Weekly Threat Briefing: Malicious Campaign Targets South Korean Users with Backdoor-Laced Torrents
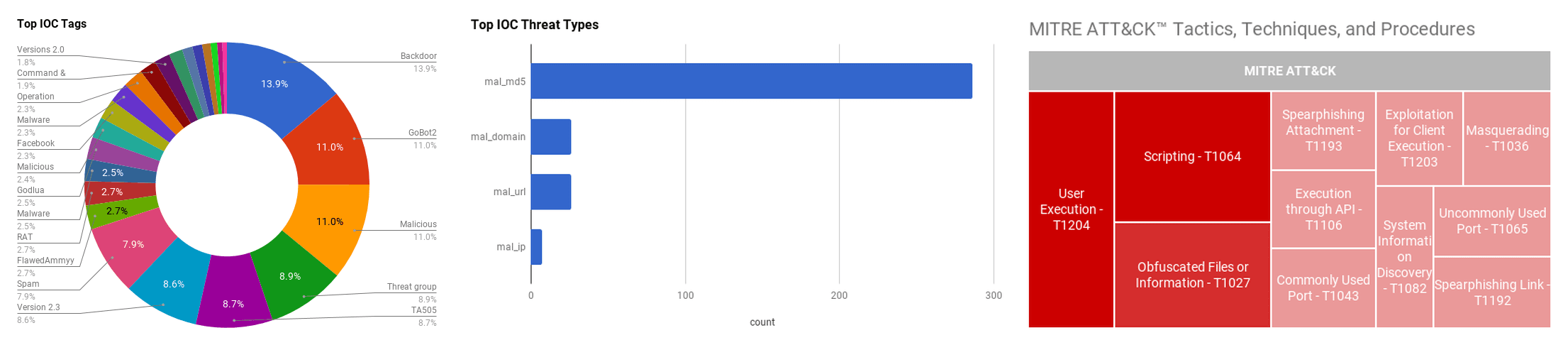

This section listed below contains summaries on various threat intelligence stories that occurred during the past week. The intelligence in this week’s iteration discuss the following threats: APT, Automated attacks, Backdoor, Breach, Malspam, Phishing, Targeted attacks, Threat groups, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Malicious Campaign Targets South Korean Users with Backdoor-Laced Torrents (July 8, 2019)
A campaign has been discovered targeting fans of Korean television in attempts to distribute a modified version of the open-source backdoor called “GoBot2,” according to ESET researchers. GoBot2 is being distributed via torrent sites masquerading as South Korean games, movies, and television shows. This campaign has been ongoing since at least March 2018 with the most infections found to be in South Korea, China, and Taiwan. The torrent sites utilized in this campaign attempt to convince users “into executing the malware by booby-trapping the content of the torrents with malicious files that have deceptive filenames, extensions and icons.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise - T1189 | [MITRE ATT&CK] Command-Line Interface - T1059 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060) | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Bypass User Account Control - T1088 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Disabling Security Tools - T1089 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Indicator Removal on Host - T1070 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Redundant Access - T1108 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] System Information Discovery - T1082 | [MITRE ATT&CK] System Network Connections Discovery - T1049 | [MITRE ATT&CK] System Owner/User Discovery - T1033 | [MITRE ATT&CK] System Time Discovery - T1124 | [MITRE ATT&CK] Remote File Copy - T1105 | [MITRE ATT&CK] Replication Through Removable Media - T1091 | [MITRE ATT&CK] Screen Capture - T1113 | [MITRE ATT&CK] Connection Proxy - T1090 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE MOBILE-ATT&CK] Standard Application Layer Protocol - T1437 | [MITRE ATT&CK] Uncommonly Used Port - T1065 | [MITRE ATT&CK] Endpoint Denial of Service - T1499 | [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Resource Hijacking - T1496
NHS Must Take Urgent Steps to Defend Against Hackers, Says White Paper (July 6, 2019)
Researchers from Imperial College London’s Institute of Global Health Innovation have published a white paper discussing risk posed to the National Health Service (NHS). The paper contends that NHS hospitals are vulnerable to threat actors due to a combination of lack of awareness, investment, and skills, in addition to the use of outdated systems. The researchers also suggest that while their report discusses the NHS, the overall position of healthcare systems around the globe remain vulnerable to cyberattacks.
Click here for Anomali recommendation
Automated Magecart Campaign Hits Over 960 Breached Stores (July 5, 2019)
Sanguine Security researchers have identified an automated, large-scale campaign in which threat actors installed payment card-skimming scripts on over 960 online stores in approximately 24 hours. Researchers believe that the threat groups, referred to as the umbrella term “Magecart,” are behind this campaign. Although researchers did not specify how the automated attack would work, they believe it is possible that Magecart was scanning for vulnerable online stores in which the data-stealing script would be injected, typically in the websites checkout page. The skimmer is capable of stealing data such as: addresses, “full credit card data,” names, and phone numbers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Scripting - T1064
7-Eleven Japanese Customers Lose $500,000 due to Mobile App Flaw (July 4, 2019)
Unknown threat actors were able to steal over $510,000 USD (¥55 million Yen) from approximately 900 customers of 7-Eleven Japan. Researchers found that the mobile application had a password reset function that would allow the password-reset link to the actor’s own email instead of the one associated with the account. The actors launched automated attacks with data including date of birth, email addresses, and phone numbers to brute force their way into the accounts. Once illicit access was gained, the actors were able to steal over $500,000 from the 7-Eleven accounts.
Click here for Anomali recommendation
New Backdoor and Malware Downloader Used in TA505 Spam Campaigns (July 4, 2019)
The financially-motivated threat group “TA505” has once again been found to have added a new malware to their arsenal, according to Trend Micro researchers. The first week in July has brought with it two publications by Trend Micro and Proofpoint, both of which identified the new downloader called “Gelup” by Trend Micro, and “Andromut” by Proofpoint. Trend Micro also observed TA505 implementing another new malware into their spam email campaigns dubbed “FlowerPippi” that is delivered via malicious attachments. FlowerPippi can function as a downloader and as a backdoor and is capable of stealing information and running commands received from a Command and Control (C2) server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Execution through API - T1106 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] DLL Side-Loading - T1073
New Godlua Malware Evades Traffic Monitoring via DNS over HTTPS (July 3, 2019)
Qihoo 360 researchers have found a new backdoor, dubbed “Godlua,” backdoor that is capable of targeting Linux and Windows machines as well as securing its communications via DNS over HTTPS (DoH). Two variant of the malware were identified. One that targets Linux that appears not being updated anymore, and the second targeting Windows that has more malicious capabilities than the former. Godlua was discovered while examining a malicious ELF file, which may indicates an infection vector, and was found to be able to infect by exploiting the Atlassian Confluence vulnerability, registered as “CVE-2019-3396.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Scripting - T1064
Bangladesh Cyber Heist 2.0: Silence APT Goes Global (July 3, 2019)
The threat group “Silence,” is believed to be responsible behind an attack targeting Dutch-Bangla Bank ATMs, according to Group-IB researchers. Silence is a financially-motivated and Russian-speaking threat group that has been active since at least 2016. The theft took place on May 1 and May 2, 2019. Silence was able to steal at least $3 million (USD) using stolen Personal Identification Numbers (PINs) and credit cards, according to the local media outlet The Daily Star. Researchers believe it is likely that the group used multiple trojans in this incident including: Silence.Download (TrueBot), Silence.MainModule, and Silence.ProxyBot. How the group gained access to the bank’s network is unknown as of this writing, but once access was achieved the group had individuals working for them (money mules) withdraw funds from Dutch-Bangla ATMs amounting to approximately $3 million.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078
TA505 Begins Summer Campaigns with A New Pet Malware Downloader, AndroMut, in the UAE, South Korea, Singapore, and the United States (July 2, 2019)
The financially-motivated threat group, “TA505,” has added a new downloader, called “AndroMut,” to their arsenal of malware and tools, according to Proofpoint researchers. Researchers note they have seen AndroMut referred to as another TA505 Remote Access Trojan (RAT) called “FlawedAmmyy,” which is based off the leaked source code of the legitimate remote access tool, “Ammyy.” Andromut is being distributed by TA505 via emails with macro-embedded attachments to recipients located in Singapore, South Korea, the UAE, and the US. Enabling the macro results in AndroMut being downloaded that is then used to download the FlawedAmmyy RAT for additional access to conduct malicious activity.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Execution through API - T1106 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
Mac Malware Pushed via Google Search Results, Masquerades as Flash Installer (July 2, 2019)
Intego researcher Joshua Long, has identified a new form of macOS-specific trojan, dubbed “OSX/CrescentCore,” infecting users in the wild. The malware is distributed on websites that impersonate Adobe Flash Player installers, some which users are redirected to via “high-ranking Google search results.” The malicious installers is actually an Apple disk image (.dmg) that will download the malware. Interestingly, different variants of OSX/Crescent were found to be capable of dropping Potentially Unwanted Programs (PUPs) such as Advanced Mac Cleaner and a malicious versions of the Safari web browser. The malware will install a LaunchAgent for additional persistence. As this writing, it is unclear what the objective is behind this malware, and it may be possible that actors are in the testing phase for a different malicious campaign.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Code Signing - T1116 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] User Execution - T1204
Google July Android Security Bulletin Fixes 3 Critical RCE Bugs (July 2, 2019)
As part of the July Android Security Bulletin, Google has released patches to address 12 vulnerabilities all rated as critical and high. In total Google issued patches for 21 vulnerabilities related to Qualcomm components used in Android devices, and other manufactures will continue to push out their own updates during this month. Three of the most dangerous, critical-rated vulnerabilities, registered as CVE-2019-2106, CVE-2019-2107, and CVE-2019-2109, reside in Android’s Media Framework and can be exploited via a custom-created file “to execute arbitrary code within the context of a privileged access.”
Click here for Anomali recommendation
Threat Spotlight: Ratsnif – New Network Vermin from OceanLotus (July 1, 2019)
ThreatVector researchers have published their findings on the usage of a Remote Access Trojan (RAT) suite dubbed “Ratsnif” used by the Advanced Persistent Threat (APT) group “OceanLotus” (APT32, CobaltKitty). The group was discovered to have used Ratsnif since at least 2016 with three out of the four analyzed samples created in 2016 and the fourth in late 2018. The Ratsnif samples have varying malicious capabilities including DNS poisoning, gateway/device ARP poisoning, HTTP injection, and MAC spoofing. At the time of this writing, it is unspecified how OceanLotus is distributing their Ratsnif malware, however, a common tactic used by APT groups is spearphishing so it is possible the malware is being distributed in this manner.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Network Service Scanning - T1046 | [MITRE ATT&CK] Network Sniffing - T1040 | [MITRE ATT&CK] System Information Discovery - T1082 | [MITRE ATT&CK] Transmitted Data Manipulation - T1493 | [MITRE ATT&CK] Uncommonly Used Port - T1065
Operation Tripoli (July 1, 2019)
A large-scale campaign has been distributing malware on Facebook for an unspecified number of years primarily targeting the country of Libya, according to Check Point researchers. The threat actors behind this campaign are utilizing the geopolitical and political pages themed around Libya that attempt to convince individuals to download malicious files. Researchers identified more than 30 Facebook pages distributing malicious links and some of the pages were found to have more than 100,000 followers. The objective of this campaign is to distribute malicious links and files, some of which are stored in services like Google Drive, or divert traffic to a compromised websites hosting the malicious files, infect a user, and steal sensitive information
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Scripting - T1064
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
MageCart Group
The threat group, “MageCart,” first emerged in 2015, according to RiskIQ and Flashpoint researchers. The umbrella term, MageCart, refers to groups that target online commercial websites and injects payment skimming scripts to illicitly obtain credit card credentials. The group is suspected to be several groups under the umbrella of MageCart, the name given to keep track of these financially-motivated groups and their malicious activity. RiskIQ and Flashpoint suggest that there are approximately six to seven groups with each group acting slightly different in their targeting, skimmer functionality, and infrastructure. Magecart will be referred to as a single entity for the purposes of this actor profile, unless specified otherwise.
TA505 The financially-motivated threat group called, “TA505,” was first reported on by Proofpoint researchers in December 2017. Malicious activity attributed to the Russian-speaking group dates back to at least 2014, and the campaigns conducted by TA505 have targeted entities and individuals around the world. The group distributes a variety of malware, both well-known strains (Dridex banking trojan, Locky ransomware), custom-created (Jaff ransomware, tRAT), and variants of legitimate remote access tools (Remote Manipulator System). The group primarily distributes malware and tools via large scale and indiscriminately-distributed malspam campaigns, often through the “Necurs” botnet, with malicious attachments or links. Incorporation of new malware, creating custom malware and the use of advanced tactics, such as the removal of malware artifacts, indicate that this group is a sophisticated threat and likely well-funded. The group is innovative and shows the flexibility to pivot to other techniques and malware trends on a global scale.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



