Weekly Threat Briefing: Hacked Bulgarian Database Reaches Online Forums
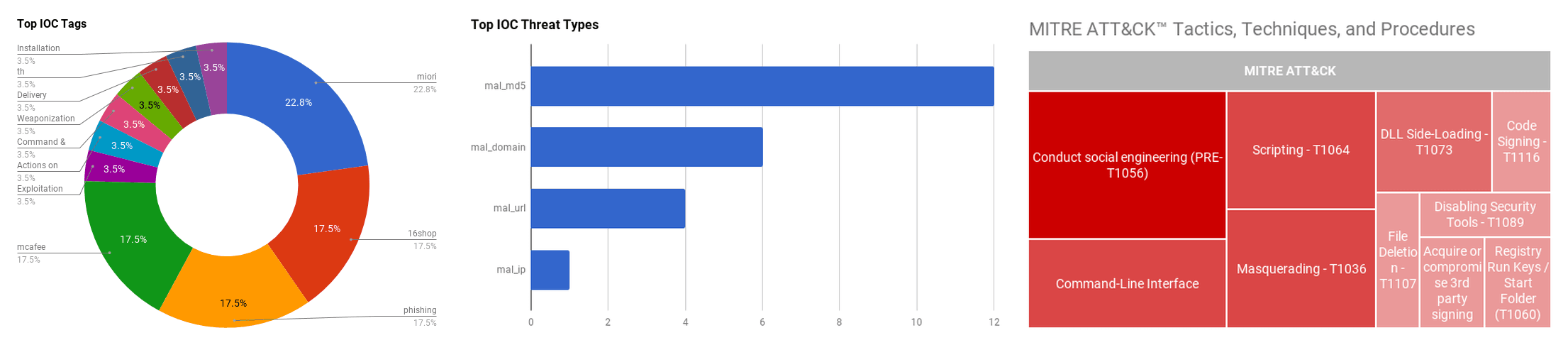

The intelligence in this week’s iteration discuss the following threats: APT, Compromise, Malspam, Phishing, Ransomware, RAT, Threat group, Underground markets, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Hacked Bulgarian Database Reaches Online Forums (July 22, 2019)
The database of Bulgaria's National Revenue Agency (NRA), which was compromised in late June 2019, is now being shared on hacking forums. Download links to the database have been shared by a data trader known as “Instakilla,” who is believed to be operating out of Bulgaria. The database contains 57 folders, 10.7 GB in size, and holds personal and financial information consistent with what Bulgarian newspapers reported receiving over the weekend. This includes Personally Identifiable Information (PII) and tax information, from both the NRA and from other government agencies who shared their data. In the meantime, the investigation into the NRA hack has advanced in Bulgaria. Bulgarian Interior Minister Mladen Marinov continues to push the idea that Russian hackers are behind the security breach.
Click here for Anomali recommendation
Elusive MegaCortex Found – Here is What We Know (July 19, 2019)
A sample of ransomware called “MegaCortex,” first found by Sophos researchers in May 2019 being used in targeted attacks, has been analyzed by security researchers MalwareHunterTeam and Vitali Kremez. The researchers found that this sample was signed with a certificate from a UK company called “ABADAN PIZZA LTD.” It is likely that the company abandoned the certificate that was then “claimed by the attackers under their own aliases in order to purchase a certificate.” The actors have also updated this MegaCortex variant no longer requires “a special base64 encoded string for the DLL payload to be unpacked and injected into memory.” These changes indicate that the threat actors utilizing MegaCortex are aiming to improve the malware by making it appear like legitimate software and making the executable more simple to run and begin encrypting the infected machine.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Code Signing - T1116 | [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Disabling Security Tools - T1089 | [MITRE PRE-ATT&CK] Acquire or compromise 3rd party signing certificates (PRE-T1109) | [MITRE ATT&CK] Data Encrypted - T1022
Monero Cryptocurrency Miner Uses 17-year Old Open Source Tool (July 19, 2019)
Analysts at Trend Micro have detected a threat infecting devices with both a Monero cryptocurrency miner and a Perl-based internet relay chat (IRC) backdoor. The threat propagates by scanning for open ports and brute forcing weak credentials and then send a command that will download the backdoor, called “Shellbot,” and the miner. The miner process is hidden using “XHide Process Faker,” a 17-year old open-source tool used to fake the name of a process. Despite these techniques and tools having been known and available for some time, the mix of these routines can still be effective if the targeted systems have weak or default usernames and passwords that can be brute-force attacked.
Click here for Anomali recommendation
FaceApp Scams Emerge Due to Heightened Popularity (July 19, 2019)
The popularity around the FaceApp application has attracted scammers who want to make some quick profits, according to ESET researchers. Scammers have been using a fake “PRO” version of the application as bait and have made an effort to spread the word about this fictitious version of the currently-viral app. The FaceApp application, which offers various face-modifying filters, is available for both Android and iOS. While the app itself is free, some features, marked as “PRO”, are paid. One form of the scam uses a fake website that claims to offer a premium version of FaceApp. The second type of scam includes YouTube videos again promoting download links for a “Pro” version. The scammers trick their victims into clicking through offers for installing other paid apps and subscriptions, ads, and surveys. Victims also receive requests from various websites to allow displaying notifications. When enabled, these notifications lead to further fraudulent offers. One of the fraudulent YouTube videos had over 150,000 views, as of this writing.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056)
New Okrum Malware Used by Ke3chang Group to Target Diplomats (July 18, 2019)
ESET researchers, while monitoring Chinese Advanced Persistent Threat (APT) group Ke3chang between 2015 and 2019, have discovered updated malware implants and a new backdoor named “Okrum.” The cyberespionage activities of the Ke3chang advanced persistent threat group (also known as APT15) span over almost a decade, going back as far as 2010, according to FireEye researchers. The threat group's primary targets are entities from the oil industry, military, government contractors, as well as European diplomatic missions and organizations. As of this writing, the initial infection vector for Okrum is unknown. After being dropped on a target's computer, the Okrum implant can gain admin rights by calling the ImpersonateLoggedOnUser API, and it will start collecting computer information such as build number, computer name, host IP address, OS version, primary DNS suffix value, and user name. Once in the system, the Ke3chang actors will use and abuse a wide variety of other tools to achieve their goals, from password dumpers and network sessions enumerators to keyloggers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Command-Line Interface - T1059 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Service Execution - T1035 | [MITRE ATT&CK] New Service - T1050 | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060) | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Shortcut Modification - T1023 | [MITRE ATT&CK] Access Token Manipulation - T1134 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Indicator Removal on Host - T1070 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] Credential Dumping - T1003 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] System Information Discovery - T1082 | [MITRE ATT&CK] System Network Connections Discovery - T1049 | [MITRE ATT&CK] System Time Discovery - T1124 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Input Capture - T1056 | Data Compressed (MITRE ATT&CK T1002) | [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Exfiltration Over Command and Control Channel - T1041 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Connection Proxy - T1090 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] Standard Cryptographic Protocol - T1032
Spam Campaign Targets Colombian Entities with Custom-made Remote Access Tools (July 18, 2019)
A spam campaign discovered by Trend Micro researchers was found targeting financial institutions and governmental organizations in the South American region, particularly in Colombia, using a new malware known as “Proyecto RAT.” Researchers believe the actors behind the campaign are regularly involved in business email compromise scams, and are unlikely to be affiliated with an Advanced Persistent Threat (APT). The main payload was a Remote Access Tool (RAT) known as Imminent Monitor. Researchers observed that this RAT downloaded and executed another payload, which is the Proyecto RAT. The actors relied on a disposable email address service called YOPmail for a command-and-control server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Exfiltration Over Command and Control Channel - T1041
“EvilGnome” Backdoor Implant Spies On Linux Desktop Users (July 17, 2019)
A new Linux malware dubbed “EvilGnome” was discovered in July 2019 masquerading as a Gnome shell extension and designed to spy on unsuspecting Linux desktop users. Researchers at Intezer Labs found that EvilGnome functionalities include desktop screenshots, file stealing, and allowing the ability to capture audio recording from the user’s microphone. The backdoor also has the ability to download and execute further modules. EvilGnome appears to be connected with the Russian threat group known as Gamaredon Group, an Advanced Persistent Threat (APT) group known to have been active since at least 2013. At the time of this writing, The backdoor implant is not detected by any of the anti-malware engines on VirusTotal.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] Screen Capture - T1113 | Data Compressed (MITRE ATT&CK T1002) | [MITRE ATT&CK] Local Job Scheduling - T1168 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Exfiltration Over Command and Control Channel - T1041 | [MITRE ATT&CK] Input Capture - T1056
Newly Discovered Malware Framework Cashing in on Ad Fraud (July 17, 2019)
A new malware framework is responsible for more than one billion fraudulent advertisement instances between May and July 2019, according to Flashpoint researchers. The activity is generating its operators significant Google AdSense revenue on a monthly basis. The framework features three separate stages that ultimately install a malicious browser extension designed to perform fraudulent AdSense impressions, as well as generate likes on YouTube videos and watch hidden Twitch streams. Google Chrome, Mozilla Firefox, and the Yandex browser are all targets on Windows machines. Infected browsers are linked into a botnet which is used to generate monthly income for fraudsters. The malware is concentrated in a few geographic locations, with most installers being in Russia, Ukraine, and Kazakhstan.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140
Metamorfo Banking Malware Hides By Abusing Avast Executable (July 16, 2019)
enSilo Threat Intelligence researchers observed malicious activity in May 2019 conducted by a Brazilian threat group distributing the banking trojan “Metamorfo.” Researchers discovered variants of the trojan that abuse an executable digitally signed by Avast, which is a well-known antivirus products company. The downloader starts by checking if the system is running in a virtual machine. If not, downloads a zip file, unzips it, deletes itself, establishes persistency, and restarts the system. Like samples from previous campaigns, Metamorfo displays fake forms on targeted banking sites to steal credentials from the victims.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE MOBILE-ATT&CK] Generate Fraudulent Advertising Revenue - T1472
New Extenbro DNS Changer Trojan Blocks Security Domains (July 16, 2019)
“Extenbro” is a newly discovered DNS-changing trojan that blocks users from accessing security sites to prevent them from downloading antivirus software. Malwarebytes Labs uncovered the trojan hidden within an adware bundler that is publicly available for download. When installed, a scheduled task will be created that automatically launches the trojan on startup. The trojan then will disable IPv6 on all compromised machines to make sure that the victims do not circumvent the attacker-controlled DNS servers. After an infected user finds and removes all rogue DNS servers added to their network settings, the malware will re-add them after a system restart since it also adds a randomly named scheduled task for this specific purpose during the infection stage. Malwarebytes has created a removal guide that is available in their forums page.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Install Root Certificate - T1130 | [MITRE ATT&CK] Scheduled Task - T1053
Abusing Microsoft’s Azure Domains To Host Phishing Attacks (July 16, 2019)
Zscaler ThreatLabZ team has detected phishing attacks that leverage Microsoft Azure custom domains. The threat actors behind this malicious activity signed their phishing sites with a Microsoft SSL certificates in an attempt to make the websites appear authentic. The phishing email being sent contained a link that once activated, redirects to an Outlook login phishing page hosted using the Azure domain. Once the login information is entered by the user, the form will post the user’s credential details to the compromised domain that is operated by the attacker. Microsoft was notified of the attacks and quickly engaged to shut these sites down, and Zscaler detected and blocked 2,000 phishing attempts from these domains over a six-week period.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] Code Signing - T1116 | [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140
SWEED Threat Actor Uses Typosquatting, UAC Bypasses to Distribute Agent Tesla (July 15, 2019)
Cisco Talso researchers have identified malicious activity conducted by a threat actor dubbed “SWEED.” The actor uses typosquatting and User Account Control bypassing techniques to distribute Agent Tesla and other malware. The researchers, who have been tracking SWEED’s efforts to distribute Agent Tesla since 2017, observed the threat actor employing various tactics to propel its attack campaigns, including using Java-based droppers and steganography to secretly decode a chain of .NET executables. The actor also incorporated previously disclosed Microsoft Office vulnerabilities, most notably “CVE-2017-8759” and “CVE-2017-11882,” into its attack campaigns before resorting to Office macros and AutoIt droppers in 2019.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Masquerading - T1036 | Data Compressed (MITRE ATT&CK T1002) | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Bypass User Account Control - T1088
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
Ke3chang The Advanced Persistent Threat (APT) group “Ke3chang” is believed to be based in China and has been active since at least 2010. FireEye researchers first identified the group in their report on a cyber espionage campaign dubbed “Operation Ke3chang” that was published on December 11, 2013. Since that initial report, the group has continued to conduct cyber espionage campaigns that target entities associated with governments, such as ministries of foreign affairs and contractors. However, specific targeting of one company within a particular industry has also been observed.
Gamaredon Group The Advanced Persistent Threat (APT) group called “Gamaredon Group” is believed to be a Russia-based group that has been active since at least 2013. The group is known for conducting cyber espionage campaigns targeting the Ukrainian government, law enforcement officials, and military. The Lookingglass Cyber Threat Intelligence Group first reported on the group in their report on a cyber espionage campaign dubbed “Operation Armageddon” in April 2015, according to Palo Alto Networks Unit 42 researchers. This led Unit 42 researchers, in February 2017, to name the group “Gamaredon Group” because they believe the group conducted Operation Armageddon.
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



