Weekly Threat Briefing: Top-Tier Russian Hacking Collective Claims Breaches of Three Major Anti-Virus Companies
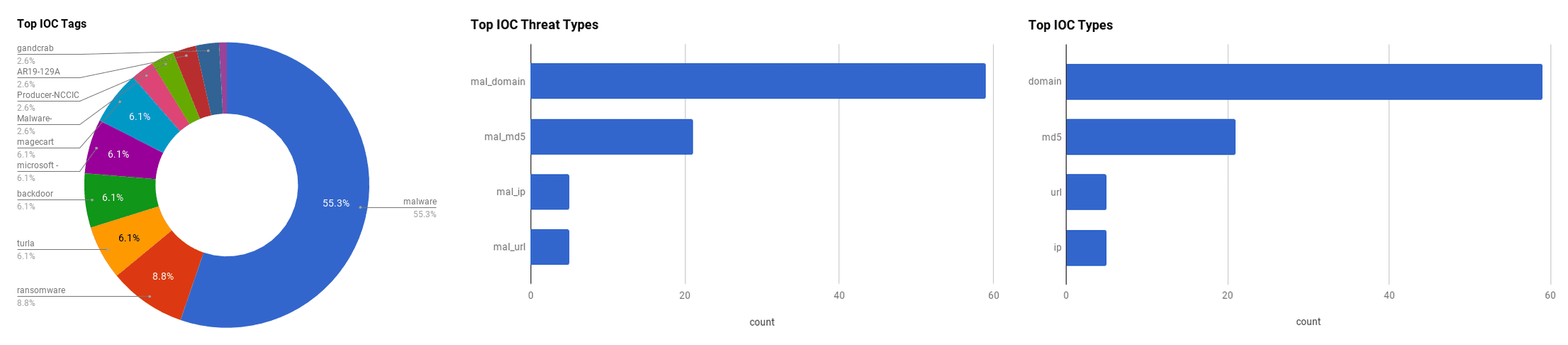

The intelligence in this week’s iteration discuss the following threats: FIN7, Gandcrab,Hidden Cobra, Rootkits, and Turla. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Top-Tier Russian Hacking Collective Claims Breaches of Three Major Anti-Virus Companies (May 9, 2019)
A Russian hacking collective named “Fxmsp” have claimed responsibility for breaching three anti-virus companies. The hack extracted source, dev documents, software base code, and security plugins from the companies, apparently totaling 30 terabytes worth of data. “Fxmsp” have a history of targeting corporate networks, generating an estimated profit of 1 million USD from selling corporate breaches, using resellers. Known TTPs of the group include accessing networks using remote desktop protocol servers, however recently claiming to have developed a credential-stealing botnet in order to set usernames and passwords from secured systems.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219)
Malware Analysis Report (AR19-129A) (May 9, 2019)
A Malicious Analysis Report (MAR) has been released by the US DHS and FBI detailing a malware used by the North Korean government. The malware named “ELECTRICFISH” uses a custom protocol to allow traffic between a source and target IP address from a Windows executable file. Once a connection is established, a funneling session is initiated with a proxy server used to bypass required authentication. With this type of malware, the attacker is able to steal information from the victim’s system, sending it to servers controlled by the group.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools (T1219) | [MITRE ATT&CK] Exfiltration Over Alternative Protocol (T1048)
Canadian Telco Exposes Unencrypted Card Details (May 8, 2019)
Researchers at vpnMentor have discovered an unprotected Freedom Mobile database. The database, containing over five million customer records, was left passwordless and unencrypted on April 17. The records included addresses, credit card numbers, CVV numbers, email address, and phone numbers. Telco claim the breach affects 15,000 customers, however, researchers claim there are potentially up to 1.5 million customers affected. Telco have blamed a third-party provider, Apptium, for the breach.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Over 275 Million Records Exposed by Unsecured MongoDB Database (May 8, 2019)
Security Discovery researcher Bob Dianhenko has discovered an unprotected “MongoDB” database that was left unprotected for more than two weeks. The database contained 275,265,298 records containing Personally Identifiable Information (PII) belonging to Indian citizens. The data includes: date of birth, email, name, and profession details such as salary. The database, hosted on AWS, was stored in a passwordless instance; left unsecured by the owner who is still unknown. The database is no longer available as a threat group known as “Unistellar” took the database offline.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
Dharma Ransomware Uses AV Tool to Distract from Malicious Activities (May 8, 2019)
Trend Micro researchers have identified a new technique used by threat actors to conceal malicious activities associated with the “Dharma” ransomware. Actors are distributing spam emails with a message persuading them to download a file via a provided link. Once the link is clicked on, the user is prompted to enter their password receiving the file. The downloaded file drops malicious files connected to the Dharma ransomware. To distract the victim, a legitimate installer appears while files are being encrypted in the background, however the malware will still be installed without the installer running. The affected individual is sent a message about where to pay the ransom to decrypt their files.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
FIN7.5: The Infamous Cybercrime Rig "FIN7" Continues Its Activities (May 8, 2019)
Kaspersky researchers have published a report discussing activity attributed to the financially-motivated threat group, “FIN7,” from the past year. The FIN7 campaigns use spear phishing emails with malicious attachments as the initial infection vector. One malicious document is used to gain context information about the infected machine, with another using macros to execute a “GRIFFON” implant. The GRIFFON implant is a Javascript validator-style implant capable of receiving modules for reconnaissance, screenshot, persistence, and downloading with the results sent to C2s. It is believed by researchers after analyzing the Tactics, Techniques, and Procedures (TTPs), that multiple other groups are interconnected to FIN7, continuing attacks.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
UC Browser for Android Vulnerable to URL Spoofing Attacks (May 8, 2019)
Security researcher, Arif Khan, has uncovered a vulnerability in UC Browser and UC Browser Mini Android video downloader apps. The disclosure, made April 30, details a vulnerability exposing users to spoofing attacks by sending them to domains controlled by malicious attackers. Users could be at risk of having their information stolen or receiving malware. Khan has reported the vulnerability to the UCWeb security team, with the report currently assigned “Ignored” by the team.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192)
GandCrab's New Evasive Infection Chain (May 7, 2019)
Threat actors distributing the “GandCrab” have been identified to have added some new techniques to their campaign, according to Cybereason researchers. GandCrab, which is estimated to be responsible for 40% of all worldwide ransomware attacks as of February 2019, is an evolving threat that targets individuals and companies. This campaign distributes GandCrab using a phishing email with a Korean document attachment. The attachment, if opened, prompts the user to enable macros, with code embedded into the document. A fileless infection chain is triggered if macros are enabled to drop the ransomware, making use of Living Of the Land Binaries (LOLBins) to fetch the payload avoiding detection. Once the ransomware runs, the ransom note appears with instructions for the user to send money.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
CVE-2019-3396 Redux: Confluence Vulnerability Exploited to Deliver Cryptocurrency Minor with Rootkit (May 7, 2019)
Alert Logic has identified a vulnerability, registered as “CVE-2019-3396,” in Atlassian Confluence Server being exploited in the wild. The vulnerability resides in the “Widget Connector” macro and is being exploited to drop “Gandcrab” ransomware. Along with dropping ransomware, attackers are also exploiting the vulnerability to deliver cryptocurrency-mining malware combined with a rootkit. The rootkit enables the attacker to avoid detection. The attack utilizes Pastebin as a Command and Control (C2) server to download malicious scripts and an actor-controlled domain to download and execute malware.
Click here for Anomali recommendation
MITRE ATT&CK: Exploitation of Vulnerability (ATT&CK T1068)
Turla Backdoor Deployed in Attacks Against Worldwide Targets (May 7, 2019)
Researchers have identified a back, attributed to the threat group “Turla,” that is targeting Microsoft Exchange mail servers. Turla is a Russian-based cyberespionage group, known for attacking a wide range of targets located in over 40 countries. The backdoor has the ability to extract data, read emails,, and send emails. Using the Exchange Server Transport Agent, the malware is able to appear legitimate and go undetected for a long period of time. The backdoor is sent to victims in the form of a JPG or PDF attachment, with the commands encoded using steganography. The use of the Exchange Server Transport Agent makes it more difficult to remove the malware as deleting the infected files will prevent users in the organization from sending and receiving emails.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
Card Skimming Hack Targets 201 Campus Stores in North America (May 6, 2019)
Trend Micro researchers have identified a threat group, dubbed “Mirrorthief” utilizing card skimming techniques used by the financially-motivated threat groups referred to as “Magecart,” to steal payment card information from college campus online stores. Researchers found that Mirrorthief conducted their payment card theft on April 14 by targeting said college/university stores located in Canada and the United States. Injecting scripts into the checkout pages of the sites, the attackers were able to steal addresses, card details, names, and phone numbers. PrismRBS, who developed the checkout pages, learned of the attack on April 26, and subsequently contacted customers, law enforcement and card providers.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064)
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
The Advanced Persistent Threat (APT) group, “FIN7,” is believed to be a Russia-based group. The group is financially motivated and has been conducting multiple spear phishing campaigns that target government organizations as well as public and private businesses. Researchers believe that FIN7 is associated with another Russian APT group called, “Carbanak” because they use the same backdoor malware.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



