Weekly Threat Briefing: The Facebook Login Phishing Campaign Can Even Trick Savvy Users
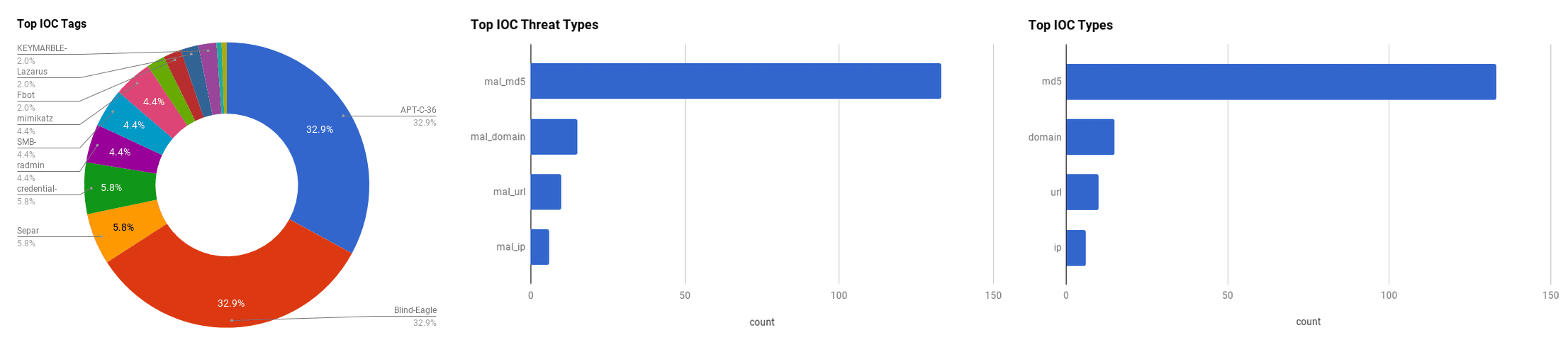

The intelligence in this weekís iteration discuss the following threats: APT28, APT-C-36, Cryptominer, Data breach, Fbot, KEYMARBLE backdoor, Malware, Mimikatz, Phishing, RADMIN, Ransomware, Rietspoof, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Fbot Malware Targets HiSilicon DVR/NVR Soc Devices (February 24, 2019)
Researchers from 360Netlab discovered that a high number of HiSilicon "DVR/NVR Soc" devices were becoming infected with a new version of the "Fbot" malware. 24,528 IP addresses were infected worldwide, according to 360Netlab, and threat actors were able to exploit the surveillance cameras via a weak security implementation of the DVRIP protocol created by HiSilicon. This allowed the actors to establish a backdoor in the device and then inject Fbot. Fbot is then able to conduct Distributed-Denial-of-Service (DDoS) attacks.
Click here for Anomali recommendation
The Facebook Login Phishing Campaign Can Even Trick Savvy Users (February 22, 2019)
Antoine Vincent Jebara, the CEO of the offline password manager and authentication company, "Myki," published a blog post describing a recent phishing campaign that has been targeting users who visit a website purporting to be a legitimate news site, "The News Week Journal." The campaign uses an HTML block with a well-crafted and fake Facebook login prompt for users to access a site, that actually steals the credentials of the user. The fake login popup allows users to interact with it as a legitimate popup such as dragging it around or dismissing it. Because of the authentic appearance of the fake login window, including the mocked up HTTPS status, it may be difficult for Facebook users to identify the campaign.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194)
POS Firm Hacked, Malware Deployed at 130+ Outlets (February 22, 2019)
Minnesota-based "North Country Business Products" released an announcement to customers stating that they suffered a cyberattack in January 2019 which resulted in their Point-of-Sale (PoS) systems to be infected with malware. The malware allowed unknown threat actors to steal customer data including cardholder's credit card number, CVV, expiration date, and name. The breach affected users who used their card at over 130 locations including Dunn Brothers Coffee, Zipps Sports Grill, and Someburros outlets between January 3 and January 24, 2019. As of this writing, it is unclear how threat actors managed to infect the PoS systems.
Click here for Anomali recommendation
Cr1ptT0r Ransomware Infects D-Link NAS Devices, Targets Embedded Systems (February 22, 2019)
A new ransomware, dubbed "Cr1ptT0r," has been observed targeting Network Attached Storage (NAS) equipment; the ransomware was first brought to the attention of researchers in BleepingComputer forums on an unspecified date. Users of D-Link DNS-360 devices notice their devices were infected with ransomware, which was likely infected via vulnerabilities in the firmware that can allow for remote code execution. The DNS-360 is noted to have several vulnerabilities in the firmware, and users who were infected by the ransomware stated that they had not updated the firmware to the latest version, despite the device being connected to the internet. The threat actors behind the ransomware request users to visit a specific URL to get more information regarding the infection and how to retrieve their files back. Threat actors requested 0.30672022 Bitcoin ($1,200 USD) or a user can pay $19.99 for individual file decryption.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
Critical Drupal Vulnerability Allows Remote Code Execution (February 21, 2019)
Drupal, the content management system, released a security update on Wednesday, February 20, 2019 regarding a "highly critical" vulnerability, registered as "CVE-2019-6340," that could allow remote code execution. The flaw is caused by a lack of proper data sanitisation, which means a threat actor could exploit this by enabling the core RESTful Web Services module and allowing PATCH and POST requests. This vulnerability affects Drupal versions 8.6.10 and 8.5.11. Drupal 7 is not affected, though it is advised users apply updates released for version 7, as well.
Click here for Anomali recommendation
Warning: Critical WinRAR Flaw Affects All Versions Released In Last 19 Years (February 21, 2019)
A critical vulnerability in Window's "WinRAR" archiver tool has been discovered by Check Point researchers that affects all versions of WinRAR released in the past 19 years. The vulnerability is due to the way the old library, "UNACEV2.DLL," extracted files compressed in ACE file format, where threat actors are able to craft a filepath string within a field, that leverages buggy code to trigger a path traversal vulnerability. An absolute path traversal bug that would allow attackers to extract compressed files to a folder of their choosing could then be leveraged to execute arbitrary code on a system.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Data Compressed (T1002)
Monero Miner-Malware Uses RADMIN, MIMIKATZ to Infect, Propagate via Vulnerability (February 20, 2019)
Researchers from Trend Micro discovered an uptake of threat actors using both "Mimikatz" and "RADMIN" open-sourced malware tools to install Monero cryptocurrency miners onto company machines based in China, Hong Kong, Italy, and Taiwan. The initial infection vector is accomplished via a user visiting a compromised website, also known as a "watering hole." The initial payload removes older versions of malware on the machine then reinstalls the initial download to ensure the infection process is updated. It then connects to several URLs and IP addresses to download files, specifically the Monero miner, Mimikatz, and RADMIN. Following the installation of the Monero miner, Mimikatz is executed to gather credentials and enable the threat actor to remotely execute commands. RADMIN is dropped on the machine to allow the threat actor remote command communication via a named pipe. This attack exploits a patched Windows SMB server vulnerability (MS17-010) which was patched in 2017.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise (T1189) | [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Credential Dumping (T1003)
Crime Syndicate Hacks 15,000 Medical Files at Cabrini Hospital, Demands Ransom (February 20, 2019)
A specialist cardiology unit at Cabrini Hospital in Australia suffered a cyber-attack where threat actors compromised their system and stole 15,000 patients' files. The medical staff were unable to access patients' files for over three weeks following the ransomware attack. The threat actors demanded the ransom paid in cryptocurrency before they would send a decryption password to the hospital. According to the article, it is understood that a ransom has been made, for an unknown amount, but some files still have yet to be recovered, including patients' personal details and sensitive medical records. An investigation is still ongoing to recover all the files.
Click here for Anomali recommendation
Microsoft Reveals New APT28 Cyber-Attacks Against European Political Entities (February 20, 2019)
Microsoft disclosed that they have observed recent activity conducted by Russian Advanced Persistent Threat Group (APT) "APT28." The activity consists of spear phishing emails designed to target European political and governmental entities, as well as NGOs and think-tanks that work closely with government officials. Between September and December 2018, there were approximately 104 accounts targeted by APT28 in Belgium, France, Germany, Poland, Romania, and Serbia. The goal was to steal user login credentials and infect victims with malware, in a suspected attempt to possibly influence the upcoming 2019 European Parliament elections that take place in May. It is unknown if the spear phishing emails were able to infect their intended targets, as of this writing.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Spearphishing Link (T1192)
A New Wave of the Separ Info-Stealer is Infecting Organizations through "Living off the Land" Attack Methods (February 19, 2019)
The credential-stealer, "Separ," has been found to be actively distributed to users in Southeast Asia and the Middle East hidden in a phishing campaign utilising fake PDF attachments. The emails and attachments are related to businesses and relate to quotations, shipment confirmations, and equipment specifications. The fake PDF document contains a self-extractor so if a user opens the attachment, it will automatically initiate and run a VBScript that sets up several directories. The script then launches a second script that changes the machine's firewall settings, opens an empty .jpg to hide command windows, runs SecurityXploded's "Email and Browser Password Dumps" to steal credentials and uploads them to a legitimate FTP client.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] Exfiltration Over Alternative Protocol (T1048)
North Korea Turns Against New Targets?! (February 19, 2019)
A new phishing campaign targeting Russian organisations is being attributed to the North Korean Advanced Persistent Threat (APT) group, "Lazarus," according to Check Point researchers. The phishing emails contained Microsoft Word or Excel attachments that had multiple images inside the document and required a user to "enable content" to view the images in the file. If the macros were enabled, a VBScript was downloaded and executed from a Dropbox host. The VBScript downloads a CAB file that contains the final payload from a compromised server, that appears as a JPEG image, and executes the final payload: the "KEYMARBLE" backdoor. The backdoor acts as a Remote Access Trojan (RAT) that allows the operator basic functionality to obtain information from the infected machines and exfiltrate the data to the Command and Control (C2) server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Scripting (T1064)
Rietspoof Malware Spreads via Facebook Messenger and Skype Spam (February 19, 2019)
A new malware, dubbed "Rietspoof," has been observed to be distributed to users via Facebook, Skype, and other instant messaging clients, according to Avast researchers. Rietspoof is a dropper malware that infects victims and obtains persistence on the compromised machine to then download other malware to the machine following instructions from the Command and Control (C2) server. The malware obtains persistence by placing a LNK shortcut file into the Windows/Startup folder and, because it is signed with legitimate certificates, it is able to evade antivirus checks. The malware is capable of downloading, executing, uploading, and deleting files in addition to deleting itself from the system in the case the malware is identified and the actor wants to delete evidence of their activities.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060)
The NoRelationship Attack Bypasses Office 365 Email Attachment Security (February 19, 2019)
A new phishing attack has been detected by researchers from Avanan that bypasses Exchange Online Protection (EOP) URL filters that are responsible for scanning Office documents to ensure they are not malicious. This attack, dubbed "NoRelationship," will exploit the fact that email filters only scan the "document.xmls.rels" file to see if any links are in the document. Threat actors will erase the URL in that file so the parser does not detect anything malicious. The email then will pass through without being detected as malicious and the user is able to open the email and potentially open the harmful document.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
APT-C-36: Continuous Attacks Targeting Colombian Government Institutions and Corporations (February 18, 2019)
Researchers from 360Netlab have been tracking a suspected South American-based Advanced Persistent Threat (APT) group, "Blind Eagle" (also known as APT-C-36). The group is believed to have been active since April 2018 and primarily target Colombian government entities and other various industries. The group utilises phishing lures with attachments that contain malware as the initial infection vector. The goal of the APT group is to establish a backdoor into the intended targets to then obtain a foothold and then move laterally once in a network for reconnaissance purposes. The phishing emails and attachments are tailored to each industry/entity the group is targeting to potentially increase the possibility that a recipient will open the email and attachment. The attachment requests that macros be enabled and, if allowed, will begin the installation process of the "Imminent" backdoor.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Remote Access Tools (T1219)
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
APT28
The Advanced Persistent Threat (APT) group ìAPT28î is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
Lazarus Group
The Advanced Persistent Threat group (APT) ìLazarus Groupî is believed to be based in the Democratic People's Republic of Korea (DPRK) and has been active since at least 2009. Lazarus Group is believed to be composed of operatives from ìBureau 121î (121?), the cyber warfare division of North Koreaís Reconnaissance General Bureau. The Reconnaissance General Bureau was formed due to a reorganization in 2009 but its exact structure is not known due to North Koreaís denial and deception tactics. Bureau 121 is North Koreaís most important cyber unit that is used for both offensive and defensive operations. Bureau 121 are referred, in South Korean open-source media, as the ìElectronic Reconnaissance Bureauís Cyber Warfare Guidance Bureauî (전자정찰국 사이버전지도국). The term ìguidanceî in the context of North Korea often denotes that an organization is personally overseen by the head of state of North Korea as a strategically significant entity. Lazarus Group has targeted financial organizations since at least July 2009, The group is well known for their tendency to engage in data destruction/disk wiping attacks, and network traffic Distributed Denial-of-Service (DDoS) attacks, typically against the Republic of Korea (South Korea). The group targets various industries and sectors including South Korean and US government organizations, Non-Governmental Organizations (NGO), media and entertainment organizations, as well as shipping and transportation organizations, Korean hydro and nuclear power, and jamming of South Korean GPS.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



