Weekly Threat Briefing: Eight US Cities See Payment Data Card Stolen
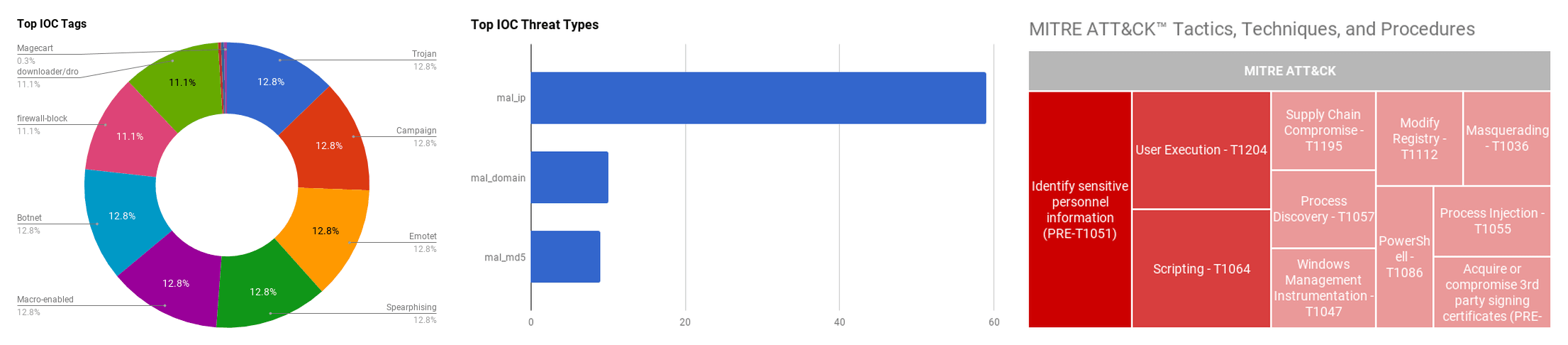

The intelligence in this week’s iteration discuss the following threats: Emotet, Gootkit, Magecart, Payment card theft, Roomleader, and Tortoiseshell. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Forcepoint VPN Client is Vulnerable to Privilege Escalation Attacks (September 20, 2019)
Researchers at SafeBreach discovered that the Forcepoint VPN Client for Windows is affected by a vulnerability that can be exploited to achieve an escalation of privilege, persistence, and defense evasion. The flaw, tracked as “CVE-2019-6145” and described as an unquoted search path issue, affects Forcepoint VPN Client for Windows versions prior to 6.6.1, and now includes a patch. According to SafeBreach, when the client application is launched, a process attempts to run several executable files that do not exist. This would allow a threat actor to place their own malicious executables in these locations that they could run when the Forcepoint application was launched, but only if the actor was local and already had some administrator privileges.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] Process Injection - T1055 | [MITRE ATT&CK] Modify Registry - T1112
Eight US Cities See Payment Data Card Stolen (September 20, 2019)
Gemini Advisory has reported that more than 20,000 payment card records have been harvested from the Click2Gov payment portals of eight U.S. cities. Click2Gov payment portals are used by many U.S. cities to provide residents with a method to pay city bills and utilities online. CentralSquare Technologies, the company that developed Click2Gov, says it has been working closely with customers and investigative resources to resolve the issues and keep systems updated and protected. According to the vendor, the vulnerability in the Click2Gov software has been patched, and the affected cities are attempting to figure out whose data was compromised and send notifications.
Click here for Anomali recommendation
Magecart Skimming Attack Targets Mobile Users of Hotel Chain Booking Websites (September 18, 2019)
A new series of “Magecart” skimming attacks have been discovered, targeting two undisclosed chain hotel booking websites. The websites affected were developed by Roomleader, a Spanish company that helps hotels build booking websites. According to researchers at TrendMicro, the attack is significant, given that the two brands have a combined 180 hotels across 14 countries. The malicious code was injected into the script of Roomleader’s “viewedHotels” module, which is used for saving the viewed hotel information in the visitor’s browser cookies. When the injected code detects the booking page, it will load another JavaScript from the URL where the card skimmer code is located. The skimmer hooks its function when a victim hits “submit” in a payment or booking, and then gathers information including credit card details, email addresses, names, and telephone numbers. Roomleader has been notified by TrendMicro regarding these attacks.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Saudi IT Providers Hit in Cyber Espionage Operation (September 18, 2019)
Symantec has identified a previously unknown threat group, dubbed “Tortoiseshell,” that targeted IT providers as an early stage of a supply chain attack operation. The researchers found the group had targeted 11 IT providers, mostly in Saudi Arabia, since mid 2018, and do not believe the group has ties to previously identified nation-state espionage campaigns or existing cybercrime operations. While the initial attack vector is unknown, at least one of the victims may have been hit via a compromised web server, which was likely used to deploy malware onto the network. Tortoiseshell uses a custom backdoor malware to steal details about the victim machine, including applications, IP configurations, network connections, and system information.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise - T1195
Gootkit Group Left Databases Exposed Online Without Passwords (September 17, 2019)
The threat actors behind the “Gootkit” trojan left their MongoDB databases misconfigured and connected to the internet without a password for about one week in July 2019. This oversight allowed security researcher Bob Diachenko to download the group's data and gain an insight into their operations. Gootkit's main functions are focused on stealing data from browsers, and can extract and exfiltrate data such as browsing history, cookie files, and passwords from multiple browser types. The content found within the two databases was aggregated data from three Gootkit sub-botnets, with a total of 38,653 infected hosts. Approximately 15,000 payment card details were stored in plaintext, as well as online user credentials for a variety of sites, with over two million entries. Diachenko said he found the servers on July 4, noted they were both taken down by July 10, and the servers have not leaked further information. A copy of the data was provided to law enforcement authorities.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
125 New Flaws Found in Routers and NAS Devices from Popular Brands (September 17, 2019)
Security researchers at Independent Security Evaluators have discovered a total of 125 different security vulnerabilities across 13 Small Office Home Office (SOHO) routers and Network Attached Storage (NAS) devices, likely affecting millions. The manufacturers of the affected devices are ASUS and subsidiary Asustor, Buffalo, Drobo, Lenovo, Netgear, QNAP, Seagate, Synology, TerraMaster, Xiaomi, Zioncom, and Zyxel. In the report, the researchers explain that the 13 devices they tested each had at least one web application vulnerability that could allow a threat actor to gain remote shell access or access to the administrative panel of the affected device. The vulnerabilities range from authentication bypass, buffer overflow, Cross-Site Request Forgery (CSRF), Cross-Site Scripting (XSS), file upload path traversal, Operating System Command Injection (OS CMDi), and SQL injection (SQLi) vulnerabilities. Independent Security Evaluators reported each of the discovered vulnerabilities to affected device manufacturers, who have in turn begun the processes of mitigating the vulnerabilities.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting - T1064
Phishing Attack Targets The Guardian's Whistleblowing Site (September 16, 2019)
The Guardian’s anonymous whistleblower submission SecureDrop site was targeted with a phishing page in an attempt to harvest information on sources using the service to correspond with journalists. The phishing site was designed to pull the anonymous sources “codename,” which can then be used to impersonate the source and steal information on the legitimate SecureDrop site. In addition to harvesting the “codenames,” the phishing site advertised a malicious “hide my location” Android mobile app that, once downloaded, could monitor a victim's activity, calls, data, location, and texts. As of this writing, the phishing page has been taken down, however those who’ve installed the malicious app may still have compromised devices.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution - T1204 | [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Emotet Is Back: Botnet Springs Back to Life with New Spam Campaign (September 16, 2019)
The threat intelligence team at MalwareBytes Labs have identified an active spam distribution campaign by threat actors behind the “Emotet” trojan. Emotet’s creators are using sophisticated spearphising functions, including referencing the user by name and hijacking email threads, to target businesses across the globe. The malicious emails lure the victim into opening the attached macro-enabled document, starting the infection process. The PowerShell command triggered by the macro attempts to download Emotet from compromised sites, and once installed, begins spreading laterally to other endpoints on the network. Emotet serves as a delivery vector for more dangerous payloads, such as TrickBot and other ransomware families.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] User Execution - T1204
A New Kind of Certificate Fraud: Executive Impersonation (September 16, 2019)
ReversingLabs have published research on the impersonation of executives through the utilization of digital certificates. The research, based on an unidentified company, provides a timeline reconstruction of an executive impersonation attack used to obtain valid digital certificates. Financially-motivated actors can reduce the chance of their malware being detected by purchasing digital certificates on the black market. Digital signatures assist threat actors in appearing as legitimate entities, and the actors observed in the theft and resale of the certificates have likely targeted more than a dozen undisclosed businesses, according to researchers at ReversingLabs.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Acquire or compromise 3rd party signing certificates (PRE-T1109) | [MITRE ATT&CK] Masquerading - T1036
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



