Weekly Threat Briefing: US Military Veterans Targeted By Iranian State Hackers
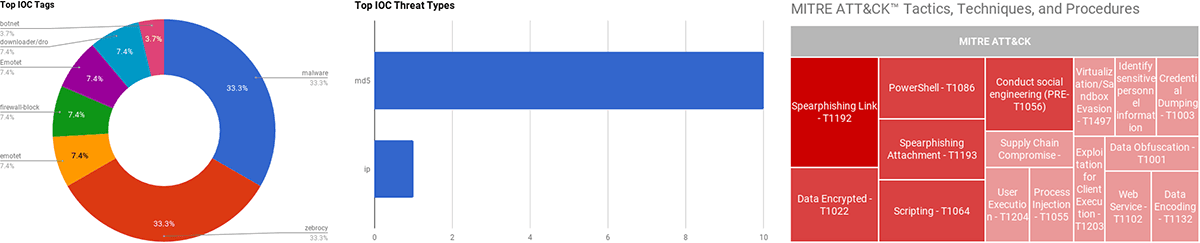

The intelligence in this Weekly Threat Briefing discusses the following threats: APT10, China, DoorDash, Emotet, Fancy Bear, Gandcrab, Malvertising, Nodersok, PcShare, REvil, Ryuk Ransomware, Sednit, Sofacy, Spamouflage Dragon, STRONIUM, Trickbot, Tropic Thunder. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Microsoft Spots Nodersok Malware Campaign That Zombifies PCs (September 26, 2019)
“Nodersok” is a new fileless malicious campaign discovered by Microsoft Defender ATP Research Team. It drops LOLBins with a Node.js-based malware which infects Windows machines and turns devices into proxies. Nodersok is delivered through drive-by downloads, which compromises the target's web browser. This leads to the download of a HTA file delivered either by the user clicking on a malicious link or malvertising. The actors use legitimate Windows tools to spread infections across networks.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] PowerShell - T1086
Research Outs Poorly Constructed Disinfo Campaign Aimed At Hong Kong Protests (September 26, 2019)
The research team from Graphika have detected a poorly conducted disinformation campaign aimed at Hong Kong protestors according to CyberScoop. The content and user accounts have been taken down by Facebook, and Twitter has taken down some of the accounts. The campaign called “Spamouflage Dragon” by Graphika appears to be acting in the interest of the Chinese Government. The badly planned campaign could be indicative of poorly invested resources and could show a lack of maturity although a ready interest in this type of activity.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056)
Microsoft rushes out patch for Internet Explorer zero‑day (September 26, 2019)
A new Zero-Day vulnerability labelled as CVE-2019-1367, has been patched by Microsoft. It is a remote code execution vulnerability and it affects IE version 9, 10 and 11. It gives the attacker the ability to gain the same access privileges as the user. So if the user has admin access then the attacker can have access to the whole system. This bug has prompted a warning from the United States Cybersecurity and Infrastructure Security Agency (CISA).
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Web Service - T1102
Chinese Hackers Hit Technology Firms in Southeast Asia With PcShare Backdoor (September 26, 2019)
BlackBerry Cylance security researchers have detected a campaign, that they believe originates from China, targeting Southeast Asian technology firms. The actors are taking advantage of the built-in Narrator “Ease of Access” feature in Windows, by replacing it with a trojanized screen reader application. The trojanized Narrator executable is just one of the post exploitation tools used by the actors that share code found in Chinese programming sites. The malware used in the campaign is executed through DLL-Side-loading, specifically using the NVIDIA Smart Maximise Helper Host application. PcShare is a Chinese backdoor that is open source, and was found to be used across multiple organisations in this campaign. The actors continue to modify the fake Narrator app to suit its target victims. BlackBerry Cylance researchers have drawn similarities in this campaign to known Chinese APT Tropic Thunder.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Process Injection - T1055 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] File Deletion - T1107
Airbus Hit By Series of Cyber Attacks On Suppliers (September 26, 2019)
According to the French news channel France24, security sources have revealed that a number of organisations in the Airbus supply chain have been targeted with cyber attacks. It is believed that the actors were attempting to capture sensitive industry information. Several sources believe that the activity is likely to have originated from Chinese threat actor APT10.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise - T1195
DoorDash Confirms Data Breach Affected 4.9 million Customers, Workers and Merchants (September 26, 2019)
The food delivery company DoorDash has had a data breach according to TechCrunch. The breach happened on May 4th and it took the company more than five months to detect it. New customers who joined before the 5th of April 2018, have had sensitive information such as email address, home address, phone numbers, order history and the last four digits of their card numbers taken. Salted passwords were also taken. Staff members who were delivery drivers also had their license number taken
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE PRE-ATT&CK] Identify sensitive personnel information (PRE-T1051)
US Military Veterans Targeted By Iranian State Hackers (September 25, 2019)
According to Cisco Talos researchers, Iran's government-backed hackers have been trying to infect US military veterans. The actors created a spoof application purporting to be an App designed to help veterans find employment. The application sends sensitive information about the machine and the network it is connected to, before downloading a Remote Access Trojan (RAT). Researchers say the actors were likely hoping the victim would download the application on the DOD network. The Talos team have linked the campaign to the Tortoiseshell group - believed to be an Iranian government backed hacking group.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE ATT&CK] System Information Discovery - T1082
GandCrab Developers Behind Destructive REvil Ransomware (September 25, 2019)
Secureworks research team have assessed that the GandCrab group “Gold Garden” is still active and that they are probably behind a new ransomware variant called “REvil”. REvil first appeared in April 2019, and has been targeting Texas municipalities and dentist offices. There are code similarities between GandCrab and REvil, and they both contain code that prevents the malware from infecting machines in Russia. REvil has quickly become one of the most dangerous ransomwares in the wild.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force - T1110 | [MITRE ATT&CK] Exploitation for Client Execution - T1203
Tibetan Groups Targeted with 1-Click Mobile Exploits (September 24, 2019)
Senior members of the Tibetan community were targeted with cyber attacks between November 2018 and May 2019. The Private Office of His Holiness the Dalai Lama, the Central Tibetan Administration, the Tibetan Parliament, and Tibetan human rights groups were all targeted during this time. Toronto based, Citizen Labs report shows the level of effort taken during the campaigns to infect the targets. Sophisticated social engineering attempts through whatsapp conversations about recent events and activities related to the target groups. These conversations were used to dupe the victim into clicking on a link which would then use web browser exploits to install android and ios malware. The malware used to conduct the browser exploits was called POISON CARP and the Android and iOS exploit kits is dubbed “MOONSHINE” by Citizen Labs.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link - T1192 | [MITRE PRE-ATT&CK] Conduct social engineering (PRE-T1056) | [MITRE MOBILE-ATT&CK] Malicious Web Content (MOB-T1059)
No summer vacations for Zebrocy (September 24, 2019)
The threat group APT28 (Sofacy, STRONIUM, Sednit or Fancy Bear) initiated a new campaign over the summer which was detected by the ESET security team. According to ESET researchers APT28 have targeted Ministries of Foreign Affairs across Eastern Europe and Central Asia much like previous campaigns. One of the distinctive aspects of this campaigns appears to be a development in the threat groups toolset; their downloader has been developed using the NIM programming language. However ESET researchers have observed that the campaign tactics of this group are quite “loud”. This is because the victim will have several downloaders installed on their machine before the final backdoor payload.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment - T1193 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Data Encrypted - T1022
Mapping the Connections Inside Russia's APT Ecosystem (September 24, 2019)
The Russian based APT groups Turla, Sofacy and APT29 have been mapped in a joint research effort between Intezer and Check Point Research. The research teams analysed around 2,000 samples attributed to Russia and discovered 22,000 connections. One of the most startling findings was that the threat groups operating out of Russia do not appear to share code with one another. The researchers also found that each actor working for Russia had its own malware development team. A detection tool has been created from this research for people to download.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping - T1003
Emotet Malspam Campaign Uses Snowden’s New Book As Lure (September 23, 2019)
Emotet resumed its activity one week ago after months of dormancy. Emotet is considered one of the most prolific threats to organizations over this last year. Whilst Emotet continued to use old methods to trick users, by incorporating invoice themed subject lines (for example). It was found to have used Edward Snowden’s new book “Permanent Record” as a lure this week. Emotet has a large and successful botnet behind it and is usually followed up by a further infection after initial compromise. Malware such as Trickbot or Ryuk Ransomware can infect an end point after compromise. Emotet has been particularly up to date with the themes of its lure.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell - T1086 | [MITRE ATT&CK] Spearphishing Attachment - T1193
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



