Weekly Threat Briefing: Hackers Steal $4.2m From State Troopers' Pension Fund

The intelligence in this week’s iteration discuss the following threats: LokiBot, Magecart, Nemty, NetWire, Purple Fox, Ryuk Ransomware, and WiryJMPer. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Database Leaks Data On Most of Ecuador's Citizens, Including 6.7 Million Children (September 16, 2019)
A database of approximately 20.8 million citizen records has been exposed via a misconfigured database, in one of the largest leaks in the country’s history. The database, held on an ElasticSearch server was discovered by researchers Noam Rotem and Ran Locar. The data contained included Dates of birth, Cedulas (national ID numbers), Education levels, Employment information, Home addresses, Marital status, Names, and Phone numbers. Information on families was also exposed including family relationships and 6.7 million records about children under the age of 18 that include addresses, cedulas, gender, names, and places of birth. After a week of being exposed, the database was finally secured after vpnMentor contacted the Ecuador Computer Emergency Response Team, who acted as an intermediary.
Click here for Anomali recommendation
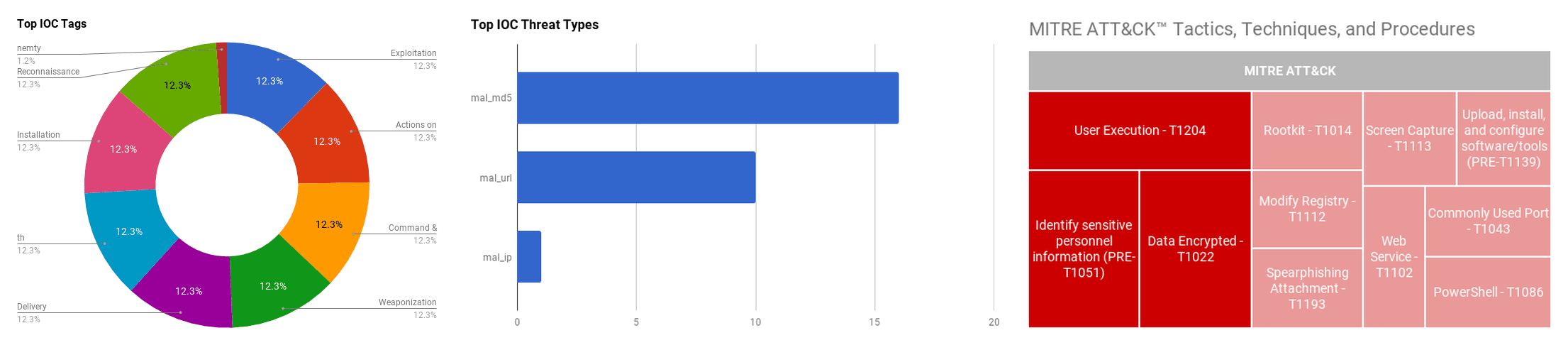
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
New WiryJMPer Droppers Hides Netwire RAT Payloads in Plain Sight (September 12, 2019)
Avast researchers have identified a new malware dropper that infects systems with Netwire malware. Netwire is a Remote Access Trojan (RAT) that allows actors to remotely control their victims’ computers. The discovery was first made as researchers noticed a cryptocurrency wallet, specifically an ABBC Coin wallet, binary was three times the size of a regular wallet. Netwire infects the system while windows are shown in the foreground to distract the user. The malware adds a shortcut in attempt to gain persistence.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Screen Capture - T1113 | [MITRE ATT&CK] Remote Access Tools - T1219 | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060)
Garmin SA Shopping Portal Breach Leads to Theft of Payment Data (September 12, 2019)
Garmin Southern Africa, a satellite technology company, disclosed that their customer data has been breached. The customer data includes address, email addresses, first and last name, and payment information including card number, CVV code and expiration date. The cause of the breach hasn’t been suggested, however it could be a Magecart skimmer due to the site running on Magento CMS, a platform that has been compromised with Magecart skimmers in recent months.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Ryuk Related Malware Steals Confidential Military, Financial Files (September 11, 2019)
The security researchers known as MalwareHunterTeam have identified a new malware that searches for sensitive files and uploads to an FTP site. The malware appears to be similar to the Ryuk Ransomware that encrypts victims’ files and demands a ransom. MalwareHunterTeam notes that the malware appears to make it seem like it is stealing files but likely does not actually do so. Targeting confidential financial, law enforcement and military files, the malware looks for files with document file extensions such as .doc and then compares the file name to a list of strings including words such as defence, military, undercover among others which are then uploaded to a server. While there are ties to Ryuk ransomware, such as code similarities, it is unknown if they are the same group or how the systems are being infected with the malware.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exfiltration Over Alternative Protocol - T1048 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] Data Encrypted - T1022
Hackers Steal $4.2m From State Troopers' Pension Fund (September 9, 2019)
A pension fund for law enforcement officers of Oklahoma have had $4.2 million stolen from a fund of over $1 billion. Occuring on August 26, 2019, the email account of an investment manager working for the Oklahoma Law Enforcement Retirement System (OLERS) was breached. The fund handled the pensions and benefits for retired law enforcement officers, highway troopers, park rangers, and state agents. The FBI is investigating the incident and, as of this writing, $477,000 has been recovered so far.
Click here for Anomali recommendation
Microsoft Teams Can Be Used To Execute Arbitrary Paylods (September 10, 2019)
Researcher Reegun Richard has a flaw that can allow actors to use binaries to execute malicious code using a fake installation folder. All that is needed is an executable and two folders that part of Microsoft Teams installation, inheriting trust of the signed executable any code placed in the folder will be deployed. Apps affected include those that use the Squirrel installation framework such as Discord, GitHub, Grammarly, Slack, and WhatsApp. While Microsoft are aware of the issue, they claim it “did not meet the bar of security issue”.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify vulnerabilities in third-party software libraries - T1389 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190
LokiBot Info-Stealer Used in Spearphishing Attack on US Company (September 10, 2019)
Researchers with the FortiGuard SE Team have identified a malspam campaign that is distributing LokiBot via phishing messages. The campaign is targeting employees of a large US manufacturing company with an email attachment, which if downloaded will infect the user with malware. Stealing information from the company including credentials, and passwords the malware then relays the information back to the Command & Control server via an HTTP POST request.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping - T1003 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | Data Compressed (MITRE ATT&CK T1002)
‘Purple Fox’ Fileless Malware with Rootkit Component Delivered by Rig Exploit Kit Now Abuses Powershell (September 9, 2019)
A new version of ‘Purple Fox’, a downloader malware that delivers cryptocurrency miners, has been discovered abusing PowerShell for fileless infection. The actors abuse vulnerabilities in VBScripts’ engine so that an .hta file redirects to use a malicious PowerShell script. The script posing as an image file then exploits vulnerabilities to escalate privileges and install the main malware component. The payload, an msi file with encrypted shellcode, restarts the system and renames its components and using its rootkit capabilities to hide and protect files and registry entries to make it more difficult for the malware to be reversed.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Rootkit - T1014
Fake PayPal Site Spreads Nemty Ransomware (September 8, 2019)
A new variant of the “Nemty” ransomware is being spread to users from a fake PayPal website. The Nemty ransomware drops a ransom note to victims demanding around $1,000, with the ability to collect users’ computer ID, computer name, operating system, and username. Pretending to be the PayPal website, the fake page advertises a return on payments made through the system of around 3-5%, with an executable containing the ransomware should users click to download. Using homograph domain spoofing, the actors are able to spoof links for various links on the fake website, making it look like the legitimate PayPal website.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Web Service - T1102 | [MITRE PRE-ATT&CK] Upload, install, and configure software/tools (PRE-T1139) | [MITRE ATT&CK] Data Encrypted - T1022
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



