Weekly Threat Briefing: Planet Hollywood Owner Suffers Major POS Data Breach
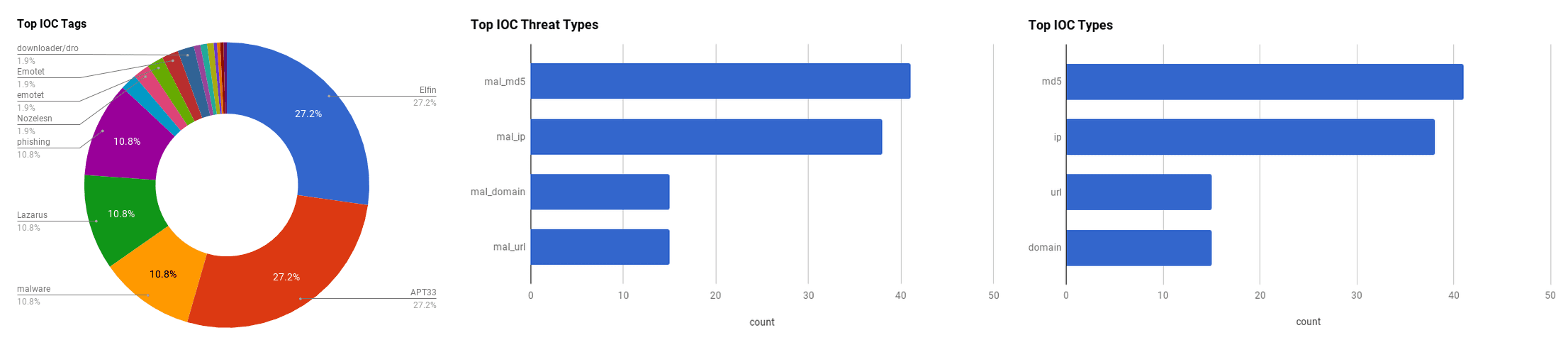

The intelligence in this weekís iteration discuss the following threats: Cryptocurrency, Data breach, Elfin, Emotet, Gustuff, Lazarus, Magento, Malware, Misconfigured databases, Ransomware, Trojans, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Planet Hollywood Owner Suffers Major POS Data Breach (April 1, 2019)
Earl Enterprises, the parent company of several restaurants including Planet Hollywood and Buca di Beppo, announced that they have suffered a data breach. The company stated that their Point-of-Sales system was affected and that customer payment card data was breached for over 10 months between May 23, 2018, and March 18, 2019. Allegedly, online orders and transactions conducted via third-party applications or platforms were not affected. At the time of this writing, it is unclear how many customers have been affected, but it is suspected to be over two million. Many of the breached card credentials were discovered on the card forum, "Joker's Stash."
Click here for Anomali recommendation
Emotet-Distributed Ransomware Loader for Nozelesn Found via Managed Detection and Response (March 29, 2019)
The banking trojan, "Emotet," has been observed distributing the "Nymaim" malware onto infected devices, according to researchers from Trend Micro. Emotet is distributed through phishing emails containing a malicious Word document that is downloaded via a web browser, in the observed instance, Google Chrome. Once opened, it will run a PowerShell script that ultimately downloads Emotet. It will then connect to the Command and Control (C2) server to obtain instructions to download more malware, specifically Nymaim, to execute on the system.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
Critical Magento SQL Injection Vulnerability Discovered ñ Patch Your Sites (March 29, 2019)
Magento released new versions of its content management software to address 37 security vulnerabilities in it. Most of the vulnerabilities could only be exploited by authenticated users, but one vulnerability could allow for a SQL injection by an unauthenticated remote threat actor. The vulnerability, labeled as "PRODSECBUG-2198" by Magento, could allow a threat actor to obtain sensitive information from databases of vulnerable e-commerce sites including administrative sessions and password hashes. The affected versions of Magento include Magento Open Source prior to 1.9.4.1, Magento Commerce prior to 1.14.4.1, Magento Commerce 2.1 prior to 2.1.17, Magento Commerce 2.2 prior to 2.2.8, and Magento Commerce 2.3 prior to 2.3.1.
Click here for Anomali recommendation
Desktop, Mobile Phishing Campaign Targets South Korean Websites, Steals Credentials Via Watering Hole (March 28, 2019)
Researchers from Trend Micro discovered a phishing campaign targeting South Korean websites via watering holes on those compromised sites. The campaign, dubbed "Soula," collects information from a spoofed login screen of a popular South Korean search engine to obtain credentials of a user. That information is sent to the threat actor's Command and Control (C2) server. At the time of the article's writing, it appears that the threat actors are just storing the data to gather information and research, likely before conducting a further campaign using the obtained information.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
UNNAM3D Ransomware Locks Files in Protected Archives, Demands Gift Cards (March 28, 2019)
BleepingComputer became aware of a new ransomware called "Unnam3d R@nsomware," that is encrypting a user's files into a password-protected RAR archive file and demands a $50 USD Amazon gift card code to decrypt the files. The ransomware is distributed via fake Adobe Flash Player update phishing emails, and once it gets onto a system it will begin moving files in the Documents, Pictures, and Desktop folders of a drive into individual RAR archives. A ransom note will pop up stating that a user needs to purchase an Amazon gift card code before receiving their files back. According to the unknown threat actors, they request the gift card code to then sell to other customers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Scripting (T1064)
Android Trojan Exploits Accessibility Services for the Disabled to Autofill Forms (March 28, 2019)
A new Android trojan, "Gustuff," has been discovered by researchers from Group-IB that utilises a mobile phone's Accessibility Services to autofill banking applications amongst others. It is initially distributed via a text message with a link to a malicious Android Package file (APK) and if clicked, it installs the trojan and interacts with the user's Accessibility Services to communicate with other applications. The trojan targets banking applications, cryptocurrency, fintech, marketplaces, online stores, and payment systems such as PayPal and eBay. Gustuff can display fake notifications with the legitimate icons of an application that allows for either a fake pop-up window for the user to enter the requested personal or payment details, or the legitimate application opens and auto fills the payment field using Accessibility Services to make illicit transactions. Gustuff can also send information about the infected device to a Command and Control (C2) server, read and send text messages, send USSD requests, launch SOCKS5 Proxy, follow links, transfer files to the C2, and reset the device to factory settings.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE MOBILE-ATT&CK] Malicious SMS Message (MOB-T1057) | [MITRE MOBILE-ATT&CK] Access Contact List (MOB-T1035) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
Cisco Bungled RV320/RV325 Patches, Routers Still Exposed to Hacks (March 28, 2019)
Cisco recently released patches for two registered router vulnerabilities, "CVE-2019-1652" and "CVE-2019-1653," did not properly fix the vulnerabilities and can still allow threat actors to exploit them. The two vulnerabilities, which have been exploited in the wild, could allow an unauthorised remote actor to obtain sensitive router configuration information in models "RV320" and "RV325," as well as execute code without a password. The patch Cisco released only blacklisted "curl," a command-line tool for transferring data online, but still could allow an actor to use non-curl scanners and exploit tools to manipulate the vulnerabilities. The company has acknowledged the problem, but has yet to announce a timeline for the new patch.
Click here for Anomali recommendation
Elfin: Relentless Espionage Group Targets Multiple Organizations in Saudi Arabia and U.S. (March 27, 2019)
Researchers from Symantec observed the Iranian Advanced Persistent Threat (APT) group, "Elfin," (also known as APT33) to be exploiting a registered vulnerability (CVE-2018-20250) in "WinRAR" to attack various organisations. Elfin is known to target Middle Eastern countries, specifically Saudi Arabia, as well as the United States, and sectors such as chemical, consulting, engineering, finance, governmental, manufacturing, research, telecoms, and several others. The attack with the WinRAR vulnerability targeted Saudi Arabian chemical organisations through phishing emails that allowed remote code execution on the infected computer once opened. The APT group is known for utilising both custom and open-sourced malware tools, and was linked to the malware, "Shamoon."
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Network Sniffing (T1040) | [MITRE ATT&CK] System Information Discovery (T1082) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Exfiltration Over Alternative Protocol (T1048)
Hackers Abuse Magento PayPal Integration to Test Validity of Stolen Credit Cards (March 27, 2019)
Threat actors have been observed to be exploiting a feature in Magento-supported PayPal "Payflow Pro" integration that is used in online stores to test the validity of stolen payment card numbers. Threat actors test the cards by attempting numerous transactions of $0 USD to see if the transactions are approved. This has been exploited in the wild, and affects stores using the PayPal Payflow Pro integration in Magento versions 2.1.x and 2.2.x.
Click here for Anomali recommendation
Cryptocurrency Businesses Still Being Targeted by Lazarus (March 26, 2019)
Researchers at Kaspersky Lab discovered a new phishing campaign conducted by Advanced Persistent Threat (APT) group, "Lazarus Group," that has been targeting South Korean cryptocurrency professionals. The phishing Korean Hangul Word Processor (HWP) document purported to be either a "Sample document for business plan evaluation of venture company" or a business overview from the Chinese technology consulting organisation, "LAFIZ." Both documents requested macros to be enabled to be viewed properly, and if allowed, would install malware on the user's machine. The malware is suited for both Windows operating systems and Mac operating systems.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] System Information Discovery (T1082) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
Family Tracking App Spilled Pics, Names and Real-time Location Data (March 26, 2019)
The geolocation tracking application, "Family Locator," was discovered to have an unsecured and unencrypted MongoDB database that could allow anyone to view all the data every registered member stored in the application. Sanyam Jain, a researcher for the GDI Foundation found that the database stored information including user's real-time location, email address, name, password, profile photo, as well as the name of the places that were geofenced according to their account which were all publicly accessible. 238,000 users were impacted by this. Microsoft, who hosted the database, took it offline after being notified.
Click here for Anomali recommendation
Apple Fixed Some Interesting Bugs in iOS and macOS (March 26, 2019)
Apple has released security updates for several applications including iCloud, iTunes, iOS, macOS, Safari, tvOS, and Xcode. Over eleven different registered vulnerabilities were patched in this update. Registered vulnerability, "CVE-2018-4461," which allowed for kernel-level memory corruption, was fixed in the Xcode software. The new iOS 12.2 update fixed seven different registered vulnerabilities such as flaws that allowed for malicious applications/websites to access a device's microphone without indication (CVE-2019-8566 and CVE-2019-6222), two flaws that could allow a malicious application to obtain root privileges (CVE-2019-8565) or overwrite arbitrary files (CVE-2019-8521), a flaw in the GeoServices component (CVE-2019-8553) that could lead to arbitrary code execution, a vulnerability in Mail, (CVE-2019-7284) that could lead to signature spoofing, and a vulnerability in Safari (CVE-2019-8554) that would allow a website to access sensor information without user consent. This update patched over 14 different registered vulnerabilities in total.
Click here for Anomali recommendation
FEMA Exposed 2.3 Million Disaster Victims' Private Data (March 25, 2019)
The US Federal Emergency Management Agency (FEMA) inadvertently shared 2.3 million records of disaster survivors' Personally Identifiable Information (PII) with an unnamed contractor, according to the Department of Homeland Security OIG report released on March 15, 2019. At the time of this writing, FEMA's Joint Assessment Team and the Office of the Chief Information Officer are currently auditing the contractor to assess if the data was further exposed. Thus far, FEMA's investigators have found that the contractor only held their network logs for 30 days of which investigators found no evidence of a breach. However, investigators did identify that the contractor's network contained 11 unspecified vulnerabilities of which four have been mitigated. The exposed records contained information such as: bank transit number, city name, electronic funds transfer number, financial institution name, street address, and zip code. Other information such as birth dates, names, and the last four digits of Social Security Numbers is data that FEMA is allowed to share with contractors.
Click here for Anomali recommendation
Bugs in Grandstream Gear Lay Open SMBs to Range of Attacks (March 25, 2019)
Several vulnerabilities have been discovered in various network products from Grandstream that could allow for remote code execution (RCE) by unauthorised users, the installation of malware, and eavesdropping on the devices. If a threat actor is able to compromise a device such as an IP PBX, conferencing gear, or an IP phone, via one of the vulnerabilities, they could then scan the device and the network it is on, install Remote Access Trojans (RATs), access the microphone or camera on said device, and spread within the network. This has the potential to be extremely dangerous for organisations, as an actor could use the vulnerabilities to spy on confidential company calls in boardrooms, record conversations in office rooms, take photos via the camera, and others.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Install and configure hardware, network, and systems (PRE-T1113) | [MITRE PRE-ATT&CK] Upload, install, and configure software/tools (PRE-T1139)
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



