Weekly Threat Briefing: Cybercriminals Spoof Major Accounting and Payroll Firms in Tax Season Malware Campaigns
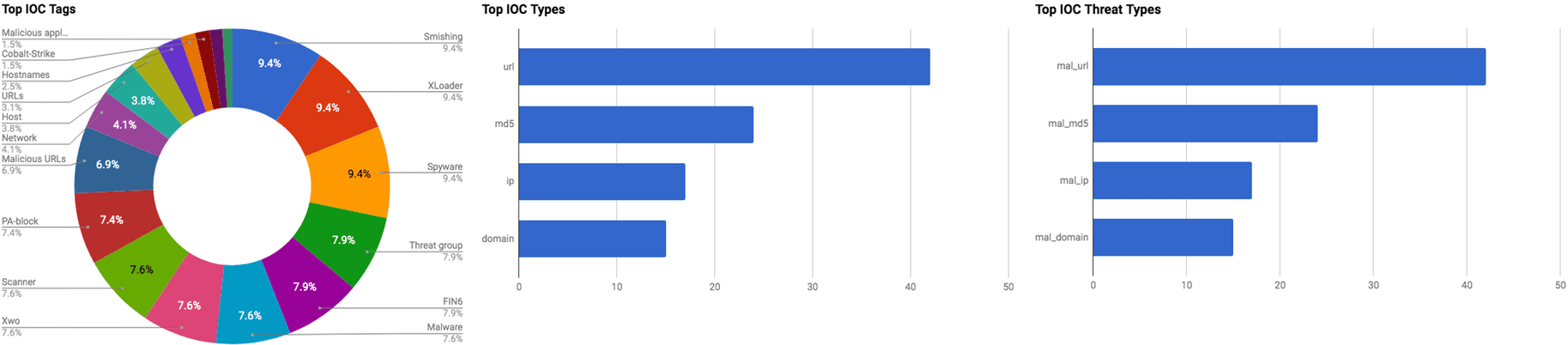

The intelligence in this week’s iteration discuss the following threats: Backdoor, FIN6, LockerGoga, MageCart, Malicious applications, Malspam, Phishing, Ransomware, Ryuk, Trickbot, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Cybercriminals Spoof Major Accounting and Payroll Firms in Tax Season Malware Campaigns (April 8, 2019)
IBM X-Force researchers have identified several tax-themed malspam campaigns that appear to be targeting business and there is the possibility that those business’ customers may become affected as well. The actors behind this campaign are distributing malspam that masquerade as accounting firms, human resource companies, and payroll organizations operating within the US. The impersonated companies include “ADP,” an HR management and services firm, and the payroll provider “Paychex.” The emails attempt to convince recipients into opening a macro-embedded Microsoft Excel document. The heavily obfuscated macro will, if enabled, begin the infection process for the “Trickbot” banking trojan. Trickbot attempts to steal as much data as possible, primarily banking credentials, before sending the information to a Command and Control (C2) server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
Pick-Six: Intercepting a FIN6 Intrusion, an Actor Recently Tied to Ryuk and LockerGoga Ransomware (April 5, 2019)
FireEye researchers responded to an incident and found that the activity was conducted by the financially-motivate threat group “FIN6.” Researchers found that the group compromised an internet-facing system of its unnamed target and then moved laterally inside the network utilizing stolen credentials for Windows’ Remote Desktop Protocol (RDP). FIN6 used two techniques to maintain persistence including PowerShell to execute an encoded command that turned out to be a “Cobalt Strike httpsstager,” which would then download a second shellcode payload configured to download a third, unknown payload. The second technique was the creation of a Windows service to execute encoded PowerShell commands that contained a “Metasploit” reverse HTTP shellcode. The objective of the campaign was to use the compromised servers to distribute malware and host tools. The staged malware was found to be the “LockerGoga” and “Ryuk” ransomware families. Using ransomware is a change of tactics for FIN6 from primarily targeting point-of-sale terminals.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Desktop Protocol (T1076) | [MITRE ATT&CK] Valid Accounts (T1078) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Exfiltration Over Alternative Protocol (T1048)
Backdoor Code Found in Popular Bootstrap-Sass Ruby Library (April 5, 2019)
Software developer, Derek Barnes, discovered a backdoor in the Ruby programming language library, “Bootstrap-Sass.” Barnes noticed the issue when someone removed a version of the library (3.2.0.2) and replaced it with a new version (3.2.0.3) on the Ruby library repository “RubyGems” but not on GitHub. Barnes noticed some embedded code inside Ruby, and the “Ruby on Rails” framework, would load a cookie file and execute its content, and this functionality was confirmed by a security researcher from Bad Packets. On April 4, 2019, Ruby version 3.2.0.4 was released on RubyGems and on GitHub.
Click here for Anomali recommendation
BEC Scam Gang London Blue Evolves Tactics, Targets (April 4, 2019)
The threat group “London Blue,” known primarily for conducting Business Email Compromise (BEC) attacks, has been found to have been conducting a new campaign since January 2019, according to Agari researchers. London Blue is a Nigerian group that has been active since at least 2011 and has members in the U.S., the U.K, and other places around the world; members not located in Nigeria are primarily involved in moving stolen funds to actor-controlled accounts. Agari researchers were able to identify the new campaign via an email sent to the company’s Chief Financial Officer (CFO). The campaign comes in multiple parts. The initial email claims that a correspondent of the recipient forwarded the sender an email to let the sender know if anything else is needed. The follow up email purports that the sender needs the recipient to assist in an acquisition and that a down payment of $86,000 USD via wire transfer is required to complete the acquisition. The email purports that this acquisition has yet to be made public and therefore requests the recipient not to discuss this with anyone else in the office.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204)
Dozens of Credit Card Info Skimming Scripts Infect Thousands of Sites (April 3, 2019)
The threat groups targeting website checkout pages with credit and debit card skimming malware, referred to collectively as Magecart, have developed new skimmers that have not been analyzed before, according to Group-IB researchers. RiskIQ researchers first reported on Magecart activity and found approximately 38 different families of skimming scripts utilized by the 12 groups that comprise Magecart. Group-IB researchers analyzed 15 of the 38 samples, which they call “JS-Sniffer,” and found that approximately 2,440 websites had been infected with a JS-Sniffer skimmer. Threat actors likely compromise the website to install the skimmer via a known vulnerability, through stolen credentials, or through a supply chain attack.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE PRE-ATT&CK] Research relevant vulnerabilities/CVEs (PRE-T1068)
Losing Face: Two More Cases of Third-Party Facebook App Data Exposure (April 3, 2019)
The UpGuard Cyber Risk team has published their findings of two third-party Facebook application datasets that were publicly accessible on the internet. One of the datasets was found originate from the Mexico-based media company, “Coltura Colectiva,” and consisting of 146 gigabytes containing 540 million Facebook records. The records contained information such as account names, comments, Facebook IDs, and likes, amongst others. Researchers also identified a different Facebook-integrated application hosted on a publicly-accessible Amazon S3 bucket called “At the Pool.” The bucket for the At the Pool application contained information consisting of data labeled as fb_books, fb+checkins, fb_events, fb_friends, fb_groups, fb_interests, fb_likes, fb_movies, fb_music, password, fb_photos, among others.
Click here for Anomali recommendation
Xwo – A Python-Based Bot Scanner (April 2, 2019)
A new malware family, dubbed “Xwo,” has been found to be utilized by threat actors by distributing a file called “xwo.exe” from a Command and Control (C2) server. Xwo is a scanner that is capable of sending stolen credentials back to a C2 server. The malware was found to share similarities in code and infrastructure with the “MongoLock” ransomware, although Xwo has no ransomware or exploit capabilities. Once Xwo has infected a machine, it will conduct an HTTP POST request using a User-Agent from a hardcoded list, and then will receive instructions from a C2 domain containing an encoded public network range to scan and gather information on. Xwo will gather data such as default credentials and SVN and Git paths, PhpMyAdmin details, use of default credentials for FTP, Memcached, MongoDB, MySQL, PostgreSQL, and Redis, among other data. Researchers believe that while this malware does not have malicious features such as ransomware or exploit capabilities, the actors behind Xwo will utilize the information gathered in the future.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] System Information Discovery (T1082) | [MITRE ATT&CK] Network Service Scanning (T1046) | [MITRE ATT&CK] Custom Command and Control Protocol (T1094)
Don’t be an April Fool: Update Your Android Mobes, Gizmos to – Hopefully – Pick up Critical Security Fixes (April 2, 2019)
Google has addressed its monthly patch release in two batches for April to address 11 CVE-registered vulnerabilities and 44 flaws. Two of the 11 CVE vulnerabilities, “CVE-2019-2027” and “CVE-2019-2028,” are Remote Code Execution (RCE) vulnerabilities and could be exploited by a threat actor by convincing someone to open a malicious message or video. The other nine CVEs consist of a privilege escalation vulnerability that could be exploited by an installed application, eight located in the Android system, five other privilege escalation flaws, and three that expose information. The nine vulnerabilities are all rated as “high severity.”
Click here for Anomali recommendation
New Version of XLoader That Disguises as Android Apps and an iOS Profile Holds New Links to FakeSpy (April 2, 2019)
A new variant of the “XLoader” spying malware (spyware) has been discovered impersonating a security application for Android devices and uses a malicious iOS profile to target iPhones and iPads, according to Trend Micro researchers. This new variant, called XLoader version 6.0, is being distributed through SMS messages (smishing) purporting to contain a link to a fake Android security application. The actors behind this campaign are hosting the malware on several fake websites, one of which was found to be an impersonation of a legitimate Japanese phone operator’s website. Following a link to an actor-controlled website will prompt the visitor to download the malicious application package (SDK). For iOS users, there is a redirection from the initial website to another that then prompts the user to “install a malicious iOS configuration profile to solve a network issue preventing the site the load.” Installation of the profile will open a fake website masquerading as an Apple ID sign-in page. XLoader is capable of stealing various forms of data from an infected device and uses social media profiles on Twitter to conceal Command and Control (C2) server addresses.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194) | [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Custom Command and Control Protocol (T1094)
Apache Bug Lets Normal Users Gain Root Access Via Scripts (April 2, 2019)
Apache Software Foundation and the OpenSSL project founding member, Mark J. Cox, posted on Twitter the details of a vulnerability, registered as “CVE-2019-0211,” that affects Apache HTTP server versions 2.4.17 to 2.4.38. The vulnerability could allow a user with read and write access to gain root privileges on Unix systems and make it possible to execute arbitrary code via scoreboard manipulation. This vulnerability, as well as two others that are registered as “CVE-2019-0217” and “CVE-2019-0215,” were patched in Apache HTTP Server version 2.4.39. CVE-2019-0217 affects versions 2.4.0 through 2.4.38 could allow a user “with valid credentials to authenticate using another username, bypassing configured access control restrictions.” CVE-2019-0215 affects Apache 2.4.37 and 2.4.38 installations and allows “client supporting Post-Handshake Authentication to bypass configured access control restrictions.” Three less-severe vulnerabilities were also addressed in Apache version 2.4.39 that could be exploited to cause crashes, read-after-free, and normalization inconsistency.
Click here for Anomali recommendation
Government Spyware Hidden in Google Play Store Apps (April 2, 2019)
Security researchers have discovered applications in the Google Play store that contain spying malware (spyware), according to Motherboard reporters. Motherboard believes that the malware is attributable to the Italian government, which reportedly purchased the spyware from a surveillance company called “eSurv.” Security Without Borders researchers claim that the malware, dubbed “Exodus,” has never been previously identified and is attributed to eSurv via a dialect Italian word and the name of a retired footballer, “RINO GATTUSO,” both of which come from the same region where eSurv is based. The Exodus malware works in two stages. The first stage consists of the malware masquerading as an application that receives “promotions and marketing offers from local Italian cell phone providers or that claim to improve the device’s performance.” The first stage will also load the second stage that is responsible for collecting data and sending it back to a Command and Control (C2) server. Exodus is capable of gathering application passwords, browsing history, contacts lists from other applications, text messages, and Wi-fi passwords.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE MOBILE-ATT&CK] Application Discovery (MOB-T1021) | [MITRE MOBILE-ATT&CK] File and Directory Discovery (MOB-T1023) | [MITRE MOBILE-ATT&CK] System Information Discovery (MOB-T1029)
Google Warns of Growing Android Attack Vector: Backdoored SDKs and Pre-Installed Apps (April 1, 2019)
Google has released its “Android Security and Privacy Year in Review 2018” in which the company explained that it has observed an increase in threat actors attempting to install Potentially Harmful Applications (PHAs) via supply chain and pre-installed applications. Actors are also targeting Over The Air (OTA) updates “that bundle legitimate system updates with PHAs.” These vectors are appealing from a threat actor’s point of view because they can target applications that come pre-installed on Android devices which leaves a user vulnerable to potential malicious activity associated with an application the user did not choose to install on his/her phone. A device could come pre-installed with malware, and then could download additional malware via compromised third-party update tools.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Hardware or software supply chain implant (PRE-T1142)
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



