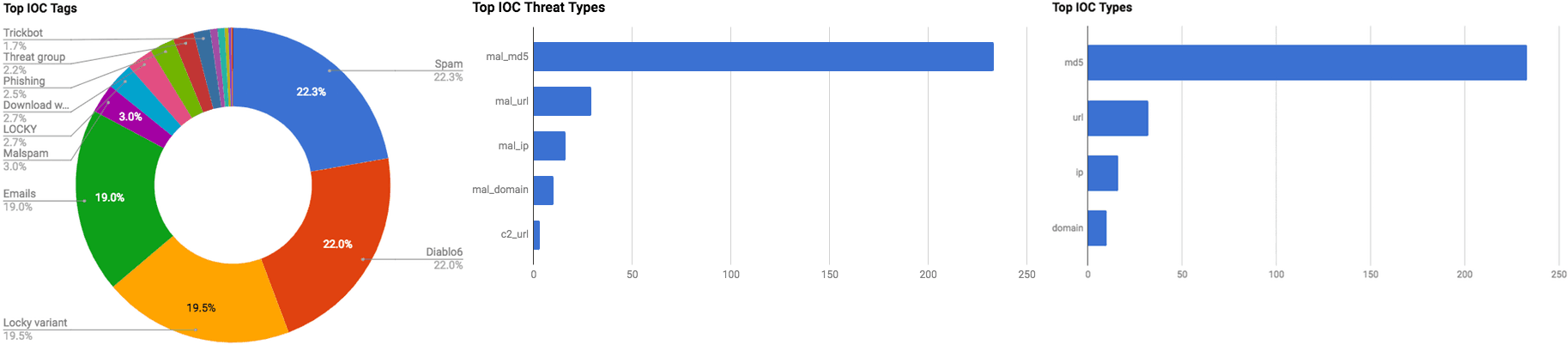

Trending Threats
The intelligence in this week’s iteration discuss the following threats: APT, Exploit Kit, Malspam, Phishing, Ransomware, Underground Markets, Vulnerabilities, and Zero-days. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Cryptocurrency Miner Uses WMI and EternalBlue To Spread Filelessly (August 21, 2017)
Since July 2017, Trend Micro researchers have observed a new fileless malware campaign that uses the Windows Management Instrumentation (WMI) Event Consumer and the EternalBlue exploit to propagate itself. The WMI Event Consumer scripting application is used to execute fileless scripts and maintain persistence and the EternalBlue exploit as the initial infection vector.
Recommendation: Your company should institute policies that actively monitor and restrict the use of applications that could potentially be used for malicious activity. The WMI service may not need to be accessible on every work machine, and only trusted IT administrators should have access to it to reduce risk of malicious use. Additionally, Microsoft patched the EternalBlue exploit in MS17-010 on March 14, 2017, and it should be applied as soon as possible if it has not been already.
Tags: Malware, Fileless, WMI, EternalBlue
Is Malware Hiding in Your Resume? Vulnerability in LinkedIn Messenger Would Have Allowed Malicious File Transfer (August 18, 2017)
On June 14, 2017, CheckPoint researchers reported vulnerabilities in the messenger platform in the business social network, "LinkedIn," and subsequently reported them to the company. LinkedIn acknowledged the flaws and patched them as of June 24, 2017. Prior to the fix, actors could bypass security measures by creating a PowerShell script and save it as a PDF file (among other techniques). This would cause the malicious payload to remain undetected and launch when a user downloaded the file.
Recommendation: This story depicts the risk of opening attachments that appear to come from legitimate senders. It is crucial that your employees understand the potential risk of opening online attachments, especially company recruiters as this story portrays.
Tags: Malware, Vulnerability, LinkedIn
New ERROR CryptoMix Ransomware Variant Released (August 18, 2017)
BleepingComputer researchers have discovered a new variant of the CryptoMix ransomware, dubbed "ERROR" after the file extensions the malware appends. The researchers note that the malware functions the same as CryptoMix, but the emails used for payment contact and the extension added to encrypted files have changed.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Ransomware, CrytpoMix variant, ERROR
Two Critical Zero-Day Flaws Disclosed in Foxit PDF Reader (August 17, 2017)
Security researchers have identified two zero-day vulnerabilities (CVE-2017-10951, CVE-2017-10952) associated with command injection and file writing in "Foxit PDF Reader." It is possible that a threat actor could exploit these vulnerabilities that could allow them to execute arbitrary code on a machine. The vulnerabilities can be exploited via a custom created PDF file and tricking the recipient into opening it.
Recommendation: As of this writing, Foxit has stated that they will not fix the vulnerabilities because they can be avoided if their users enable Safe Reading Mode while opening files.
Tags: Vulnerability, Zero-day
Google Chrome Remote Code Execution Flaw Detailed, PoC Released (August 17, 2017)
The vulnerability assessment company, "Beyond Security," has released Proof of Concept (PoC) code for a remote code execution vulnerability that affects Google Chrome. The vulnerability resides in the incorrect optimization by the turbofan compiler that causes confusion when trying to access an object array or a value array. The researchers said that the vulnerability was discovered in Chrome version 59, and that it may affect other versions as well.
Recommendation: Your company should have policies in place to ensure that the most recent and secure version of software is being used. If Google chrome has not been updated to version 60, it should be done so as soon as possible because the PoC code may cause threat actors to attempt to exploit the vulnerability.
Tags: Vulnerability, Google Chrome, Remote code execution
It's Back: Locky Ransomware Is On The Rise Again (August 17, 2017)
A new variant of the "Locky" ransomware has been identified being distributed via spam emails, according to Sophos researchers. This version is called "Lukitus" after the title of the file extensions the malware appends. The spam emails use subject lines such as "PAYMENT" and claim that the attached zip file is a payment receipt. If the zip file is opened, a VBScript downloader will download the Locky payload.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, it is important to have a comprehensive and tested backup solution in place for the unfortunate case of ransomware infection.
Tags: Spam, Ransomware, Locky variant, Lukitus
GhostClicker Adware is a Phantomlike Android Click Fraud (August 16, 2017)
Trend Micro researchers have discovered approximately 340 applications in the Google Play Store that contain auto-clicking adware called, "GhostClicker." While some of the applications were removed from Google Play, researchers stated that as of August 7, 2017, there 101 infected applications that still remained. One of the applications was downloaded as many as five million times. GhostClicker is capable of generating fraudulent advertisement revenue by falsely generating clicks on advertisement and generating fake traffic.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, Android, Adware, GhostClicker
ShadowPad In Corporate Networks (August 15, 2017)
In July, 2017, Kaspersky Labs discovered a backdoor that was implanted in software created by the secure connectivity solution company, "NetSarang Computer Inc." The backdoor was identified by researchers via suspicious DNS requests that originated from the software. The backdoor is capable of downloading and executing arbitrary code and stores all files it creates at a unique location with encryption to make detection more difficult.
Recommendation: Supply-chain attacks are becoming increasingly common in today's threat environment. Defending against these attacks is difficult as software updates often come through legitimate channels and would otherwise be trustworthy.
Tags: Backdoor, ShadowPad, Supply-chain
Get Rich or Die Trying: A Case Study on the Real Identity Behind A Wave of Cyberattacks on Energy, Mining and Infrastructure Companies (August 15, 2017)
Check Point researchers have identified a campaign that took place over approximately four months and targeted over 4,000 organizations around the world. The exact amount of companies who were infected was not mentioned but some affected companies include construction, oil and gas, marine and energy, mining, and transportation. A campaign on this this scale is typically attributed to a threat group, but researchers discovered that one Nigerian man was behind the wave of phishing emails. The phishing emails infected recipients with the "NetWire" Remote Access Trojan (RAT), which gives the actor full control over an infected machine, as well as the "Hawkeye" keylogger.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified. Furthermore, maintain policies regarding what kind of requests and information your employees can expect to receive from colleagues, business partners, and management.
Tags: Phishing, Cybercriminal
Malspam Pushing Trickbot Banking Trojan (August 15, 2017)
Researchers have discovered that threat actors are distributing the "Trickbot" banking trojan via typosquatted domains created to impersonate financial institution's legitimate websites. The actors are using emails that purport to come from financial institutions' email addresses and claim that the user has received a secure attachment. The attachment has been discovered to be either an HTML file that downloads a Microsoft Office document, or an Office document. The Office attachment will infect the recipient with the Trickbot trojan if macros are enabled.
Recommendation: All employees should be educated on the risks of phishing. Additionally, it is important to know what kind of emails you and your company can expect to receive from the financial entities with whom you conduct business. This will assist in identifying potential malspam and phishing attempts.
Tags: Malspam, Trickbot
A Quick Look At A New KONNI RAT Variant (August 15, 2017)
A new variant of the KONNI Remote Access Trojan (RAT) has been observed being distributed via phishing emails, according to Fortinet researchers. The decoy document is titled "12 things Trump should know about North Korea" and contains a Visual Basic macro that drops and then executes the KONNI installer.
Recommendation: All employees should be educated on the risks of phishing, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. It may also be useful for employees to stop using email attachments, in favor of a cloud file hosting service like Box or Dropbox.
Tags: KONNI, Phishing
The Blockbuster Saga Continues (August 14, 2017)
Palo Alto Networks' Unit 42 researchers have identified a new phishing campaign believed to be conducted by a group associated with the North Korean Advanced Persistent Threat (APT) group. Specifically, the group that conducted "Operation Blockbuster" and "Operation Blockbuster Sequel." Researchers note that this campaign has been ongoing through July and began in April 2017. The actors are using phishing emails with malicious Microsoft Office attachments that are targeting U.S. defense contractors with appropriately themed decoy documents such as fake job descriptions.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of phishing, and how to identify such attempts.
Tags: Threat group, Phishing
New Disdain Exploit Kit Sold on Underground Hacking Forums (August 14, 2017)
Security researcher, David Montenegro, has discovered that a new exploit kit called, "Disdain," is being advertised for purchase on underground forums. The exploit kit is being advertised by an actor called, "Cehceny," for others to purchase for rent on a basis of daily, weekly, or monthly subscriptions costing $80, $500, and $1,400 USD. Cehceny is advertising 15 CVEs and other capabilities and features for Disdain including browser and IP tracking, domain rotator, geolocation availability, untraceable panel server from payload server, RSA key exchange for exploits, and a scan domain. Researchers note that Cehceny has been labeled as a "scammer" on another well-known underground forum, and therefore it is unclear if this exploit kit will become popular.
Recommendation: Always keep your browser and operating system up to date, including any browser add-ons you may need (Flash, Java). Employ network as well as host based detection and prevention systems where possible.
Tags: Exploit kit, Underground forum, Cybercriminal
Locky Strikes Another Blow, Diablo6 Variant Starts Spreading Through Spam (August 14, 2017)
A new variant of the notorious "Locky" ransomware dubbed, "Diablo6," is being distributed via a new spam campaign, according to Fortinet researchers. The emails purport to have receipt attachments or simply just a file attachment. The attachment will attempt to launch a compressed VBS downloader that leads to a download URL to fetch the Diablo6 payload if opened. The ransom note states that all of the files are encrypted with RSA-2048 and AES-128 ciphers and provides a link to follow for ransom payment.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, it is important to have a comprehensive and tested backup solution in place for the unfortunate case of ransomware infection.
Tags: Locky, Malspam
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs.
Locky Tool Tip
Locky is ransomware that is widely spread via phishing messages. Locky first appeared in early 2016. Locky is strongly correlated with the cyber criminal groups related to the dridex and necurs botnets. Multiple waves of Locky samples are distributed daily. The delivery mechanism has evolved over time. The delivery mechanism has been spam messages with executable attachments, MS Word document attachments using Macros to retrieve then execute Locky, and Zip files that extract JavaScript loaders that retrieve then execute Locky. Hosts compromised by Locky display a ransom-note with instructions on how to decrypt the encrypted files. Encrypted files are renamed .locky or .zepto.
Tags: Locky, Ransomware
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



