Weekly Threat Briefing: Tor Weaponized to Steal Bitcoin
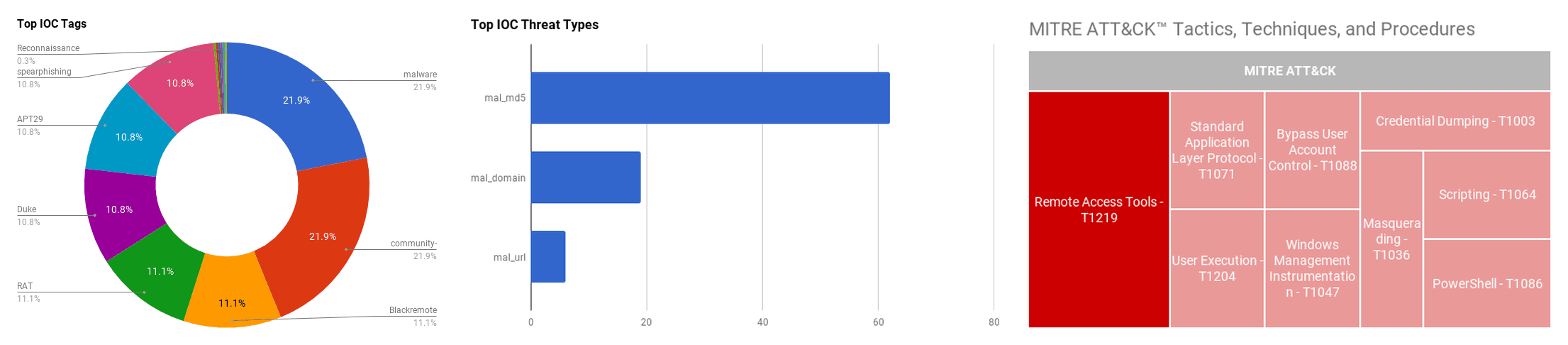

The intelligence in this week’s iteration discuss the following threats: APT29, Bitcoin theft, Blackremote, FTCode ransomware, Operation Ghost, and SDBot. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Researcher Discovers Critical Linux WiFi Vulnerability That Existed For Four Years (October 21, 2019)
A critical Linux WiFi vulnerability has been discovered that could allow attackers to compromise vulnerable machines. The Linux WiFi vulnerability has existed for about four years, according to the researcher that identified the flaw, Nico Waisman. The vulnerability “CVE-2019-17666” exists in the “rtlwifi” driver, which is a software component used to allow certain Realtek WiFi modules, used in Linux devices, to communicate with the Linux operating system. According to Waisman, the vulnerability may lead to remote code execution upon exploit, but is still working on a proof-of-concept. Versions through 5.3.6 of the Linux kernel operating system are impacted, and only affects devices using the Realtek chip. A fix has been proposed by the Linux kernel team, but has not yet been released.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools - T1219
FTCode Ransomware Drops, Rocks, & Locks Files (October 18, 2019)
Office 365 customers in Italy are being targeted with “FTcode” ransomware in an email phishing campaign that plays German rock music while encrypting files on the victim's computer. Security analysts at AppRiver report that the malicious emails contain files posing as “resumes, invoices, or document scans”. In one instance, whilst monitoring for new variants, researchers discovered a Visual Basic file launches PowerShell to download and play an .mp3 file from archive.org. As a mix by Rammstein plays, the script reaches out to a domain to pull down a “Jasper” malware loader, enabling the threat actors to load the desired ransomware. Upon encrypting the file types, they will be renamed to an .ftcode extension. A note will be left on the desktop of the machine instructing the user to download, install, and visit an onion site for further instructions. The cost of the ransom is set at $500 USD if paid within the first three days, after which time the ransom increases to $25,000 USD.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] User Execution - T1204
Tor Weaponized to Steal Bitcoin (October 18, 2019)
Researchers at ESET have discovered an ongoing Bitcoin theft campaign targeting Russian individuals interested in downloading the privacy-oriented Tor browser. The campaign, which appears to have been active since 2017, uses a series of steps to convince users to install a malicious version of Tor masquerading as a Russian language version of the browser. Settings and extensions loaded within the malicious browser allow the criminals to manipulate the pages displayed to users, leading them to sites that take Bitcoin from wallets without the owners' permission. According to ESET malware researcher Anton Cherepanov, the JavaScript payload seen delivered by the malicious websites attempts to alter Bitcoin wallets located on three of the largest Russain-speaking darknet markets.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Masquerading - T1036
Operation Ghost: The Dukes aren’t back - they never left (October 17, 2019)
ESET researchers have identified three new malware families that they attribute to Advanced Persistent Threat (APT) group “The Dukes,” or more commonly known as “APT29.” The researchers believe that the newly identified implants, dubbed “PolyglotDuke”, “RegDuke” and “FatDuke”, show that APT29 have been targeting Ministries of Foreign Affairs as recently as June 2019, proving that the threat group remains an active threat. The most recent campaign tactics show many similarities to previous APT29 activities, such as the use of Twitter to host Command and Control (C&C) URLs and steganography in images to hide payloads and C&C communications. APT29 have mostly disappeared from public reports, leading researchers to believe that the threat group had stopped its activities, but these new findings show that APT29 have been flying under the radar while continuing to compromise high-value targets.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping - T1003 | [MITRE ATT&CK] Windows Management Instrumentation - T1047
New SDBot Remote Access Trojan Used in TA505 Malspam Campaigns (October 16, 2019)
The financially-motivated threat group TA505, have been discovered utilizing new malware variants spreading via phishing campaigns, they include a downloader called “Get2” and a Remote Access Trojans (RAT) called “SDBot” according to Proofpoint researchers. Get2 is being used to send other RAT malware payloads to an individual's machine, these include FlawedAmmyy, FlawedGrace and snatch. SDBot is being used as a second-stage payload to compromise users machines. It was noted in early September 2019 that phishing emails containing the Get2 malware began to be used by TA505 to target financial institutions in Georgia, Greece, Lithuania, Singapore, Sweden and the United Arab Emirates (UAE), among others. It had been noticed from Proofpoint researchers that thousands of emails were being targeted towards Canadian and U.S sectors by distributing Microsoft excel and .ISO attachments.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Bypass User Account Control - T1088 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] Remote Access Tools - T1219
Over 100 Million IoT Attacks detected in 1H 2019 (October 16, 2019)
Kaspersky researchers have said their honeypots have detected a total of more than 105 million attacks that originated with 276,000 unique IP addresses. Compared to the 1st half of 2018 with 12 million attacks and 69,000 IP addresses detected, this is a massive difference. This surge could be the result of large number of users transitioning to smart devices and with many not having strong in-build security. There has been a consistent use of Mirai-like attacks where devices with weak default logins are taking advantage of and converted into remotely controlled bots that become part of a botnet to launch Denial-of-Service (DDoS) and other attacks. China has been the largest target making up 30%, with Brazil second at 19%.
Click here for Anomali recommendation
Streaming Devices Track Viewing Habits, Study finds (October 16, 2019)
It has been revealed by a study conducted by researchers from Princeton University and University of Chicago that certain streaming devices are tracking the viewing habits of its users. The research found that streaming devices Roku and Amazon Fire TV had widespread tracking on its platforms. 69% of Roku channels had trackers in-place whereas AmazonFire TV had 89% of its channels being tracked. Both of these devices are referred to what is called Over-The-Top (OTT) devices which allow smart features to be added to your TV, online streaming libraries being of focus.
Click here for Anomali recommendation
Blackremote: Money Money Money – A Swedish Actor Peddles an Expensive New RAT (October 15, 2019)
In September 2019, Unit 42 researchers discovered a new, undocumented commodity Remote Access Tool (RAT) that was observed in more than 2,200 attack sessions within the first month of it being sold. The RAT, dubbed “Blackremote,” has been promoted on dark web forums and on a sale site since September 2019 by the author, an unidentified 18-year old Swedish citizen, and time-limited licenses can be purchased using cryptocurrencies such as Bitcoin. The features of the RAT include keystroke capture, remote audio, remote desktop, remote file manager, and remote webcam. The author describes the tool as being able to, “give you full access and control over a remote machine through a countless number of features, giving you the ability to monitor, access or manipulate every activity and data remotely, just like you are in front of it!” Unit 42 have reported their findings, including the identity of the author, to the proper authorities.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Remote Access Tools - T1219
Argentinian Security Researcher arrested after Tweeting about Government Hack (October 15, 2019)
The security researcher Javier Smaldone has recently been detained by Argentinian police with his home being raided on suspicion of breaching government systems and the leaking government data. On release, Javier published court documents regarding his arrest on Twitter which stated that the authorities believe Javier had been part of a government attack,only because of tweet that he had posted regarding the attack. Javier a known cyber activist in Argentina,describes the situation as political persecution and believes that his arrest and the raid on his home is the government acting out in revenge for Javier’s criticisms of the Argentinian government and its practices.
Click here for Anomali recommendation
Global Shipping Firm Pitney Bowes Affected by Ransomware Attack (October 14, 2019)
Pitney Bowes, a global mailing and shipping company has announced that it has been hit by a ransomware attack which encrypted certain systems. This resulted in a temporal system outage that affected customer access to various services. Pitney Bowes provides data, e-commerce, financial services, mailing and managing transactions for over 1 million clients which includes a large majority of Fortune 500 companies.This ransomware attack doesn’t come long after recent publications from the FBI regarding the increased numbers of ransomware attacks.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



