Weekly Threat Briefing: Email Verification Service Takes Itself Offline After 800 Million Records Get Publicly Exposed
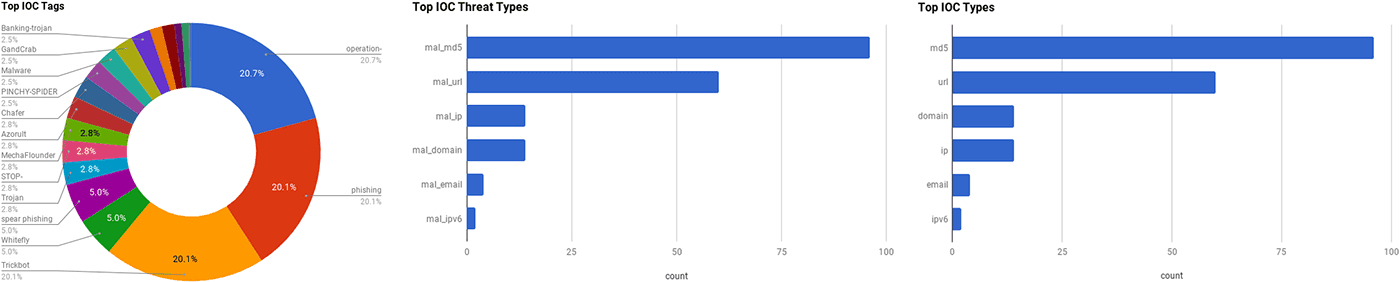

This section listed below contains summaries on various threat intelligence stories that occurred during the past week. The intelligence in this week’s iteration discuss the following threats: APT40, Backdoor, Chafer, Data breach, IRIDIUM, Phishing, Malware, RATs, Ransomware, Vulnerabilities and Whitefly. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Iranian Group Stole 6TBs of data from Citrix (March 11, 2019)
"IRIDIUM," an Iranian-related threat group has been attributed to a cyber espionage campaign against governmental organisations, oil and gas, and technology sectors that resulted in 6 terabytes (TB) of data being stolen from the software company, "Citrix." According to researchers from the company, "Resecurity," the attack occurred around Christmas 2018 and used "proprietary techniques designed to bypass two-factor authentication systems, and methods to access VPNs and single sign-on (SSO)." Information stolen includes e-mail correspondence, files in network shares, and other services used for project management and procurement.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
STOP Ransomware Installing Password Stealing Trojans on Victims (March 10, 2019)
The ransomware family, "STOP," has been seen to have added more capabilities to its most recent variant that now also installs the "AZORult" password-stealing trojan onto the victim's computer to steal account credentials, cryptocurrency wallets, desktop files, amongst others. The ransomware is distributed by a fake software update with a Windows Update screen pop-up appearing, whilst it disables Windows Defender and blocks access to security sites.
Click here for Anomali recommendation
Email Verification Service Takes Itself Offline After 800 Million Records Get Publicly Exposed (March 8, 2019)
Researchers Bob Diachenko and Vinny Troya discovered a MongoDB database containing over 800 million records that was not password-protected but publicly accessible over the internet. The database, owned by email verification company "Verifications.io," contained information including email addresses, names, phone numbers, as well as individuals' city, date of birth, and gender. These records appear to be unique records that have not been leaked from previous breaches, according to the website "HaveIBeenPwned." Researchers contacted the company who then took the database offline on March 7, 2019.
Click here for Anomali recommendation
New SLUB Backdoor Uses GitHub, Communicates via Slack (March 7, 2019)
A watering hole attack has been observed by Trend Micro researchers that exploits a VBScript engine vulnerability, registered as "CVE-2018-8174," to infect users with the backdoor "SLUB." If the user is infected, a multi-stage infection process begins to initially check what antivirus software is running on the machine, and will exit the process if it finds the machine has one of the seven antivirus processes. If not, the downloader tries to exploit the Windows vulnerability, "CVE-2015-1701," to obtain local privilege escalation. The final payload installed is the "SLUB" backdoor which uses both Slack and Github to communicate with the Command and Control (C2) server and receive commands.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068) | [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Drive-by Compromise (T1189)
Op. "Pistacchietto": An Italian Job (March 6, 2019)
Yoroi researchers observed a new campaign, dubbed "Operation Pistacchietto," targeting organisations in Italy with multiple specific malwares. The campaign begins as a fake Java page that requests the user update their Java version to continuing surfing the internet. It provides a link to the "update" that downloads a .bat file, and begins to install malicious code. The malicious script is made up of two parts: the first part fools users into allowing the code administrative privileges, whilst the second part downloads additional components and obtains persistence by using the Windows Task Scheduler. Before the second part of the script downloads additional components, it checks the machine's architecture to download the correct backdoor malware for the machine. The malicious file is able to bypass antivirus detection because the signature changes every time. On top of installing a backdoor specific to the machine's operating system, the malware is able to install the Android Remote Access Trojan (RAT) "AhMyth Android Rat" if it determines it is on an Android mobile.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Scheduled Task (T1053)
Fake Dun & Bradstreet Company Complaint Delivers Trickbot (March 6, 2019)
A phishing email has been observed to be targeting users by masquerading as a company complaint email from "Dun and Bradstreet," a commercial data and analytics organisation, to install the Trickbot banking trojan. The email is from "service@dnbcomplaint.com" which is a typosquatted email address to trick users into opening the email attachment and enable macros in the document. If a user enables macros, the malware will drop several .bat files into the temp folder on a user' machine than renames the "bitsadmin.exe" to "ld0CIC0.exe" to bypass security software detection. The malware then calls out to a specified download site then downloads multiple binary files that create the full Trickbot payload to install on the infected machine.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
Whitefly: Espionage Group has Singapore in Its Sights (March 6, 2019)
A threat group called "Whitefly," has been attributed to the July 2018 breach of the Singaporean company, "SingHealth," and is suspected to continuously be conducting attacks against organisations based in Singapore, according to Symantec researchers. The group uses spear phishing emails as the initial infection vector that contain malicious images or documents that pretend to be relevant to the user's organisation to increase the likelihood of it being opened. If opened, a trojan is downloaded onto the machine to obtain privilege escalation, and then contacts the Command and Control (C2) server. The C2 sends information to download additional malicious tools such as Mimikatz, a custom-made malware to facilitate information stealing, and open-source tool "Termite," which allows Whitefly the ability to conduct more complex actions such as controlling multiple compromised machines at a time. The threat group is believed to be sophisticated because of the ability to maintain presence on a network for a long time before discovery.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Credentials in Files (T1081)
Spotlight on Troldesh Ransomware, aka ‘Shade' (March 6, 2019)
According to researchers from Malwarebytes, the ransomware "Troldesh," (also known as Shade) has had an uptick of infections in the past few months. The malware is typically distributed through phishing emails containing malicious .zip file attachments and targets Windows OS machines. The email frequently states that the attachment should be opened quickly and unzipped. If the target follows those directions, the malicious payload is then downloaded onto the machine from compromised Content Management System (CMS) websites. Troldesh is believed to be of Russian origin because the ransom note is in both Russian and English, and requires the victim to email a given address for further information to retrieve their files back.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
New Google Chrome Zero-Day Vulnerability Found Actively Exploited in the Wild (March 6, 2019)
Clement Lecigne, a security researcher from Google's Threat Analysis Group, discovered a high-severity vulnerability, registered as "CVE-2019-5786," in Google Chrome. This vulnerability could allow a remote threat actor to execute arbitrary code and obtain full control over a vulnerable machine. The vulnerability affects the Chrome web browsing software for the operating systems Microsoft Windows, Apple macOS, and Linux, and it is a use-after-free flaw in the "FileReader" component of Google Chrome. A threat actor could exploit this vulnerability by tricking a user into opening or accessing a specially-crafted webpage, and has been observed to be exploited in the wild.
Click here for Anomali recommendation
PINCHY SPIDER Affiliates Adopt "Big Game Hunting" Tactics to Distribute GandCrab Ransomware (March 6, 2019)
"PINCHY SPIDER," the developers behind the popular ransomware, "GandCrab," have been observed to deploy GandCrab in enterprise networks, utilising lateral movement and toolsets commonly associated with nation-related threat groups, in ransomware deployments known as "big game hunting." According to CrowdStrike, PINCHY SPIDER sells GandCrab to others in criminal forums, and has been consistently updating their ransomware capabilities due to the cybersecurity world developing decryptor tools and mitigations for GandCrab. The threat group was found to be recruiting for people who had remote desktop protocol (RDP) and VNC (Virtual Network Computing) skills, as well as have experience in corporate networking.
Click here for Anomali recommendation
APT40: Examining a China-Nexus Espionage Actor (March 4, 2019)
A new Advanced Persistent Threat (APT) group "APT40," has been announced by researchers from FireEye that are tied to a 2016 campaign that targeted defence, education, engineering, maritime, and transportation infrastructure. The APT group specifically targeted multiple countries including Belgium, Cambodia, Germany, Hong Kong, Malaysia, Norway, Philippines, Saudi Arabia, Switzerland, the United States, and the United Kingdom. APT40 was observed masquerading as an Unmanned Underwater Vehicle (UUV) manufacturer and attempted to illicitly acquire information and technology to help further advance China's naval capabilities. APT40 utilises web server exploitation, registered vulnerabilities, and malicious phishing documents, amongst other tactics, to get into a network and then use a variety of malware to conduct reconnaissance, escalate privileges, establish a foothold, and exfiltrate information back to the APT group.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Web Service (T1102) | [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
New Python-based Payload MechaFlounder Used by Chafer (March 4, 2019)
The threat group, "Chafer," has been observed targeting Turkish government institutions and attempting to install a Python-based trojan, dubbed "MechaFlounder," according Palo Alto Networks researchers. Although the initial infection vector is unclear to researchers, users somehow download a file that initiates the payload to begin installation. MechaFlounder functions as a backdoor that allows the threat group to upload and download files remotely on a machine, as well as run other commands onto an infected machine received via the Command and Control (C2) server. This new malware appears to have been developed with both custom code and code snippets that are available via open-source.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219)
Fileless Banking Trojan Targeting Brazilian Banks Downloads Possible Botnet Capability, Info Stealers (March 4, 2019)
Researchers from Trend Micro observed a fileless malware that installed a banking trojan and information stealer into machines that are related to the Brazilian banks Banco Bradesco, Banco do Brasil, and Sicredi. Once the first trojan infects a machine, it downloads and executes PowerShell codes which drops .LNK files into the Startup folder of the machine and forces the machine to restart. This triggers a lock screen to appear after reboot that looks like a legitimate logon screen but is actually malicious. The objective of the lock screen is to fool the user into entering their system username and password. The malware then sends the obtained credential information to the threat actor's Command and Control (C2) server. A second trojan is then initiated that attempts to open Microsoft Outlook and obtain any email addresses stored in it, although if Outlook is not on the machine, it skips that step. The "RADMIN" malware is also installed onto the machine to obtain administrative privileges and monitor screen activity of the user, as well as spread within the network. The final payload installed is a banking trojan. The largest infections were observed in Brazil and Taiwan.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060)
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



