Weekly Threat Briefing: Notorious MyDoom Worm Still on AutoPilot After 15 Years
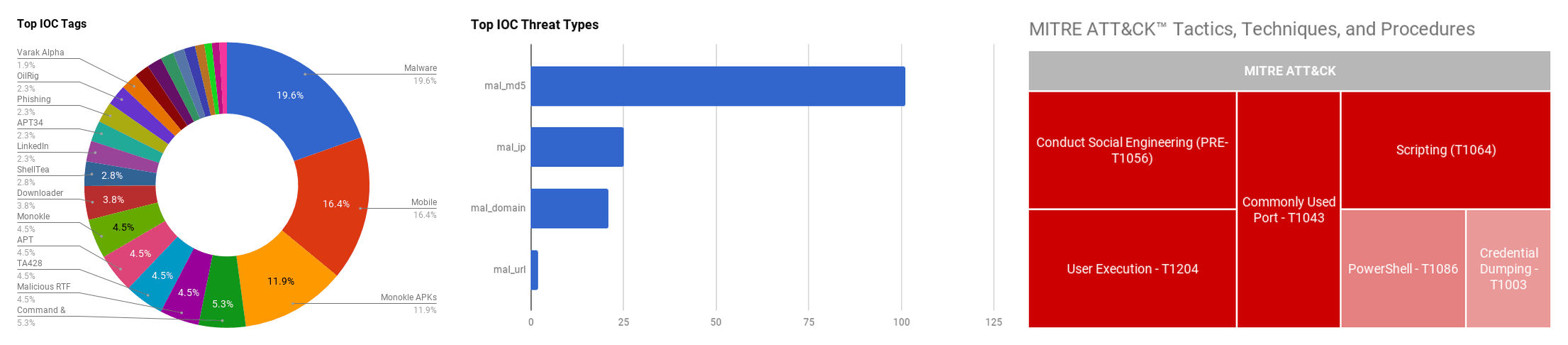

The intelligence in this week’s iteration discuss the following threats: APT, Data exposure, Malspam, Phishing, Ransomware, Targeted attacks, Threat groups, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
200 Million Enterprise, Industrial, and Medical Devices Affected by RCE Flaws in VxWorks RTOS (July 29, 2019)
Armis researchers have discovered 11 vulnerabilities in the real-time operating system, “VxWorks,” that is used by over 200 million devices. VxWorks is used by organizations in the industrial and medical sectors and is utilized by numerous types of devices and equipment such as elevators, firewalls, industrial controllers, patient monitors, printers, MRI machines, and VOIP phones. Six of the vulnerabilities can result in Remote Code Execution (RCE) and are registered as CVE-2019-12256, CVE-2019-12255, CVE-2019-12260, CVE-2019-12261, CVE-2019-12263, and CVE-2019-12257. The other five vulnerabilities can result in denial-of-service, information exposure, and logical errors are registered as CVE-2019-12258, CVE-2019-12262, CVE-2019-12264, CVE-2019-12259, and CVE-2019-12265. At the time of this writing, no observations of these vulnerabilities have been identified in the wild.
Click here for Anomali recommendation
Brazilian Financial Service Exposed 250GB of Local Banks’ Customer Data via Unsecured Server (July 28, 2019)
An unsecured server owned by an unnamed Brazilian financial service provider and containing approximately 250GB of data has been identified, according to Data Group researchers. The data consisted of Personally Identifiable Information (PII) including scanned ID cards, social security numbers, and documents related to proof of address and service request forms. Researchers found that a majority of the data belonged to customers of Banco Pan, and the bank has stated that the server and the information is managed by a commercial partner in response.
Click here for Anomali recommendation
Notorious MyDoom Worm Still on AutoPilot After 15 Years (July 26, 2019)
A prolific malware strain dating back to 2004 called “MyDoom” has been found to still be automatically conducting its malicious activity. MyDoom is distributed via email with malicious attachments or links, or directly through peer-to-peer connections. Once a machine has been infected, the malware will open TCP ports 3127 and 3198 to grant threat actors remote access for additional malicious purposes. The malware’s automatic features are conducted after infection by collecting email addresses from a user and then send itself to the addresses with an attached copy of itself.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Automated Collection - T1119
GandCrab Doppelgänging His Shell (July 25, 2019)
EnSilo researchers have a new downloader, dubbed “TxHollower,” that uses a variation of the Process Doppelgänging technique. Process Doppelgänging “involves replacing the memory of a legitimate process, enabling the veiled execution of malicious code that may evade defenses and detection,” according to MITRE. Analysis of the now defunct GandCrab ransomware led to the discovery of seven versions of TxHollower. The downloader is a shellcode that “in contrast to the original technique [Process Doppelgänging], instead of using an existing executable on disk a new file [is] created inside the transaction in %TEMP% folder.” TXHollower is used by over 20 different malware families and is likely distributed in a variety of ways such as malspam and malvertising, among others
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Security Software Discovery - T1063
Chinese APT “Operation LagTime IT” Targets Government Information Technology Agencies in Eastern Asia (July 24, 2019)
An Advanced Persistent Threat (APT) email campaign has been targeting government agencies in Eastern Asia since early 2019, according to Proofpoint researchers. The campaign, dubbed “Operation LagTime IT,” consists of threat actors distributing malicious Rich Text Format (RTF) documents to government entities associated to various sectors including: domestic affairs, economic development, foreign affairs, information technology, and political process. The RTF documents are distributed in attempts to exploit a Microsoft Equation Editor vulnerability registered as CVE-2018-0798. Analysts attribute this activity to a Chinese APT group dubbed, “TA428.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071
This Android Malware Can Take Photos and Videos and Spy on You App History (July 24, 2019)
A new custom malware, dubbed “Monokle,” is being utilized by unknown threat actors to conduct surveillance on chosen individuals, according to Lookout researchers. Monokle functions as a Remote Access Trojan (RAT) that has multiple malicious capabilities such as keylogging, taking photos/video, tracking user location, and stealing application and web browser history, among others. The malware will install trusted certificates to gain root access to the device that allows Monokle to further conduct its theft and monitoring functionalities. Researchers believe that Monokle has been active since at least 2016 with its activity consisting of small bursts targeting individuals in the Caucasus region. The Lookout infrastructure has been connected to the Russian company Special Technology Centre based in St. Petersburg. While this activity is targeting Android users, researchers have also identified iOS components in the malware, likely indicating that targeting iOS is under development or may be already underway.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE MOBILE-ATT&CK] Abuse Accessibility Features - T1453 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Install Root Certificate - T1130 | [MITRE ATT&CK] Audio Capture - T1123 | [MITRE MOBILE-ATT&CK] Premium SMS Toll Fraud - T1448 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Credential Dumping - T1003
Stock Trading App Robinhood Says User Passwords were Readable on Internal Systems (July 24, 2019)
The stock-trading application “Robinhood” has confirmed that its security team detected on July 22, 2019 that the application was storing usernames and associated passwords in plain text inside the company’s systems. A spokesperson for Robinhood stated that customers who may be affected by this incorrect data storage were notified by email and that, as of this writing, it appears that the data was not accessed by anyone who was unauthorized.
Click here for Anomali recommendation
Iranian Threat Group Targets LinkedIn Users (July 23, 2019)
The Iranian Advanced Persistent Threat (APT) group “APT34,” (also known as OilRig), has once again been found to be conducting malicious activity on the social networking site, LinkedIn, according to FireEye researchers. The threat actors created LinkedIn profiles pretending to a member of Cambridge University to distribute malicious documents. These malicious documents were found to be infecting users with APT34’s custom credential-stealing malware “PICKPOCKET.” Researchers also identified three new malware families the group has added to their arsenal dubbed “LONGWATCH” (keylogger), “ToneDeaf” (backdoor), and “VALUEVAULT” (credential stealer).
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Credential Dumping - T1003 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Valid Accounts - T1078
Discovering BADHATCH and a Detailed Look at FIN8’s Tooling (July 23, 2019)
The financially-motivated threat group “FIN8,” which was first identified by FireEye researchers in 2016, have added a new tool to their malicious arsenal, according to Gigamon researchers. The new tool, dubbed “BADHATCH,” is likely distributed through malspam emails and is capable of reverse shell functionality and transferring files. The emails contain Microsoft Word document attachments with malicious macros that, once enabled, will execute a PowerShell command to begin the BADHATCH infection process. Researchers believe that malspam email is likely the initial infection method, however, as of this writing they were unable to retrieve a document sample.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Data Staged - T1074 | [MITRE ATT&CK] Data from Local System - T1005 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] Custom Command and Control Protocol - T1094 | [MITRE ATT&CK] Custom Cryptographic Protocol - T1024 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Multiband Communication - T1026 | [MITRE ATT&CK] Remote File Copy - T1105 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] Standard Cryptographic Protocol - T1032 | [MITRE ATT&CK] Uncommonly Used Port - T1065 | [MITRE ATT&CK] Access Token Manipulation - T1134 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Execution Guardrails - T1480 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] File Permissions Modification - T1222 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Process Injection - T1055 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] Network Share Discovery - T1135
Multistage Attack Delivers BillGates/Setag Backdoor, Can Turn Elasticsearch Databases into DDoS Botnet “Zombies” (July 23, 2019)
Threat actors are targeting Elasticsearch servers with the objective of installing backdoors that use the infected hosts for a larger botnet used to conduct Distributed Denial-of-Service (DDoS) attacks. The actors behind this campaign are scanning the internet for publicly accessible Elasticsearch servers to exploit a previously-patched vulnerability, registered as “CVE-2017-1427,” located in the Groovy scripting engine. CVE-2015-1427 affects Elasticsearch. Post exploitation, the “Setag” backdoor is installed that is capable of stealing system information and launching DDoS attacks. Setag is also capable of exploiting a vulnerability in Apache Struts 2 registered as CVE-2017-5638 and appears to be similar to “BillGates” malware which is also capable of hijacking systems and DDoS attacks.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Indicator Removal on Host - T1070 | [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] Data Encoding - T1132
BrushaLoader Still Sweeping Up Victims One Year Later (July 22, 2019)
Proofpoint researchers have published their research conducted on the downloader called “BrushaLoader” and found that malware actors are utilizing this tool in attempts to be more stealthy in their malicious operations. BrushaLoader, which first appeared in June 2018, is distributed malspam emails with containing malicious attachments, typically compressed VBS attachments. The malware is used by threat actors to download other payloads onto an infected machine, taking advantage of the fact that BrushaLoader has relatively effective in previous campaigns.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] PowerShell - T1086
GandCrab Out – Sodinokibi In! Meet The New Sodinokibi Ransomware (July 22, 2019)
The Ransomware-as-a-Service (RaaS) called “Sodinokibi,” was discovered approximately three months ago and since then it appears that it is filling the void left by now defunct RaaS called GandCrab. Researchers believe that Sodinokibi is more advanced than GandCrab and is distributed via exploitation of an Oracle WebLogic vulnerability, (CVE-2019-2725), malspam and phishing emails with links and/or attachments, malvertisements leading to the RIG exploit kit, and compromised managed service providers. An infected machine will have its desktop picture changed to a notice of file encryption and provides a ransom notice to pay approximately $1,300 USD (0.13490081 bitcoins) for the decryptor.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Third-party Software - T1072 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Commonly Used Port - T1043 | [MITRE ATT&CK] User Execution - T1204 | [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056)
ProFTPD Remote Code Execution Bug Exposes Over 1 Million Servers (July 22, 2019)
The publicly-available and cross-platform FTP server, “ProFTPD,” is affected by a Remote Code Execution (RCE) vulnerability, registered as “CVE-2019-12815,” that puts over one million servers at risk. The vulnerability was identified by security researcher Tobias Mädel and reported to ProFTPD in September 2018. A temporary fix was issued on July 17 , however, no official patch has been issued.
Click here for Anomali recommendation
Critical RCE Flaw in Palo Alto Gateways Hits Uber (July 22, 2019)
Researchers identified an interesting Remote Code Execution (RCE) vulnerability located in Palo Alto Networks’ GlobalProtect portal and GlobalProtect Gateway security software products. The critical-rated vulnerability, registered as “CVE-2019-1579,” could be exploited by a threat actor by sending a custom-created request to a vulnerable system to allow the remote execution of arbitrary code. Interestingly, while CVE-2019-1579 was still unknown it was unintentionally fixed in later versions of GlobalProtect. The vulnerability affects the following PAN versions: PAN-OS 7.1.18 and earlier, PAN-OS 8.0.11 and earlier, and PAN-OS 8.1.2.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
OilRig The Advanced Persistent Threat (APT) group “OilRig” is believed to be an Iranian-based group that has been active since at least 2014. OilRig conducts cyber espionage operations focused on reconnaissance that benefits Iranian nation-state interests. OilRig uses a mix of public and custom tools to primarily target entities located in the Middle East.
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



