Weekly Threat Briefing: Cloud Atlas Threat Group Updates Weaponry with Polymorphic Malware
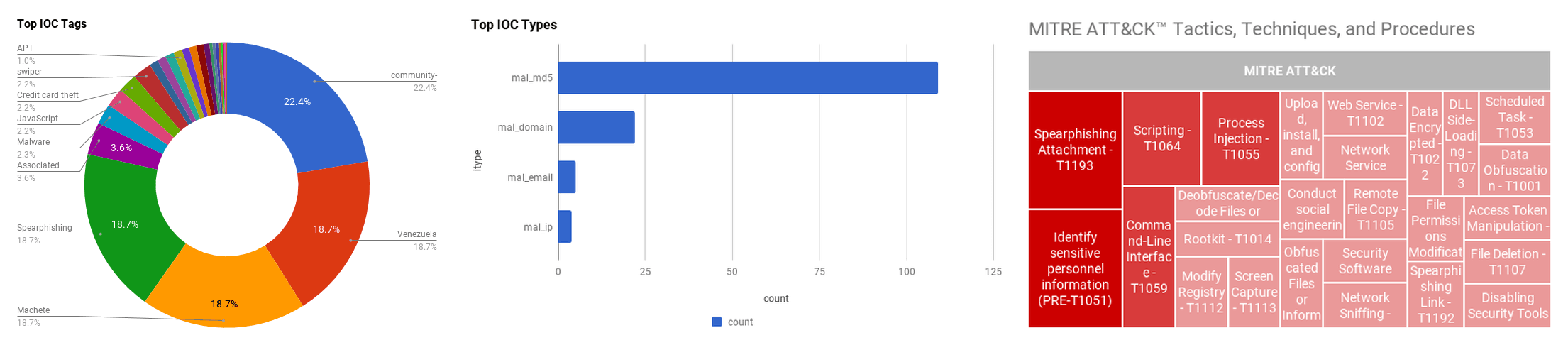

The intelligence in this week’s iteration discuss the following threats: APT, Data breach, Malware, Ransomware, Spearphishing, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Cloud Atlas Threat Group Updates Weaponry with Polymorphic Malware (August 12, 2019)
Cloud Atlas, an Advanced Persistent Threat (APT) group also known as Inception, has updated its attack techniques with new tools that allow it to avoid detection through standard indicators of compromise. Kaspersky researchers have seen Cloud Atlas targeting the international economics and aerospace industries as well as governmental and religious organizations in Russia, as well as Portugal, Romania, Turkey, Ukraine, and other countries. Cloud Atlas is distributed through spearphishing emails and, upon successful infiltration, it will collect system information and log passwords, and then exfiltrate recent files to a command and control server. This application collects initial information about the attacked computer, and executes malicious module “VBShower,” which erases evidence of the presence of malware. The main differentiator in the new infection chain is the fact that a malicious HTML application and the VBShower module are polymorphic, meaning the code in both modules will be new and unique in each case of infection.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Data Obfuscation - T1001
FDNY EMS Notifies More Than 10,000 Patients of Possible Data Breach (August 9, 2019)
The New York City Fire Department has notified over 10,000 people previously treated or transported by its ambulance services that their personal information may have been compromised. According to FDNY, an employee uploaded the information onto their personal hard drive, which was later reported as missing in March 2019. A total of 10,253 patients, 235 of whom are minors, were notified by mail of the possible breach, with all of them having been treated and or transported by EMS between 2011 and 2018. In the notices, the FDNY says the missing hard drive contained names and health information related to the reason for the ambulance call, as well as associated addresses, dates of birth, gender information, insurance information, telephone numbers, and in approximately 3,000 cases, social security numbers. While there is currently no evidence that any of the information stored on the personal device has been accessed, the FDNY is treating the incident as if the information may have been seen by an unauthorized person.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Baldr Credential-Stealing Malware Targets Gamers (August 8, 2019)
Sophos has published a paper covering a trojan called “Baldr” and how it is being used to target the gaming community. The malware package is inadvertently installed by users that believe the application can be used to gain an advantage in a number of online games, when in reality, the application's primary purpose is to acquire credentials the victim might use while the malware was active. The trojan pulls credentials from browsers, FTP clients, instant messaging clients, and some VPN configuration files, and then sends information back to the command and control server. Distribution methods to potential victims include data compression archive files (such as .ACE archives) and Office documents, either hosted on malicious sites or spammed in emails. The malware package was first seen for sale in Russian cybercrime-related forums near the end of January this year, and victims of Baldr include users in Russia, the United States, Singapore, Brazil, India, and Germany.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] Scheduled Task - T1053
Avaya Deskphone: Decade-Old Vulnerability Found in Phone’s Firmware (August 8, 2019)
McAfee researchers revealed the existence of a security vulnerability in a desk phone developed by Avaya, a VOIP solution provider and vendor for business desk phones. According to Avaya, 90 percent of Fortune 500 companies are signed up to its services. A severe remote code execution (RCE) vulnerability (CVE-2009-0692) was present in an open-source component within the firmware of the Avaya 9600 series IP model device. The open-source module was implemented but never patched, leaving these devices vulnerable since the vulnerability was reported in 2009. McAfee says that threat actors could leverage the RCE to hijack a phone's normal operations, extract and steal audio, and "bug" a device for surveillance purposes. A firmware update and disc image have now been published by Avaya.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Process Injection - T1055 | [MITRE ATT&CK] Remote File Copy - T1105 | [MITRE ATT&CK] Command-Line Interface - T1059
Steam Zero-Day Vulnerability Affects Millions of Users (August 8, 2019)
Popular PC gaming platform Steam is vulnerable to a zero-day security vulnerability, experts have warned. According to new findings, approximately 72 million Windows users are at risk of having their systems taken over by a threat actor who could then compromise passwords, install malware, and steal data. The vulnerability was disclosed by security researcher Vasily Kravets, who discovered a privilege escalation vulnerability which could allow an attacker with minimal user permissions to gain the same levels of access as the system administrator. The vulnerability affects the Steam Client Service which launches with full systems privileges on Windows. Proof-of concept-Code (POC) has been made available online. This makes the vulnerability more likely to be attempted to be exploited be threat actors of varying levels of sophistication, making the vulnerability even more serious as potential attackers now know how to exploit it. At the time of this writing, Valve Corporation, the developer behind the Steam platform, have not yet fixed the vulnerability.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] File Permissions Modification - T1222 | [MITRE ATT&CK] Modify Registry - T1112
“Machete” Cyberattack Strikes Venezuela (August 7, 2019)
The cyber-espionage campaign known as "Machete" has been observed stealing sensitive files from the Venezuelan military, according to researchers at ESET. While there are some compromised devices in Ecuador, Colombia, and Nicaragua, the primary focus is Venezuela, with over half of the compromised computers in the campaign belonging to the Venezuelan military. ESET researchers write that until May of this year, more than 50 computers were actively communicating with threat actor-controlled’ command and control server and bleeding gigabytes-worth of data each week. The primary interest of the campaign is Venezuelan military grids, positioning, and navigation routes, and the toolset used by Machete is capable of stealing documents commonly used in the office suite, but also those created using geographic information systems (GIS) software. Machete’s operators use refined spearphishing techniques, targeting specific individuals that have been carefully researched by the group. Although the actors’ identities remain unknown, Machete has long been used in campaigns against Latin American countries, and has been active since 2010.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE PRE-ATT&CK] Upload, install, and configure software/tools (PRE-T1139) | [MITRE ATT&CK] Screen Capture - T1113
FTC Warns of Fake Equifax Settlement Sites (August 7, 2019)
The Federal Trade Commission (FTC) is warning people of scams targeting individuals who mean to claim benefits available under the terms reached with Equifax regarding their 2017 data breach. Equifax, a US-based credit report company,is paying for identity restoration services and up to $125 USD to as many as 147 million potential claimants. The FTC says fake settlement claim sites have begun to appear, with threat actors using claims as an opportunity to access Personally Identifiable Information (PII) and other sensitive data from their victims. The FTC is informing potential claimants that they never have to pay to file a claim to get benefits from the settlement, and to start the eligibility and claims process at the official FTC website.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
APT41: A Dual Espionage and Cyber Crime Operation (August 7, 2019)
FireEye researchers have identified a new Advanced Persistent Threat (APT) group, dubbed APT41. APT41 is believed to be based in China and conducts state-sponsored espionage activity in parallel with financially motivated operations. According to researchers, the group has established and maintained strategic access to organizations in the healthcare, high-tech, and telecommunications sectors.The financially-motivated activities have primarily focused on the video game industry. APT41 leverages more than 46 different malware families and tools to accomplish their missions, including publicly available utilities, malware shared with other Chinese espionage operations, and tools unique to the group.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Rootkit - T1014
Autoloaded Server-Side Swiper (August 6, 2019)
Sucuri published a blog post analyzing server-side swipers and how they differ from commonly reported client-side swipers. In these campaigns, the swiper's JavaScript is injected directly into a compromised site's HTML, which means web scanners can quickly identify their presence. Server-side swipers, however, are injected into the backend code hosted on the site's server. The researchers provide information about an investigation they worked on that leveraged this technique to hide a swiper, and conclude that once threat actors compromise an e-commerce site, they can inject both client-side and server-side credit card stealing malware.
Click here for Anomali recommendation.
MITRE ATT&CK: [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Web Service - T1102
Monzo Customers Must Reset PIN Following Log File Blunder (August 6, 2019)
British bank, Monzo, has notified thousands of its customers that they must reset their PIN immediately following a security issue that could have left accounts compromised. The company contacted 480,000 customers, a fifth of the bank’s users, after they discovered PIN details were being copied and recorded into log files in a different part of the company’s internal systems. According to Monzo, the misconfigured logs were discovered on August 2, 2019 and repaired the next day. By August 5th, the last of the logged data had been deleted. While these systems could have been accessed by unauthorized staff, there is no indication that any criminal activity may have taken place.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
APT28 Intrusion - Corporate IoT (August 5, 2019)
In April 2019, Microsoft Threat Intelligence Center researchers discovered infrastructure of the Russian cyber espionage Advanced Persistent Threat (APT) group APT28 communicating to several external devices. The target was not named in this instance, however, APT28 attacks have largely targeted governmental organizations, as well as companies focused on defense, education, engineering, IT, medicine, and military. Researchers uncovered attempts by the group to compromise popular Internet of Things (IoT) devices (a voice over IP phone, an office printer, and a video decoder) across multiple locations. The actor used these devices to gain initial access to corporate networks. In two of the cases, the passwords for the devices were deployed without changing the default manufacturer’s passwords and in the third instance, the latest security update had not been applied to the device. Once the actor had successfully established access to the network, a simple network scan to look for other insecure devices allowed them to discover and move across the network in search of higher-privileged accounts that would grant access to higher-value data.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Network Sniffing - T1040 | [MITRE ATT&CK] Network Service Scanning - T1046 | [MITRE ATT&CK] Scripting - T1064
New Version of MegaCortex Ransomware Targets Business Disruption (August 5, 2019)
IDefence engineers have identified an updated version of the “MegaCortex” ransomware. MegaCortex is a particularly dangerous ransomware because it has caused significantly expensive incidents across various industries in Europe and North America. The original version of the ransomware had its main payload protected by a custom password that was only available during live infection. This new version can self-execute, and the requirement of a password for installation has been hard-coded in the binary. MegaCortex authors have incorporated some anti-analysis features within the malware module and the functionality to stop a wide range of security products and services, all of which were previously manually executed. The actors behind MegaCortex are believed to be targeting corporations, and those involved with recent activity have not yet been disclosed. Ransom notes request between two and 600 bitcoin, worth approximately $22,715 and $6,814,680USD as of this writing, leading researchers to believe that the actors behind MegaCortex are targeting corporations instead of home users.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Security Software Discovery - T1063 | [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] Process Injection - T1055 | [MITRE ATT&CK] Access Token Manipulation - T1134 | [MITRE ATT&CK] Disabling Security Tools - T1089 | [MITRE ATT&CK] Command-Line Interface - T1059
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
APT28 The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



