Weekly Threat Briefing: Scammers Ride on Popular Vote411 Voter Info Site to Push Scareware Alerts
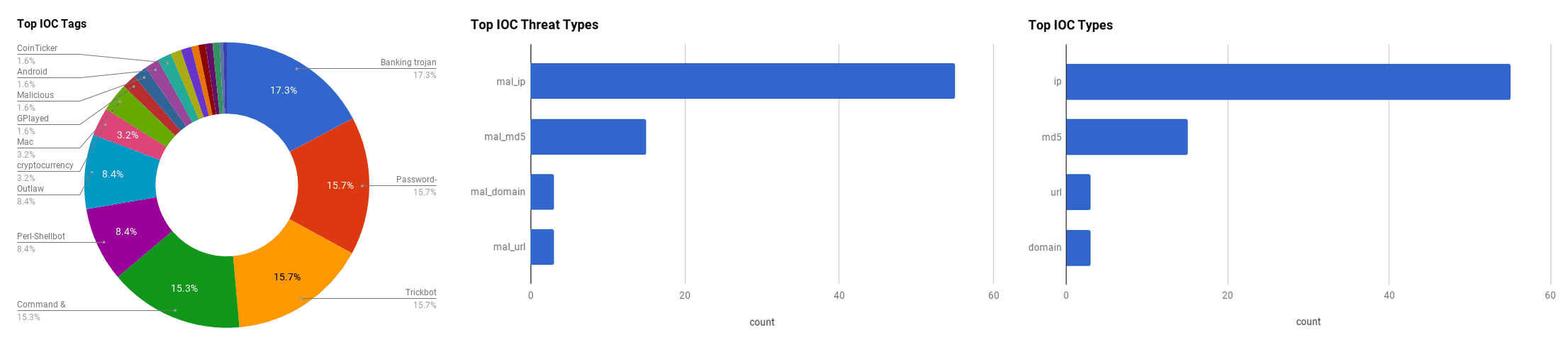

The intelligence in this week's iteration discuss the following threats: Backdoors, CommonRansomware, Data breaches, Magecart, Malware, Phishing, Ransomware, Stuxnet, Trickbot, Typosquatting, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Scammers Ride on Popular Vote411 Voter Info Site to Push Scareware Alerts (November 5, 2018)
Following the public promotion of the site "VOTE411[.]org" by comedian John Oliver in the lead-up to the US midterm elections, threat actors have exploited the site's increase in visits by typosquatting the Top-Level Domain (TLD) name to conduct a technical support scam. The threat actors changed the domain name to end with a "[.]com" instead of the official "[.]org" and victims that went to the typosquatted site were given a pop-up image. The pop-up stated their iOS device was infected with "Pegasus" spyware and needed to phone a particular number to pay for a removal process. The typosquatted domain sends the user through multiple redirects and ultimately does not attempt to deliver a malicious binary, but instead leads users to either a text message subscription or enter credit card information to remediate the purported Pegasus infection.
Click here for Anomali recommendation
Spam Campaign Targets Exodus Mac Users (November 2, 2018)
A phishing email campaign targeting Mac users has been observed by researchers at F-Secure that targets Exodus, a multi-cryptocurrency wallet. The phishing email appears to be an update for Exodus, containing an "Exodus-MacOS-1.64.1-update.zip" attachment. This fake update is attempting to update the user's version to 1.64.1 (the most recent legitimate version of Exodus is 1.63.1). If the user extracts the attached .zip file and runs the extracted application, it installs a type of spyware onto the infected machine. The spyware appears to originate from "realtime-spy-mac[.]com" which is a cloud-based surveillance and remote spy tool that allows for the threat actor to view images and data uploaded from the infected machine, as well as allows for keylogging abilities. It is unclear the scale of this campaign or if it was targeted in any way.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
New Ransomware Using DiskCryptor with Custom Ransom Message (November 2, 2018)
Independent researchers by the Twitter handle "MalwareHunterTeam" discovered a new ransomware campaign that installs the "DiskCryptor" encryption service onto the infected machine and restarts the computer. A ransom note is then shown following the reboot, giving the victim instructions on how to retrieve their files. The threat actors behind this new campaign are suspected to possibly be compromising a target machine's Remote Desktop Services (RDS) to install the ransomware manually. During the ransomware's installation process, a log in the machine's Public files shows the current stage of the encryption process. Once the machine has been fully encrypted, it will initiate a reboot that then shows the ransom note with the instructions for payment. The instructions indicate that the email "mcrypt2018@yandex[.]com" be contacted to receive the decryption password as well as find out the cost of the ransom and make the payment. It is unclear the initial attack vector of the ransomware.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Desktop Protocol (T1076)
Magecart Claims Fresh Victim in Electronics Kit Seller Kitronik (November 2, 2018)
Electronic kit seller, Kitronik, disclosed that they are the most recent victim of the payment skimming threat group, "Magecart." The company released a statement that they suffered a data breach that impacts their online customers who utilised their site to purchase items between August 2018 and September 2018. Magecart's payment skimming malware was detected on their online checkout page following an investigation that was triggered by a notification from Kitronik's payment gateway provider regarding a higher than normal amount of fraud on their site. According to Kitronik, the data stolen by Magecart includes: bank card numbers, CVV numbers, email addresses, names, and post addresses. Customers who created accounts before August 2018 are believed to not have their addresses compromised because only details entered at the checkout stage on the site between those dates might have been stolen. How Magecart compromised the website is currently unclear.
Click here for Anomali recommendation
Systemd Vulnerability in Linux Could Trigger Remote Attacks and System Crashes (November 2, 2018)
A flaw in "Systemd" in Linux operating systems that could allow for remote execution has been discovered by a researcher from Google. The flaw is located in the Systemd suite's written-from-scratch DHCPv6 client. The client can be initiated automatically when receiving IPv6 router advertisements, if IPv6 support is enabled. The vulnerability is registered as "CVE-2018-15688" and is an out-of-bounds write that can allow a threat actor to execute arbitrary code or cause a Denial-of-Service (DoS) due to a heap-based buffer overflow. The caveat to this vulnerability, however, requires a threat actor to have access to a rogue DHCPv6 server that is on the same network of the target DHCPv6 server. Creators of Systemd have released a patch for all Linux distributions that utilise this.
Click here for Anomali recommendation
Cisco Zero-day Exploited in the Wild to Crash and Reload Devices (November 1, 2018)
Cisco Talos researchers has reported that a zero-day vulnerability in the Session Initiation Protocol (SIP) inspection engine has been observed affecting their products that run "Adaptive Security Appliance" (ASA) and "Firepower Threat Defence" (FTD) software. This vulnerability, registered as "CVE-2018-15454," allows for an unauthenticated user to remotely force a device to reload or trigger high CPU, resulting in a Denial-of-Service (DoS) condition. Several Cisco devices have been seen to be affected by this vulnerability, mainly products that run ASA 9.4 and later versions or FTD 6.0 and later versions. This vulnerability has already been observed to have been exploited in the wild in a limited number of attacks. At the time of this writing, there has yet to be a security patch released.
Click here for Anomali recommendation
Perl-Based Shellbot Looks to Target Organizations via C&C (November 1, 2018)
Trend Micro researchers have discovered a new campaign targeting various organisations through a command injection vulnerability in Internet-of-Things (IoT) devices and Linux servers. The threat group behind the attacks have been dubbed "Outlaw" and utilises a variant of "Perl Shellbot" for various malicious purposes. The threat group has been observed targeting organisations in Japan and Bangladesh, thus far, through compromised File Transfer Protocol (FTP) servers. The botnet first runs a command on a target IoT device to verify that the host accepts commands from the command-line interface (CLI) and then, if the command runs successfully, a payload (n3 file) will download onto the machine that runs with a Perl interpreter. Interestingly, this n3 file is removed at the final stages of the attack so there is no traceable activity left on the infected system. Once this botnet is installed onto the machine, it connects to the threat actor's Command and Control (C2) server. Following the initial infection, the bot modifies the Domain Name System (DNS) settings to confirm that the target is not a honeypot and has connectivity to the internet. The network communication appears to send out an "XMR rig" Monero mining monitoring tool output.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Command-Line Interface (T1059)
BleedingBit Exposes Enterprise Access Points and Unmanaged Devices to Undetectable Chip Level Attack (November 1, 2018)
Two Bluetooth Low Energy (BLE) vulnerabilities have been discovered, dubbed "BLEEDINGBIT," that affect the access points that deliver Wi-Fi to enterprise networks manufactured by Cisco, Meraki, and Aruba, according to researchers at Armis. The vulnerabilities are registered as "CVE-2018-16986" and "CVE-2018-7080." These two vulnerabilities allow an unauthenticated threat actor remote access to enterprise networks without detection by granting initial access via the unsecured access points. A threat actor would then be able to move laterally between network segments and could bridge them together. The BLE chips are becoming increasingly utilised by a variety of industries which are supposed to help create close-knit networks and enable the use of Internet-of-Things (IoT) devices by enterprises.
Click here for Anomali recommendation
Trickbot Shows Off New Trick: Password Grabber Module (November 1, 2018)
Trend Micro researchers have identified that threat actors utilising the "Trickbot" banking trojan have added a new feature to the malware to include a password-stealing module. The new module is capable of stealing passwords from multiple applications such as Microsoft Outlook, Filezilla, and WinSCP as well as passwords in web browsers including Chrome, Edge, Firefox, and Internet Explorer. The data that can be stolen includes: autofills, browsing history, HTTP posts, internet cookies, and usernames and passwords. The Trickbot version that contains this new module is primarily targeting individuals in Canada, the Philippines, and the US. Furthermore, this variant has also been observed to contain an auto-start service that allows the malware to run every time an infected machine is started as well as a "shareDll32" module to propagate itself throughout a network. As of this writing, the distribution method for this Trickbot variant has not yet been reported.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Email Collection (T1114) | [MITRE ATT&CK] Input Capture (T1056)
New Stuxnet Variant Allegedly Struck Iran (October 31, 2018)
A more aggressive and sophisticated variant of Stuxnet has been recently observed targeting infrastructure and strategic networks in Iran. There is little information at the time of the publication of the article; however, General Gholamreza Jalali, the head of Iran's Passive Defence Organisation, stated that they had discovered and neutralised a new generation of Stuxnet that contained several parts attempting to breach various Iranian systems. A variant of Stuxnet is likely to emerge in a non-recognisable form, since there has been so much news attention and cyber security research on that specific malware.
Click here for Anomali recommendation
CommonRansom Ransomware Demands RDP Access to Decrypt Files (October 30, 2018)
A researcher named Michael Gillespie has identified a new ransomware dubbed "CommonRansomware" that stands out from other malware with similar functionalities in that it makes an unusual request of the victim to decrypt their files. To note, the initial infection vector for CommonRansomware has not yet been reported at the time of this writing. Once a machine has been infected, the ransom note appears that requests 0.1 bitcoins (approximately $633.42 USD). The strange factor of this malware comes with another request in which the note asks to send an email to "old@nuke[.]africa" with various forms of information including: IP address and RDP port number, username and password of administrator account, time when Bitcoin payment was made, and victim ID number.
Click here for Anomali recommendation
Girl Scout Issues Data Breach Warning to 2,800 Members (October 29, 2018)
The Girl Scouts of America branch in Orange County, California issued a statement on October 22, 2018 in which it confirmed that it had suffered a data breach. The breach was conducted by an unknown threat actor(s) who was able to gain illicit access to an email account used by the Girl Scouts of Orange County (GSOC). The compromised email address was likely then used by threat actors to distribute phishing emails, however, GSOC did not specify what kind of emails were sent from its email address. The compromised email account was used by GSCO to organise travel for its members so it is possible that Personally Identifiable Information (PII) associated with approximately 2,800 girls and their families was compromised. Information contained in the email account consists of date of birth, full name, health history, home address, and insurance policy numbers.
Click here for Anomali recommendation
GPlayed's Younger Brother is a Banker - and It's After Russian Banks (October 29, 2018)
A new version of the "GPlayed" Android banking trojan, first reported on in early October 2018, has been identified impersonating the Google Play Store application, according to Cisco Talos researchers. This variant, dubbed "GPlayed Banking," specifically targets "SherBank AutoPay" users while the previous version targeted banking information in general. SherBank AutoPay is a service offered by SherBank, which is a Russian state-owned bank. GPlayed Banking is distributed by posing as the Google Play Store application with the labelled "Play Google Market and, once downloaded, asks the user to change settings to grant the application administrator privileges. Interestingly, the application does not need administrator privileges to conduct its malicious activity that consists of stealing SMS messages and sending SMS messages to SherBank to determine an account balance. If the balance is lower than $3,000 the trojan stops, if larger than 68,000 the malware requests a value of 66,000, otherwise, the total amount minus 1,000 is requested.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Trusted Relationship (T1199)
Mac CryptoCurrency Ticker App Installs Backdoors (October 29, 2018)
A MalwareBytes forum user informed the researchers of a malicious macOS application he/she discovered that is masquerading as a cryptocurrency price-checker. The application, called "CoinTicker," does function by showing the current prices of various cryptocurrencies, but it also attempts to install two different backdoors onto the machine running the application. Upon launching on a machine it was downloaded on, CoinTicker subsequently downloads and installs two publicly available backdoors called "EggShell" and "EvilOSX." Both backdoors are relatively flexible in their capabilities because they are open source and therefore could be modified by threat actors.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Trusted Relationship (T1199)
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



