Weekly Threat Briefing: New SpeakUp Backdoor Infects Linux and macOS with Miners
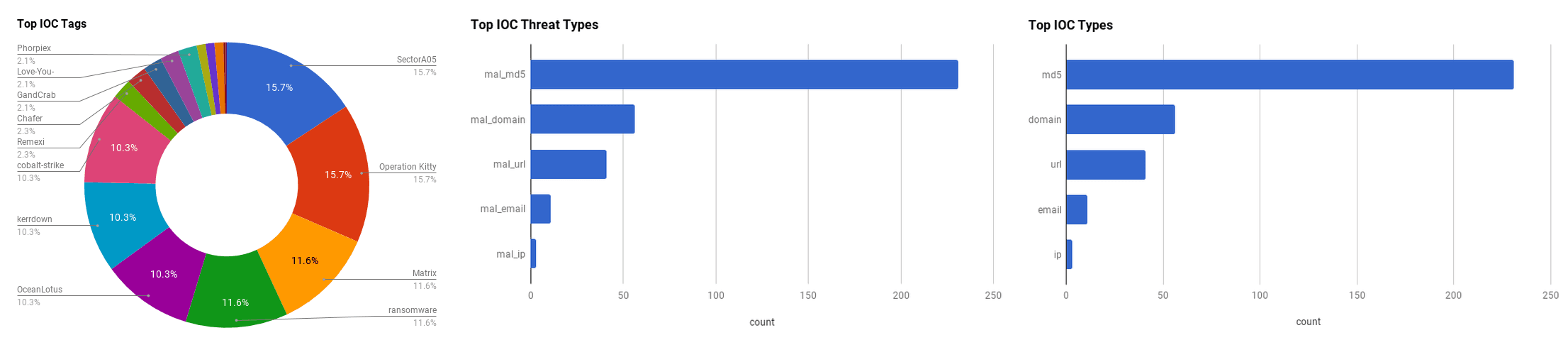

The intelligence in this weekís iteration discuss the following threats: APT32, APT39, Backdoors, CookieMiner, Cryptominers, Data breach, Malspam, Malware, Phishing, SectorA05, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
New SpeakUp Backdoor Infects Linux and macOS with Miners (February 4, 2019)
Check Point researchers have observed a malware campaign that has been distributing a new backdoor, dubbed ìSpeakUp.î The malware appears to be targeting Linux and macOS servers primarily based in Brazil, China, Columbia, Ecuador, India, Mexico, Paraguay, South Korea, amongst others. The malware uses a known vulnerability, ìCVE-2018-20062,î in the Chinese PHP framework ìThinkPHP,î that allows for remote code execution as the initial infection vector to install a Perl backdoor. Once it obtains access to the Linux or macOS server, it it contact its Command and Control (C2) server to relay the newly infected machineís information to it. The other vulnerabilities exploited in this campaign include: ìCVE-2012-0874,î a JBoss Enterprise Application Platform multiple security bypass, ìCVE-2010-1871,î a JBoss Seam Framework remote code execution (RCE), ìCVE-2017-10271,î an Oracle WebLogic wls-wsat Component Deserialization RCE, ìCVE-2018-2894,î a vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware, and ìCVE-2016-3088,î an Apache ActiveMQ Fileserver file upload RCE.
Click here for Anomali recommendation
Tracking OceanLotusí New Downloader, KerrDown (February 1, 2019)
Advanced Persistent Threat (APT) group, ìOceanLotusî (also known as APT32), has been observed utilising a new custom downloader family, named ìKerrDown,î according to researchers at Palo Alto Networks. The downloader can be distributed in one of two ways: a malicious Microsoft Office Document with macros, or a RAR archive containing a legitimate program with DLL side-loading. The document and RAR archive are both in Vietnamese which indicates the likely targets are Vietnamese-speakers. The malicious Word document and RAR archive will drop the KerrDown DLLs that install the final payload of the malware, which appears to be a variant of Cobalt Strike Beacon.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
TheMoon Rises Again, With a Botnet-as-a-Service Threat (January 31, 2019)
An Internet-of-Things (IoT) botnet, ìTheMoon,î that targets home routers and modems, has been observed to have a new module added to it that can allow it to be sold Software-as-a-Service (SaaS) to threat actors. TheMoon is a botnet that targets vulnerabilities in routers by ASUS, D-Link, GPON, Linksys, and MikroTik to brute-force credentials, obfuscate traffic, and, with the newest module, act as a SOCKS5 proxy. The botnet is capable of spreading like a worm, and has been observed to utilise up to six exploits at a time to increase its victim count. This iteration of the botnet allows the threat actor behind it to sell its proxy network as a service for other threat actors to utilise.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Connection Proxy (T1090)
Mac Malware Steals Cryptocurrency Exchangesí Cookies (January 31, 2019)
Palo Alto Networksí researchers have found a new strain of cryptocurrency mining malware that specifically targets macOS operating systems. The malware, dubbed ìCookieMiner,î is a variant of the ìOSX.DarthMinerî malware. The Malware initiates its attack with a shell script that targets macOS, and copies the Safari browserís cookies to a folder and uploads those to a remote server. It also targets Google Chrome with a python script that extracts saved credentials and credit card information from Chromeís local data storage. CookieMinerís is capable of installing the ìEmPyreî backdoor, mining cryptocurrency, in addition to stealing various forms of data. The data it aims to steal include: stealing cryptocurrency wallet data and keys, Google Chrome and Apple Safari browser cookies, iPhoneís text messages if backed up, saved credit card credentials in Chrome, and saved usernames and passwords in Chrome. The various forms of data the malware is capable of stealing may allow threat actors to bypass forms of multi-factor authentications. The malware mines for the ìKotoî cryptocurrency which is associated with Japan specifically.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] PowerShell (T1086)
Matrix Ransomware: A Threat to Low-Hanging Fruit (January 31, 2019)
Researchers from Sophos published a report, ìMatrix: A Low-Key Targeted Ransomware,î in which they discuss an unsophisticated malware called ìMatrixî that attempts to brute-force weak Remote Desktop Protocols (RDPs). Once it gains access into a system, the malware will use other RDPs to obtain persistence in the network and spread. Matrix bundles several payload executables into it to accomplish tasks, including free, legitimate system administrator tools. The ransom note that is presented to the infected user requests victims to email the attackers to find out the ransom amount as well as get their files back. The authors behind the malware initially request $2,500 in Bitcoin and increase the amount by $1,000 if the victim does not pay after the first 24 hour period. They then state that the private key to obtain the decryption key will be deleted if the user does not pay the ransom after 96 hours of the initial encryption.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Desktop Protocol (T1076) | [MITRE ATT&CK] Brute Force (T1110)
Chafer Used Remexi Malware to Spy on Iran-based Foreign Diplomatic Entities (January 30, 2019)
A campaign targeting foreign diplomatic entities in Iran has been observed to install the malware, ìRemexi,î according to researchers from Kaspersky Lab. The campaign is attributed to the Advanced Persistent Threat (APT) group, ìChafer.î It is unclear how the campaign is initiated, but once the malware is on a machine, it has the ability to keylog, take screenshots, obtain credentials, view logon and browser history, and execute remote commands. It establishes persistence in a network by utilising scheduled tasks and system registries.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060)
Indiaís Largest Bank SBI Leaked Account Data on Millions of Customers (January 30, 2019)
State Bank of India (SBI) suffered a data breach due to a misconfigured server that stored two months-worth of customer financial data from ìSBI Quick,î including bank balances and recent transactions. The server was not configured to be protected by a password, thus allowing anyone to be able to access information such as: bank account balances, partial bank account numbers, phone numbers, recent transaction, text messages to customers, and when a check had been cashed. According to the article, SBI Quick permitted: ìSBIís banking customers to text the bank, or make a call, to retrieve information back by text message about their finances and accountsÖ the service recognises the customerís registered phone number and will send back the current amount in that customerís bank account. The system can also be used to send back the last five transactions, block an ATM card and make inquiries about home or car loans.î The accessible database allowed anyone to see those messages in real-time. The database was secured following the disclosure of the misconfiguration.
Click here for Anomali recommendation
ìLove youî Malspam Gets a Makeover for Massive Japan-targeted Campaign (January 30, 2019)
Researchers from ESET discovered that a recent ìLove Youî malspam campaign has been modified to target users in Japan. The unknown threat actors used Japanese-relevant subject headers to entice users to open the email and extract the malicious .zip file in it. If a user opens the .zip folder, a JScript file will initiate the first-stage payload that downloads one or more final payloads: ìGandCrabî ransomware, an unspecified cryptominer, ìPhorpiex worm,î a system settings changer, and/or a locale-specific downloader that only downloads further payloads if the default language on an infected machine indicates the user is in Australia, China, Germany, Japan, South Korea, Turkey, the UK, or Vietnam.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
The Double Life of SectorA05 Nesting in Agora (Operation Kitty Phishing) (January 30, 2019)
The threat group, ìSectorA05,î has been observed conducting a phishing campaign against personnel of the South Korean government and cryptocurrency exchanges to install malware, according to researchers at Threat Recon. This campaign has been dubbed ìOperation Kitty Phishingî and the phishing emails purport to be related to ìthe Unification Ministry of South Koreaî and contains two .zip folders that contain an executable disguised as a Hangul Word Processor (HWP) file. The executable will execute two Remote Access Trojans (RATs) in the hopes at least one is not blocked by antivirus. Once one of the RATs is successfully downloaded, it will run reconnaissance on the machine, obtaining screen captures, keylog, and steal passwords. The goal of the infection appear to be to mine for cryptocurrency as well as steal information from the South Korean government.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Hooking (T1179) | [MITRE ATT&CK] Execution through API (T1106) | [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Spearphishing via Service (T1194)
APT39: An Iranian Cyber Espionage Group Focused on Personal Information (January 29, 2019)
Researchers from FireEye disclosed that they have identified a new Iranian Advanced Persistent Threat (APT) group, ìAPT39,î that has been observed stealing personal data from victims. Their targeted victims are based in several Middle Eastern countries, Spain, and the US, with specific focus upon Middle Eastern targets. This APT group focuses on victimising telecommunications and travel industries to monitor, track, and perform surveillance operations on specific individuals as well as aim to collect customer and commercial information for operational uses, and establish additional access vectors for future campaigns. APT39 utilises spear phishing emails with malicious attachments or links that result in ìPOWBATî malware infection. They leverage backdoors such as ìSEAWEED,î ìCACHEMONEY,î and a variant of ìPOWBATî to establish a presence in a network to obtain persistence and privilege escalation in the future.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Remote Access Tools (T1219)
New FaceTime Bug Lets Callers Hear and See You Without You Picking Up (January 29, 2019)
An unpatched bug in Appleís FaceTime application was discovered that allows a person initiating a call to hear or see the recipient before they accept the call. This could allow a user to call any iPhone number via FaceTime and eavesdrop, even when the call is not actively answered. The bug works on the latest iOS version: iOS 12.1.2, as well as macOS Mojave.
Click here for Anomali recommendation
Zero-Days in WordPress Plugin Actively Exploited (January 28, 2019)
The WordPress plugin, ìTotal Donations,î was found to be affected by several zero-day vulnerabilities that could allow unauthorised actors administrative access to affected WordPress sites, according to Wordfence. The plugin is intended to make receiving online donations easier and allow the site owner to view progress bars as well as manage tasks and campaigns. 88 unique AJAX actions can be accessed by unauthorised users, 49 of which can be exploited to see sensitive data and make unauthorised changes to a siteís content and configuration. The vulnerabilities are tracked as ìCVE-2019-6703.î The pluginís developers have yet to respond to security researchers contacting them, and no patch has been announced to be in the works.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
Analyzing Digital Quartermasters in Asia – Do Chinese and Indian APTs Have a Shared Supply Chain?
Anomali Labs recently analyzed a large number of weaponized RTF phishing files related to APT groups aligned with Chinese and Indian state interests. This analysis has identified a shared object dimension and shared obfuscation methods across weaponized RTF files utilized by the APT groups known as Sidewinder (Indian State Interests), Goblin Panda/Conimes (Chinese State Interests), Temp.Periscope/ APT40 / Leviathan (Chinese State Interests), and Temp.Trident / Dagger Panda & Nomad Panda / Icefog (Chinese State Interests). Both unique object dimensions and multiple shared obfuscation methods are visible in the RTF files which appear to be artifacts of a shared RTF phishing weaponizer. In addition to shared RTF properties, a distinct pattern of post-exploitation TTP’s is shared between the APT groups aligned with China, whereas a unique post-exploitation execution chain can be seen in Sidewinder APT campaigns. The use of a common RTF phishing weaponizer alongside distinct post-exploitation TTPs introduces the possibility that Chinese and Indian APTs may have an overlapping supply chain for the acquisition of exploits and phishing weaponizers. However, after these tools are acquired a distinct and complex network of APT digital quartermasters may determine how these tools are equipped with payloads and deployed in distinct operations.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



