SIEM
Modern SIEM — Powered by Intelligence & Agentic AI
Optimize or replace traditional SIEM with an intelligence-native approach built for speed, scale, and action.
Legacy SIEMs generate noise, rely on static rules, and struggle to scale. Anomali modernizes SIEM by unifying threat intelligence, always-hot analytics, and agentic AI so teams can enhance existing SIEM investments or transition away from legacy platforms while detecting real threats faster, investigating with full context, and acting with confidence.
Why Traditional SIEMs Falls Short
Alert floods with low signal-to-noise
Static correlation rules that don’t adapt
High ingestion, storage, and compute costs
Slow investigations across fragmented tools
Intelligence treated as an add-on, not a foundation
Anomali reimagines SIEM from the ground up — making intelligence and agentic AI foundational, not an afterthought.
Anomali’s Core SIEM Capabilities
Log Collection & Intelligence Enrichment
Collect and normalize logs across endpoint, network, cloud, and identity sources, enriching events with real-time threat intelligence to enhance or replace SIEM detections.
Correlation with Campaign Context
Correlate telemetry, entities, and campaigns to reduce noise and surface real threats — improving legacy correlation or replacing brittle rules.
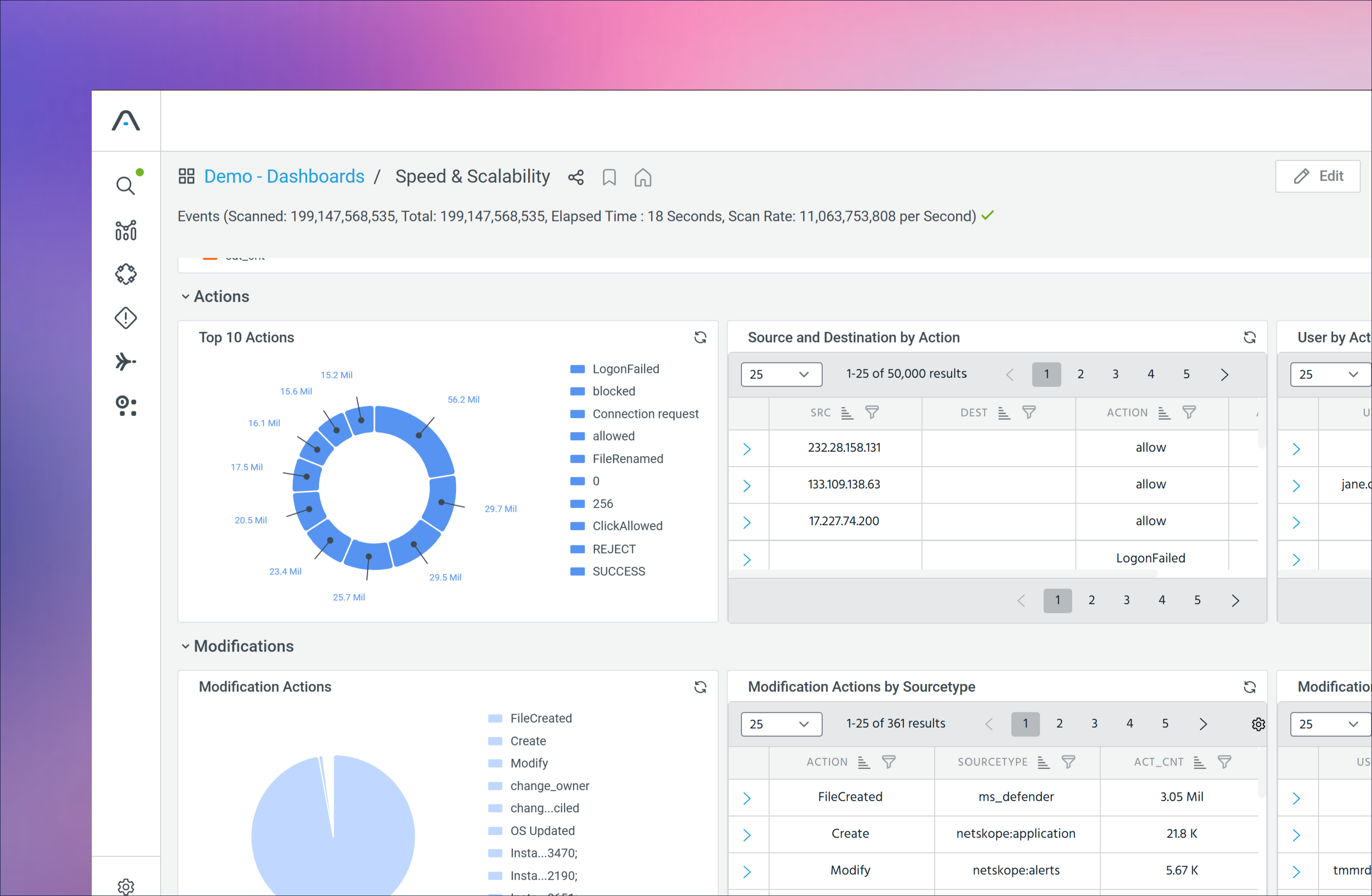
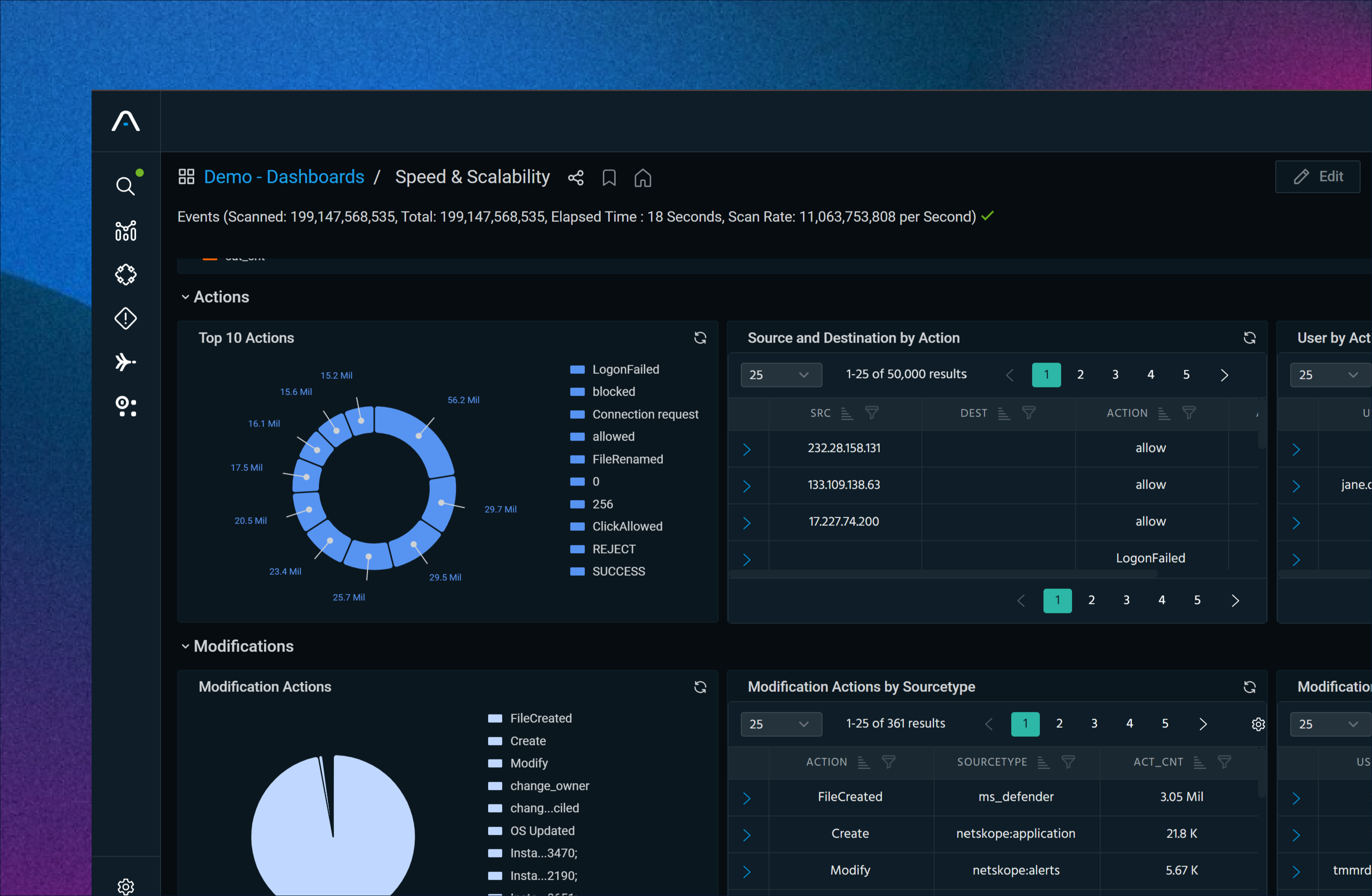
Agentic AI–Guided Investigations
Ask questions, pivot across live and historical data, and get recommended next steps to accelerate investigations across SIEM environments.
Always-Hot Analytics at Scale
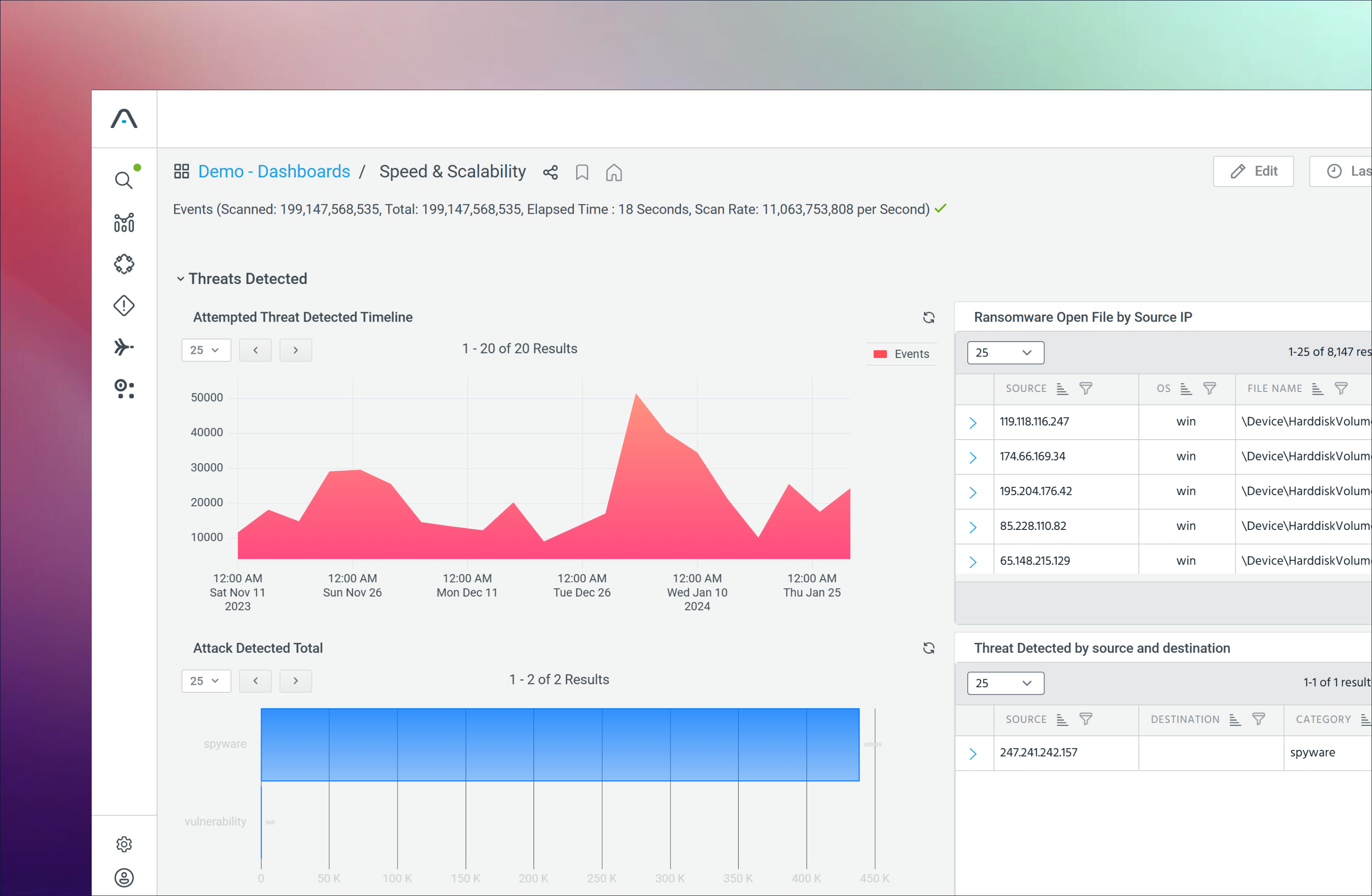
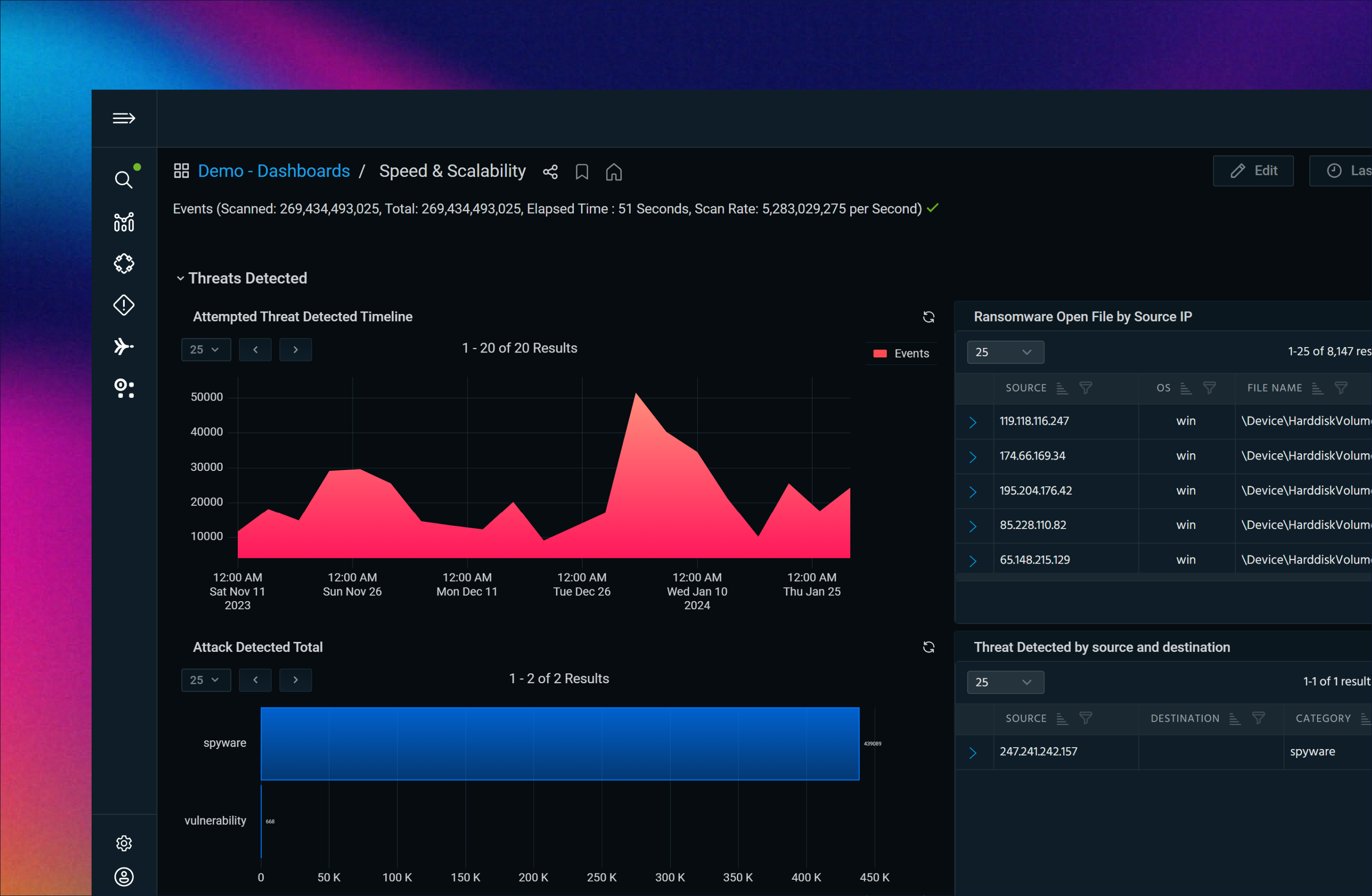
Analyze telemetry in real time with always-hot storage, keeping 7+ years of full-fidelity data instantly searchable while offloading costly SIEM storage and searches.
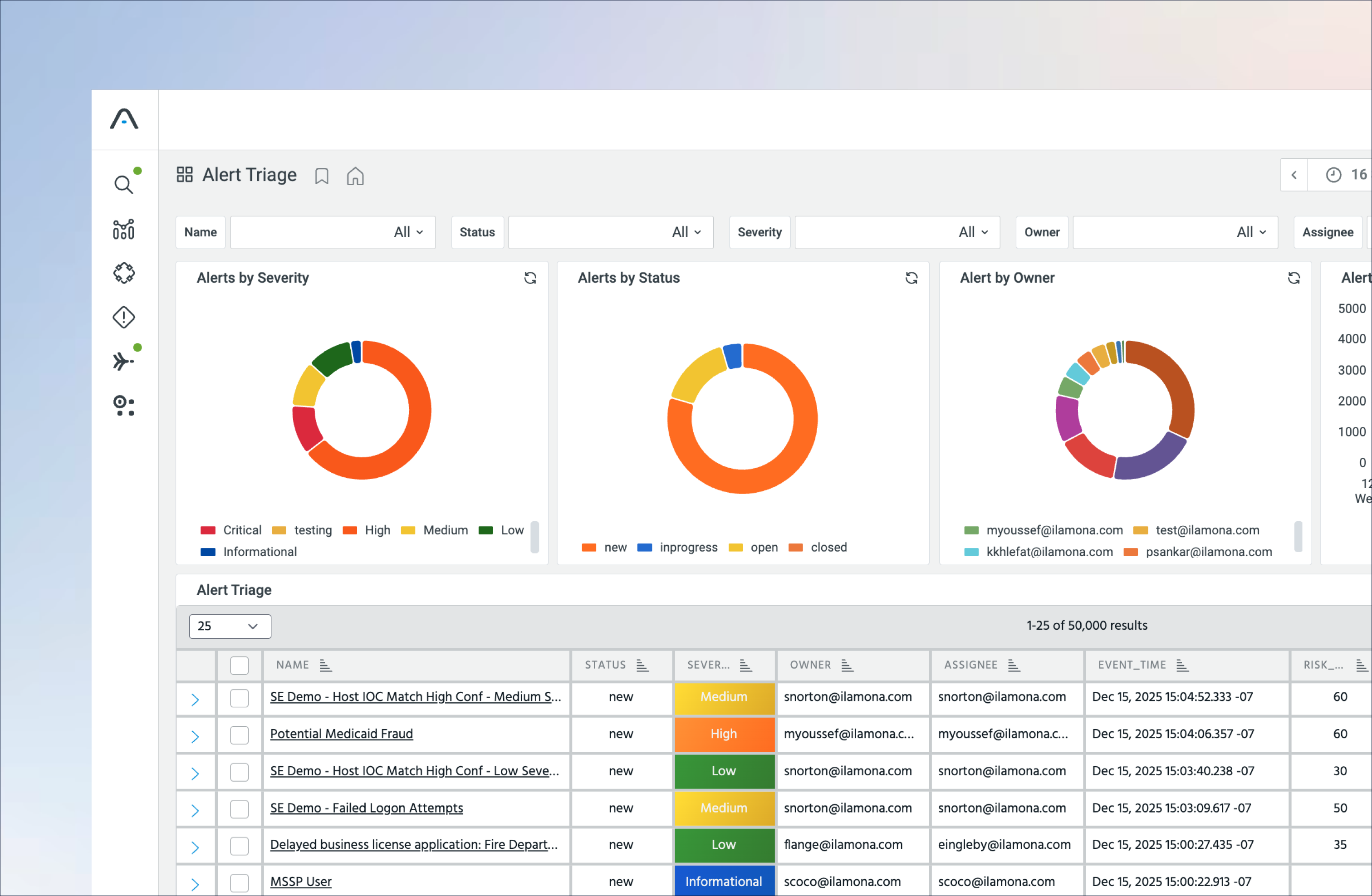
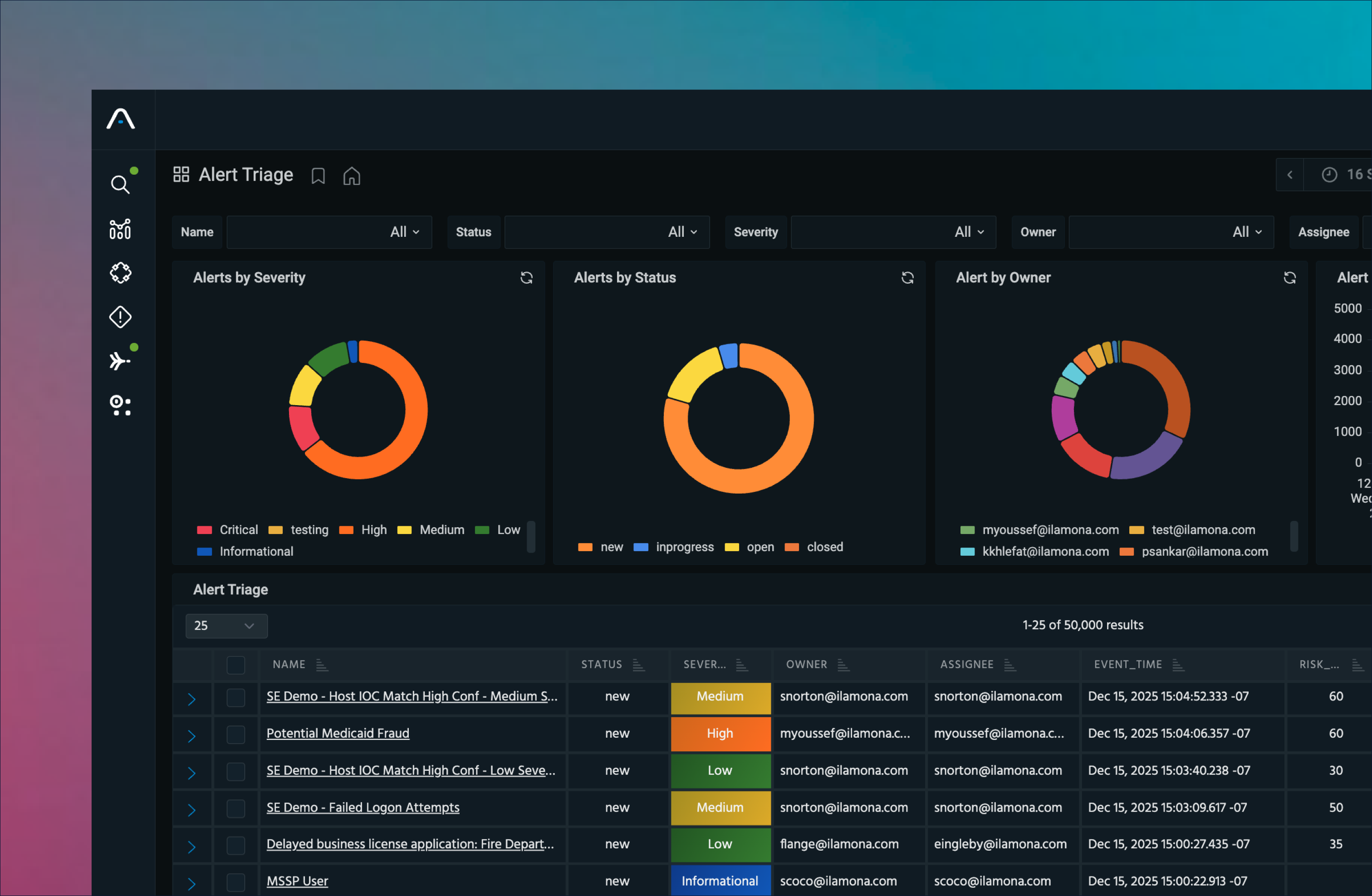
Your Path to SIEM Modernization
Optimize Your Existing SIEM
Enhance current SIEM investments without disruption.
Enrich SIEM alerts with real-time threat intelligence
Reduce false positives with intelligence-led correlation
Offload long-term storage and high-cost searches
Add agentic AI guidance to accelerate investigations
Accelerate analyst workflows without changing core SIEM operations
Replace Legacy SIEM
Move beyond rigid, cost-heavy SIEM platforms.
High-speed analytics on always-hot data
Intelligence-native detection and prioritization
7+ years of full-fidelity, searchable telemetry
AI-guided investigations instead of static rules
Lower cost, higher performance at scale
Unified security data lake
Complete visibility, AI-guided insights, and unified workflows to detect, investigate, and respond at machine speed.
Guide: Discover Why Anomali Outpaces Next-Gen SIEMs
Next-Gen SIEMs may promise advanced capabilities, but many fall short on delivering what SOC teams need most: rapid investigations, unified platforms, and seamless threat intelligence integration. Our exclusive guide, "Anomali vs. Other Next-Gen SIEMs," reveals how Anomali transforms security operations

Latest from Anomali

Modernize SIEM Without Disruption
Whether you’re optimizing an existing SIEM or ready to replace it entirely, Anomali delivers intelligence-led detection, analytics, and guided response — at machine speed.






