Introducing Anomali Copilot: Your AI-Powered Security Assistant


We are excited to announce the launch of Anomali Copilot, our suite of generative AI solutions designed to revolutionize the way Security Operations Centers (SOCs) detect, investigate, and respond to incidents and alerts. With Copilot by your side, your SOC will be supercharged in its mission to safeguard your organization from cyber threats.
Security teams and CISOs are being asked to do more with less. While the threats are increasing and getting complex, CISOs face challenges in hiring skilled cybersecurity talent that is efficient in addressing these threats. To add to this, there is tremendous pressure on the security team to cut costs. Automation of the workflows and assisting in addressing the changing threat landscape by leveraging the enhancements in AI provides a new way to address the talent gap, and rising costs while getting easier and better insights into threats.
Cybersecurity professionals and organizations striving to enhance their security posture should be particularly interested in Anomali Copilot. Whether you're a security analyst, threat intelligence professional, or SOC team lead, Anomali Copilot will become your indispensable ally in navigating the complex landscape of cyber threats. With Anomali Copilot's AI-powered assistance, you can amplify your capabilities, increase efficiency, and drive faster and smarter decision-making.
Detect, Investigate, and Respond with Confidence
Anomali Copilot leverages the industry’s largest threat repository (ThreatStream), is built on a secure and private foundation of AI models, and is an integral part of the Anomali Security Operations Platform. By harnessing the power of generative AI, Anomali Copilot addresses the critical challenges faced by security teams, empowering them to streamline their efforts and stay one step ahead of evolving threats.

Streamlined Summarization
With Anomali Copilot, you can say goodbye to information overload. Generative AI excels at processing vast amounts of data, condensing it into key insights and actionable intelligence. From complex threat models to news articles, Anomali Copilot will swiftly summarize the key takeaways, enabling you to focus your efforts on containment and response.
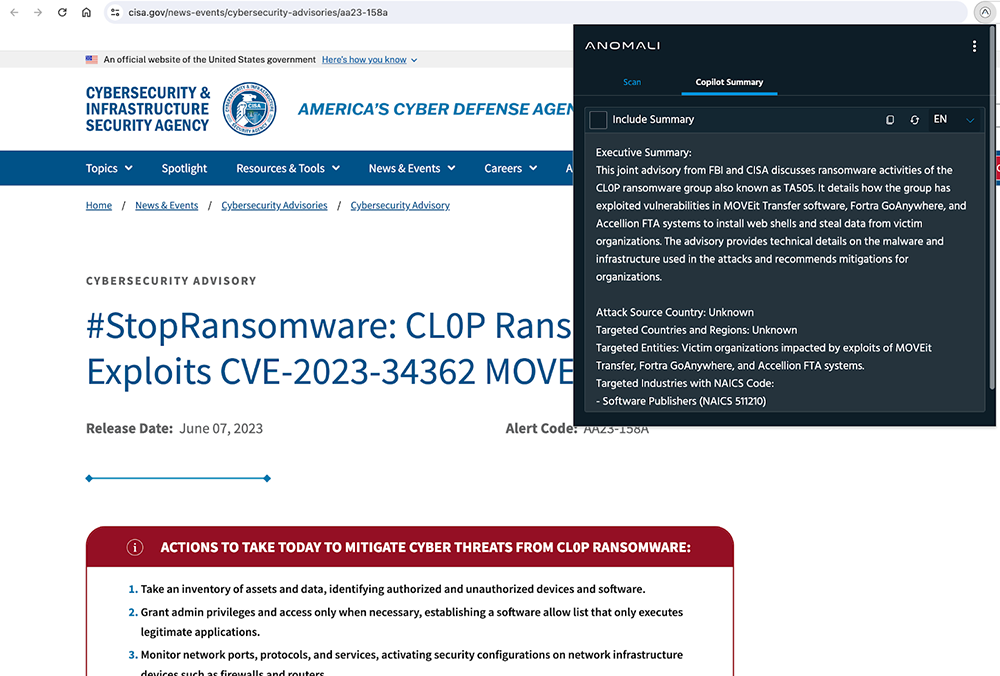
Effortless Natural Language with AQL
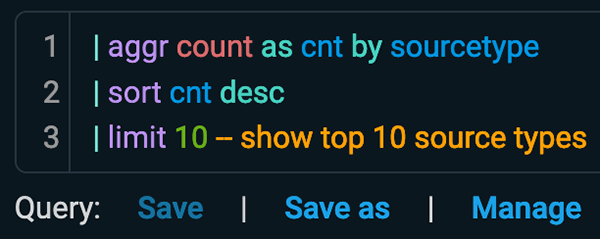
You don't need to be an expert in query languages to gain valuable insights from your data. Anomali Copilot simplifies the process by translating your queries into Anomali Query Language (AQL), allowing you to generate dashboards and alerts in seconds. And if you’re already a ninja in another query language, Anomali Copilot will assist you in translating your detections effortlessly.
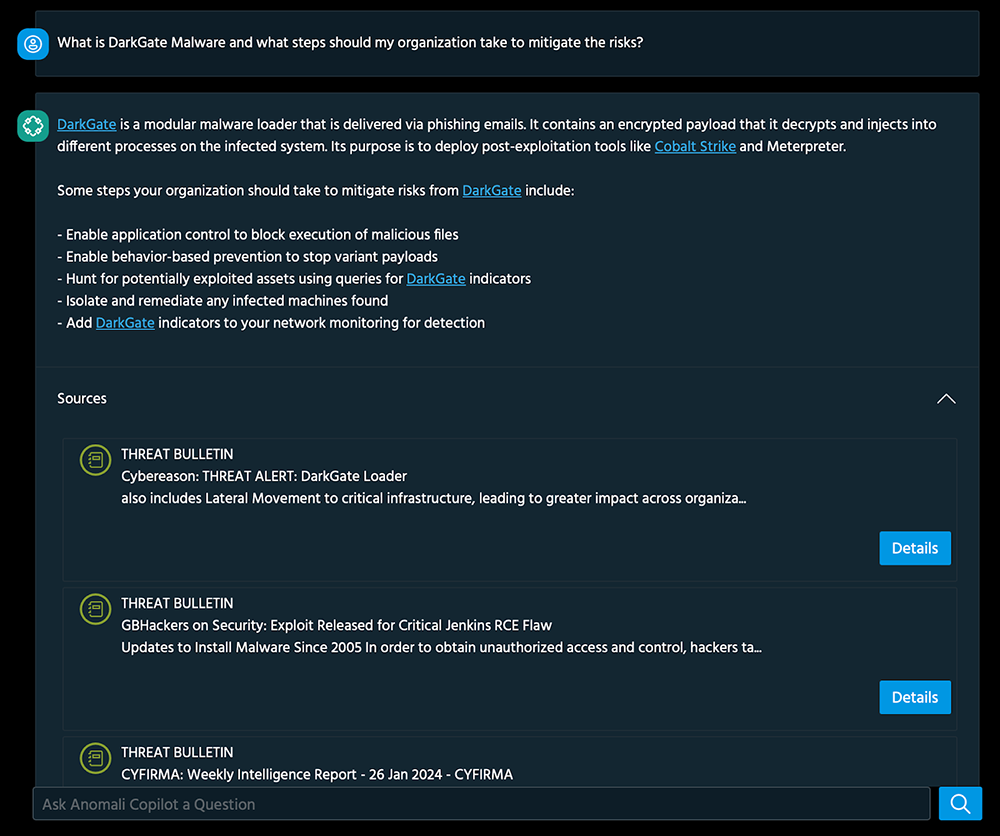
Seamless Chat Experience
Engage in conversations with an expert threat intelligence advisor who understands the unique needs of your organization. Anomali Copilot enables you to use natural language to interact with your threat intelligence, providing you with answers backed by verified sources and searches. Whether you need guidance, best practices, or quick access to information, Anomali Copilot will be by your side.
Empowering MITRE Attack Flow Automation
Anomali takes pride in our collaboration with MITRE concerning Attack Flow analysis. Anomali Copilot leverages this partnership to automatically analyze and create Attack Flows, saving you precious time and resources. By applying these insights to your alerts and detections, you can prevent harmful events before they occur, bolstering your proactive defense strategy.

Anomali Copilot complements and accelerates your SOC Analysts
Anomali Copilot represents another milestone in our commitment to continuously innovate and push boundaries in the field of cybersecurity. By incorporating generative AI technology into our product offering, we aim to equip security teams with advanced tools to combat the ever-evolving threat landscape effectively. Anomali Copilot is just the beginning of our journey to transform the cybersecurity industry, and we invite you to join us as we shape the future together.
Learn more about Anomali Copilot and schedule a personalized demo today!
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



