Weekly Threat Briefing: Cobalt Threat Group Serves Up SpicyOmelette Fresh Bank Attacks
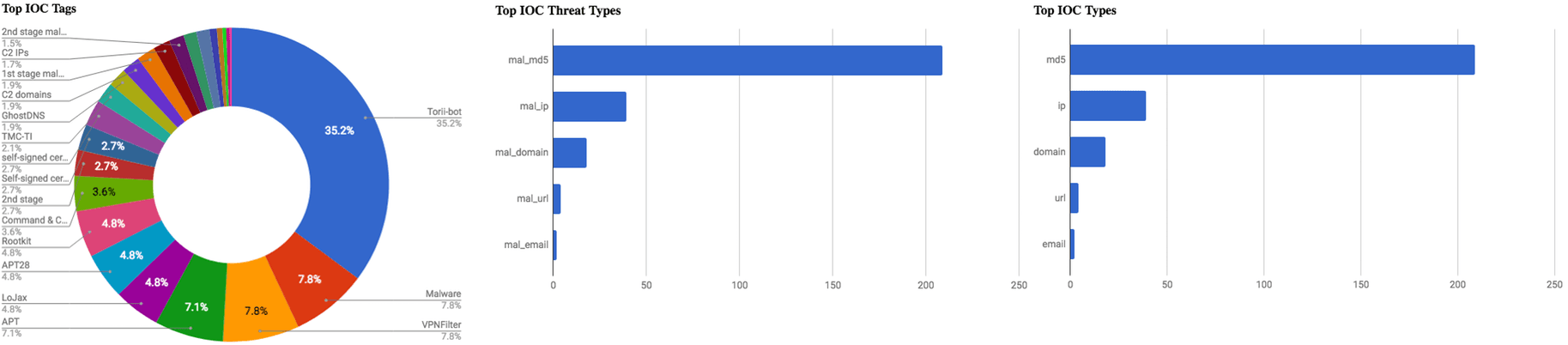

The intelligence in this week’s iteration discuss the following threats: APT28, Botnet, Cobalt Group, Data Breach, DDoS, Ransomware, Vulnerabilities, and Zero day. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
70+ Different Types Of Home Routers (All Together 100,000+) Are Being Hijacked By GhostDNS (September 29, 2018)
Researchers from 360 Netlab have found a DNS Changer campaign, dubbed “GhostDNS,” targeting home routers in Brazil. The attack is believed to have affected over 100,000 router IP addresses, over 70,000 routers, and more than 50,000 domain names in Brazil to steal login credentials. GhostDNS attempts to brute force the password on the target router’s web authentication page to change the default DNS address to the unknown threat actor’s Rogue DNS. The GhostDNS system contains four parts: DNS Changer module, Phishing Web module, Web Admin module, and the Rogue DNS module. The DNS Changer module is the main module of GhostDNS and is responsible for information collection and exploitation. It obtains the passwords for the web authentication of the home routers to change the default DNS address to the Rogue DNS server. The Rogue DNS server has been observed to have targeted at least 52 domains, including Brazilian banks, cloud hosting services, and even a security company named Avira. The targeted domains are resolved to redirect users to a phishing webpage. Victims who access those domains will be sent to malicious phishing sites instead of the intended domain.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
Cobalt Threat Group Serves Up SpicyOmelette Fresh Bank Attacks (September 27, 2018)
The Advanced Persistent Threat (APT) group Cobalt Gang (also called Cobalt Group or Gold Kingswood) targeted high-value financial institutions around the world in a recent campaign. The APT group used phishing emails to lure targets into clicking what appears to be a malicious PDF file that redirects victims to an Amazon Web Services (AWS) URL. Here, the malware “SpicyOmelette” is installed onto the device which harvests information to gain elevated privileges so the APT group can steal financial data and obtain transaction data that can be used for malicious purposes in the future. Cobalt Group has been connected to several campaigns against banks and other financial institutions and is believed to have caused over €1 billion ($1,161,650,000 USD) in damages.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Trusted Developer Utilities (T1127)
Torii Botnet - Not Another Mirai Variant (September 27, 2018)
A new Internet of Things (IoT) botnet has been observed in the wild that appears to differentiate itself from the better-known botnets such as Mirai and QBot. This malware has been dubbed “Torii,” by security researchers. The botnet initially infects a device by brute forcing default credentials or weak passwords. If it gains access, it executes a shell script that attempts to gather device architecture information that is used to download appropriate, subsequent payloads t. The first payload, an ELF file, acts as a dropper for the second stage payload and installs a secondary ELF file. This second stage payload remains persistent in the system by utilising approximately six different methods to ensure the file stays on the device and constantly running all those methods simultaneously. This second-stage payload is the actual bot that connects to the command and control (C2) server to get commands. The bot contains features such as anti-debugging techniques, data exfiltration, and multi-level encryption, amongst others. An infected device can also communicate with the C2 server to execute code or deliver a payload to act as a modular platform. Torii can be difficult to detect on a network because it does not scan for other targets.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Brute Force (T1110) | [MITRE ATT&CK] .bash_profile and .bashrc (T1156) | [MITRE ATT&CK] Launch Daemon (T1160) | [MITRE ATT&CK] Local Job Scheduling (T1168)
Phorpiex Worm Pivots To Infect The Enterprise With GandCrab Ransomware (September 27, 2018)
An unsophisticated botnet malware, dubbed “Phorpiex,” has been observed to be active in a recent campaign that is infecting machines with the “GandCrab” ransomware. This campaign attempts to infect Windows machines through USB drives, removable storage, and malspam. The Phorpiex malware has minimal evasion techniques, is not packed during delivery, and has little subtly when dropping files onto a disk or using hard-coded strings. This campaign attempts to infect compromised machines with GandCrab by targeting machines in corporate networks that operate server-side applications with poor security protocols that can be remotely accessed. It searches for internet-facing Remote Desktop Protocols (RDP) and Virtual Network Computing (VNC) end-points and once it finds one, it launches a brute force attack to compromise weak passwords. Phorpiex uses this endpoint as the initial attack vector to then install the GandCrab malware into the corporate network. The unknown threat actors appear to be targeting organisations within countries that they deem “well-off” such as Australia, Canada, Japan, and the United States.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
APT28 Uses LoJax, First UEFI Rootkit Seen in the Wild (September 27, 2018)
ESET researchers have identified that the Russian Advanced Persistent Threat group “APT28” has added a new malicious tool to their arsenal, a rootkit dubbed “LoJax.” The rootkit targets a machine’s Unified Extensible Firmware Interface (UEFI), which is used by software to connect a machine’s firmware to its operating system and is the first program that runs upon booting a machine. LoJax is the first malware observed to target UEFI specifically, and its objective is to drop malware onto a Windows operating system at startup. At the time of this writing, LoJax is primarily targeting government entities in the Balkans, and Central and Eastern Europe. Furthermore, no distribution has yet been reported.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] System Firmware (T1019)
VPNFilter III: More Tools for the Swiss Army Knife of Malware (September 26, 2018)
The multi-stage, modular framework malware, “VPNFilter,” which was first reported on in May 2018, has been found to have new capabilities such as data filtering and multiple encrypted tunneling capabilities to mask data exfiltration traffic, according to Cisco Talos researchers. VPNFilter has been attributed to the Russian Advanced Persistent Threat (APT) group “APT28.” The estimated amount of devices, typically consisting of routers, infected with VPNFilter is approximately 500,000. The malware has three stages in which malicious activity is conducted that each boast fail-safe measures in the case that one activity fails. The complexity of the malware and versatile components make VPNFilter an information-stealing and destructive malware at the same time. Talos researchers note that the nature of the malware makes it difficult to attribute any one actor.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted (T1022) | [MITRE ATT&CK] Remote System Discovery (T1018) | [MITRE ATT&CK] Network Sniffing (T1040) | [MITRE ATT&CK] Connection Proxy (T1090)
Hide and Seek IoT Botnet Learns New Tricks: Uses ADB over Internet to Exploit Thousands of Android Devices (September 26, 2018)
Bitdefender researchers have discovered that the threat actors behind the Android-targeting Internet of Things (IoT) botnet, “Hide and Seek,” which was first discovered in early 2018, have added new updates. New Hide and Seek samples were found to have a new feature in which it can exploit the Android Debug Bridge (ADB), a command line tool that can be used to communicate with a connected Android device. Researchers note that ADB is typically disabled by default, there are some Android devices that are shipped with the feature enabled. Hide and Seek abuses this feature, which can leave a potential access point to internet-connected devices, to target and infect devices. As of this writing, the Hide and Seek malware is primarily targeting devices in Taiwan, Korea, China, the U.S., and Russia. Researchers believe that this new functionality could allow the botnet to infect another 40,000 devices in addition to the 90,000 Hide and Seek infected in the first few days it was active.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application (T1190)
New CVE-2018-8373 Exploit Spotted in the Wild (September 25, 2018)
A new exploit has been observed in the wild using a use-after-free vulnerability, registered as “CVE-2018-8373.” This vulnerability affects the VBScript engine in newer Windows versions (7 and 10), and the new exploit obtains execution permissions from “Shell.Application” by modifying its SafeMode flag. SafeMode is intended to decide whether a script is safe to run or not, therefore, by altering VBScript’s SafeMode so it is not running, the shellcode in the script can run directly with no intentional authorisation. The exploit does not work on machines that are supported by Microsoft or have patched versions of Internet Explorer. Microsoft has since issued a patch for this vulnerability.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064)
Security Researcher Fined For Hacking Hotel Wi-Fi And Putting Passwords On The Internet (September 25, 2018)
A Chinese security researcher was fined by Singapore authorities after he compromised a hotel’s WiFi system without authorisation and published the passwords for the internal network in a blog post. He brute forced the internet gateway system device, which was using the default password, and subsequently utilised scripts and exploits to gain elevated access on the system. He then found the password for the MySQL database with information on the hotel’s internal network. He did not report these security issues to the hotel, but published a public blog piece about it that contained all the passwords for threat actors to take advantage of and use in a potential future attack. He was arrested by authorities and fined for the breach.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
United Nations WordPress Site Exposes Thousands Of Resumes (September 25, 2018)
One of the United Nations’ (UN) WordPress websites was discovered to be misconfigured in a way that allowed for public access to job applications uploaded to the site since 2016. The misconfiguration left access to a directory index of applications containing CVs that reportedly contain thousands of documents according to researcher, Mohamed Baset, who discovered the leak. Baset reported the misconfiguration to someone at UN security, who stated that the issue pertained to the UN Development Programme (UNDP) and not the UN Secretariat. Following 48 days after reporting the incident to the UN, they had yet to fix the misconfiguration or even respond to the notice.
Click here for Anomali recommendation
Hackers Attack RWE Website Amid Hambach Forest Evictions (September 25, 2018)
German electric utilities company, Rheinisch-Westfälisches Elektrizitätswerk (RWE), suffered a Distributed Denial-of-Service (DDoS) attack following the forcible evictions of protesters from the Hambach Forest. The DDoS attack caused the RWE website to go down on Monday September 24, and as of Tuesday, September 25, it was still completely inaccessible. No other servers were attacked, according to the company. Protesters have been squatting in the forest since the company declared it intended to expand coal mining operations and clear the historic forest. The removals stopped following the death of a journalist in the forest, but had started to continue again on Monday, September 24. The German-speaking sect of the Anonymous hacktivist group, Anonymous Deutsche, released a YouTube video clip claiming the DDoS attack against the company’s main site, and stated it would continue to attack the servers and bring down their web pages until the company stopped expansion into the Hambach forest.
Click here for Anomali recommendation
GandCrab V5 Released With Random Extensions And New HTML Ransom Note (September 25, 2018)
The latest version of the ransomware, “GandCrab,” has been released with several notable changes. Similar to previous versions, this version of GandCrab is distributed via malvertising, redirecting users to sites containing the “Fallout” exploit kit that installs the malware on the victim’s machine. The new changes to this version of GandCrab include using a random five-character extension for encrypted files and contains an HTML ransom note. The malware encrypts files on the local drive, as well as searches for network shares and will encrypt network files on those if there is access to the larger network. The ransom note contains a URL to a Tor site that contains further instructions on how to decrypt files and states the ransom amount of $800 USD paid in DASH (DSH) cryptocurrency. There is currently no free way to decrypt files for free that are encrypted with GandCrab v5.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Scheduled Task (T1053)
SHEIN Breach Exposes Emails, Encrypted Passwords Of 6.42M Customers (September 25, 2018)
Online fashion retailer, SHEIN, suffered a data breach when unknown threat actors were able to access emails and the encrypted passwords of 6.42 million customers. The data breach was reported to occur before August 22, which is when the company became aware that customer information was compromised. The company stated that while emails and passwords were compromised, no credit card information was taken, though SHEIN did not discuss the full extent of the breach. According to the company, their online website is safe to visit and use, and they highly recommend resetting their account passwords.
Click here for Anomali recommendation
macOS Mojave Privacy Bypass Flaw Allows Access To Protected Files (September 24, 2018)
Security researcher, Patrick Wardle, discovered a zero-day vulnerability in the new macOS Mojave update that could allow for unauthenticated applications to bypass authorisation. The new update’s “dark-theme” contains a flaw in their implementation that could allow for a malicious or untrusted application to bypass the new security mechanism and access sensitive details. According to Wardle, this bypass does not work for all of the new update’s privacy protection features, and certain hardware features like the webcam are not affected by this vulnerability. At the writing of this article, Apple has not recognised the vulnerability and a patch has yet to be released.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial. Additional information regarding the threats discussed in this week’s Community Threat Briefing can be found below:
APT28
The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



