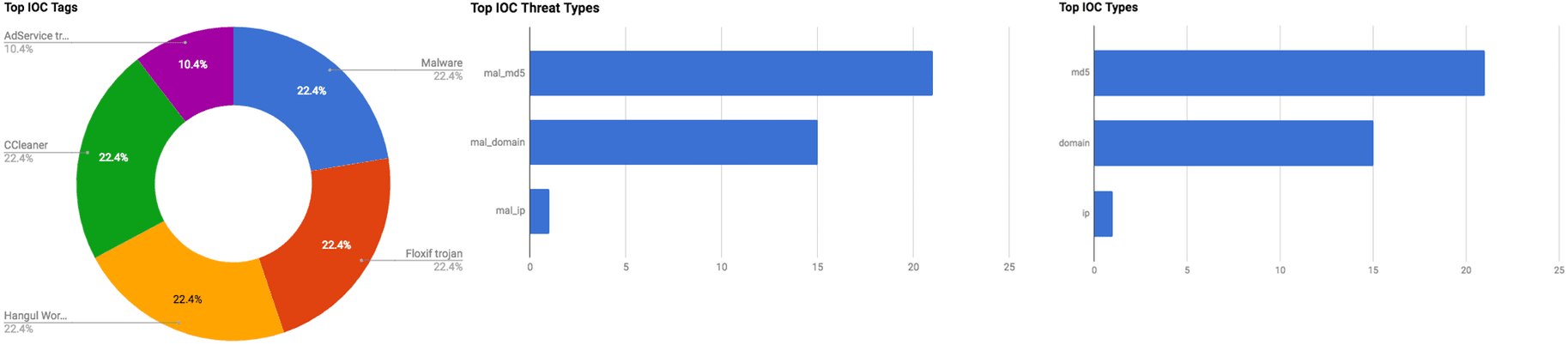

The intelligence in this week’s iteration discuss the following threats: Adware, Compromise, Data Breach, Malspam, Malicious Plugin, Phishing, and Vulnerability. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
CCleanup: A Vast Number of Machines at Risk (September 18, 2017)
The system maintenance application, "CCleaner," has been identified to contain malware, specifically, version 5.33, according to Cisco Talos researchers. The authentic version of CCleaner 5.33 distributed by the software company, "Avast," was found to contain a multi-stage malware payload in addition to the CCleaner application. The malware was found to be the "Floxif" trojan. The downloaded installation executable was signed with a legitimate digital signature that was issued to software company, "Piriform." The affected CCleaner version was released on August 15, and researchers discovered that the malicious version was still hosted on the download servers as recent as September 11, 2017.
Recommendation: Threat actors are willing to go to great lengths to abuse trust relationships in supply-chain attacks. If CCleaner version 5.33 was downloaded it is likely that the machine is infected with malware. As of this writing, detection signatures have been made available by and they should be run against your systems to check for potential malicious activity. Additionally, Piriform suggests that its CCleaner users updated to version 5.34 as soon as possible.
Tags: Compromise, CCleaner, Malicious version, Malware
Poisoned WordPress 'Display Widgets’ Plugin Finally Purged (September 15, 2017)
Since June 2017, approximately 200,000 WordPress sites have been corrupted by a plugin called "Display Widgets," according to Wordfence. Display Widgets was discovered to have been updated with malicious code on multiple occasions. Wordfence CEO, Mark Maunder, warned customers to remove the Display Widgets plugin as soon as possible because the plugin contains a backdoor, allowing the author to publish content on any site with the plugin installed.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Compromised websites, Malicious plugin, Display Widgets
Adware Installs InfoStealer Trojan That Loads via Chrome DLL Hijacking (September 15, 2017)
Researchers have discovered that the "AdService" trojan is being distributed by threat actors via adware bundles. This Trojan performs Dynamic Link Library (DLL) hijacking in Chrome web browsers. AdService is capable of stealing passwords for online accounts such as Facebook and Twitter. AdService uses DLL hijacking to load itself when Chrome is executed and attempts to load a DLL that contains malware. In this instance, AdService is placing a malicious version "winhttp.dll" in the "C:Program Files (x86)GoogleChromeApplication" folder.
Recommendation: The AdService Trojan is installed on a victim's computer via free programs that do not disclose that other software is being installed along with it. All applications should be carefully researched prior to installing on a personal or work machine. Additionally, all applications, especially free versions, should only be downloaded from trusted vendors. If given an option between a "quick/express" installation or a "custom" installation, always choose the custom installation as it is more likely to disclose other applications being installed. If you are installing a desired application, check that you are getting the installer from the author's website and not a third party installer. It is also recommended to have trusted antivirus software installed and that it always kept up-to-date, as AdService is detected by most of the antivirus vendors.
Tags: Adware, Trojan, AdService, Chrome
ExpensiveWall: A Dangerous 'Packed’ Malware on Google Play That Will Hit Your Wallet (September 14, 2017)
More than 100 applications in the Google Play Store have been found to contain a mobile malware family called, "ExpensiveWall," according to Check Point researchers. The malicious applications were identified to have been downloaded approximately 5.9 to 21.1 million times. The malicious code was found to reside within a Software Development Kit (SDK) named, "gtk."ExpensiveWall’s objective is to generate revenue by registering users to premium services and sending premium SMS messages which charge the victim without their knowledge. ExpensiveWall is capable of mimicking clicks on any multi-step procedure as well as hiding confirmation SMS messages. As of this writing, Google has removed the malicious applications from the Google Play Store.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Android, Mobile, Malware, ExpensiveWall
Potential Phishing Scams Related to Equifax Data Breach (September 14, 2017)
The U.S. Federal Trade Commission (FTC) has issued an alert warning individuals to be aware of malicious activity associated with the Equifax breach. The FTC is warning consumers to be aware of potential calls or emails from individuals purporting to be Equifax employees. Equifax representatives will not contact individuals asking to verify their information.
Recommendation: Significant data breaches often result in threat actors attempting to steal information by capitalizing on fear-tactics. Individuals who are concerned about the Equifax breach can check to see if their data may have been affected by using the following website "https://www.equifaxsecurity2017.com/potential-impact/". Furthermore, it is important that individuals understand, as the FTC stated, that Equifax representatives will not contact consumers to verify their information.
Tags: Scams, Equifax, Data breach
Hangul Word Processor and PostScript Abused Via Malicious Attachments (September 14, 2017)
Trend Micro researchers have discovered a new campaign in which actors are exploiting PostScript code in the Hangul Word Processor (HWP) software. Older versions of HWP were discovered to have implemented a branch of PostScript called "Encapsulated PostScript," incorrectly. Encapsulated PostScript adds restrictions to code that can be run within HWP documents. However, the incorrect implementation has caused malicious documents to be capable of dropping malicious files on the affected machine.
Recommendation: All employees should be educated on the risks of malspam, and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided.
Tags: Vulnerability, HWP
Equifax Confirms Apache Struts Security Flaw It Failed to Patch is to Blame for Hack (September 14, 2017)
The consumer credit reporting agency, "Equifax," has confirmed that the breach that affects approximately 143 million individuals was caused by a web server vulnerability in Apache Struts. The vulnerability, registered as CVE-2017-5638, was patched by Apache back in March 2017. The Equifax breach took place from mid-May to July 2017.
Recommendation: Zero-day based attacked can sometimes be detected by less conventional methods, such as behavior analysis, and heuristic and machine learning based detection systems. Threat actors are often observed to use vulnerabilities even after they have been patched by the affected company. As this story portrays, it is crucial that policies are in place to ensure that all employees install patches as soon as they are made available in order to prevent exploitation by malicious actors.
Tags: Vulnerability, Patch
Phishers Targeting LinkedIn Users via Hijacked Accounts (September 13, 2017)
Researchers have identified a phishing campaign in which threat actors are using compromised LinkedIn accounts in attempts to steal credentials. The actors are using LinkedIn’s "InMail" feature to distribute a shortened "Owd[.]ly" link that state that the sender has just shared a document via GoogleDoc/Drive. The link directs recipients to a fake login page for AOL, Gmail, or Yahoo that steals user credentials if entered.
Recommendation: All employees should be educated on the risks of phishing, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. Emails that request that the recipient follow a link that then asks for credentials to be entered is often an indicator of a phishing attack.
Tags: Phishing, LinkedIn, Compromised accounts
Immediately Patch Windows 0-Day Flaw That’s Being Used to Spread Spyware (September 13, 2017)
Microsoft’s "Patch Tuesday" for September addresses 81 vulnerabilities that affect all supported Windows operating systems and other Microsoft products. The vulnerabilities affect eight Microsoft products. 27 of the vulnerabilities are rated critical and 54 are rated important. 39 vulnerabilities could allow an actor to remotely execute code on a vulnerable machine.
Recommendation: Your company should regularly check the software you use in everyday business practices to ensure that everything is always up-to-date with the latest security features. Using the automatic update feature in Windows operating systems is a good mediation step to ensure that your company is always using the most recent version.
Tags: Vulnerabilities, Windows, Malware
BlueBorne Bluetooth Attack Puts 5 Billion Devices at Risk (September 13, 2017)
A new attack vector has the potential to put billions of Bluetooth-enabled devices at risk of compromise, according to Armis researchers. Threat actors could potentially connect to a Bluetooth-enabled device using zero-day buffer overflow vulnerabilities researchers discovered in devices associated with Apple, Google, Linux, Microsoft, and Samsung. The vulnerabilities were reported to said companies who are currently working on patches.
Recommendation: All devices should be kept up-to-date with the latest software versions to use the newest security features implemented in the updated. Additionally, only trusted devices should be connected to via Bluetooth, and Bluetooth should be turned off when not in use.
Tags: Vulnerability, Bluetooth, BlueBorne
Massive ElasticSearch Infected Malware Botnet (September 12, 2017)
Thousands of publicly accessible ElasticSearch nodes have been identified to be hosting variants of Point of Sale (POS) malware, according to Kromtech researchers. Among the ElasticSearch servers, researchers discovered file names that are associated with the AlinaPOS and JackPOS malware families. This discovery coincides with other findings in which new variants of POS malware have been advertised for purchase on various underground forums. As of this writing, approximately 4,000 ElasticSearch servers were found to be infected with POS malware.
Recommendation: This story depicts the potential dangers that may reside in publicly accessible services. A public service that uses some form a authentication should be required if open source resources are being used. Additionally, databases should not be directly accessible over the internet, and they should require a form of authentication to access.
Tags: Breach, ElasticSearch servers, Malware, Botnet
Multiple Vulnerabilities in FreeXL Library (September 11, 2017)
Cisco Talos researchers have released information regarding two remote code execution vulnerabilities in the "FreeXL" library. FreeXL is an open source software that is used to extract data from a Microsoft Excel spreadsheet. The two vulnerabilities can be exploited via a buffer overflow that could possibly allow a threat actor to execute arbitrary code on a machine.
Recommendation: Zero-day based attacked can sometimes be detected by less conventional methods, such as behavior analysis, and heuristic and machine learning based detection systems. Threat actors are often observed to use vulnerabilities even after they have been patched by the affected company. Therefore, it is crucial that policies are in place to ensure that all employees install patches as soon as they are made available.
Tags: Vulnerabilities, FreeXL Library
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



