Weekly Threat Briefing: Emissary Panda Attacks Middle East Government Sharepoint Servers
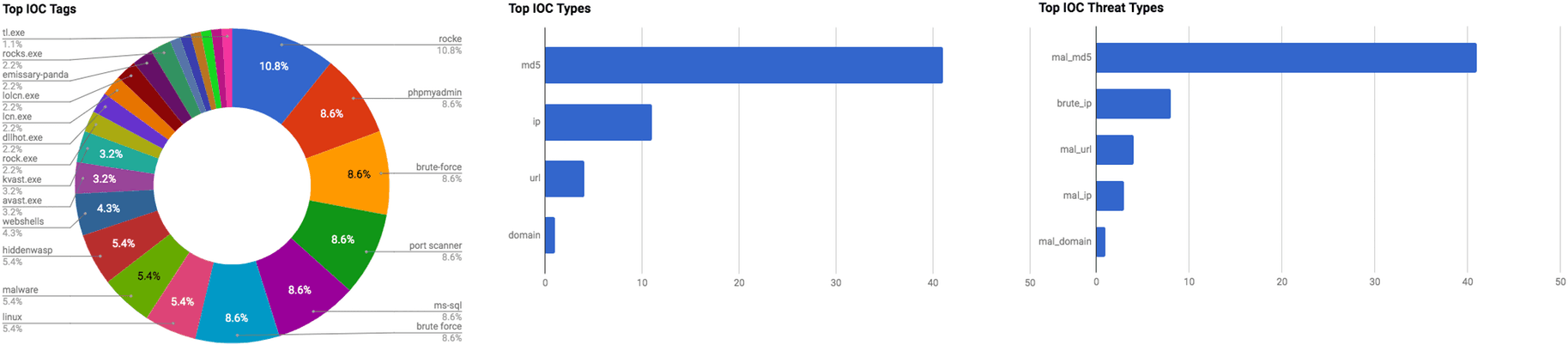

The intelligence in this week's iteration discuss the following threats: APT, Credential theft, Cryptomining, Data theft, Phishing, Payment card theft, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Improper App Check Revives the Synthetic Clicks Issue in macOS Mojave (June 3, 2019)
macOS researcher, Patrick Wardle, has identified an unpatched flaw in the app verification process on macOS Mojave. The vulnerability allows for legacy apps to load and execute unverified code. A trusted application can be changed by executing code on the machine without the users knowledge, allowing for a malicious event. Automatic clicks allows for prompts to be included to reduce user interaction. This is the second reported zero-day issue in two weeks that affects macOS Mojave, with a flaw that allows bypassing Gatekeeper with unsigned code on a network share was discovered by Filippo Cavallarin.
Click here for Anomali recommendation
Infected Cryptocurrency-mining Containers Target Docker Hosts With Exposed APIs, Use Shodan to Find Additional Victims (May 30, 2019)
Trend Micro researchers have identified o Docker containers with exposed APIs that are being used to host threats. Using the internet-scanning tool, Shodan, a script is created to search for hosts with exposed APIs, and once one is found Docker commands are used to create a container for malicious code. A coin-mining binary for Monero cryptocurrency is then called with scripts looking for new hosts to infect. Each host is added to an IP list that Command and Control (C2) servers will iterate through when looking for a new host, looping back to the beginning to begin the process again.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] User Execution (T1204)
Checkers Restaurant Chain Discloses Card Breach (May 30, 2019)
The US-based drive-thru restaurant chain, "Checkers and Rally's," has disclosed that an attack took place on May 29 that impacted over 100 locations. The company said their systems were breached with malware planted on the payments-processing system to steal information from the magnetic stripe of a payment card. The information includes cardholder name, card number, card verification code, and expiration date. Most restaurants were cleaned in April 2019, when the malware was discovered, however the infections date back to September 2016, with most occurring in 2018 and 2019. Checkers is working with federal law enforcement in regards to the attack.
Click here for Anomali recommendation
HiddenWasp Malware Stings Targeted Linux Systems (May 29, 2019)
A new malware named "HiddenWasp" has been found targeting Linux systems, according to Intezer researchers. The malware is a trojan used for targeted remote control of a system utilizing advanced evasion techniques. Due to analysis on the infected systems, it appears as the target systems may already be under control from attackers or another group working aside this threat group. Using a deployment script, trojan and rootkit, the threat actors behind this malware can gain remote access to a target system, and enforcing persistence. As the malware creates a new sftp, the actors can still have access to the system even when HiddenWasp is removed.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Create Account (T1136) | [MITRE ATT&CK] Rootkit (T1014) | [MITRE ATT&CK] Hooking (T1179) | [MITRE PRE-ATT&CK] Host-based hiding techniques (PRE-T1091) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
Crypto Scam Alert: Youtube Videos Promoting "Bitcoin Generator" Really Pushing Malware (May 29, 2019)
A new cryptomining campaign has been discovered by a researcher called "Frost," that uses Youtube to persuade users to download a "Bitcoin generator." Once the user clicks on the download link, they are directed to download and run a Setup.exe file, which will infect their machine with the "Qulab" trojan. The Qulab Trojan attempts to steal data from user's browser including history, cookies and social media credentials, saved credentials, including .txt, .mafiles and .wallet files. Clipboard data is also stolen by Qulab, which can contain cryptocurrency addresses, the attacker can then change the victims public key, sending their crypto to the attackers wallet instead.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204)
The Nansh0u Campaign - Hackers Arsenal Grows Stronger (May 29, 2019)
Guardicore Labs have been monitoring a Chinese-based attack that seeks to infect MS-SQL and PHPMyAdmin servers to drop a crypto-miner. The attacks appear to have begun around February with 20 versions of payload being utilized to date. The targets of the campaign include IT, healthcare, media and telecommunications with over 50,000 infected servers. The MS-SQL attacks were comprised of three components - a port scanner, MS-SQL brute-force tool, and a remote code executor. This attack uses cyber weapons that would previously be used in nation state attacks, however they are becoming more accessible to non-state actors.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Authentication attempt (PRE-T1158) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Brute Force (T1110) | [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068) | [MITRE ATT&CK] Obfuscated Files or Information (T1027)
Emissary Panda Attacks Middle East Government Sharepoint Servers (May 28, 2019)
Unit 42 researchers, has observed an attack by Emissary Panda (APT27) targeting two Middle Eastern government organizations. The attack took place on April 1 and April 16, 2019, with the group exploiting a remote code execution vulnerability in Microsoft Sharepoint, CVE-2019-0604. This vulnerability allowed for the actors to remotely upload three webshells which included backdoors, vulnerability scanners and tools to steal credentials. Although Microsoft patched the vulnerability, attackers were able to quickly abuse it before the victims' systems had been updated. Once Emissary Panda gained access through the Sharepoint vulnerability, they were able to exploit another vulnerability, CVE-2017-0144 (EternalBlue) to pivot to other systems. The affected governments have not been named.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Shell (T1100) | [MITRE ATT&CK] Scripting (T1064) | [MITRE PRE-ATT&CK] Upload, install, and configure software/tools (PRE-T1139) | [MITRE ATT&CK] DLL Side-Loading (T1073)
DuckDuckGo Android Browser Vulnerable to URL Spoofing Attacks (May 28, 2019)
A security flaw has been identified by security researcher, Dhiraj Mishra, on the Android mobile browser version of the "DuckDuckGo" search engine. The vulnerability, registered as "CVE-2019-12329," can allow for threat actors to spoof the address bar. By changing the URL in the address bar, attackers can trick users into believing they are on a trusted website, while being redirected to malicious websites, such as phishing sites, or a website containing malware. These attacks are particularly dangerous as they are much more difficult for users to detect.
Click here for Anomali recommendation
Contain Yourself, Docker: Race-condition Bug Puts Host Machines at Risk... Sometimes, Ish (May 28, 2019)
A vulnerability in all versions of Docker, a widely used platform for deploying applications, has been discovered by Aleksa Sarai. The vulnerability can potentially be exploited to read and write on host machine, bypass container security protections and execute code. Exploiting this vulnerability, can allow a threat actor to alter the host file system when a host administrator is copying data in or out of a docker container. Using a symlink, term for a file that contains another reference to another file or directory, the host file system paths could be altered that could enable the host file system to also be altered. The research suggests that changes to docker are almost impossible, with less ideal fixes such as such as pausing containers during file operations being the suggested fix.
Click here for Anomali recommendation
New Rocke Variant Ready to Box Any Mining Challengers (May 28, 2019)
A malware threat group specializing in cryptomining called, "Rocke", has been observed by FortiGuard Labs researchers to have added new features the cryptomining malware. Hosted on PasteBin, the malware can be installed on systems through a number of means including automated internet vulnerability scanning, service login brute-forcing and exploitations. Using hook libraries, the malware is able to stay on the system longer, as it is more difficult for users to detect and remove. Recently, threat actors have been targeting systems running Jenkins by attempting to exploit the vulnerabilities CVE-2018-1000861 and CVE-2019-1003000.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | Cron Job/Scheduled Tasks | [MITRE ATT&CK] Data Compressed (T1002) | [MITRE ATT&CK] New Service (T1050) | [MITRE ATT&CK] Hooking (T1179) | [MITRE ATT&CK] Brute Force (T1110) | [MITRE ATT&CK] Connection Proxy (T1090)
Phishing Email Pretends to be Office 365 'File Deletion' Alerts (May 28, 2019)
A new phishing campaign has been launched pretending to be from Microsoft Office 365. The actors behind this campaign distributes emails claiming that an unusual amount of files have been deleted on their account, sending a "medium-severity" alert. A link titled "View Alert Details" brings the user to a fake Microsoft login page.The credentials entered into the site were observed being sent to an Azure website controlled by the actors who may save them for future malicious purposes or offer them for purchase on underground forums.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Spearphishing Link (T1192)
Nearly One Million Still Vulnerable to "Wormable" BlueKeep RDP Flaw (May 28, 2019)
Two weeks after Microsoft released a security patch for a wormable, remote code execution vulnerability, registered as "CVE-2019-0708," nearly one million systems are still unpatched. The vulnerability, named "BlueKeep," could allow for a remote attacker to gain access to a target computer by sending requests to the Remote Desktop Service via the Remote Desktop Protocol, with the potential for an attack similar to the global ransomware campaigns, WannaCry and NotPetya. During Microsoft's May 2019 Patch Tuesday, a patch was released to address the vulnerability, however a scan performed by Robert Graham revealed almost one million systems have not deployed the patch.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Desktop Protocol (T1076)
Return of the City of Cron Malware Infections on Joomla and WordPress (May 27, 2019)
A persistent malware infection has been found in a shared hosting environment by Sucuri. The malware operates by detecting if the website is Joomla or WordPress by their directory structures, which it uses to determine which method to utilize in infecting the files. Using a backdoor cron job, the malware is still able to reinfect files, even after they have been cleaned. The files are stored in the /tmp directory which makes it harder to detect malicious files, as it is rarely scanned.
Click here for Anomali recommendation
MITRE ATT&CK: Cron Job/Scheduled Tasks
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



