Detecting the ToolShell SharePoint Exploit


ToolShell is a term used by researchers to describe a sophisticated post-exploitation attack chain targeting Microsoft SharePoint servers. This campaign has been widely observed exploiting a zero-day vulnerability now registered as, CVE-2025-53770, allowing unauthenticated remote code execution via crafted requests to ToolPane.aspx. Threat actors, including those attributed to China-based groups such as Linen Typhoon, Violet Typhoon, and Storm-2603, began abusing this flaw in mid-2025. The attack chain involves harvesting cryptographic keys, crafting valid signed payloads, and achieving persistent access. This report walks through the exploitation steps, detection strategies, and four Anomali Query Language (AQL) queries designed to assist defenders in identifying potential suspicious activity.
Introduction
The CVE-2025-53770 vulnerability affects SharePoint Server 2016, 2019, and Subscription Edition. It allows threat actors to exploit the ToolPane.aspx endpoint without authentication by spoofing the Referrer header to point to SignOut.aspx. If successful, the attacker can drop a reconnaissance payload (spinstall0.aspx) and begin harvesting the server’s cryptographic keys.
This report aims to provide a detection-focused breakdown of this threat, outlining four AQL log-based hunting queries that security teams can deploy to uncover different stages of the attack chain.
What is ToolShell?
"ToolShell" is a name given by cybersecurity researchers to a SharePoint-focused attack sequence, not a downloadable toolkit. The attack involves:
- Gaining initial access via ToolPane.aspx (active server page extended files (ASPX) are webpages that use Active X scripting and are created by Internet servers).
- A reconnaissance payload is typically a dropped .aspx file like spinstall0.aspx, though advanced variants perform in-memory key extraction without writing any file to disk.
- Dumping machine keys from memory or config files.
- Using those keys to craft malicious ViewState payloads for unauthenticated remote code execution (RCE).
Key behaviors observed:
- spinstall0.aspx is a malicious .aspx file that extracts ValidationKey and DecryptionKey values from the target server.¹
- These stolen keys are used with tools like ysoserial.net to craft signed ViewState payloads that trigger remote execution when submitted to vulnerable endpoints.²
- Additional modules such as reflective loaders, PowerShell payloads may be used after the initial compromise for persistence or lateral movement.³
Exploitation Chain Breakdown
ToolShell Attack Chain
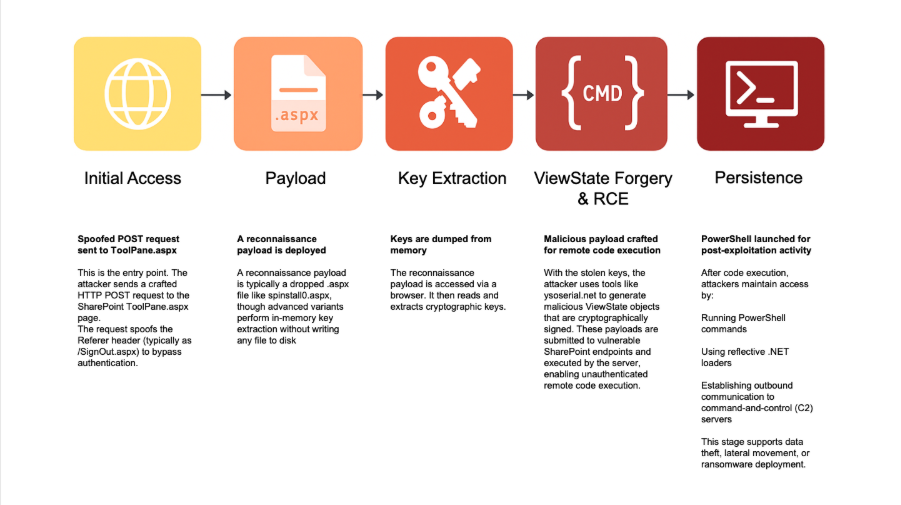
Step 1: Initial Access
A spoofed HTTP POST request is sent to:
/layouts/15/ToolPane.aspx?DisplayMode=Edit
with a Referrer header set to SignOut.aspx, bypassing authentication checks.⁴
Step 2: Reconnaissance Payload Deployment
A PowerShell command writes payload (spinstall0.aspx) into the SharePoint LAYOUTS directory.⁵
Step 3: Key Extraction
spinstall0.aspx is invoked via HTTP GET, dumping sensitive values such as:
- ValidationKey
- DecryptionKey
These are typically found in the web.config file or pulled from memory.⁶
Step 4: ViewState Forgery and RCE
With the keys, attackers use ysoserial.net to create malicious ViewState payloads that allow unauthenticated command execution.⁷
Step 5: Post-Exploitation & Persistence
Command execution typically involves PowerShell payloads, in-memory .NET reflection, or outbound Command and Control (C2) to hardcoded IPs such as 107.191.58[.]76.⁸
ToolShell Kill Chain
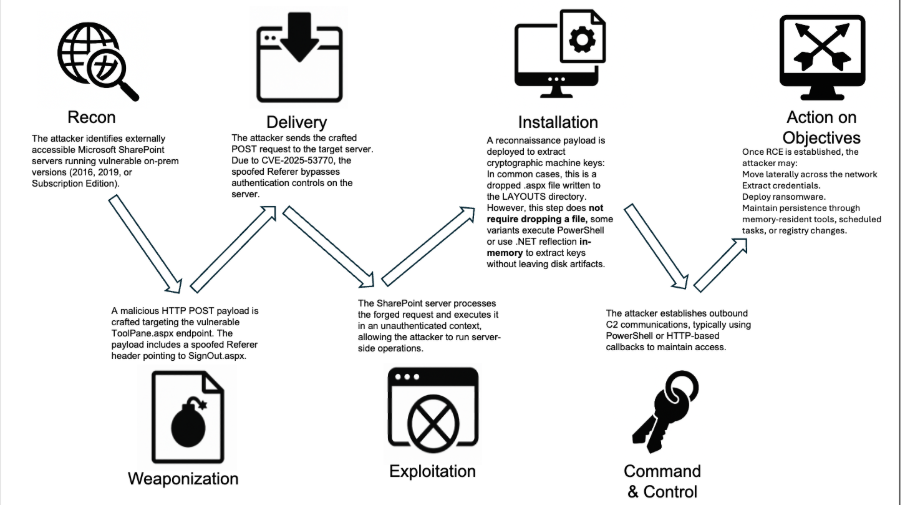
Detection Strategy Overview
Detection is structured into four categories, each with a tailored AQL query:
Recommended Log Sources:
- Internet Information Services (IIS), web proxy logs for HTTP detection
- Sysmon or EDR for process tracking
- Network/firewall/IDS logs (for C2 detection)
About spinstall0.aspx
spinstall0.aspx is not a web shell in the conventional sense. It does not provide interactive access but instead performs a single function, dumping cryptographic key material from the SharePoint environment. This file is a key part of the attack chain and should be treated as a high-confidence IOC.⁹
Detection Queries
Query 1: HTTP Request Indicators (Initial Exploitation)
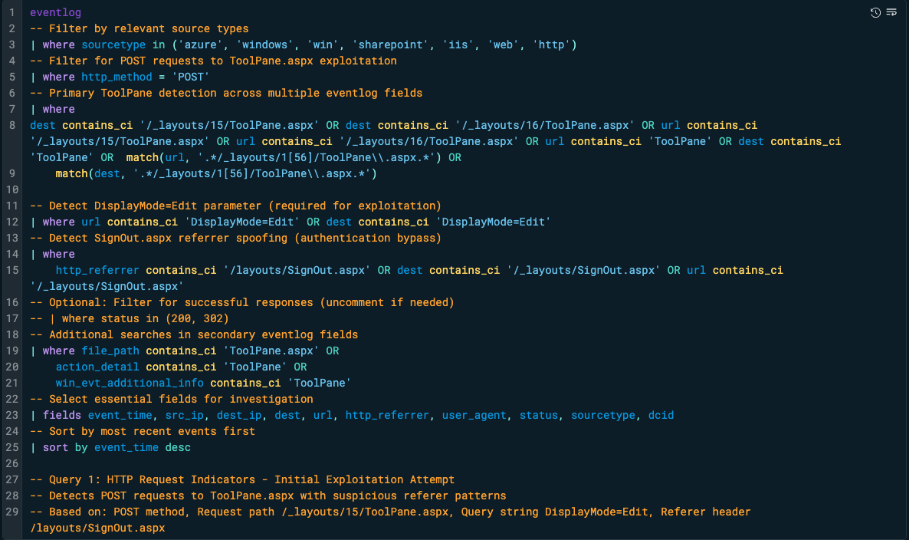
This detection query targets the initial access vector of the ToolShell attack chain by identifying suspicious HTTP POST requests to ToolPane.aspx, a key component exploited in CVE-2025-53770.
The query focuses on web logs and filters for requests where the URL includes /layouts/15/ToolPane.aspx or /layouts/16/ToolPane.aspx, combined with the query parameter DisplayMode=Edit. This specific parameter is required to trigger the vulnerable SharePoint control.
To catch authentication bypass attempts, the query looks for spoofed Referrer headers referencing /layouts/SignOut.aspx. Multiple fields such as url, dest, file_path, action_detail are checked to account for differences in how various logging systems store request data. The use of the POST method, the exact path and parameter combination, and the forged referrer together form a high-confidence indicator of a possible exploitation attempt. This approach aims to ensure visibility into both successful and blocked requests, while minimising false positives.
The query tightens focus by inspecting web request metadata for ToolShell specific indicators, including:
- POST requests to /layouts/15/ToolPane.aspx or /layouts/16/ToolPane.aspx
- Presence of the DisplayMode=Edit query parameter (required to trigger the vulnerable control)
- Spoofed Referrer headers pointing to /layouts/SignOut.aspx (used for authentication bypass)
- Matching references to ToolPane.aspx across multiple fields (url, dest, file_path, action_detail)
- Optional filtering for successful HTTP response codes (200, 302)
Query 2: Web Shell Indicators (Malicious File Access and Creation)
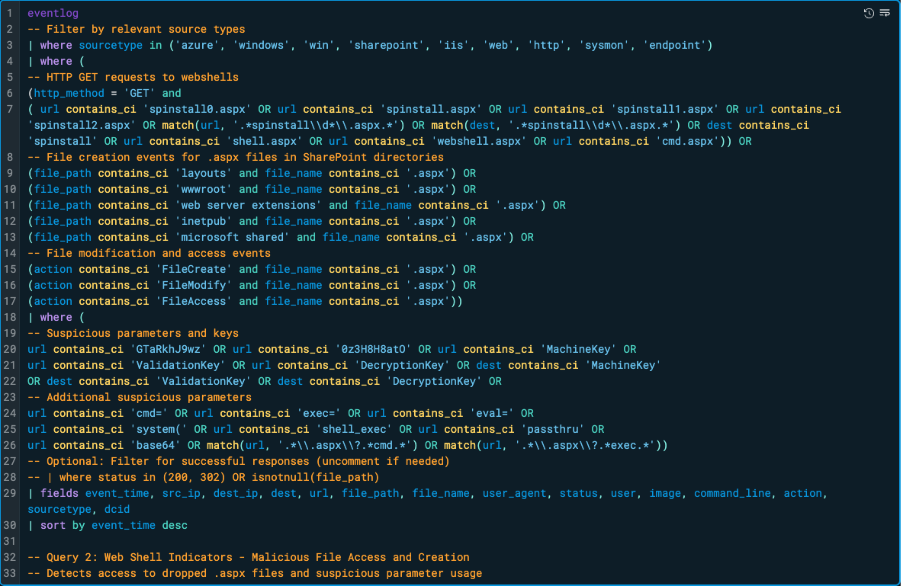
This detection query identifies post-exploitation activity tied to the deployment and use of malicious .aspx files, specifically reconnaissance payloads like spinstall0.aspx used in the ToolShell attack chain. It monitors both HTTP GET requests and local file system activity to catch cases where these payloads are either accessed via the web or created on disk.
The query looks for .aspx file creation, modification, or access events under typical SharePoint paths such as LAYOUTS, wwwroot, inetpub, Microsoft Shared, as these are common targets for attacker webshell drops. Moreover, the query inspects URL and destination fields for known ToolShell-related filenames such as spinstall0.aspx and patterns “spinstall\d+.aspx” as well as generic web shell indicators like cmd.aspx or webshell.aspx.
Furthermore, the query flags suspicious URL parameters that signal key extraction such as ValidationKey, DecryptionKey, MachineKey or remote code execution attempts cmd=, exec=, eval=. This two-fold focus on both file activity and HTTP traffic ensures the detection can catch both interactive web shell use and stealthy reconnaissance payloads that masquerade as legitimate content.
The query tightens focus by detecting malicious file activity and HTTP access patterns, including:
- Web shell access patterns (spinstall0.aspx, cmd.aspx, and webshell.aspx)
- File creation and access in SharePoint paths (layouts, inetpub, wwwroot, Microsoft Shared)
- Key extraction strings (MachineKey, ValidationKey, DecryptionKey)
- Remote execution parameters (cmd=, exec=, eval=, system()
Query 3: Process and Execution Indicators (Suspicious Child Processes)
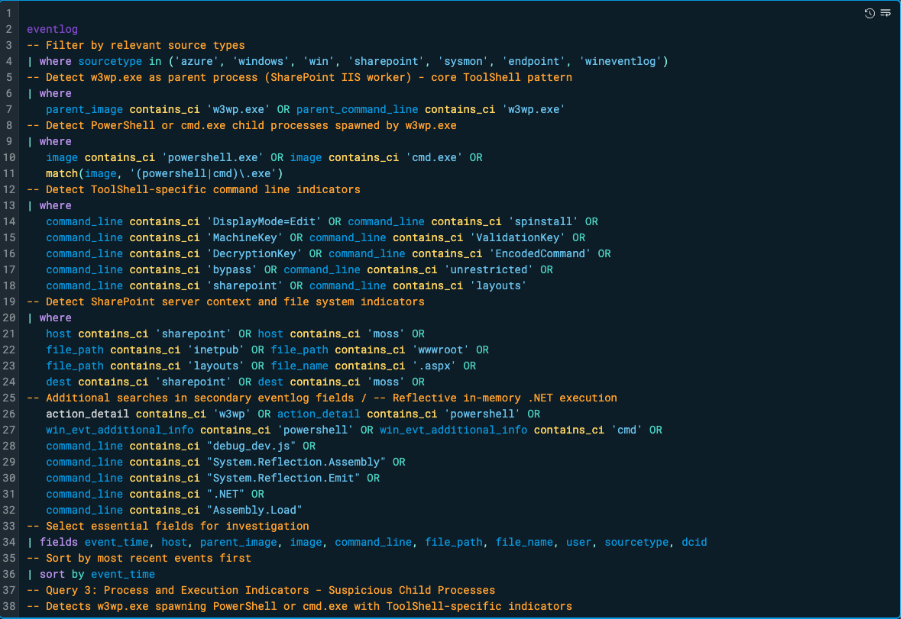
This query is designed to detect malicious post-exploitation behaviour tied to the ToolShell attack chain, specifically focusing on process creation events stemming from SharePoint's IIS worker process w3wp.exe.
It identifies instances where w3wp.exe spawns suspicious child processes like cmd.exe or powershell.exe. This is highly abnormal in legitimate SharePoint operation and typically signals the execution of malicious payloads.
The query tightens focus by inspecting the command_line field for known ToolShell indicators, including:
- Exploit artefacts like DisplayMode=Edit and spinstall
- Key extraction strings (MachineKey, ValidationKey, DecryptionKey)
- Obfuscation techniques (-EncodedCommand, bypass, unrestricted)
- .NET reflection patterns (Assembly.Load, System.Reflection.Emit)
It also ensures the context is SharePoint-specific by looking for hosts or file paths referencing SharePoint, layouts, inetpub, or .aspx files, common in the observed attack path. If any command execution includes those terms and is linked to a w3wp.exe parent, it is a strong indication of ToolShell exploitation in progress.
Query 4: Network Indicators (Traffic to/from Malicious IPs)
![This detection query identifies potential C2 communication related to ToolShell, by monitoring for traffic involving known malicious IPs attributed to the campaign 96.9.125[.]147, 107.191.58[.]76, 104.238.159[.]149.](https://cdn.prod.website-files.com/68228a4fdbfec3b02c9c51b7/6944323428dc7646125729fe_6899fda7d3594dfc6b2756b7_f9c09daf.png)
This detection query identifies potential C2 communication related to ToolShell, by monitoring for traffic involving known malicious IPs attributed to the campaign 96.9.125[.]147, 107.191.58[.]76, 104.238.159[.]149. These IPs were publicly shared in research and incident reports and are consistently used across multiple infection stages.
The query checks both src_ip and dest_ip, as well as src and dest fields, to cover variation in log field naming. The inclusion of action_detail ensures visibility into auxiliary log fields that might contain embedded IP references from network appliance alerts or enriched metadata.
To avoid false positives from irrelevant hits, it requires some evidence of successful or attempted communication. This guarantees that events captured involve active data flow rather than passive background noise.
The host filter restricts results to SharePoint-relevant infrastructure, catching outbound requests from affected systems or inbound scans to known exploitation paths like /ToolPane.aspx. Together, these conditions help analysts flag command-and-control traffic, exfil attempts, or lateral movement signalling active compromise.
The query tightens focus by inspecting network traffic fields for ToolShell related C2 activity, including:
- C2 IPs linked to ToolShell activity (96.9.125.147, 107.191.58.76, 104.238.159.149)
- Traffic direction fields (src, dest, src_ip, dest_ip) including enriched logs (action_detail)
- Evidence of active communication (e.g. bytes_out > 0, status codes, port activity)
- SharePoint-specific hosts or URLs (/ToolPane.aspx) to reduce noise
Mitigation Notes
- Patching: Microsoft released security updates in July 2025 for SharePoint Server 2016, 2019, and SE. ¹⁰
- Key Rotation: Rotate machineKey values (ValidationKey and DecryptionKey) across SharePoint server's post-patch.
Hunting Advice:
- Look for unknown .aspx files in the LAYOUTS directory
- Look for w3wp.exe → cmd.exe → powershell.exe chains
- Trace any outbound traffic from SharePoint servers to known ToolShell IPs
Conclusion
The ToolShell attack chain highlights the ongoing risk of web application vulnerabilities being chained with misconfigurations and credential harvesting. While ToolShell is not a downloadable toolkit, the techniques used in the chain represent a serious threat to SharePoint infrastructure. Defenders should prioritise hunting based on the provided queries and update detections to include signs of ViewState forgery, dropped reconnaissance payloads, and suspicious outbound network activity.
Access the Threat Bulletin in ThreatStream
Anomali ThreatStream users can access a full write-up on ToolShell within the ThreatStream UI, including more detail on CVE-2025-53770, associated threat actors, and recommended queries for detecting ToolShell activity.
Endnotes
- ESET, "ToolShell: An All-You-Can-Eat Buffet of SharePoint Vulnerabilities," WeLiveSecurity, accessed August 5, 2025, published July 22, 2025, https://www.welivesecurity.com/en/eset-research/toolshell-an-all-you-can-eat-buffet-for-threat-actors/.
- Picus Security, "CVE-2025-53770 and ToolShell Exploit Analysis," accessed August 5, 2025, published July 24, 2025, https://www.picussecurity.com/resource/blog/cve-2025-53770-critical-unauthenticated-rce-in-microsoft-sharepoint.
- Cara Lin, "Inside The ToolShell Campaign" FortiGuard Labs, accessed August 5, 2025, published July 26, 2025, https://www.fortinet.com/blog/threat-research/inside-the-toolshell-campaign.
- Microsoft Threat Intelligence, "Disrupting active exploitation of on-premises SharePoint vulnerabilities," Microsoft Security Blog, accessed August 5, 2025, published July 22, 2025, https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/.
- Palo Alto Unit 42, "Active Exploitation of Microsoft SharePoint Vulnerabilities: Threat Brief (Updated July 31)," accessed August 5, 2025, published July 31, 2025, https://unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770/.
- Trend Micro, "Proactive Security Insights for SharePoint Attacks (CVE-2025-53770 and CVE-2025-53771)," accessed August 5, 2025, published July 22, 2025
- Picus Security, "CVE-2025-53770 and ToolShell Exploit Analysis."
- ESET, "ToolShell: An All-You-Can-Eat Buffet."
- Picus Security, "CVE-2025-53770 and ToolShell Exploit Analysis."
- Microsoft, "Customer guidance for SharePoint vulnerability CVE-2025-53770," MSRC, accessed August 5, 2025, published July 19, 2025, https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/#:~:text=How%20to%20protect%20your%20environment,attackers%20from%20exploiting%20this%20vulnerability; “UPDATE: Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities,” CISA, accessed August 6, 2025, published August 6, 2025, https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities.
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



