Weekly Threat Briefing: Spam Campaign Uses Recent Boeing 737 Max Crashes to Push Malware
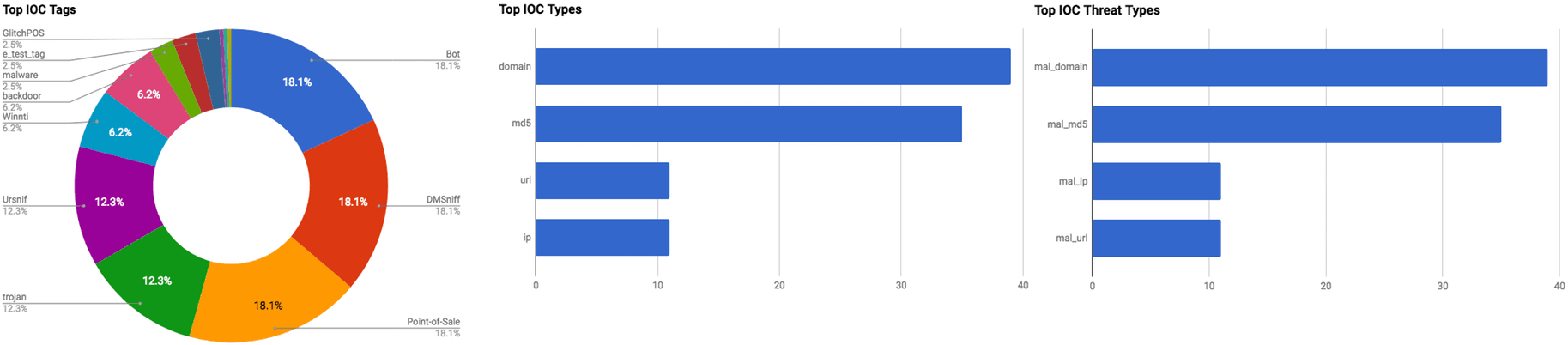

The intelligence in this week’s iteration discuss the following threats: APT, Data breach, Malspam, Malware, Phishing, Point-of-Sale, Ransomware, RAT, Supply chain, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Spam Campaign Uses Recent Boeing 737 Max Crashes to Push Malware (March 18, 2019)
360 Threat Intelligence Center researchers have observed a spam campaign that is attempting to take advantage of the two crashes of the Boeing 737 Max aircraft. The threat actors behind this campaign are distributing emails with the account “info@isgec[.]com” with the subject line “Fwd: Airlines plane crash Boeing 737 Max 8.” The emails purport to have been written by a private investigator named “Joshua Berlinger” and attempt to convince the recipient into opening an attached JAR file. Researchers identified that the objective of this campaign is to drop the “H-WORM” Remote Access Trojan (RAT” onto the recipient’s machine via the malicious JAR file attachment.
Click here for Anomali recommendation
Intel Releases Security Advisories on Multiple Products (March 15, 2019)
The United States Computer Emergency Readiness Team (US-CERT) has issued an advisory regarding vulnerabilities in multiple products created by the semiconductor manufacturing company, “Intel.” Intel has released security advisories to address vulnerabilities in multiple products including: Accelerated Storage manager in RSTE, USB 3.0 Creator Utility, Software Guard Extensions SDK, and Matrix Storage Manager. Some of the vulnerabilities could be exploited by a threat actor to take control of an affected system, according to the US-CERT.
Click here for Anomali recommendation
Unsecured Gearbest Server Exposes Millions of Shoppers and Their Orders (March 15, 2019)
“Gearbest,” a Chinese e-commerce company, exposed over 1.5 million customers’ information and orders due to an unsecured Elasticsearch server. According to researcher Noam Rotem, the server was not password-protected and was publicly accessible. Information that was publicly visible include Personally Identifiable Information (PII): account passwords, address, date of birth, email addresses, IP address, name, national ID and passport information, order number, payment information, payment type, phone number, postcode, and products purchased.
Click here for Anomali recommendation
Kathmandu Probes Possible Card Skimming Breach (March 15, 2019)
New Zealand-based outdoor clothing store, “Kathmandu,” is investigating a possible data breach where customer’s credit card credentials were harvested from their website. Between January 8, 2019 and February 12, 2019, an unauthorised third-party gained access to the retailer’s website and stole customers’ personal information and payment details. An investigation is ongoing to determine what happened fully, but it is hypothesised it could be a recent MageCart attack, though that is unconfirmed.
Click here for Anomali recommendation
GlitchPOS: New PoS Malware for Sale (March 13, 2019)
Cisco Talos researchers discovered a new malware, dubbed “GlitchPOS,” that is being sold on crimeware sites by actors suspected to be behind the “DiamondFox L!NK” botnet. The Point-of-Sale (POS) malware is disguised as a fake game and displays a variety of pictures of cats upon deployment, whilst the malware payload is decoded in the background. The GlitchPOS malware only has a small number of functions including: clean itself off the system, exfiltrate credit card numbers from the memory of the infected system, receive tasks from the Command and Control (C2) server, register the infected systems, update the "encryption" key, update the exclusion list of scanned processes, and update the User Agent. The objective of the malware is to steal credit card numbers from the memory of an infected system.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041) | [MITRE ATT&CK] Scripting (T1064)
‘DMSniff’ POS Malware Actively Leveraged to Target Small-, Medium-Sized Businesses (March 13, 2019)
Researchers from Flashpoint reported on a Point-of-Sale (POS) malware called “DMSniff” that utilises Domain Generation Algorithms (DGA) to create lists of Command and Control (C2) on an ad hoc basis to avoid C2 domains being removed by ISPs or law authorities. This malware has reportedly been active since at least 2016, and is targeting small to medium-sized businesses such as restaurants and theaters. It is believed that threat actors are able to gain initial access to devices by brute-forcing SSH connections or using known vulnerabilities in the devices. To steal data, the bot will loop to find credit card numbers and packages that information and sends it to the C2. The data will then be exfiltrated somewhere else to either store or sell onwards.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Custom Command and Control Protocol (T1094) | [MITRE ATT&CK] Brute Force (T1110) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
Patch Tuesday, March 2019 Edition (March 13, 2019)
Microsoft’s March “Patch Tuesday” addressed over five dozen security vulnerabilities were fixed in Windows OS, Internet Explorer, Edge, Office, and Sharepoint. Two major vulnerabilities patched were “CVE-2019-0797” and “CVE-2019-0808.” CVE-2019-0797 is a zero-day vulnerability that can allow for privilege escalation and deploy arbitrary code in kernel mode that has been observed to be exploited in the wild. CVE-2019-0808 is another zero-day privilege escalation vulnerability in Windows 7 and Windows Server 2008 that has been seen to be exploited in the wild in conjunction with the Google Chrome browser vulnerability “CVE-2019-5786.”
Click here for Anomali recommendation
Yatron Ransomware Plans to Spread Using EternalBlue NSA Exploits (March 13, 2019)
“Yatron,” a new Ransomware-as-a-Service (RaaS), is being promoted for sale on Twitter by the actor behind the malware. The ransomware reportedly uses the “EternalBlue” and ”DoublePulsar” exploits to propagate within a network, and the ransomware will attempt to delete encrypted files if a user does not pay the ransom after 72 hours. Yatron is based off another ransomware, “HiddenTear,” but is modified so it cannot be decrypted for free using current methods available. According to Bleeping Computer, the “exploits are incomplete and the ransomware does not currently include the Eternalblue-2.2.0.exe and Doublepulsar-1.3.1.exe executables that it relies on” so it is not fully effective in utilising those vulnerabilities. Yatron can also spread within a network via Peer-to-Peer (P2P), USB, and LAN.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Forced Authentication (T1187)
WordPress Shopping Sites Under Attack (March 12, 2019)
WordPress-based shopping sites have been found to be vulnerable to threat actors exploiting a cross-site scripting (XSS) vulnerability in a shopping cart plug-in to drop backdoors and compromise sites. Threat actors appear to be exploiting sites that use “Abandoned Cart Lite for WooCommerce," which is on over 20,000 WordPress sites. According to “Defiant,” the company who created WordFence, this benign XSS flaw is weaponised by “automating operations against WordPress WooCommerce-based stores to generate shopping carts that contain products with malformed names. They add exploit code in one of the shopping cart's fields, then leave the site, an action that ensures the exploit code gets stored in the shop's database. When an admin accesses the shop's backend to view a list of abandoned carts, the hackers' exploit code is executed as soon as a particular backend page is loaded on the user's screen.” It is unclear what the end-goal of the threat actors is by installing these backdoors into the sites.
Click here for Anomali recommendation
New Ursnif Variant Targets Japan Packed with New Features (March 12, 2019)
Japan has been observed to be one of the top countries affected in recent years by the information-stealing malware, “Ursnif,” in conjunction with the “Bebloh” malware, according to Cybereason. Bebloh acts as a downloader that runs tests to find out if it is running in a sandbox or Virtual Machine (VM), and if it determines neither is the case, it then downloads Ursnif onto the infected machine. The malware is initially sent via phishing emails containing a malicious attachment that requests macros to be enabled. If macros are enabled, the malware will determine whether the machine is located in Japan, and if it is, it will download a PowerShell payload that appears as an image. Embedded in the image is another PowerShell code that, once decrypted, will install Bebloh, which subsequently downloads Ursnif. This variant of Ursnif has new features such as a new persistence mechanism, revamped and new stealer modules, cryptocurrency and disk encryption software module, and an Anti-PhishWall module to counteract “PhishWall,” a Japanese security product.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] PowerShell (T1086)
Gaming Industry Still in the Scope of Attackers in Asia (March 11, 2019)
Researchers from ESET discovered a supply-chain attack that has been compromising game developers to drop a backdoor into video games’ build environment and have the malware distributed as legitimate software. The attacks appear to be highly targeted at the Asia gaming industry, specifically (ordered by highest amount of infections to least) Thailand, Philippines, Taiwan, Hong Kong, Indonesia, and Vietnam. The same backdoor was found on three different software products. The backdoor is launched in-memory before normal execution of the video game, and connects to a Command and Control (C2) server that is hosted at a domain that masquerades as a legitimate site related to the game or developer. The malware will stop running if it detects the system language is Chinese or Russian. The backdoor only has four commands that can be used by the threat actors: “DownUrlFile,” “DownRunUrlFile,” “RunUrlBinInMem,” and “UnInstall.”
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Binary Padding (T1009) | [MITRE ATT&CK] Commonly Used Port (T1043) | [MITRE ATT&CK] Standard Cryptographic Protocol (T1032) | [MITRE ATT&CK] Multilayer Encryption (T1079) | [MITRE ATT&CK] Data Encrypted (T1022) | [MITRE ATT&CK] New Service (T1050) | [MITRE ATT&CK] Supply Chain Compromise (T1195)
Pandora's Box: Another New Way to Leak All Your Sensitive Data (March 11, 2019)
The cloud-based content management platform, “Box,” was discovered to be publicly accessible and thus leaking companies share files and folders if a user guessed an organisation’s unique subdomain URL, according to Adversis. Accessible data included: archives of years of internal meetings, customer lists, Employees lists, Financial data, High profile technology prototype and design files, internal issue trackers, invoices, IT data, network diagrams, passport photos, Social Security and bank account numbers, and VPN configurations. According to security researchers, this feature in Box has been reported on before since June 2017, though no changes have been made on Box’s side.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
Lazarus Group
The Chinese APT group called “Winnti” (also known as Threat Group-3279) has been active since at least 2009, and is known to attack gaming companies to steal digital certificates and source code. Winnti was discovered in 2011 when researchers put together clues as to why an unspecified amount of computers had been infected with a new trojan. The clue led researchers to identify that all the infect machines shared on similarity in that they all played a well-known online game. It was then determined that the game users had been infected by receiving updates from a compromised server that belonged to the company.
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



