
The intelligence in this week’s iteration discuss the following threats: APT, Banking malware, Cryptocurrency miner, Data leak, Exploit kit, Malvertising, Ransomware, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Georgia Court System Hit in Ransomware Attack (July 1, 2019)
The U.S. State of Georgia Court Systems have been targeted with a ransomware attack, resulting in IT systems being taken offline. While it remains unclear how many systems were compromised, a spokesman for the Administrative Office of the Courts has confirmed that not all court systems have been affected. Officials stressed that they do not store private information that is not a public document in these systems, and that no social security numbers or other such sensitive information would be compromised. As a precaution, the network was taken offline while trying to determine the attack’s extent.
Click here for Anomali recommendation
Europol coordinates arrests of six in $28 million crypto scam (June 29, 2019)
Europol coordinated the arrest of five men and one woman accused of running a cryptocurrency ring that stole at least $28 million USD in Bitcoin. The suspects were arrested in the United Kingdom and the Netherlands, and the theft is believed to have affected at least 4,000 victims in 12 countries. Europol released a cybercrime report that notes the widening trouble law enforcement agencies face with cryptocurrency scams and ransomware, and Europol intends to continue treating these types of investigations very seriously. The Europol report notes that there is a need for “greater and enhanced cooperation between international law enforcement agencies,” and that “we do not make the difference between online and real-world investigations. For us, they are interlinked. Every investigation nowadays has a cyber component.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Service - T1102 | [MITRE ATT&CK] Spearphishing Link - T1192
Golang Spreader Used in Cryptocurrency-Mining Malware Campaign (June 28, 2019)
Trend Micro researchers have identified a Golang-based spreader being used in a campaign that drops a cryptocurrency miner payload. Golang is an open-source programming language that has been recently associated with malware activity. The spreader used in this campaign scans for machines running vulnerable vulnerable web applications, particularly ThinkPHP and Drupal to propagate. Cybercriminals are possibly turning to Golang to make the analysis of their malware more difficult, as it’s not as commonly used for malware as compared to other languages. Trend Micro has been detecting the use of the spreader since May 2019 and observed it again in a campaign in June 2019.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Disabling Security Tools - T1089 | [MITRE ATT&CK] Clear Command History - T1146 | [MITRE ATT&CK] Process Discovery - T1057
Client Data at Ford, TD Bank Exposed by Attunity (June 28, 2019)
Attunity, a data integration and data management company, left client data files exposed on the internet, according to a June 27 report from UpGuard.. The security issue stems from misconfiguration of three Amazon S3 buckets used by Attunity, which the company has now secured. The incident involves two high-profile impacted clients, Ford and TD Bank, with exposed data related to internal business functions, as well as information technology architecture and solutions related to Attunity. Researchers at UpGuard stated that while the total size of the database is uncertain, “The researcher downloaded a sample of about a terabyte in size, including 750 gigabytes of compressed email backups. Backups of employees’ OneDrive accounts were also present and spanned the wide range of information that employees need to perform their jobs: email correspondence, system passwords, sales and marketing contact information, project specifications, and more.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
New Dridex Variant Evading Traditional Antivirus (June 28, 2019)
A new variant of “Dridex” malware has been discovered, according to an eSentire Threat Intelligence report from June 27, 2019. Dridex malware has been known to target Windows users who open email attachments in Word or Excel, causing macros to activate and download Dridex, infecting the computer and opening the victim to banking theft. The new variation that has been identified allows the macros to respond to different levels of employee engagement. The eSentire report explains that as of the morning of June 27, only 16 antivirus solutions of about 60 detected the suspicious behavior. Researchers believe that actors behind this variant of Dridex will continue to change up indicators throughout the current campaign, given the “tendency to utilize randomly generated variables and URL directories.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Service - T1102 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
New Highly-Critical Cisco Nexus Security Flaws - Require Urgent Update (June 27, 2019)
Admins using Cisco's automation software or Nexus kit are being urged by Cisco to patch core network-management software. The two security bugs are considered highly critical, and affect Cisco’s Data Center Network Manager (DCNM) software in its web-based management interface. The first flaw, “CVE-2019-1619,” is an authentication bypass that allows an attacker to take a valid session cookie without knowing the admin user password. The second vulnerability, “CVE-2019-1620,” would allow anyone on the internet to upload malicious files on the DCNM filesystem on affected devices. According to Cisco, the vulnerability is due to incorrect permission settings, which could be exploited to gain root privileges on the affected device.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Service - T1102 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Remote Access Tools - T1219
Iranian Threat Actor “APT33” Targets Saudi Organizations (June 26, 2019)
Inskit and Recorded Futures researchers suspect that Iranian state-sponsored threat group “APT33,” also known as “Elfin,” or a closely aligned threat actor, continue to conduct and prepare for a widespread cyberespionage campaign. Since March 28, 2019, over 1,200 domains have been used to target mainly Saudi Arabian organizations across a variety of industries. There appears to be a strong emphasis on using commodity malware, which is an attractive option for nation-state threat actors who wish to hinder attribution efforts. Historically, APT33 targeting has focused on the aerospace and defense industries, as well as the oil and gas industry, with a strong focus on companies based in Saudi Arabia. According to the Recorded Futures researchers, a preliminary analysis identified 1,252 unique, correlated domains likely administered by the same APT33 attackers behind an APT33 campaign documented in March 2019 by Symantec.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Exploitation for Privilege Escalation - T1068 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Network Sniffing - T1040 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] User Execution - T1204
Malvertising Campaign by “ShadowGate” Utilizes GreenFlash Sundown EK (June 26, 2019)
A recent global malvertising campaign has been associated with the cybercriminal group “ShadowGate” utilizing the “GreenFlash Sundown” exploit kit. ShadowGate is known for their elusive and stealthy tactics, and have not been associated with a large scale incident since 2016. The campaign is responsible for pushing “SEON” ransomware, a cryptominer, and the “Pony” credential-stealer. Users that navigate to a popular online video conversion site, OnlineVideoConverter<.>com, are redirected to the exploit kit if they interacted with a fake GIF image that contains the launching piece of JavaScript. A careful pre-check process using PowerShell identifies whether or not the environment is ideal before deciding to drop the payload. Based on telemetry data from Malwarebytes, this campaign is active in North America and Europe, which is new territory for the ShadowGate group, having been previously only observed in East Asian countries.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell - T1086 | [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
BlueStacks Flaw Lets Attackers Remotely Control Android Emulator (June 25, 2019)
A DNS Rebinding vulnerability was identified in BlueStacks Android Emulator by security researcher Nick Cano in April 2019. BlueStacks Android Emulator is the most widely used Android emulator globally, allowing Windows PC and Mac OS users to run Android applications. The DNS rebinding flaw allowed attackers to gain access to the emulator’s interprocess communications (IPC) functions. DNS Rebinding takes advantage of the ability to set low TTLs on DNS responses so that the attacker can constantly rotate the mapped IPs, allowing the script to bypass Same Origin Policy (SOP) and access the local host. The vulnerability was discovered and reported to BlueStacks, and was fixed in the newest release of BlueStacks 4.90.0.1046 on May 27th, 2019.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools - T1219 | [MITRE ATT&CK] Web Service - T1102 | [MITRE ATT&CK] Exfiltration Over Alternative Protocol - T1048 | [MITRE ATT&CK] System Information Discovery - T1082
Riltok Mobile Banking Trojan Identified by Kaspersky Lab (June 25, 2019)
Kaspersky Lab researchers have identified a new variant of the Riltok mobile banking trojan that has been in operation since March 2018. The actors distributing Riltok have primarily focused on targeting individuals that reside in Russia, but versions for markets in France, Italy, Ukraine, and the United Kingdom have been detected in 2019. The trojan is distributed via SMS with a malicious link pointing to a fake website that simulates an ad-free version of one of the following popular mobile apps: Avito, Youla, Gumtree, Leboncoin, or Subito. During installation of the imitated app, Riltok asks the user for permission to use special features within the AccessibilityService, which then allows Riltok to prompt users with fake payment screens requesting bank card information. Once Riltok performs basic validation on the bank card details, the information is directed back to the criminal's Command and Control (C2) server. Additionally, the trojan can hide notifications from certain banking apps installed on the device.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE MOBILE-ATT&CK] Abuse Accessibility Features - T1453
Operation Soft Cell: A Worldwide Campaign Against Telecommunications Providers (June 25, 2019)
An advanced, persistent attack targeting telecommunication providers, active since at least 2012, according to Cybereason researchers. The attack, dubbed Operation Soft Cell, was aiming to obtain all data stored in the active directory of a large telecommunications provider, compromising usernames and passwords within the organization, as well as billing information, call detail records, credentials, email servers, and personal identifiable information. The attack consisted of customized and highly-modified versions of the China Chopper web shell, Poison Ivy rat, and “mimikatz” to ultimately obtain credentials. The attackers worked in waves, abandoning one thread of the attack when detected and stopped, but would return months later with new techniques. Cybereason believes with a high level of certainty that the threat actor is affiliated with China and is likely state-sponsored. The tools and techniques used throughout these attacks are consistent with several Chinese actors believed to operate on behalf of the Chinese Ministry of State Security.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Command-Line Interface - T1059 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Web Shell - T1100 | [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] Indicator Removal from Tools - T1066 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | Credential Dumping (ATT&CK T1003)
Sodinokibi Ransomware Now Pushed by Exploit Kits and Malvertising (June 24, 2019)
Exploit kit researcher nao_sec has discovered “Sodinokibi” ransomware is now being distributed though malvertising that leads to the RIG exploit kit. Sodinokibi has been making news since the “GandCrab” family of ransomware has retired, but by distributing through hacking sites to replace legitimate software with ransomware, and by hacking into the backends of Managed Service Providers (MSPs). The new use of exploit kits shows Sodinokibi is widening it’s stream of vectors to infect victims with ransomware. According to ID-Ransomware, Sodinokibi has been growing and continues to use similar tactics that GandCrab used in the past.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Service - T1102 | [MITRE ATT&CK] Remote Access Tools - T1219
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
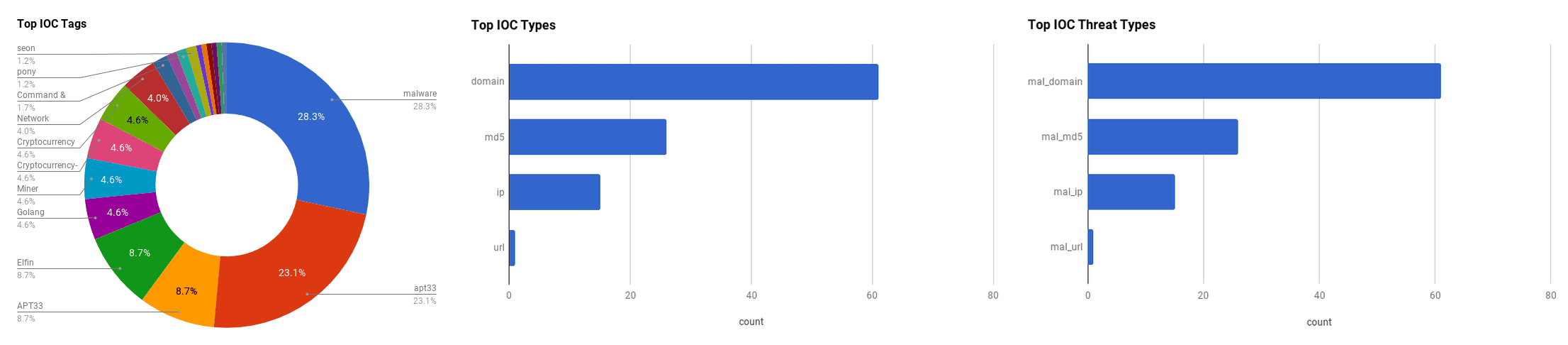
APT33 The Advanced Persistent Threat (APT) group “APT33” is believed to be an Iranian-based group that has been active since at least 2013. APT33 conducts cyber espionage campaigns and deploys destructive malware on an organizations primarily situated in Saudi Arabia but have also targeted firms in South Korea and the United States. They are believed to be a state-sponsored group, because their campaigns target firms that would align to Iranian government and military interests. They have heavily targeted the aviation industry in Saudi Arabia, which may suggest that they are attempting to acquire knowledge on Saudi Arabia’s military aviation capabilities in order to enhance their domestic aviation abilities and to support strategic decisions. Their targeting of the South Korean petrochemical industry may been to gain insight into South Korea’s partnerships with Iran’s petrochemical industry as well as their relationships with Saudi Arabian petrochemical companies. Possibly in an attempt to help gain information needed to expand Iran’s petrochemical production and competitiveness in the Middle East.
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



