Weekly Threat Briefing: New Credential Phish Targets Employees with Salary Increase Scam

The intelligence in this week’s iteration discuss the following threats: APT, Data leak, Phishing, PII, Targeted attacks, Vulnerabilities, and Zero day. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Chrome 0-day Exploit CVE-2019-13720 Used in Operation WizardOpium (November 1, 2019)
Security researchers from Kaspersky have discovered a new vulnerability in Google’s Chrome Browser, registered as “CVE-2019-13720”. Attacks using this zero-day are being referred to as “Operation WizardOpium”, and there is yet to be any clear evidence to link the attacks with known threat actors. The zero-day was exploited by placing malicious JavaScript code on a Korean-language news portal. The script loads a profiling script which checks if the victim is running Google Chrome version 65 or higher. If the Chrome version condition is met, then the script will make requests to the attacker controlled Command and Control (C2) server. These requests download encrypted chunks of exploit code. An image file will be sent as well with an embedded key to decrypt the final payload. Once the chunks are concatenated and payload decrypted, this will give the attacker a new piece of JavaScript code to exploit the browser. The focus of the exploit code is to undergo several operations which will allocate/free memory space which will give actors read/write capabilities. This is used to create an object that can be used to perform code execution for a shellcode payload.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Bypass User Account Control - T1088 | [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Custom Command and Control Protocol - T1094 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Execution through API - T1106
New Credential Phish Targets Employees with Salary Increase Scam (October 31, 2019)
A phishing campaign focused on collecting Office365 credentials of employees expecting pay raises has been discovered by the Cofense Phishing Defense Center (PDC). Threat Actors are creating fake emails pretending to be the company’s HR department. The actors did this by spoofing the “From” field in the headers to make it appear as if the email came from a company representative. The employee is advised to click an attachment for a which they believe will show an Excel spreadsheet detailing salary increases. It will actually redirect them and request to log into a fake Microsoft Office365 login page. This will then give the actor access to the employee’s email and be able to pursue other malicious activities depending on what can be found. This could include various pieces of Personally Identifiable Information (PII) that could be used for identity fraud and stealing employee money.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056)
MESSAGETAP: Who's Reading Your Text Messages? (October 31, 2019)
The Chinese Advanced Persistent Threat (APT) group, “APT 41” have recently started using a new malware variant named “MESSAGETAP” as discovered by FireEye Mandiant. MESSAGETAP is an espionage tool utilized by APT41 to observe and save Short Message Service (SMS) traffic from specific phone numbers. MESSAGETAP was discovered on a series of Linux servers that were operating as SMSC servers. Once installed on servers, MESSAGETAP will search for two files, “keyword_parm.txt” and “parm.txt”. These files are being used as commands for MESSAGETAP to focus on SMS messages and save their contents. These files are then deleted from the disk once the configuration files are loaded into memory. MESSAGETAP will now monitor all network communications coming in and out of the server collecting SMS message data which are then stored in a CSV file. The keyword list contains items of interest to Chinese intelligence. This includes political leaders, military and intelligence organizations and political movements that are against the Chinese Government.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Automated Collection - T1119 | [MITRE ATT&CK] System Network Connections Discovery - T1049
NHS Pagers are Leaking Medical Data (October 30, 2019)
Daley Borda, a security researcher discovered using an amatuer radio rig, that he was able to collect real-time medical and personal data of individuals. The information was being broadcasted by hospitals and ambulances from across the U.K. Daley realized that the communications were coming from the NHS’ use of pagers for communication. They are still being commonly used in hospitals since they work on low frequencies and can travel further and deeper inside large buildings, this is beneficial for hospitals due to thick walls protecting people from harmful radiation. The problem being that the main protocols used by pagers are not encrypted and be easily viewed.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE PRE-ATT&CK] Enumerate externally facing software applications technologies, languages, and dependencies (PRE-T1038) | [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Xhelper: Persistent Android dropper app infects 45K devices in past 6 months (October 30, 2019)
A new Android malware called “Xhelper”, has been found to be downloaded in excess of 45,000 times since March of this year and countries affected include India, Russia, and U.S.A, according to Symantec researchers. Xhelper has persistent capabilities to remain on the device even after it is uninstalled manually. With Xhelper’s command and control capabilities, it allows the threat actor to download and execute additional payloads. It is believed by Symantec researchers that the malware is still under development with many more functions not yet implemented.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exfiltration Over Command and Control Channel - T1041 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE MOBILE-ATT&CK] Standard Application Layer Protocol - T1437
Indian Nuke Plant’s Network Reportedly Hit by Malware tied to N.Korea (October 29, 2019)
A cyber attack on India’s Kudankulam Nuclear Power Plant has been reported to be linked to the North Korean malware “Dtrack”. This development comes from former analyst Pukhraj Singh of India's National Technical Research Organization (NTRO) which was then reported India's National Cyber Security Coordinator on September 4. Dtrack has been connected to North Korea’s Lazarus Group via another malware used by the group called “DarkSeoul”. it was used to to wipe hard drives in South Korean media companies and banks in 2013. The attack on the power plant used Windows SMB network drive share with hard-coded credentials to steal files. The attack did not focus on reactor controls but instead focused on research and technical data.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Automated Collection - T1119 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Bypass User Account Control - T1088
Details for 1.3 million Indian Payment Cards Put Up for Sale on Joker’s Stash (October 29, 2019)
Security researchers from Group-IB recently discovered that more than 1.3 million payment card details were put up for sale on one of the largest underground card selling shops, Joker’s Stash. It is believed from initial analysis that the card details were taken using skimming devices planted on ATMs or Point-of-Sale (POS) systems. There was no specific bank targeted due to the variety of cards being put for sale coming from multiple banks. Group-IB discovered that India made up 98% of all the credit card dumps, with Colombia banks being involved in 1% of the dump.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Russian Hackers Targeting Anti-Doping Agencies Ahead of 2020 Tokyo Olympics (October 29, 2019)
A Russian Advanced Persistent Threat (APT) group, Fancy Bear, has once again been attributed to a cyberattack targeting the World Anti-Doping Agency (WADA). Microsoft has observed an increase in highly-targeted cyberattacks by Russian state-sponsored threat actors targeting multiple anti-doping authorities and different sporting organizations from around the world. Fancy Bear is also known as APT28, Pawn Storm, Sandworm, Sednit, Sofacy, and Strontium. The attacks on these organisations come shortly after the World Anti-Doping Agency (WADA) found anomalies in a Russian database regarding its national anti-doping lab. The group targeted these organisations with multiple techniques including: brute force, exploiting internet-connected devices, spearphishing, and the use of open-source and custom malware.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Brute Force - T1110 | [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Communication Through Removable Media - T1092
Fashion Site Sixth June Leaking Card Data to Magecart Hackers (October 29, 2019)
RapidStrike security researcher “Jenkins” posted on Twitter to announce the discovery of card skimmers being implanted on the popular clothes retailer, “Sixth June”. Detailed analysis of the Magecart skimmer’s showed that would specifically look for website visitors’ credit card numbers, credit card owner names, CVV number, and expiration date. The technique of placing card skimmers on compromised ecommerce sites is common practice for threat groups tracked under the Magecart umbrella term. This skimmer unique because the malware does not collect details for non-U.S visitors or visitors who were running Linux. This infection of Sixth June follows similar attacks on retail outlets including the website of First Aid Beauty, a popular skin care brand.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Input Capture - T1056 | [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
UniCredit Bank Suffers "Data Incident" Exposing 3 Million Italian Customer Records (October 28, 2019)
The Italian banking and financial services company, UniCredit, announced that there has been a security breach in which the personal details of at least three million Italian customers was leaked. The compromised data included the names, cities, numbers and email addresses of said customers. UniCredit have not detailed publicly how the threat actors were able to compromise the Personal Identifiable information (PII) of these three million customers. but did state the attacker compromised a file created in 2015 containing the records of these customers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Largest Cyber-Attack in Georgia’s History Linked to Hacked Web Hosting Provider (October 28, 2019)
Georgia has stated that it was the target of the nation’s largest-recorded cyberattack in which over 15,000 websites were compromised. The attack impacted various banks, courts, newspapers, government agencies, and TV stations, with at least two television stations taken off the air. Following the attack, Pro-Service, a Georgian web hosting provider, announced they were the affected company. Pro-Service stated that the actor was able to breach its network and take down a significant number of customer websites. With this attack, actors replaced the original contents of the website with their own content. The attackers consistently posted images of former Georgian President Mikheil Saakashvili with the overlay text, “I’ll be back.”
Click here for Anomali recommendation
Observed Threats
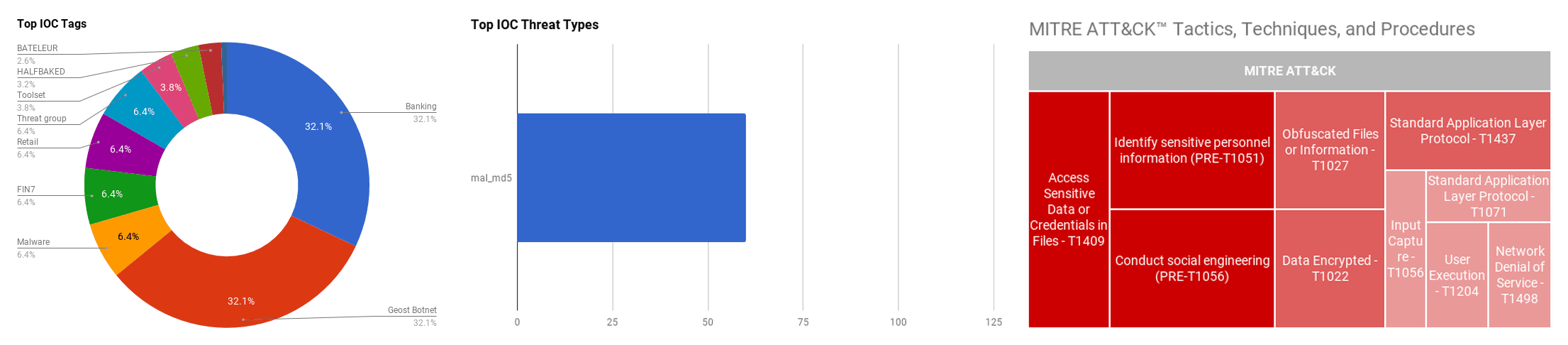
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
APT28 The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
MageCart The term, “MageCart,” first emerged in 2015, according to RiskIQ and Flashpoint researchers. The umbrella term, MageCart, refers to groups that target online commercial websites and injects payment skimming scripts to illicitly obtain credit card credentials. The group is suspected to be several groups under the umbrella of MageCart, the name given to keep track of these financially-motivated groups and their malicious activity. RiskIQ and Flashpoint suggest that there are approximately six to seven groups with each group acting slightly different in their targeting, skimmer functionality, and infrastructure. Magecart will be referred to as a single entity for the purposes of this actor profile, unless specified otherwise.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



