Weekly Threat Briefing: HealthCare.gov Suffered Data Breach as Hackers Stole 75,000 Records
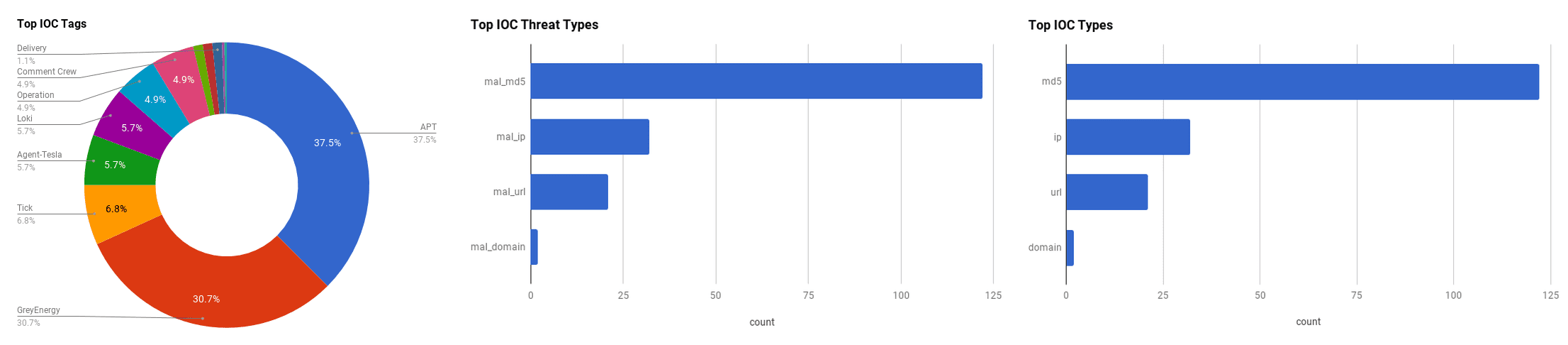

The intelligence in this weekís iteration discuss the following threats: APT, Cryptomining, Data breach, DDoS, Spear phishing, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Web Hosting Software VestaCP Server Compromised With DDoS Malware (October 22, 2018)
Vesta Control Panel, an open-source hosting solution company suffered a supply chain attack. The company states presumably that threat actors were able to use a bug in the company's API of an older software version (affected versions are 0.9.8-20), to change the installation bash scripts for the Ubuntu target, to log administrative passwords and IPs. Users affected in the supply chain attack also discovered a binary located at "/usr/bin/dhcprenew" that could open a shell or launch DDoS. The malware appeared to have been a Linux/ChachaDDoS malware strain.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application (T1190) | [MITRE ATT&CK] Supply Chain Compromise (T1195)
HealthCare.gov Suffered Data Breach As Hackers Stole 75,000 Records (October 22, 2018)
The US government's health insurance system, "HealthCare.gov" suffered a data breach following a cyber-attack. The breach was discovered after the Centres for Medicare and Medicaid Services (CMS) detected suspicious activity in the Direct Enrollment Pathway intended for agents and brokers. At least 75,000 records were accessible by threat actors, including sensitive personal information. The full extent of information accessed by the unknown threat actors was not disclosed, but it is suspected that Personally Identifiable Information (PII) and Personal Health Information (PHI) such as health records, and social security numbers were vulnerable. An investigation is still ongoing to determine how the Direct Enrollment Pathway was vulnerable and the full extent of the breach. An official disclosed that the direct HealthCare.gov site was unaffected and remains safe to use.
Click here for Anomali recommendation
Zero-day In Popular jQuery Plugin Actively Exploited For At Least Three Years (October 19, 2018)
A zero-day exploit in the jQuery File Upload plugin has been observed to be abused by threat actors for at least three years. This File Upload plugin is one of the most popular jQuery projects on GitHub and has been forked (where a user copies the original source code and creates a distinct and separate piece of software) in over 7,800 projects. The vulnerability, registered as "CVE-2018-9206," is in the plugin's expected behaviour for file uploads to PHP servers due to a change in the Apache Web server. The vulnerability affects jQuery file upload versions before 9.22.1, and can be used to upload malicious files on servers. This vulnerability has been observed to be exploited in the wild by a variety of threat actors for years, and is a well-known exploitable vulnerability within the threat actor community. The number of affected projects is at least 7,800, but it is expected that this number will increase exponentially since this particular plugin is fairly ubiquitous in web-facing services such as blogging platforms, enterprise solutions, CRMs, and CMSs.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Shared Webroot (T1051)
Tracking Tick Through Recent Campaigns Targeting East Asia (October 18, 2018)
The Advanced Persistent Threat (APT) group, "Tick" (also known as "Bronze Butler" and "Redbaldknight"), has been active since 2016 targeting countries such as Japan and South Korea, as observed by researchers at Cisco Talos. While initial attack vectors are unclear, it is assumed the APT group is likely to deliver their malware via drive-by downloads or watering hole attacks on South Korean and Japanese sites. An insecure South Korean laundry service website was observed to be a host to one of the Command and Control (C2) servers controlled by the APT group. The group is observed to utilise malware known as "Datper" that can execute shell code onto a victim's computer to obtain hostnames and drive information, as well as the "xxmm" and "Emdivi" backdoors. It was discovered that several IP addresses that Tick uses to host their C2 servers actually resolve to hijacked, but legitimate South Korean and Japanese websites, and it is possible that the APT group purchased them to make them less suspicious and detectable.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise (T1189)
GreyEnergy: Updated Arsenal Of One Of The Most Dangerous Threat Actors (October 18, 2018)
Researchers from ESET have discovered a new malware framework that has been observed to be used by a newly observed Advanced Persistent Threat (APT) group, dubbed "GreyEnergy." Their attacks have been focused upon energy companies and other high-value targets in Poland and Ukraine for the last three years, working to stay under the radar. The malware the APT group utilises is similar to that of "BlackEnergy," an APT group who caused power grid system failure in Ukraine in 2015 that left over 230,000 people without electricity. This APT group has two methods to infect a target: spear phishing and compromising public-facing web servers. Compromising a public-facing web server, allows the group to infect users, as well as move laterally in the network to other workstations. They use Mimikatz, custom port scanners, WinExe, and others to help deploy their malware and establish backdoors as well as log keystrokes, steal credentials and passwords, and extract files.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping (T1003) | [MITRE ATT&CK] Exploit Public-Facing Application (T1190)
Oceansalt CyberattackWave Linked To Defunct APT Comment Crew (October 18, 2018)
A new campaign targeting has been observed to be targeting organisations in Canada, South Korea, and the US utilising malware once attributed to the Chinese Advanced Persistent Threat (APT) group "Comment Crew" (APT1), according to Symantec researchers. The campaign, dubbed "Operation Oceansalt," consists of five waves of attacks with the objective of cyber espionage and data reconnaissance. The APT group was observed to first target a South Korean organisation in May 2018. How this new group, or if it is a re-emergence of Comment Crew, is targeting the unnamed organisations or what industry the organisations are in, has not yet been reported in open sources. However, the group is reported to use a data reconnaissance implant that shares code with Comment Crew's "Seasalt" malware implant.
Click here for Anomali recommendation
Critical Flaws Found In Amazon FreeRTOS IoT Operating System (October 18, 2018)
Security researcher Ori Karliner has discovered 13 vulnerabilities located in Amazon's "FreeRTOS" real-time operating system. FreeRTOS functions as a kernel for microcontroller devices and is currently being used in Internet-of-Things (IoT) devices and multiple industries included aerospace, automotive, and medical, among others. The 13 vulnerabilities could result in the following: one Denial-of-Service (DoS), seven information leak, four Remote Code Execution (RCE), and one classified as "other."
Click here for Anomali recommendation
Overboard: How Tea Party Campaign Assets Were Exposed Online (October 17, 2018)
Over 527,000 individuals had their Personally Identifiable Information (PII) publicly exposed due to a misconfiguration of an Amazon S3 bucket that belonged to the American Tea Party Patriots Citizens Fund (TPPCF). The leaked data consisted of strategy documents, call scripts, marketing assets, and other files for the TPPCF. The breach was discovered by researchers at UpGuard on August 28, 2018, and they notified the TPPCF on October 1, 2018. By October 5, 2018, all access to the bucket was removed. Approximately two gigabytes of data was accessible.
Click here for Anomali recommendation
LibSSH Flaw Allows Hackers To Take Over Servers Without Password (October 16, 2018)
A four-year-old vulnerability in the Secure Shell (SSH) implementation library called "libssh" has been discovered that allows for authentication bypass and complete administrative control without a password. The vulnerability, registered as "CVE-2018-10933," is an authentication bypass that was found in Libssh version 0.6 released in 2014 which allowed for organisations' servers that utilised it to be vulnerable to exploitation by threat actors for four years. The vulnerability was due to a coding error that could allow a threat actor complete access to a server by sending a "SSH2_MSG_USERAUTH_SUCCESS" response to libssh that will believe that a request was successful and authorises that access without the need for a password to be entered. This vulnerability does not affect sources like GitHub as the way they utilise the library does not allow for the vulnerability to be actionable. Up to 6,500 internet-facing servers in a variety of organisations could be impacted by this vulnerability. Libssh has released a security patch to this.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application (T1190)
Microsoft Store Has Been Hosting An Ad Clicker Disguised As A Google Photos App (October 16, 2018)
An application called "Album by Google Photos" was available for download in the official Microsoft Store that turned out to be an ad clicker that hides adverts in Windows 10 Operating System instead of being a legitimate photo album application. The application claims it was developed by "Google LLC," and despite most reviews being negative and stating it is a fake application, it still has yet to be removed by Microsoft from the store. The application is a Progressive Web Application (PWA) that acts as a front end for Google photos that is combined with an ad-clicker. The application runs and clicks ads in the background which produces income for the developers after connecting to a specific URL "http://11k.online/Ad/constants/9n0wkj6hpz86.json" that contains the configuration settings file necessary to run the ads and generate income. As of October 22, 2018, the application is no longer available in the official Microsoft Store.
Click here for Anomali recommendation
Vulnerability Spotlight: Linksys E-Series Multiple OS Command Injection Vulnerabilities (October 16, 2018)
Cisco Talos recently disclosed several operating system command injection vulnerabilities they have discovered in the Linksys E Series home routers. The three vulnerabilities, registered as "CVE-2018-3953," "CVE-2018-3954," and "CVE-2018-3955" can be exploited by a threat actor sending an authenticated HTTP request to the network configuration. Vulnerability CVE-2018-3953 is exploited when the "nvram_get" call function is used to get the value of the user-controlled "machine_name" NVRAM entry, and once that value is obtained it can be used directly in a command to write the hostname to a file and execute said file. CVE-2018-3954 is triggered by a "set_host_domain_name" function in libshared.so and results in combining the machine name parameter with a string and sends it directly to the system command. CVE-2018-3955 is exploited similar to CVE-2018-3955, but is triggered when data entered into the "Domain Name" field of the web portal is submitted as a "wan_domain" POST parameter. All of these vulnerabilities could allow for the execution of arbitrary code in these home/small office routers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Process Injection (T1055)
Cyber Criminals Have Been Targeting Literary Agencies And Publishers (October 16, 2018)
Literary scouting agency, Eccles Fisher and other companies in the literary industry such as Penguin Random House UK, have faced a series of spear phishing emails feigning to be from the owner of the company or other literary agents. These emails appear legitimate and requests author manuscripts from the recipient. Specific to Eccles Fisher, the unknown threat actors also request the password to the Eccles Fisher website, pretending to be the owner, Catherine Eccles. Penguin Random House and Pan Macmillan have issued internal briefings to their employees across the globe about the phishing scam.
Click here for Anomali recommendation
iPhone A Growing Target Of Crypto-Mining Attacks (October 15, 2018)
iPhone's have seen a substantial increase of almost 400% in the last two weeks of September 2018 for cryptomining attacks targeting the Safari browser. Attackers were observed by Check Point researchers to have used Coinhive mining malware to specifically target iPhones. Since September 2018, there has been a sharp increase in cryptomining and other malware attacks targeting the Safari browser, and subsequently, iPhone users.
Click here for Anomali recommendation
Old Dog, New Tricks - Analysing New RTF-based Campaign Distributing Agent Tesla, Loki With PyREbox (October 15, 2018)
A new malware campaign has been discovered by researchers at Cisco Talos that is distributed via an RTF document fetched from inside a malicious Microsoft Office DOCX file relationship reference. The malicious file drops two different information stealing trojans: "Agent Tesla" and "Loki." The malicious document is able to go undetected by common antivirus software, due to the modification of the exploit chain used by the threat actors. This campaign utilises the memory buffer vulnerability, registered as "CVE-2017-11882," that allows for arbitrary code execution. The malware initially runs the Microsoft Equation Editor, a tool used by Microsoft Office to embed mathematical equations into documents, to run "scvhost.exe" which creates the connection to the threat actor's Command and Control (C2) server. This "scvhost.exe" also contains shellcode that eventually delivers the final payloads for both Agent Tesla and Loki onto the infected machine. Agent Tesla and Loki are both information-stealing Remote Access Trojans (RATs) that can steal passwords, capture screens, access the webcam, and download additional malware onto the machine.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Masquerading (T1036)
FEATURED RESOURCES

Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more


