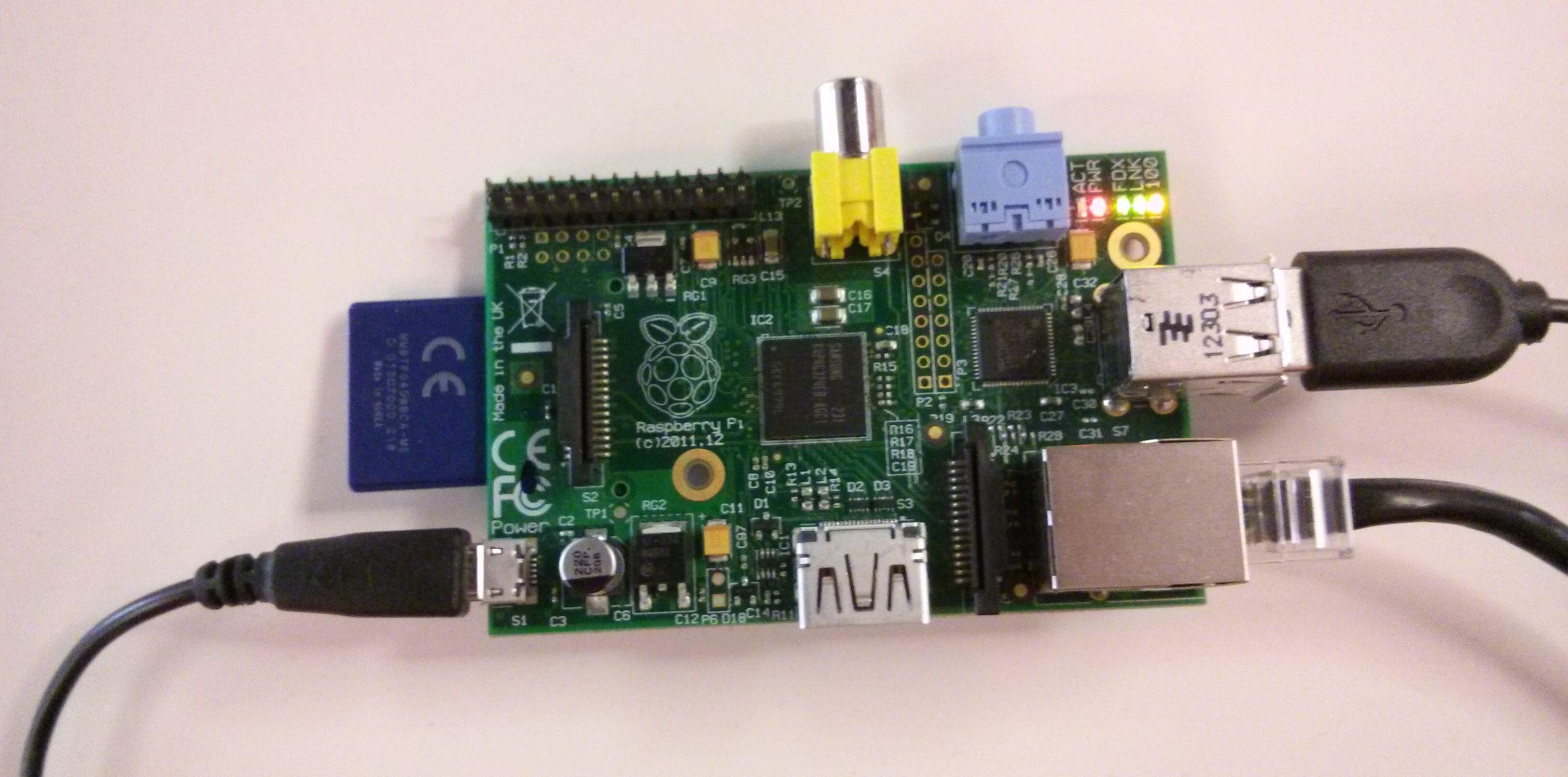

<p>Hi! My name is <a href="http://www.linkedin.com/in/nathanmyee" target="_blank">Nathan Yee</a> and I’m an intern at ThreatStream. I’m studying computer science and mathematics at the <a href="http://www.arizona.edu/" target="_blank">University of Arizona</a>. Most recently, I worked on deploying a Raspberry Pi as a Dionaea honeypot for the recently announced <a href="http://threatstream.github.io/mhn/" target="_blank">Modern Honey Network</a> project.</p><h2><span style="line-height: 1.6;">Why Internal Honeypots?</span></h2><p><span style="line-height: 1.6;">Let’s start with a plausible scenario. A colleague opens a link from an email which promises pictures of <a href="http://www.vpfunworld.com/wp-content/uploads/2014/03/cute-puppy-photos-.jpg" target="_blank">cute puppies</a>, but it’s actually malware which installs an <a href="http://en.wikipedia.org/wiki/Advanced_persistent_threat" target="_blank">advanced persistent threat</a> (APT) malware kit. Now, the attacker has access to the compromised machine and our internal network. She begins scanning the network to start the covert information gathering process and to find additional exploitable machines.</span></p><p>Organizations typically focus on monitoring inbound and outbound network traffic via firewalls, yet ignore internal network traffic due to the complexity involved. In the scenario above, a firewall will not protect or alert us.</p><p>By running honeypots on our internal network, we are able to detect anomalous events. We gain awareness and insight into our network when network hosts interact with a Raspberry Pi honeypot sensor. Since there isn’t a good reason to interact with it (since it doesn’t do anything), activity on the Raspberry Pi is usually indicative of something roaming around our network and a possible security breach.</p><h2><span style="line-height: 1.6;">Why Raspberry Pi?</span></h2><p><span style="line-height: 1.6;">We wanted to use a Raspberry Pi as a honeypot because of its low profile, minimal power consumption, and most importantly, it’s CHEAP! Understandably, not everyone has a big budget to spend on monitoring things like internal network traffic. Raspberry Pi devices are cost effective, so it is realistic to add 30 network sensors, which would cost around $1,000. Imagine (and experience for yourself) how powerful it is to add this kind of tooling to your security arsenal (or your house)!</span></p><h2>MHN + Raspberry Pi = #WINNING</h2><p>When we released MHN, it included the capability of deploying four types of honeypots: Dionaea, Kippo, Snort, and Conpot. These are deployed across servers worldwide to collect a diverse set of threat intelligence indicators.</p><p>We want to make the process of adding a Raspberry Pi to an MHN system easy and painless. It is my hope I’ve been successful here. It’s as simple as running a single command. Last week I created a <a href="https://github.com/threatstream/mhn/wiki/Deploying-Dionaea-on-a-Raspberry-Pi" target="_blank">step-by-step tutorial</a> with lots of pictures that covers the process from start to finish.</p><p><img alt="" src="https://cdn.filestackcontent.com/mluNYgp5RDu8GUFrMJgt"/></p><p><span style="line-height: 1.6;">If you have any comments, questions, or feedback, feel free to contact us at <a href="mailto:modern-honey-network@googlegroups.com?subject=MHN%20raspberry%20pi%20question">modern-honey-network@googlegroups.com</a></span><span style="line-height: 1.6;">. We created the Raspberry Pi and MHN integration to collectively help others with an important, but often overlooked aspect of network security. Stay tuned for more as this project continues to evolve!</span></p>
FEATURED RESOURCES

Anomali Cyber Watch
Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more
Zero-Click Remote Code Execution Flaw Affects Claude Desktop Extensions. Threat Actors Exploit SolarWinds Web Help Desk Vulnerabilities to Deploy Velociraptor. Fake 7-Zip Site Distributes Trojanized Installer Converting Systems to Proxy Nodes. ZeroDayRAT Commercial Mobile Spyware Targets Android and iOS. And more..

Anomali Cyber Watch
Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more
Notepad++ Supply Chain Attack Delivers Chrysalis Backdoor. Android RAT Uses Hugging Face Platform to Host Malicious Payloads. Fancy Bear Exploits Microsoft Office Flaw in Ukraine. Nitrogen Ransomware Decryptor Fails Due to Coding Error. And more...


