additional malware for Internet Explorer users. Chrome users have been observed to be targeted with the HoeflerText popup that claims text is missing and that the web page must be updated to properly view the text. If "updated," Spora ransomware will infect the machine.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Compromised websites
Spear Phishing Fileless Attack with CVE-2017-0199 (May 30, 2017)
FortiGuard researchers have discovered a spearphishing campaign that is distributing malicious Rich Text Format (RTF) file attachments. If the file is opened in a vulnerable version of Microsoft Word, the exploit registered as CVE-2017-0199 is activated. It will then proceed to download a malicious HTML Application (HTA) payload that is capable of conducting multi-vector attacks.
Recommendation: Microsoft issued a patch to fix this vulnerability in April 2017, and the patch should be applied as soon as possible if has not been done so already. Spear phishing emails represent a significant security risk because the sending email will often appear legitimate to the target; sometimes a target company email is compromised and used for such emails. Education is the best defense, inform your employees on what to expect for information requests from their managers and colleagues. Employees should also be aware of whom to contact when they suspect they are the target of a possible spear phishing attack.
Tags: Spear Phishing, Vulnerability
Vulnerability Opens FreeRADIUS Servers to Unauthenticated Attackers (May 30, 2017)
A vulnerability has been discovered in the open source FreeRADIUS server that could be exploited to bypass authentication via Protected Extensible Authentication Protocol (PEAP) or Tunneled Transport Layer Security (TTLS). At the time of this writing, the vulnerability has not been identified to have been exploited in the wild, however, with this information available in public sources the probability of attacks increases. The FreeRADIUS Development Team has issued a patch to fix the vulnerability.
Recommendation: Ensure that your server is always running the most current software version. Additionally, maintaining secure passwords for RDP and other remote access systems is paramount; passwords should be a minimum of eight characters and should be used in combination with multi-factor authentication. Intrusion detection systems and intrusion prevention systems can also assist in identifying and preventing attacks against your company's network. Furthermore, always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe). In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: Vulnerability
Around 36.5 Million Android Devices Have Been Infected by Judy Malware (May 29, 2017)
The Android malware called "Judy," which was first reported by Check Point researchers in late May, has infected approximately 36.5 million devices. Researchers believe that the Judy malware campaign is the largest to have ever been identified in the Google Play store (Google has since removed the malicious applications). The auto-clicking adware was observed to have been located in 41 applications developed by the Korean company Kiniwini. In addition to generating clicks for advertisement revenue, Judy will also display advertisements that leave users no other option except to click on the advertisement itself.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. Additionally, applications should not be trusted based off of their store ratings alone.
Tags: Android, Mobile, Malware
Shadow Brokers Lay Out Pitch – and Name Price – for Monthly Zero-day Subscription Service (May 29, 2017)
The threat group "The Shadow Brokers" (TSB), known for leaking U.S. National Security Agency (NSA), has launched a new service. The service is a subscription-based zero-day feed that must be paid for with the Zcash (ZEC) cryptocurrency. TSB is currently asking 100 ZEC (approximately $21,000 USD) per month for this subscription.
Recommendation: The Shadow Brokers have leaked malicious tools to open sources in the past, so it is possible that they may do so again, or they may be purchased. It is also possible that the malicious tools will be used in future attacks and, if that occurs, companies will be racing to issue patches to fix the problems. Therefore, it is crucial to stay up-to-date on the latest security patches.
Tags: Cybercrime
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
RIG exploit kit Tool Tip
The RIG exploit kit is a framework used to exploit client side vulnerabilities in web browsers. The RIG exploit kit takes advantage of vulnerabilities in Internet Explorer, Adobe flash, Java and Microsoft Silverlight. The RIG exploit kit was first observed in early 2014. The RIG exploit kit's objective is to upload malicious code to the target system. The RIG exploit kit is known to distribute ransomware, spambots and backdoors. Victims are redirected to the RIG exploit kit with a landing page coming from malvertising or compromised sites.
Tags: RIG, exploitkit
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



