Weekly Threat Briefing: Massive Botnet Chews Through 20,000 WordPress Sites

The intelligence in this week’s iteration discuss the following threats: APT, Banking trojan, Botnet, BEC, Data theft, Malspam, Phishing, Targeted attacks, Threat group, Vulnerabilities and Website compromise. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Massive Botnet Chews Through 20,000 WordPress Sites (December 10, 2018)
The WordPress security company, “Wordfence,” found that unknown threat actors had managed to compromise approximately 20,000 WordPress websites. The actors compromised the websites by brute force-attacking administrator account credentials and were observed using the websites to create a large-scale botnet. The botnet was observed utilizing the remote procedure protocol “XML-RPC” which functions as an interface “that lets one piece of software make requests to another by sending it remote procedure calls (RPCs) written in the extensible markup language (XML).” The actors created a script that utilized XML-RPC in its brute force attacks to automatically generate username and password combinations. If a weak password is compromised and grants an actor access to the website, the actor then uses that website to target other WordPress website with brute force attacks.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110) | [MITRE ATT&CK] Connection Proxy (T1090)
DanaBot Evolves Beyond Banking Trojan with New Spam-Sending Capability (December 6, 2018)
The threat actors behind the “DanaBot” banking trojan have been testing out some new features in the malware, according to ESET researchers. The actors have been trying some new email address-stealing and malspam distribution techniques while targeting individuals located in Italy. The malspam technique is interesting in that the malware, once it has infected a machine, is capable of using the email accounts to propagate itself. DanaBot will look at an infected user’s email account and reply to existing emails with malspam. ESET researchers also believe that the actors behind DanaBot are cooperating with the group behind the “GootKit” trojan due to a VBS file found on a DanaBot Command and Control (C2) server that pointed to a GootKit downloader module.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] PowerShell (T1086)
Patch Now (If You Can!): Latest Android Update Fixes Clutch of RCE Flaws (December 6, 2018)
Android has released its December security bulletin to address 53 vulnerabilities, 11 of which are rated as “critical.” Out of those 11 critical vulnerabilities, five are Remote Code Execution (RCE) vulnerabilities. Google notes that, as of this writing, it has not observed that any of these vulnerabilities have been exploited in the wild. The vulnerabilities could be exploited by a remote actor by “using a specially crafted file to execute arbitrary code within the context of a privileged process.”
Click here for Anomali recommendation
More Data Joy: Email Scammers Are Buying Mark’s Info from Legit Biz Intelligence Firms (December 6, 2018)
Agari researchers have published a report in which they discuss their findings on a Business Email Compromise (BEC) campaign primarily targeting C-suite level executives, specifically, chief financial officers. The group behind this BEC campaign, dubbed “London Blue” because one of its members tagged himself in locations on Instagram, is believed to be a well-organized Nigerian group. Researchers believe that London Blue is separated into distinct groups, each of which have certain responsibilities such as: distributing the BEC emails, making the illicit bank transactions, and passing the money up the ladder to the primary actors. The group uses a database to store records for which they use “legitimate sales leads services” to find potential targets.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194)
Adobe Fixes Zero-Day Flash Player Vulnerability Used in APT Attack on Russia (December 5, 2018)
A vulnerability in Adobe’s “Flash Player” is reported to have been exploited in part of an Advanced Persistent Threat (APT) attack against Russia’s FSBI “Polyclinic #2,” according to Qihoo 360 researchers. The vulnerability, registered as “CVE-2018-15982,” was used to target the medical and cosmetic clinic by distributing, likely via email but the specific method is not mentioned, a malicious Word document with an embedded Flash object that poses as an employee questionnaire. A user is shown a warning when the exploit is triggered that states “The embedded content contained in this document may be harmful to your computer.” If the recipient agrees to the prompt, a file called “backup.exe” runs and infects the user with a backdoor that impersonates the “Nvidia Control Panel” application that uses a stolen certificate named “IKB SERVICE UK LTD.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Supply Chain Compromise (T1195)
Stolen Pencil Campaign Targets Academia (December 5, 2018)
A new spear phishing campaign, potentially attributed to the Democratic People’s Republic of Korea (DPRK), has been discovered to be targeting academic institutions since at least May 2018, according to ASERT researchers. The campaign, dubbed “STOLEN PENCIL,” consists of actors distributing spear phishing emails that contain a link to one of multiple domains controlled by the actors. Visiting the domain, a user would be prompted to download a “Font Manager” extension from the Chrome web store. The extensions had five star reviews from Google+ accounts compromised by the actors that were copied over from other reviews, some of which were negative but still gave five stars. The objective of the campaign is to use the extensions to steal data from the user when using various websites, and after gaining access to a system, using Microsoft’s Remote Desktop Protocol (RDP) to maintain persistence.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Remote Desktop Protocol (T1076)
Bloom is off the Rose: Canadian 1-800-FLOWERS Operation Discloses Four-Year Breach (December 4, 2018)
The Canadian company “1873349 Ontario, Inc.” has stated that the website for its retail operations “1-800-FLOWERS,” had its website compromised for at four least years. The website, “1800Flowers[.]ca,” was infected with information-stealing malware by unknown threat actors from August 15, 2014 to September 15, 2018. Any individuals who made purchases during this time may have had the information entered on the website stolen. The compromise was confirmed on October 30, 2018 when the company identified suspicious activity on its website. The information that could have stolen from the website customers includes: card security code, expiration date, name, and payment card number.
Click here for Anomali recommendation
New Ransomware Spreading Rapidly in China Infected Over 100,000 PCs (December 4, 2018)
Velvet Security researchers have found a previously unknown ransomware with password-stealing capabilities is targeting individuals located in China. The malware, as of this writing, has infected approximately 100,00 users who have downloaded applications that use the “EasyLanguage” programming language. The actors behind this campaign were able to add malicious code into the EasyLanguage programming software that was created to inject ransomware code “into every application and software product compiled through it.” Thus, any user who downloaded an affected application would be infected with ransomware that demands 110 yuan ($16 USD) to be sent to the actor’s “WeChat” account in three days for the decryption key.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise (T1195)
California-Based Professional Employer Organization Hacked by TheDarkOverlord; Thousands of Employees’ Files Stolen (December 4, 2018)
The threat group “TheDarkOverlord” (TDO), has claimed responsibility for compromising the professional employer organization “Prime Staff Inc,” according to the data breach website databreaches[.]net. The website reports that it received an email from an email address from Prime Staff, Inc. stating “HELP” above bodies of text that appeared to be from TDO. Databreaches attempted to find a way to communicate safely with the email sender and received a reply that said “There’s no safe way to contact Shields.” This response appears to indicate that TDO had gained complete control over Prime Staff’s systems. TDO engaged in tactics known for them: stealing company data and blackmailing the company into paying for their files back or risk them being destroyed. In addition, TDO also included some incentives by offering gradual decreases from the original ransom amount of $50,000, for referring other TDO victims to pay the group.
Click here for Anomali recommendation
KoffeyMaker: Notebook vs. ATM (December 4, 2018)
Kaspersky Lab researchers have published a report regarding and ATM-stealing toolkit, dubbed “KoffeyMaker,” after unnamed banks in Eastern Europe found their ATMs were attacked. KoffeyMaker utilizes a “black box” attack tactic, using a physical device connected to the machine, where the actor connects a laptop to the ATM. The actor was found to have opened the ATM, connected the laptop with ATM dispenser drivers installed on it along with a patched KDIAG tool, and closed the ATM. Remote access to the laptop was accomplished via “a connection to a USB GPRS modem” that was used to instruct the KDIAG tool to force the ATM to dispense cash.
Click here for Anomali recommendation
IBM Db2 Vulnerabilities Left IBM Database Installations at Risk of Hacks (December 4, 2018)
Two vulnerabilities have been addressed in IBM products. One vulnerability, registered as “CVE-2018-1987,” has been identified in IBM’s “IBM Db2” management software, according to researcher Eddie Zhu. This vulnerability could be exploited by a threat actor who has first obtained local user access to elevate privileges by running custom-crafted applications. Another vulnerability, registered as “CVE-2018-1723,” was found in IBM’s “Spectrum Scale” and “could allow a GPFS command line utility allows an unprivileged, authenticated user with access to GPFS node to read arbitrary files on this mode,” according to IBM’s advisory.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Bypass User Account Control (T1088)
The Evolution of BackSwap (December 3, 2018)
The threat actors behind the “BackSwap” banking trojan have regularly made changes to the malware over the past few months, according to Check Point researchers. BackSwap is written in assembly and was first discovered in May 2018 by Polish CERT researchers and Michal Poslusny from ESET. The malware is primarily distributed via legitimate programs such as FileZilla, Notepad++, and 7-Zip in which the actors have bundled the malicious code. If a malicious application is downloaded and run, only the BackSwap code will be executed and any legitimate code in the application will not. Researchers found that actors have been modifying BackSwap’s event interception techniques in regards to identifying URLs, to which the malware decrypts “a resource from its .rsrc section which turns out to be its web-injects.” The retrieved code checks the URL to see if it matches any banks that it targets and if so, uses the web injections to steal banking credentials.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Hooking (T1179) | [MITRE ATT&CK] Web Service (T1102)
Container Code Cluster-Fact: There’s a Hole in Kubernetes That Lets Miscreants Cause Havoc (December 3, 2018)
Co-founder of Rancher Labs, Darren Shepherd, found a privilege escalation vulnerability in the open source container orchestration software, “Kubernetes,” registered as “CVE-2018-1002105.” This vulnerability is rated as “critical” because a threat actor could exploit it remotely without any user interaction or specific privileges. Exploitation of the vulnerability could allow an actor to use the “Kubernetes API server to connect to a backend server to send arbitrary requests.” This could then allow actors to inject code, steal data, or shut down applications inside a target’s firewall.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
Jared, Kay Jewelers Parent Fixes Data Leak (December 3, 2018)
“Signet Jewelers,” the parent firm of the jewelry stores “Jared” and “Kay Jewelers,” has fixed a bug in its subsidiaries’ websites (jared[.]com and kay[.]com). The bug, identified in mid-November by web designer Brandon Sheehy, exposed Jared and Kay customer order information that was conducted through their respective websites. Sheehy discovered that he could alter the link sent in the confirmation email and paste it in a web browser which he found exposed a different customer’s order information. The exposed data consists of: billing address, customer order, delivery date, email address, items and total amount purchased, last name, and tracking link. Sheehy reached out to Signet about this issue but did not hear anything back for several weeks after which he reached out to KrebsOnSecurity. Signet chief information security officer, Scott Lancaster, has stated that this issue has now been fixed.
Click here for Anomali recommendation
Quora Hacked – 100 Million User’s Data Exposed (December 3, 2018)
The question and answer website “Quora” has issued a statement in which it confirms that its website was compromised. The website is reported to be the “95th largest website in the world” with approximately “700 million visits per month.” Quora discovered that the breach had occurred on November 30, 2018, and it is unknown at the time of this writing if the breach took place on that date or sometime prior. Regardless, this incident affects approximately 100 million of its users by threat actors accessing user data consisting of: data imported from linked networks (when authorized by users), email addresses, encrypted passwords, and names. Other exposed data includes public content and actions, as well as non-public content and actions such as direct messages. As of this writing, Quora does not know how threat actors gain unauthorized access to their systems.
Click here for Anomali recommendation
Observed Threats
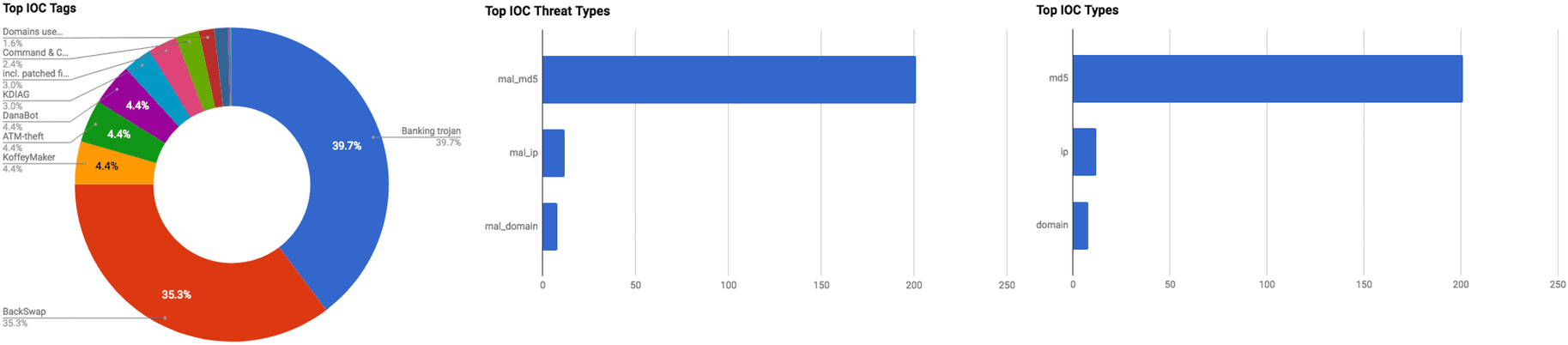
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial. Additional information regarding the threats discussed in this week’s Community Threat Briefing can be found below:
TheDarkOverlord TheDarkOverlord is a threat group that has been active since at least June 2016 when they started to list dumps for sale on the forum called “Real Deal Marketplace.” The group engages in extortion and data leaks of company data and Personally Identifiable Information (PII). The first incidents the group was involved in revolved around gaining access to healthcare organization servers, stealing information, and then demanding payment for not releasing the data. The data typically consists of PII and Protected Health Information (PHI). The group later expanded from solely targeting the healthcare industry to others such as education and finance, however, the group’s tactics remained the same; steal data and demand payment for not releasing it to open source locations.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



