Weekly Threat Briefing: Russian State Hackers Phish Euro Governments Ahead of Elections

The intelligence in this weekís iteration discuss the following threats: APT28, APT32, Cryptominer, FIN7, IoT, MageCart, Phishing, Ransomware, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Operation ShadowHammer (March 25, 2019)
Kaspersky Lab GReAT researchers have published a report detailing a new supply chain attack dubbed "Operation ShadowHammer." The attack targeted the "ASUS" computer hardware company's "ASUS Live Update" software to distribute malware to thousands of machines. Kaspersky found approximately 57,000 instances of its customers had unwittingly downloaded a backdoor onto their machines via a compromised version of ASUS Live Update. The number of infected machines is likely far higher because Kaspersky only has visibility on users who are using their software. Threat actors were able to compromise an ASUS server responsible for distributing updates some time between June and November 2018. The objective of this attack "was to surgically target an unknown pool of users, which were identified by their network adapters' MAC address. To achieve this, the attackers had hardcoded a list of MAC addresses in the trojanized samples and this list was used to identify the actual intended targets of this massive operation." The campaign was not discovered until January 2019 and the largest number of users infected with the malicious update appear to be located in Russia, followed by Germany, France, Italy, and the United States. Researchers believe that this operation may have been conducted by the APT group "BARIUM" due to a previous supply chain attack that distributed a backdoor.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise (T1195) | [MITRE PRE-ATT&CK] Identify supply chains (PRE-T1023)
Fake CDC Emails Warning of Flu Pandemic Push Ransomware (March 21, 2019)
MyOnlineSecurity researchers have found a phishing email that purports to be from the "Centers for Disease Control and Prevention" (CDC) concerning a "Flu pandemic warning." The email claims that influenza infections are "severely elevated," and that 20,000 people have been killed by the flu with an additional 220,000 people being "urgently hospitalized." The email advises a recipient to view the attached Microsoft Word document called "Flu pandemic warning." Opening the document will cause a user to be prompted to "Enable Editing" or "Enable Content" to properly view it. Enabling content will launch a malicious macro that begins the infection process for the "GandCrab v5.2" ransomware.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Scripting (T1064)
Russian State Hackers Phish Euro Governments Ahead of Elections (March 21, 2019)
Two threat groups believed to be sponsored by the Russian Federation government, Advanced Persistent Threat (APT) group "APT28" and the "Sandworm Team," have been found to be targeting NATO member countries and European countries, according to FireEye researchers. The researchers claimed that the groups are distributing spear phishing emails to said entities with the objective of stealing governmental credentials by directing email recipients to a fake login page to government portals. The two groups' spear phishing campaigns appear to be coordinated except that the Sandworm Team tends to utilize open source tools while APT28 uses customized tools. While this malicious activity is taking place prior to the European Parliament election (May 23-26, 2019), it is yet to be confirmed that the objective of these groups is to gather information about the election.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Spearphishing for Information (PRE-T1174) | [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE ATT&CK] User Execution (T1204)
Fake or Fake: Keeping Up With OceanLotus Decoys (March 20, 2019)
ESET researchers have observed the Advanced Persistent Threat (APT) group "OceanLotus," also known as APT32, to have begun incorporating self-extracting archives to run their malicious code. The group was also found to be utilizing a memory corruption vulnerability in Microsoft Office, registered as "CVE-2017-11882," in their phishing campaigns. Proof-of-concept code for CVE-2017-11882 is publicly available so even less-sophisticated groups have a higher likelihood to attempt to utilize the exploit. The objective of the group's phishing campaign, first observed in January 2019, is to deliver malicious documents, or documents that contain malicious macros, that utilizes the Office vulnerability. Other email attachments were found to install an information-stealing backdoor on the recipients machine.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Spear phishing messages with malicious links (PRE-T1146) | [MITRE PRE-ATT&CK] Spear phishing messages with malicious attachments (PRE-T1144) | [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Regsvr32 (T1117) | [MITRE ATT&CK] Service Execution (T1035) | [MITRE ATT&CK] New Service (T1050) | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060) | [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Binary Padding (T1009) | [MITRE ATT&CK] DLL Side-Loading (T1073) | [MITRE ATT&CK] Modify Registry (T1112) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Timestomp (T1099) | [MITRE ATT&CK] File and Directory Discovery (T1083) | [MITRE ATT&CK] Query Registry (T1012) | [MITRE ATT&CK] System Information Discovery (T1082) | [MITRE ATT&CK] Data Compressed (T1002) | [MITRE ATT&CK] Data Encrypted (T1022) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041) | [MITRE ATT&CK] Exploitation for Client Execution (T1203) | [MITRE ATT&CK] Custom Command and Control Protocol (T1094) | [MITRE ATT&CK] Uncommonly Used Port (T1065)
FIN7 Revisited: Inside Astra Panel and SQLRat Malware (March 20, 2019)
The financially-motivated threat group "FIN7" has added new malicious tools to its arsenal since three reported leaders of the group were indicted in August 2018, according to Flashpoint researchers. The group has been attributed to activity that is believed to have begun in January 2018. FIN7 has added a new attack panel called "Astra," that is written in PHP and includes a script-management system that can distribute malicious scripts to compromised machines. The group has also incorporated two new malware families. One of which, dubbed "SQLRat," is distributed via malicious documents, likely through phishing, and is capable of dropping files and executing SQL scripts on an infected host. The second malware, called "DNSbot," is used to "exchange commands and push data to and from compromised machines." In addition, the group was also found to use a customized version of "TinyMet" called "TiniMet," which is a variant of the open source DLL injection stager, "Meterpreter." The threat group uses daily scheduled tasks to maintain persistence with the overall objective to steal financial data.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Custom Command and Control Protocol (T1094) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] File Deletion (T1107)
Consumers May Lose Sleep Over These Two New Magecart Breaches (March 20, 2019)
RiskIQ researchers have identified that the financially-motivated threat actors referred to as "Magecart," have breached two companies. The affected companies are the mattress company "Amerisleep," and pillow company "MyPillow." At the time of this writing, researchers note that of the two incidents "[o]ne has been resolved but was never disclosed and another is ongoing despite numerous attempts by us to contact the affected retailer." Magecart actors targeted the companies' websites and injected scripts designed to steal payment data. Amerisleep was targeted from April 2017 to at least October 2017 and again in December 2018; it is unclear if this campaign is still ongoing. MyPillow was reported to have target with payment skimmers in early and late October 2018, and it was not reported if the campaign is still ongoing.
Click here for Anomali recommendation
PuTTY Releases Important Software Update to Patch 8 High-Severity Flaws (March 20, 2019)
The developers of the open source SSH and telnet client "PuTTY," have released a new version (0.71) to address eight "high-severity" vulnerabilities. The eight vulnerabilities are listed as so: authentication prompt spoofing, code execution via CHM hijacking, buffer overflow in Unix PuTTY Tools, reusing cryptographic random numbers, integer overflow flaw, and the final three vulnerabilities are terminal denial-of-service attacks. The multiple vulnerabilities could grant threat actors numerous ways to conduct malicious activity.
Click here for Anomali recommendation
Severe Security Bug Found in Popular PHP Library for Creating PDF Files (March 19, 2019)
An Italian security researcher going by the handle "Polict," discovered that the vulnerability identified by Sam Thomas in summer 2018 that affected the "TCPDF" PHP library has inadvertently been "un-patched." The newly found vulnerability is a variation of the one discovered by Thomas, registered as "CVE-2018-17057," that was reportedly fixed in TCPDC version 6.2.20. The vulnerability was accidentally reintroduced when the TCPDF team attempted to fix the vulnerability reported by Polict. The vulnerability is a PHP serialization issue that could be exploited by threat actors in two ways. First, an actor could find a website that "allow[s] user input to be part of the PDF file generation process, such as when adding names of other details inside invoices." Second, the vulnerability could be exploited on websites that are already affected by Cross-Site Scripting (XSS) attacks "where an attacker can plant malicious code inside the HTML source code that will be fed to the TCPDF library to convert into a PDF."
Click here for Anomali recommendation
Check Point Forensic Files: Monero CryptoMiner Campaign Adapts APT Techniques (March 19, 2019)
A cryptomining campaign has been discovered utilizing Tactics, Techniques, and Procedures (TTPs) similar to Advanced Persistent Threat (APT) style of malicious activity, according to Check Point researchers. This "Monero" cryptocurrency campaign was identified in mid-January 2019 and was observed to utilize two different malware in tandem to accomplish its objectives. APT TTPs similarities include: achieving persistence, lateral movement, and use of different malware in combination, among others. The actors use two variants of trojan tracked as "Trojan.Win32.Fsysna," and a variant of a Monero cryptominer. As of this writing, it is unclear how actors first infect a target machine, however, the malware does utilize the "Mimikatz" credential-stealing malware to move laterally on a network.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041) | [MITRE ATT&CK] System Network Connections Discovery (T1049) | [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Command-Line Interface (T1059) | [MITRE ATT&CK] Windows Management Instrumentation (T1047) | [MITRE ATT&CK] PowerShell (T1086)
JNEC.a Ransomware Spread by WinRAR Ace Exploit (March 18, 2019)
Threat actors have been observed exploiting the WinRAR vulnerability registered as "CVE-2018-20250." Actors are incorporating the vulnerability in a new ransomware called "JNEC.a." The ransomware was identified to infect a machine via the WinRAR vulnerability. The actors behind the malware request .05 bitcoins (approximately $199.97 USD) from a user who has had their files encrypted and appended with the ".Jnec" extension. Interestingly, the actors use a unique ID for each infected machine to generate a Gmail account for the individual to use that the actors claim the decryption key will be sent to. The ransom notes shows the Bitcoin ransom amount, the Bitcoin wallet address to make the payment, number of encrypted files, and the unique Gmail address. Qihoo 360 Intelligence researchers found a .rar archive in the wild that contained the ransomware, it is likely that this is the distribution method for JNEC.a.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204) | [MITRE ATT&CK] Data Compressed (T1002)
New Mirai Variant Targets Enterprise Wireless Presentation and Display Systems (March 18, 2019)
Palo Alto Networks Unit 42 researchers have discovered a new variant of the "Mirai" Internet-of-Things (IoT) botnet malware. This new variant of the notorious Distributed Denial-of-Service (DDoS) malware is specifically targeting "WePresent WiPG-1000 Wireless Presentation" systems and LG "Supersign" televisions, as of this writing. Researchers note that both of these products are intended for businesses which may potentially indicate that Mirai is shifting toward enterprise-focused targeting. The new variant was also found to have new credentials added to its list to conduct brute force attacks as well as 11 new exploits to infect the aforementioned targets, among other new features. Mirai now has 26 exploits at its disposal that include various CVEs and router vulnerabilities. Researchers also found that the malware was pulling payloads from an IP address that was also distributing the "Gafgyt" information-stealing trojan.
Click here for Anomali recommendation
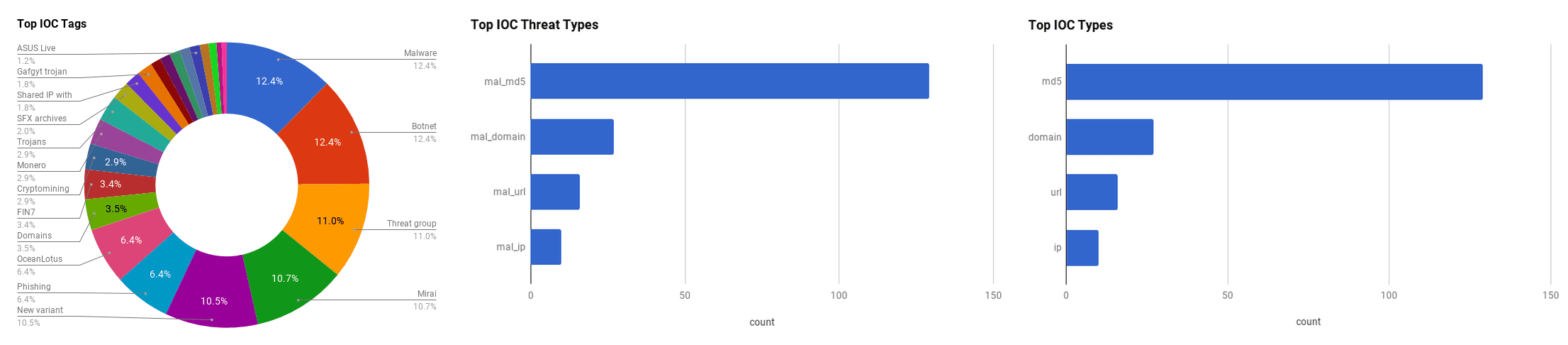
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
The Advanced Persistent Threat (APT) group ìAPT28î is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
APT32 has been conducting cyberespionage campaigns since at least 2013, with a particular focus on individuals and businesses with ties to Vietnam. FireEye researchers contend that the groupís malicious activity is aligned with Vietnamese government interests. Security firms have not yet released the specific targets and victims in order to protect their customers. The group uses their own unique malware in addition to open source tools to attack their targets. The combination of malware and tools allows the group to maintain presence on an infected machine or system, as well as moving laterally through a network.
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



