Weekly Threat Briefing: China-linked APT15 Develops New “MirageFox” Malware
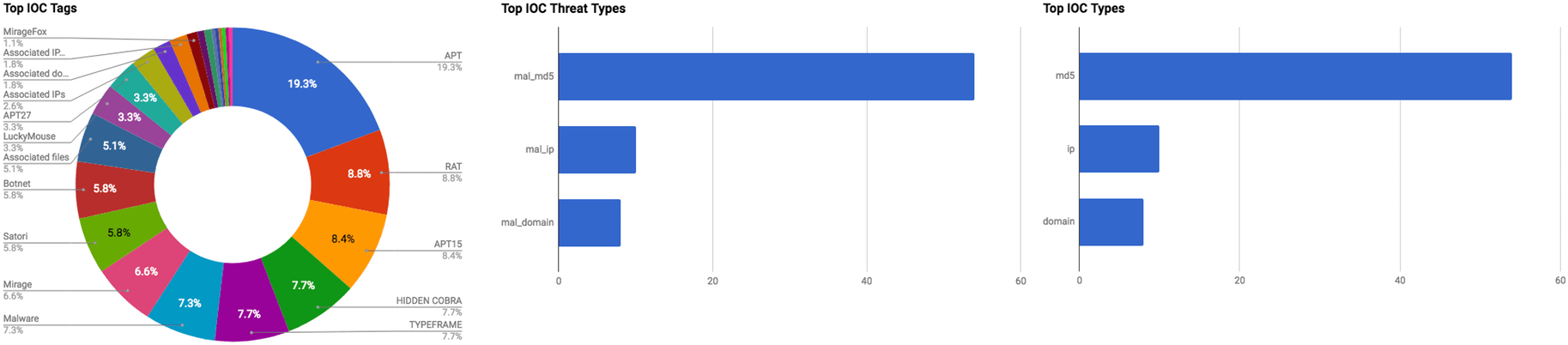

The intelligence in this week’s iteration discuss the following threats: APT, Banking trojan, Backdoor, Botnet, Cryptocurrency-miner, Data breach, Data theft, Misconfigured account, Spear phishing, Ransomware, RAT, Targeted attack and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
China-linked APT15 Develops New “MirageFox” Malware (June 18, 2018)
The Advanced Persistent Threat (APT) group “APT15” has been found to have added a new malware to its arsenal, according to Intezer researchers. The malware, a Remote Access Trojan (RAT) dubbed “MirageFox,” incorporates code from the “Mirage” malware previously attributed to the China-based group (among others), as well as code from the “Reaver” malware known to be used by multiple Chinese threat actors. MirageFox appears to conduct Dynamic Link Library (DLL) hijacking via distributing an authentic McAfee binary to load the DLL into a legitimate-looking process. MirageFox is capable of stealing various forms of information from an infected machine, in addition to installing a backdoor, launching processes, modifying files, and terminating itself.
Click here for Anomali recommendation
Botnets Never Die, Satori REFUSES to Fade Away (June 15, 2018)
One June 14, 2018, Qihoo Lab researchers observed that the “Satori” botnet, a variant of the “Mirai” Internet-of-Things (IOT) malware, was performing a network-wide scan searching for “uc-httpd 1.0.0” devices. Researchers believe that the threat actors are conducting the scanning in search of the vulnerability registered as “CVE-2018-10088” that affects “XiongMai” uc-httpd 1.0.0 devices. Satori is scanning traffic on ports 80 and 8000.
Click here for Anomali recommendation
Cyber Attackers Are Targeting Kiwi Work Printers (June 15, 2018)
HP has addressed the fact that company printers that are connected to the network are the newest Internet-of-Things (IOT) target for threat actors. Many printers are a weak link in an organization and potentially an easy entry point to get access into a network. Actors have noticed that company printers tend to either have no restrictions on access or they are not securely locked down, thus making them accessible to threats. Threat actors can upload malware to a printer which can then infiltrate the rest of a company’s network through the networked-connection. On top of the ability to upload malware via printers, any files sent to and printed off the printers are obtainable for actors who can then use those files as they please.
Click here for Anomali recommendation
DBGer Ransomware Uses EternalBlue and Mimikatz to Spread Across Networks (June 14, 2018)
The “Satan” ransomware, which first appeared in January 2017 on a Ransom-as-a-Service (RaaS) portal, has recently received a few upgrades, according to the security researcher known as “MalwareHunterTeam”. The new features also bring with it a new name “DBGer.” The most notable change to the “product” is its ability to propagate to other machines on the same network. Infecting other devices involves exploitation of Remote Code Execution (RCE) vulnerabilities and using network credentials acquired by the “Mimikatz” tool. DBGer has also incorporated a version of the “EternalBlue” SMB exploit, which was also used in the past by other ransomwares; WannaCry, NotPetya and UIWIX. The list of exploits identified, include: EternalBlue SMB exploit CVE-2017-0143, JBoss CVE-2017-12149, Weblogic XMLDecoder CVE-2017-10271.
Click here for Anomali recommendation
Malware Analysis Report (AR18-165A) MAR-10135536-12- North Korean Trojan: TYPEFRAME (June 14, 2018)
The U.S. Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI), along with other governmental partners, have published a report discussing a new trojan, dubbed “TYPEFRAME,” that is attributed to the Advanced Persistent Threat (APT) “HIDDEN COBRA”, also known as the “Lazarus group.” The group is believed to be sponsored by the Democratic People’s Republic of Korea (DPRK) government. TYPEFRAME is a Remote Access Trojan (RAT) that appears to be distributed via a malicious Microsoft Word document. The malicious executable files were found to have the following capabilities: connect to Command and Control (C2) server to receive additional instructions, download and install malware, install proxy and RAT, and modify an infected user’s firewall to allow incoming connections.
Click here for Anomali recommendation
MysteryBot; A New Android Banking Trojan Ready for Android 7 and 8 (June 14, 2018)
A new Android banking trojan, dubbed “MysteryBot,” has been identified to share a Command and Control (C2) server with in the information-stealing malware “LokiBot,” according to ThreatFabric researchers. The malware is capable of keylogging, injecting overlays to steal banking credentials, and ransomware functionality. MysteryBot has multiple overlays that target numerous financial institutions and other services such as Microsoft Outlook, PayPal, and messaging applications. At the time of this writing, the malware is not widely spread because it is still under development, however, it does appear that MysteryBot is distributed via a fake Adobe Flash Player application.
Click here for Anomali recommendation
Another Potential MuddyWater Campaign Uses PowerShell-based PRB-Backdoor (June 14, 2018)
Trend Micro researchers have published a report discussing another potential occurrence of the “MuddyWater” campaign. MuddyWater is a spear phishing campaign that targets the Saudi Arabian government that was first identified in 2017. In this instance, researchers observed emails themed around a reward or promotion being distributed; this may indicate that the actors behind MuddyWater have expanded their targets to entities that are not directly associated to the Saudi Arabian government. The emails attempt to trick the recipient into opening a Microsoft Word document attachment and enabling a malicious macro to “properly” view the content. If the macro is enable, typically by requesting “Enable Content” or “Enable Editing,” the macro will launch and PowerShell script to install the “PRB-Backdoor.”
Click here for Anomali recommendation
Google Releases Security Update for Chrome (June 13, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding a vulnerability located in the Google Chrome web browser. The vulnerability could be exploited by threat actors to take control of an affected system.
Click here for Anomali recommendation
LuckyMouse Hits National Data Center to Organize Country-level Waterholing Campaign (June 13, 2018)
The Advanced Persistent Threat (APT) group “LuckyMouse” (APT27, Emissary Panda) has been engaged in an active campaign targeting an unnamed data center in Central Asia, according to Kaspersky Lab researchers. As of this writing, it is unknown how the group gained initial access to the data center, but researchers note that LuckyMouse likely gained access to a wide array of sensitive government information. While the initial infection vector is unknown, the group was observed using the “HyperBro” trojan as their final-stage in-memory Remote Access Tool (RAT).
Click here for Anomali recommendation
Dixons Carphone mega-breach sees 5.9 million credit card records exposed (June 13, 2018)
Dixons Carphone, which owns companies like Carphone Warehouse and Curry’s PC World, experienced a large data breach that resulted in the theft of 1.2 million users’ general data and files and 5.9 million card details. According to the company, about 5.8 million of the card details are chip-and-pin protected and no CVV data was stolen, however, the other 105,000 cards were identified to not use chip-and-pin protection and are therefore vulnerable to fraudulent activity. The company has stated that they have patched the hole in the system that allowed the breach, though they have not reported how it occurred in the first place. The company faced a similar breach in 2015 where 2.4 million customers had their data stolen.
Click here for Anomali recommendation
New Cortana Vulnerability Could Allow Cybercriminals to Bypass Lock Screen On Windows 10 Devices (June 13, 2018)
A vulnerability in the default settings in Windows 10 regarding the Cortana voice assistant has been discovered by a McAfee researcher. This vulnerability can retrieve information from Cortana or start an application from a machine’s lock screen. This vulnerability could also be exploited to bypass the login on a Windows 10 device to reset default passwords and settings even while the device is locked. The vulnerability is exploited by clicking on the Cortana button on the lock screen and typing something into the search bar. Search results (including documents and other confidential files) will pop up, which can then be hovered over to see location and file information. This could allow an attacker or non-authorized user to reset passwords and other things on the lockscreen of a machine.
Click here for Anomali recommendation
Android Users: Beware These Popularity-faking Tricks on Google Play (June 12, 2018)
New Android-specific applications are being launched on Google Play using falsified download numbers to get users to install the applications. Scammers fraudulently set a high number of installs in the developer name to appear to have a high user base. These applications use semantics like “Trusted Developer’s App” or “Verified Application” to get users to download them. Some have even incorporated a checkmark into the name similar to the real Google Play “verified app” checkmark to also increase downloads. These applications have little to no functionality, but overloads users with advertisements.
Click here for Anomali recommendation
Cryptojacking Invades Cloud. How Modern Containerization Trend Is Exploited by Attackers (June 12, 2018)
Kromtech Security Center researchers have published their findings regarding 17 malicious images that were available for download on the official Docker container repository. The images contained a backdoor that would begin the functions to mine “Monero” cryptocurrency and were observed to have been downloaded more than five million times prior to their removal. The threat actors behind this campaign created an automated tool that forced misconfigured “Kubernetes” accounts to mine Monero.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



