Here's How ThreatStream Matches as Notable Events in Splunk
Is it possible to include a threat incident, where a raw event matches a known indicator of compromise, as a Notable Event in Splunk Enterprise Security? Yes!
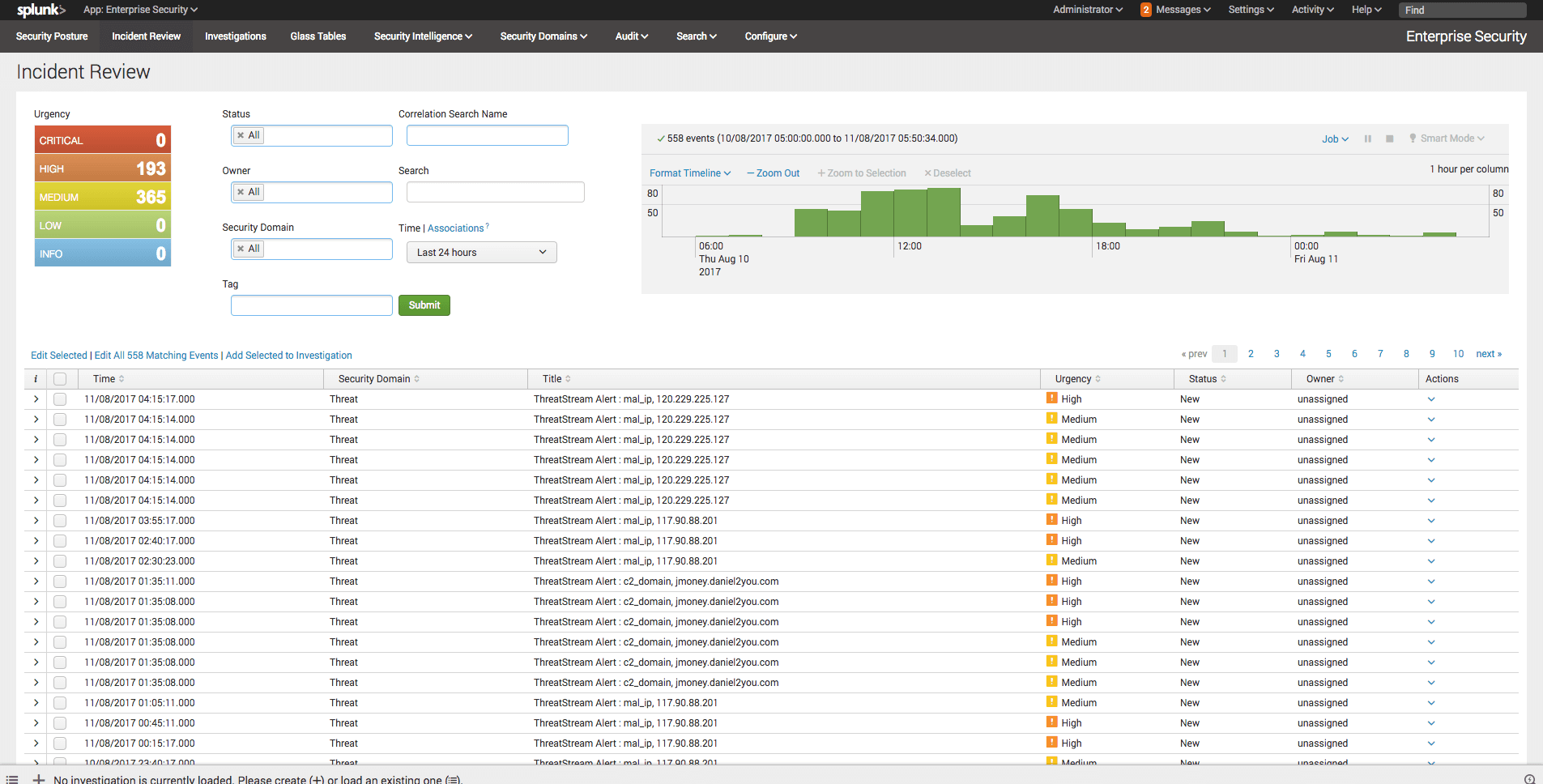

<p>In a previous post <a href="https://www.anomali.com/blog/threatstream-app-for-splunk-introducing-seamless-integration-with-enterpris">I showed how the Anomali ThreatStream Splunk app can integrate with Splunk's own Enterprise Security app</a> to provide analysts with familiar and powerful investigation workflows. Since the post was published I've received a number of emails <a href="https://forum.anomali.com/">from the Anomali community</a> asking; is it possible to include a threat incident, where a raw event matches a known indicator of compromise, as a Notable Event in Splunk Enterprise Security?</p><p>Let me give you an example one of the community posed to me. They have a team of 5 threat analysts whose investigations tended to start in Enterprise Security's Incident Review dashboard. The Notable Events being triggered at the time covered network and endpoint domains, increases in port activity or malware outbreaks for example, however none of these utilised any threat intelligence. The analysts knew that their investigations could be improved if; existing Notable Events utilised threat intelligence and, matched threat intelligence events from the ThreatStream Splunk app also raised Notable Events.</p><p>The first use case can be achieved using the Anomali ThreatStream Splunk app native Adaptive Response functionality <a href="https://www.anomali.com/blog/threatstream-app-for-splunk-introducing-seamless-integration-with-enterpris">described in the previous post</a>. The Adaptive Response action within a Notable Event lets an analyst look up an event field, perhaps an IP address, against millions of known indicators in a single click. The second, takes a little more work, but don't worry it's easy...</p><h2>Notable Event 101</h2><p><img alt="" src="https://cdn.filestackcontent.com/1onmLywpRrmRepo18R1R"/></p><p>Some of you might be wondering what a Notable Event is in the context of Splunk's Enterprise Security. <a href="https://docs.splunk.com/Splexicon:Notableevent">Splunk describe it as</a>; "An event generated by a correlation search as an alert. A notable event includes custom fields to assist in the investigation of the alert conditions and to track event remediation".</p><p>Now I hear you asking; "what is a correlation search?". <a href="https://docs.splunk.com/Splexicon:Correlationsearch">I'll let Splunk answer that one too</a>; "[Correlation search] A special type of scheduled report that lets you detect suspicious events and patterns in your data. You can configure a correlation search to generate a notable event when search results meet specific conditions. You can investigate notable events using the Incident Review dashboard in Splunk Enterprise Security".</p><h2>Building a Correlation Search</h2><p><img alt="" src="https://cdn.filestackcontent.com/z2zCOAsJRPaA9JHTWzDR"/></p><p>A Correlation Search works like any normal search in Splunk. Enterprise Security ships with a number of Notable Events out-of-the-box. You can create new ones inside the Enterprise Security App by navigation to: Configure > Content Management > Create New Content > Correlation Search.</p><p>You can use any search from the Anomali ThreatStream app, or create your own using the rich indicator match data generated by the app. For this example we will simply copy one of the searches from the ThreatStream App that alerts based on high priority indicator matches for APT, C2, or malware indicators with a high-confidence, and convert it to a Correlation Search.</p><p>The search looks like this:</p><p>| `ts_tstats_all` | `ts_lookup_details` | `ts_get_time_offset(_time, ts_date_last)` | where ts_confidence >= 80 AND Age < 31 AND (like(ts_itype, "apt%") OR like(ts_itype, "c2%") OR like(ts_itype, "mal%")) | eval orig_sourcetype=sourcetype</p><p><img alt="" src="https://cdn.filestackcontent.com/GOUejtTcU6w0AtAFLcAz"/></p><p>The following settings can be modified as required, though I've given some defaults you can use to create the Correlation Search:</p><pre> Search Name: ThreatStream High Priority Matches Application Context: ThreatStream UI Dispatch Context: Enterprise Security Description: Confidence>80 , Age < 31 and iType is mal, c2 or apt Mode: Manual Search: | `ts_tstats_all` | `ts_lookup_details` | `ts_get_time_offset(_time, ts_date_last)` | where ts_confidence >= 80 AND Age < 31 AND (like(ts_itype, "apt%") OR like(ts_itype, "c2%") OR like(ts_itype, "mal%")) | eval orig_sourcetype=sourcetype Time Range Earliest: -17m@m Time Range Latest: -12m@m Cron Schedule: */5 * * * * Scheduling: Real-time Schedule Window: 0 Schedule Priority: Default Trigger alert: when number of results > 0 </pre><h2>Add Notable Event Action</h2><p>Before hitting save, select: Add New Response Action > Notable</p><p>Again, I've added some default configuration settings for the Notable Event all of which can be amended if needed:</p><pre> Title: ThreatStream Alert : $ts_itype$, $ts_lookup_key_value$ Description: Trigger when confidence>80 and age<31 and itype in (mal, apt, c2) Security Domain: Threat Severity: high Default Owner: (leave as system default) Default Status: (leave as system default) Drill-down name: contributing events Drill-down search: | datamodel Web Web search | search $ts_lookup_key_value$ Drill-down earliest offset: $info_min_time$ Drill-down latest offset: $info_max_time$</pre><p>All you need to do now is hit "save".</p><p>Note, if you receive a message stating the macro is unaccessible to be executed in search, make sure the Anomali ThreatStream app permissions are set to global. You can do this by navigating to: Manage apps > ThreatStream > Permissions</p><h2>Triage Notable Events</h2><p><img alt="" src="https://cdn.filestackcontent.com/UuwXW7ZiQnohmNNfwMi4"/></p><p>You'll now start to see any high priority matches appear as Notable Events in the Incident Review dashboard (hopefully not too many!).</p><p>The SOC team can now assign these threat incidents using the familiar Enterprise Security workflow.</p><h2>AMA (Ask Me Anything)</h2><p>I'm hosting a technical webinar on the 22nd of August showing how you can operationalise threat intelligence - from early warning to breach investigation - using Anomali and Splunk. We'll cover everything in this post and a whole host more, from detecting the unknown to helping you and your team perform more efficient security investigations. You'll have the chance to ask me <em>anything</em>.</p><p><button>Register / view the webinar here</button></p><p>If you're reading this post far into the future, good news, we're going to record the session and it will still be available using the link above.</p>
FEATURED RESOURCES

Anomali Cyber Watch
Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more
LockBit 5.0 Ransomware Targets Windows, Linux, and VMware ESXi in Active Campaigns. Google Patches Actively Exploited Chrome Zero-Day CVE-2026-2441. Infostealer Targets OpenClaw Configuration Files to Capture Credentials and User Context. And more...



