Weekly Threat Briefing: Apple “chaiOS” Flaw Can Crash Your iPhone and macOS with a Single Text Message
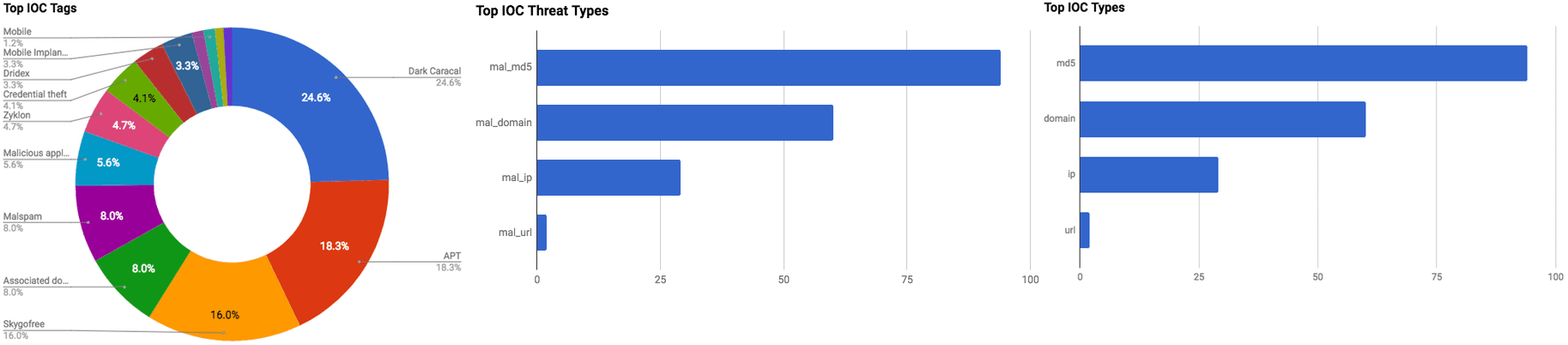

The intelligence in this week’s iteration discuss the following threats: APT, Banking trojan, Data breach, Data theft, Malspam, Phishing, Spyware, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Half of Norway’s Population May Have Been Breached (January 22, 2018)
On January 8, 2018, the security team (HelseCert) for Norway’s healthcare provider “Helse Sør-Øst RHF” (Health South-East RHF) notified Helse IT delivery partner “Sykehuspartner HF” of “abnormal activity.” On January 15, 2017, Helse released a statement in which the company confirmed that it had suffered a data breach by an “advanced and professional” threat actor or group. Helse provides healthcare for the most-populous section of Norway that includes approximately three million people out of a country with a population of approximately five million. At the time of this writing, it is unknown if the actor/group managed to steal any Personally Identifiable Information (PII), and authorities are continuing their investigation of this incident.
Click here for Anomali recommendation
Apple “chaiOS” Flaw Can Crash Your iPhone and macOS with A Single Text Message (January 21, 2018)
Security researcher Abraham Masri discovered a vulnerability, dubbed “chaiOS Text Bomb,” that is located in Apple operating systems iOS and macOS. The vulnerability can be exploited to freeze or force a crash on an iPhone, iPad, or Mac. The vulnerability can be exploited by an actor by sending a text message that provides a link to a webpage that hosts JavaScript code. Apple’s iMessage application cannot handle the JavaScript code which leads to a crash or perpetual reboot loop of the applications.
Click here for Anomali recommendation
OnePlus Confirms Hack Exposed Credit Cards of Phone Buyers (January 19, 2018)
The China-based smartphone manufacturing company “OnePlus” has confirmed that its systems were breached by an unknown actor(s). On January 19, 2017, the company began emailing its customers to warn them about the incident after multiple individuals who purchased OnePlus phone reported fraudulent credit card transactions. The company discovered that a malicious script had been inserted on the company’s pages that would steal any data that was entered. The affected data consists of credit card numbers, expiry dates, and security codes.
Click here for Anomali recommendation
New Year, New Look – Dridex via Compromised FTP (January 18, 2018)
A new malspam campaign has been identified to be distributing a variant of the “Dridex” banking trojan, according to Forecepoint researchers. The actors behind this campaign are using compromised File Transfer Protocol (FTP) to host the malicious documents in the malspam emails. Two different types of malicious documents were observed in this campaign. One is a DOC file that abuses Microsoft’s Dynamic Data Exchange (DDE) feature to execute a shell command to download Dridex. The second is an XLS file with a malicious macro that downloads Dridex from an actor controlled domain.
Click here for Anomali recommendation
Researchers Uncover Government-Sponsored Mobile Hacking Group Operating Since 2012 (January 18, 2018)
Lookout and Electronic Frontier Foundation (EFF) have released a joint report discussing the discovery of an Advanced Persistent Threat (APT) they have dubbed “Dark Caracal.” The researchers believe that the group has been active since at least January 2012 and is believed to be operating out of a building that belongs to the Lebanese General Security Directorate (GDGS). The group appears to be primarily focused on malicious activity associated with mobile devices and is believed to have conducted a global campaign called “Operation Manul” with their custom malware called “Pallas.” Dark Caracal distributes their malware via malicious applications located in third-party application stores. The group has targeted defense contractors, financial institutions, governments, manufacturing companies, militaries, and utilities around the world.
Click here for Anomali recommendation
Downloaders on Google Play Spreading Malware to Steal Facebook Login Details (January 18, 2018)
Numerous malicious applications have been identified on the Google Play store, according to Avast researchers. The applications are capable of downloading additional applications that masquerade as Android system applications. Some of the applications were observed to be capable of stealing user credentials, specifically, for Facebook. The malicious applications purport to be various legitimate applications such as barcode scanners, a chess game, and voice recorders that target English and Vietnamese-speaking Android users. Upon download of one of the applications, a user will be requested to enable “Google Play services” which, if not granted, will perpetually display fake crash popups. If the fake Google Play services is enabled, a user will be shown dialogue boxes that claim there is an error with their Facebook account and to enter credentials to fix the issue.
Click here for Anomali recommendation
Exobot Author Calls It Quits and Sells Off Banking Trojan Source Code (January 17, 2018)
Security researchers have observed that the creator of a sophisticated Android banking trojan, called “Exobot,” is offering the source code of his/her malware for purchase on an underground forum. Exobot dates back to June 2016, and prior to this sale offer the malware author never allowed actors access to the source but rather allowed a “renting” access. Actors would pay a fee to gain access to configuration panels to create malicious applications with custom settings which would then be distributed to infect users with Exobot. Exobot has been one of the more active Android mobile trojans for the past two years. Now with an actor’s ability to purchase the code, and potentially leak it to open sources, malicious activity associated with Exobot will likely increase.
Click here for Anomali recommendation
A Coin Miner with A “Heaven’s Gate” (January 17, 2018)
Malwarebytes Labs researchers have published information regarding a new technique being used by threat actors to steal cryptocurrency. The technique itself, called “Heaven’s Gate,” is not a new technique as it dates back to 2009, however, it appears to be new in regards to being used to steal cryptocurrency. Heaven’s Gate is a technique that can allow software to call 64-bit code from a 32-bit process which can bypass API hooks often used in detection software. The actor’s objective in this campaign is to change the wallet location to one they control to steal cryptocurrency.
Click here for Anomali recommendation
Cisco Releases Security Updates (January 17, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding vulnerabilities in multiple Cisco products. The US-CERT states that a threat actor could exploit one of these vulnerabilities to take control of an affected system. The vulnerabilities are listed as follows: Email and Content Security Management Appliance Privilege Escalation, NX-OS Software Pong Packet Denial of Service, and Unified Customer Voice Portal Denial of Service.
Click here for Anomali recommendation
Microsoft Office Vulnerabilities Used to Distribute Zyklon Malware in Recent Campaign (January 17, 2018)
FireEye researchers have discovered a new malicious campaign in which threat actors are distributing the open-source “Zyklon” malware via spam emails. The spam emails were observed to contain zip file attachments that contain a malicious lure DOC file that exploit vulnerabilities in Microsoft Office registered as CVE-2017-11882 and CVE-2017-8759; the attachment was also observed using Office’s Dynamic Data Exchange (DDE) feature to begin the download process of a Zyklon payload. Zyklon is a backdoor that is capable of multiple malicious features which include conducting Distributed Denial-of-Service (DDoS) attacks, downloading and executing additional plugins, keylogging, stealing passwords, and self-updating and self-removal.
Click here for Anomali recommendation
Skygofree: Following in the Footsteps of Hacking Team (January 16, 2018)
A new family of malware, dubbed “Skygofree,” has been identified in the wild and is primarily targeting individuals located in Italy, according to Kaspersky Lab researchers. The malware is capable of infecting Android and Windows devices.The researchers first discovered the malware in October 2017, and identified that the first variants of Skygofree were created in 2014. Additionally, it appears that the actors behind the malware have been updating Skygofree since said time, however, the oldest domains associated with this campaign date back to 2015. The malware is distributed via landing pages that load the malware implant on to a visiting Android device. Researchers note that Skygofree is one of the most powerful spyware tools that they have observed. Some of the capabilities of Skygofree include complex payload structures, never-before-seen-surveillance features, using multiple exploits, and recording surrounding audio.
Click here for Anomali recommendation
Phishers Target Netflix Users, Ask for Info and Photo of Their ID (January 16, 2018)
Researchers have observed yet another phishing campaign that is targeting Netflix users. The actors behind this campaign are distributing emails that purport to be from Netflix, however, upon closer inspection of the email subject line reveals that Netflix is spelled with the Greek letter chi which appears similar to a larger “X.” The content of the message claims that the Netflix user needs to update their billing information and provides a link for the recipient to follow. If the link is followed, a user will be taken to a compromised HTTPS website that redesigned to impersonate Netflix’s login page. The “login” page requests billing address, Netflix credentials, payment card information, and a picture of themselves holding an identification card.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



