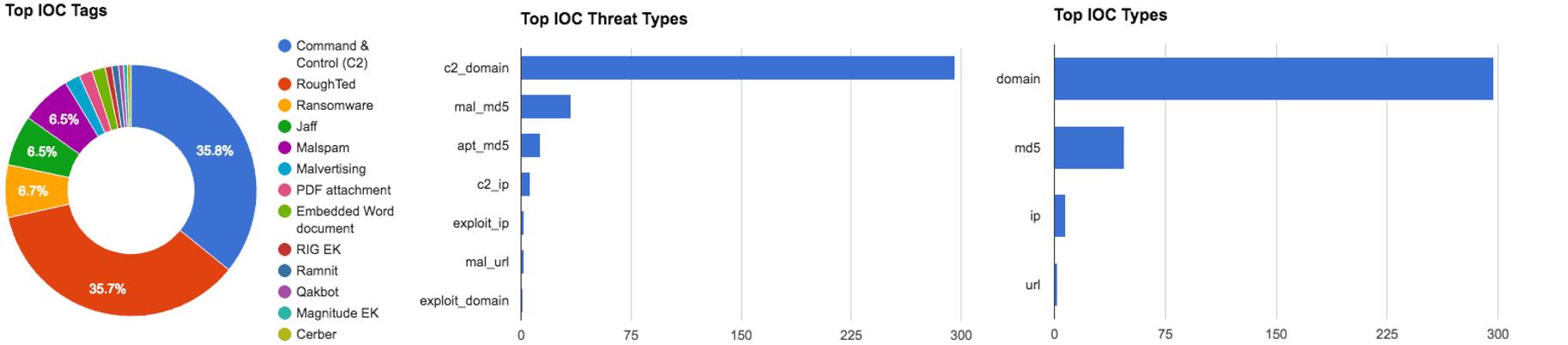

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
Most Chipotle Restaurants Hacked With Credit Card Stealing Malware (May 28, 2017)
Chipotle restaurants has released additional information concerning a malware infection that has affected "most, but not all restaurants." The restaurant first confirmed the incident on April 25, 2017, and has now reported that the breaches took place between March 24 and April 18. The malware was designed to steal track data from the magnetic strip on credit cards by infecting Chipotle cash registers. At the time of this writing, it is unknown how many people may have had their credit card data stolen.
Recommendation: Point-of-Sale (POS) Security relies on the same type of preventative measures as all others, because they are a unique type of computer. In the case of a confirmed infection, the POS must be taken offline until it can be completely wiped and restored to its original factory settings. An audit of the transactions performed on the POS should occur along with a formal incident response investigation.
Tags: Breach, Credit card theft
RoughTed: The Anti Ad-Blocker Malvertiser (May 25, 2017)
Malwarebytes researchers have published their findings regarding a large-scale malvertising campaign dubbed "RoughTed" that has been active for at least one year. The actors behind this campaign tailor fingerprinting techniques to bypass ad-blockers. The malicious advertisements direct users to domains that host exploit kits that tailor the malicious payloads. The payloads vary depending on the geolocation, operating system, and web browser of the visiting machine.
Recommendation: Malvertising and exploit kits in general are being developed and improved constantly by cybercriminals, so keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: Malvertising
Malspam Pushing Jaff Ransomware (May 24, 2017)
A new malspam campaign has been discovered to be distributing Jaff ransomware via malicious PDF attachments. The PDF attachments have embedded Word documents that will infect the machine if macros are enabled. As of this writing, the malware demands 0.33359562 Bitcoins ($896.19 USD) for the decryption key.
Recommendation: All employees should be educated on the risks of malspam, and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided
Tags: Ransomware, Malspam
7-Year-Old Samba Flaw Lets Hackers Access Thousands of Linux PCs Remotely (May 24, 2017)
A remote code execution vulnerability, registered as CVE-2017-7494, has been discovered in all versions after 3.5.0 the open source networking software, Samba. Samba uses Server Message Block (SMB) protocol that allows operating systems like Linux, or macOS to share network shared files, folders, and printers with Windows operating systems. Researchers used the Shodan search engine and discovered that, as of this writing, approximately 485,000 computers are using Samba, and 104,000 machines are running vulnerable versions.
Recommendation: Threat actors are often observed to use vulnerabilities even after they have been patched by the affected company. Therefore, it is crucial that policies are in place to ensure that all employees install patches as soon as they are made available.
Tags: Vulnerability
Qatar Begins Probe After State News Agency Hacked (May 24, 2017)
The Qatar Communications Office has stated that the Qatar News Agency (QNA) website and Twitter account were compromised by unknown actors. The cybercriminals then posted content on the QNA website pretending to come from the country’s foreign minister, Mohammed bin Abdulrahman Al-Thani. The foreign minister's purported content discussed the Palestinian-Israeli conflict, Palestinian Islamist movement Hamas, and strategic relations with Iran. Social media platforms subsequently erupted in Gulf countries as users insulted and accused each other of wrongdoings. This incident occurred as U.S. President Trump was traveling in Middle Eastern countries.
Recommendation: This story represents potential threats and attacks that can arise based on current political geopolitical developments. Therefore, awareness of tension between countries and governments can potentially grant some insight as to where attacks may originate. It is crucial that server software be kept up-to-date with the most current versions and that all external facing assets are carefully monitored and scanned for unusual activity and vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Compromised website, Geopolitical
Threat Spotlight: The Return of Qakbot Malware (May 23, 2017)
The information stealing malware called "Qakbot" (Qbot) has been observed to be increasing its infection efforts, according to Cylance researchers. The researchers note that, as of this writing, it is unknown what is causing the increased infections, although it may be possible that the actors behind Qakbot are using different exploit kits for propagation. The polymorphic features have assisted the malware in remaining active since at least 2009.
Recommendation: Always keep your browser and operating system up to date, including any browser add-ons you may need (Flash, Java). Employ network as well as host based detection and prevention systems where possible. In the case of Qakbot infection, the affected system must be wiped and reformatted, and other devices on the network should be checked for similar infections.
Tags: Malware, Exploit Kits
Jaff Ransomware Gets a Makeover (May 23, 2017)
Security researcher Brad Duncan has discovered that the "Jaff" ransomware, first discovered in early May 2017, has been updated. This new variant has an updated decoy document that is being distributed via the Necurs botnet and is using the .wlu file extensions for encrypted files. The Jaff malspam campaign is using PDF attachments with embedded Word documents that pose as an invoice, and request that macros be enabled to properly view the document. If done, the ransomware will encrypt and append .wlu to files. The cybercriminals request approximately 0.356 Bitcoins ($837 USD) for the decryption key.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, it is important to have a comprehensive and tested backup solution in place for the unfortunate case of ransomware infection.
Tags: Ransomware, Malspam
Russia Dismantles Major Cybercrime Operation Targeting Bank Accounts via Android Malware (May 23, 2017)
The Russian Interior Ministry has announced that it has identified 20 suspects believed to be associated with the threat group behind the Android banking trojan called "Cron." Russian authorities apprehended 16 members in November 2016, and another member in April 2017. The Cron malware dates back to at least 2015, and could be leased by cybercriminals on underground markets. Researchers believe that the malware has stolen approximately $900,000 USD.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores.
Tags: Cybercrime
Tax Worker Fired After Biggest Privacy Breach at Revenue Canada (May 22, 2017)
An employee at the Canada Revenue Agency (CRA) has been fired for unauthorized access of approximately 1,264 CRA accounts. The CRA stated that they discovered that this incident had occurred after an investigation was launched on March 23, 2016, but they are just now releasing information about the breach. Data associated with the accounts consisted of contact information, employment information, full name, income and deductions, and social insurance number.
Recommendation: Policies should be in place regarding employee account privileges in order to limit access to data. Additionally, guidelines should also be in place that educate employees who do have access to sensitive information on how to properly access and handle the data.
Tags: Breach
Be Aware: WannaCry Ransomware Outbreak Used by Phishing Attacks (May 22, 2017)
Researchers have discovered a new phishing campaign that purports to be a "security upgrade" from the U.K. telecommunications provider, British Telecommunications (BT). The email claims that due to recent "security breaches on an international scale" BT is launching preventative measures via a security update. The email provides a link that directs a recipient to a fake website that will steal BT credentials.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified.
Tags: Ransomware, Phishing
New XData Ransomware Spreads Faster Than WannaCry (May 22, 2017)
A new ransomware campaign has been identified to be targeting businesses and individuals in Ukraine at a s significant pace, according to the security researcher MalwareHunter. The ransomware is called "XData" and, as of this writing, has infected four times as many victims than an entire week of the global WannaCry ransomware campaign.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. If a reproducible backup is not available, there may a decryptor available that can assist in retrieving encrypted files. Additionally, educate your employees about the dangers of downloading applications when they are not offered from the website of the official provider/developer.
Tags: Ransomware
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
RIG exploit kit Tool Tip
The RIG exploit kit is a framework used to exploit client side vulnerabilities in web browsers. The RIG exploit kit takes advantage of vulnerabilities in Internet Explorer, Adobe flash, Java and Microsoft Silverlight. The RIG exploit kit was first observed in early 2014. The RIG exploit kit's objective is to upload malicious code to the target system. The RIG exploit kit is known to distribute ransomware, spambots and backdoors. Victims are redirected to the RIG exploit kit with a landing page coming from malvertising or compromised sites.
Tags: RIG, exploitkit
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



