Weekly Threat Briefing: APT15 is Alive and Strong: An Analysis of RoyalCli and RoyalDNS
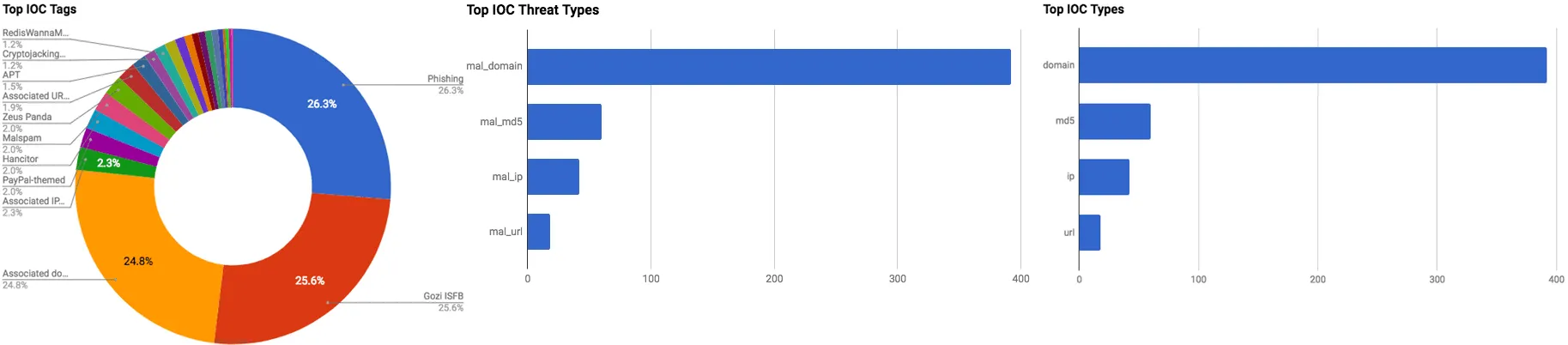

The intelligence in this week’s iteration discuss the following threats: APT, Backdoor, Banking trojan, Cryptocurrency malware, Malspam, Mobile malware Phishing, Spear phishing, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
APT15 is alive and strong: An analysis of RoyalCli and RoyalDNS (March 10, 2018)
While investigating an incident in May 2017; NCC Group’s Incident Response team discovered that their client had been compromised by the Advanced Persistent Threat (APT) group “APT15” (GREF, Ke3chang, Mirage, Playful Dragon, Vixen Panda). The response team found that APT15 had compromised their client’s network and managed to steal “a number of sensitive documents” via three backdoors. The first backdoor, called “BS2005,” is known to be used by the group, however, two new backdoors dubbed “RoyalCli” and “RoyalDNS” were also observed. NCC Group believes that APT15 was targeting data related to U.K. government departments and military technology.
Click here for Anomali recommendation
The Slingshot APT FAQ (March 9, 2018)
A new Advanced Persistent Threat (APT) group, dubbed “Slingshot,” has been identified and found to have been active since at least 2012, according to Kaspersky Lab researchers. The researchers discovered the cyber espionage group while investigating an incident involving a keylogger which led to the finding of a malicious library that could interact with a virtual file system; a sign indicative of APT activity according to researchers. The primary initial infection vector for the group has not yet been identified. However, researchers did find some cases in which the group gained access to “Mikrotik” routers and placed a component downloaded by “Winbox” loader (Mikrotik management suite) to infect the router administrator. Approximately one hundred targets have been identified that are located mainly in Africa and the Middle East.
Click here for Anomali recommendation
Hidden Cobra Targets Turkish Financial Sector With New Bankshot Implant (March 8, 2018)
The Advanced Persistent Threat (APT) group “Hidden Cobra” (Lazarus Group) is continuing their targeting of cryptocurrency organizations and financial institutions with a recently observed attack on a Turkish financial system, according to the McAfee Advanced Threat Research team. Hidden Cobra was able to gain unauthorized access to an unnamed Turkish financial institution via a new variant of the group’s custom “Bankshot” implant that was distributed via spear phishing emails. The spear phishing emails contain Microsoft Word document with an embedded Adobe Flash exploit that exploits the vulnerability registered as “CVE-2018-4878” that can allow an actor to execute arbitrary code.
Click here for Anomali recommendation
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits (March 8, 2018)
Imperva researchers have published information regarding a cryptojacking campaign that is targeting both application and database servers. One of these observed campaigns, dubbed “RedisWannaMine,” is reported to be responsible for approximately “90% of all remote code execution attacks in web applications.” The threat actors behind this campaign are using remote code execution vulnerabilities, one of such is “CVE-2017-9805,” (REST plugin vulnerability in Apache Struts) to download and execute an external resource. In Imperva’s given example, the external resource was found to be located on a remote host and included a list of files. One of the said files was a shell script that downloads a crypto-miner. Other techniques observed in these campaigns include downloading the open source tool “masscan” from GitHub, and launching a process called “redisscan.sh” which utilizes masscan to scan the internet with the objective of infecting publicly available “Redis” servers with crypto-mining malware. Furthermore, researchers also observed this campaign using the “EternalBlue” Server Message Block (SMB) exploit.
Click here for Anomali recommendation
Hardcoded Password Found in Cisco Software (March 8, 2018)
Cisco has released 22 security advisories that address vulnerabilities in their products, two of which are rated critical. The first critical vulnerability, registered as “CVE-2018-0141,” affects Cisco’s “Prime Collaboration Provisioning” (PCP). A threat actor could exploit this vulnerability by connecting to the affected systems via Secure Shell (SSH) using the hardcoded password to gain full control over the system. Researchers note this vulnerability can only be exploited by local threat actors. The second vulnerability, registered as “CVE-2018- 0147,” affects Cisco’s Secures Access Control Systems (ACS) and can be exploited when ACS attempts to deserialize user-supplied Java-serialized content. This would allow an actor to execute arbitrary code without the need for user credentials.
Click here for Anomali recommendation
Hancitor Malspam – Fake PayPal Notice (March 7, 2018)
Security researcher have observed that the “Hancitor” (malicious downloader) malspam campaign has begun distributing PayPal-themed Word documents with the object of installing the “Zeus Panda” banking trojan. The emails purport to come from “PayPal Invoice Service” and claim that the recipient has been sent an invoice. The PayPal-themed email also provides a link for the recipient as well as a due date to instill a sense of urgency. If the link is followed, a recipient will be asked to open or save the Word document. If opened, the document requests that “Enable Editing” be clicked that, if clicked, will launch a malicious macro which will begin the infection process for Zeus Panda.
Click here for Anomali recommendation
Exim vulnerability opens 400,000 servers to remote code execution (March 7, 2018)
Security researchers have discovered that the “Exim” mail transfer agent is vulnerable to a remote code execution vulnerability, specifically if Exim is used on Unix-like systems. The buffer overflow vulnerability, registered as “CVE-2018-6789,” was discovered and reported by Meh Chang of the DEVCORE research team in February. Researchers note that this vulnerability is present in all Exim versions prior to version 4.90.1, which at the time of DEVCORE’s publication discussing the vulnerability, was reported to affect approximately 400,000 Exim servers.
Click here for Anomali recommendation
Patchwork Continues to Deliver BADNEWS to the Indian Subcontinent (March 7, 2018)
The threat group called “Patchwork,” which was first discovered in December 2015, has been observed conducting cyber espionage campaigns against targets located in the Indian subcontinent. The group is distributing their custom “BADNEWS” malware via two Encapsulated PostScript (EPS) exploits (CVE-2015-2545, CVE-2017-0261) that are packaged into legitimate documents. The documents have been observed to be themed after topics such as information related to the Pakistan Energy Commission and Ministry of the Interior, and military promotions within the Pakistan Army. BADNEWS functions as a backdoor that can grant actors control of an affected machine. Researchers note that this version of BADNEWS is different than prior iterations which indicates that the group is increasing in sophistication.
Click here for Anomali recommendation
Gozi ISFB Remains Active in 2018, Leverages “Dark Cloud” Botnet For Distribution (March 6, 2018)
Cisco Talos researchers have discovered several new “relatively low-volume” malware campaigns in which actors are using the “Dark Cloud” botnet to distribute the “Gozi ISFB” banking trojan. Researchers have found that the actor(s) behind this campaign distributing a low-volume of spam emails with a focus on creating more convincing emails to increase the likelihood of a recipient opening a malicious attachment. In addition, these emails are only being distributed to specific organizations, and out of more than 100 emails and their attachments that were analyzed the majority of them are unique. The file attachments are Microsoft Word documents which the text of the emails purport to be related to a sales order. If the attachment is opened, it asks the user to “Enable Editing” and then to “Enable Content.” If these are enabled, malicious macros will begin the infections process for Gozi ISFB.
Click here for Anomali recommendation
Coins LTD Campaign Uses Rig EK to Push Ursnif (March 5, 2018)
Security researchers have found that the “Coins LTD” malspam campaign, which uses cryptocurrency-themed emails and domains to deliver malware, is now delivering the “Ursnif” banking trojan. Prior to this, the Coins LTD campaign was observed distributing malicious attachments and links to malicious domains that attempt to infect uses with the “Ramnit” and “Trickbot” banking trojans. Currently, this malspam campaign is attempting to direct recipients to malicious websites that host the Rig Exploit Kit (EK) that uses an Adobe Flash exploit to drop Ursnif.
Click here for Anomali recommendation
Triada Trojan Pre-Installed on Low Cost Android Smartphones (March 5, 2018)
The “Triada” trojan, first discovered in early 2016, has been identified to come preinstalled on some lower-cost Android smartphones, according to Dr. Web researchers. Affected models include the following: Leagoo M5 Plus, Leagoo M8, Nomu S10, and the Nomu S20, among others which brings the overall amount to over 40 devices. Triada injects its module into the Zygote process on Android devices to infiltrate all applications running on a device. The malware is able to download and launch other applications, redirect SMS transactions to buy content or steal money directly from the owner of the affected device. Dr. Web researchers found that devices that were launched as recently as December 2017 were observed to come preinstalled with Triada.
Click here for Anomali recommendation
Sure, I’ll take that! New ComboJack Malware Alters Clipboards to Steal Cryptocurrency (March 5, 2018)
Palo Alto Unit 42 researchers have discovered a new cryptocurrency-stealing malware, dubbed “ComboJack,” that is being distributed by threat actors via a malspam campaign. Proofpoint and Unit 42 researchers observed that the malspam emails purport that the sender has found a passport in her/his office, and asks the recipient to open the attached PDF file to check if he/she knows the owner. If the PDF attachment is opened, a user will be presented with a single line of text that refers to an embedded doc file. The doc file is an embedded HTA file that contains Powershell commands that, if the file is opened, will begin the infection process for ComboJack. Combojack targets popular digital payment systems such as “WebMoney” and Yandex Money by entering a loop in which every half second it checks the affected machine’s clipboard for data such as wallet information for various currencies.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more


