Weekly Threat Briefing: CSE Malware ZLab - Operation Roman Holiday - Hunting the Russian APT28

The intelligence in this week’s iteration discuss the following threats: APT28, AZORult, BlackTeck, Golden Cup, Leviathan APT, Magecart and Upatre. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
CSE Malware ZLab – Operation Roman Holiday – Hunting the Russian APT28 (July 15, 2018)
Researchers from "Z-Lab" have published an analysis on a number of malware samples that belong to the Russian Advanced Persistent Threat (APT) group Fancy Bear (also known as APT29). New versions of the groups "X-Agent" malware have been discovered. New packed droppers written in Delphi were used to drop the malware, which uses HTTPS to communicate with the Command and Control servers. They have discovered that one of the possible targets is the Italian Marina Militare, or associated entities.
Click here for Anomali recommendation
Upatre Continues to Evolve with New Anti-Analysis Techniques (July 13, 2018)
Palo Alto Networks Unit 42 researchers have found a new variant of the "Upatre" downloader, which was first discovered in 2013, active in the wild as of March 2018. The most interesting updates made to Upatre include code flow obscuration, decryption for network communications, and a new method for the malware to detect if it is running in a virtual machine.Uptare connects Namecoin ".bit" domains to communicate with its Command and Control infrastructure. These domains are resolved via hard coded IP addresses for blockchain supported DNS servers because these domains are not ICANN recognized TLDs. In the past, Upatre was observed downloading malware families such as Dridex, GameOver Zeus, Keotip, and Locky. At the time of this writing, it has not been reported what malware Upatre is downloading or how it is being distributed.
Click here for Anomali recommendation
Google Play Users Risk a Yellow Card With Android/FoulGoal.A (July 12, 2018)
A Google Play distributed Android application has been installing spyware on victim's devices according to McAfee researchers. The application, named "Golden Cup," promised to stream World Cup games and to look up information on current and past World Cups. Whilst the application does contain some multimedia content and information about the most recent World Cup, in the background, without user consent, the application exfiltrates information to a different server. The Golden Cup application takes information such as the device phone number, installed packages, the model, serial number, and Android version. The application is a first stage malware has it has the ability to load "dex" files from remote sources. The delivered dex files has spy functions to steal SMS messages, contacts, files and retrieve device location.
Click here for Anomali recommendation
Chinese Espionage Group TEMP.Periscope Targets Cambodia Ahead of July 2018 Elections and Reveals Broad Operations Globally (July 10, 2018)
The threat group known as "TEMP.Periscope" (also known as Leviathan) has been found to have a significant interest in Cambodia's politics, according to FireEye researchers. The group has actively compromised entities associated with the Cambodian government that are involved in overseeing the elections that take place on July 29, 2018. Researchers found that TEMP.Periscope uses the same infrastructure for the Cambodian attacks to also target an unnamed chemical company in Europe and the defense industrial base in the U.S. It appears that the group used spear phishing emails as the initial infection vector to deliver the group's "AIRBREAK" downloader that delivered the"EVILTECH" backdoor. Other malware used by the group include "DADBOD," "HOMEFRY," and "MUKRYTOP." Furthermore, TEMP.Periscope's tactics are similar to Chinese Advanced Persistent Threat (APT) group tactics, therefore, researchers contend that TEMP.Periscope is likely a Chinese group.
Click here for Anomali recommendation
Inside and Beyond Ticketmaster: The Many Breaches of Magecart (July 10, 2018)
RiskIQ researchers have found that the data breach affecting the online ticket sales and distribution company "Ticketmaster," which was first announced by the company on June 27, 2018, is part of a wider credit-card skimming campaign. The researchers believe that the threat group "Magecraft" is behind the campaign that affects approximately 800 e-commerce websites around the globe. The group accomplished the Ticketmaster breach by compromising third-party components, therefore, it is possible that the over 800 websites believed to part of this campaign may have been compromised in a similar manner.
Click here for Anomali recommendation
Adobe Releases Security Patch Updates for 112 Vulnerabilities (July 10, 2018)
Adobe has issued security updates in this month's "Patch Tuesday" iteration that affect multiple products. The affected products include Adobe Acrobat and Reader, Adobe Connect, Adobe Flash Player, and Adobe Experience Manager. The majority of vulnerabilities are located in Adobe Acrobat and Reader with 104 in total and 51 of those rated as critical. Researchers note that none of the vulnerabilities were previously disclosed to the public and that they have not been observed to have been exploited in the wild, as of this writing. However, with the public exposure of the vulnerabilities, the likelihood of potential exploitation does increase.
Click here for Anomali recommendation
Certificates Stolen from Taiwanese Tech-Companies Misused in Plead Malware Campaign (July 9, 2018)
Threat actors were found to have distributed malware via stolen certificates belonging to the Taiwanese manufacturing company "D-Link," according to ESET researchers. The researchers informed D-Link, who subsequently launched their own investigation and revoked the stolen certificate on July 3, 2018. Two different malware families were found to have used the compromised certificate; one was identified as "Plead," which is a remotely-controlled backdoor, and the other was a password-stealing malware. Trend Micro researchers attribute Plead to the cyberespionage group "BlackTech." To note, ESET researchers also observed malware using a certificate belonging to the Taiwanese security company "Changing Information Technology"; the certificate was revoked by the company on July 4, 2018.
Click here for Anomali recommendation
Two Democratic Campaigns Hit with DDoS Attacks in Recent Months (July 9, 2018)
Cyberscoop has discovered from private sources that Distributed Denial-of-Service (DDoS) were conducted against at least two municipal-level Democratic campaigns in 2018. These attacks were previously unknown to the public prior to this report. These attacks were also discovered to have taken place at times when disruption would be the most valuable, from the perspective of a threat actor. The DDoS attacks targeted campaign websites at crucial moments. With one attack taking place against a website during a fundraising event, while the other attack targeted a candidate's website after receiving good publicity from a public speaking event.
Click here for Anomali recommendation
Breach Department: Unauthorized Party Accesses Macys.com and Bloomingdales.com Customer Accounts (July 9, 2018)
The U.S.-based retail company "Macy's" has confirmed that threat actors gained unauthorized access to its, and its child company "Bloomingdales," customer information from April 26 to June 12, 2018. The breached data consists of the following: birthdates, email addresses, full names, home addresses, and payment card numbers with associated expiration dates. At the time of this writing, Macy's has not confirmed how many individuals may be affected by this incident.
Click here for Anomali recommendation
Apple Releases Multiple Security Updates (July 9, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding vulnerabilities located in multiple Apple products. According to US-CERT, a threat actor could exploit some of these vulnerabilities to take control of an affected system. Apple has released updates to address these vulnerabilities which affect the following products: iTunes 12.8 for Windows, iCloud for Windows 7.6, Safari 11.1.2, macOS High Sierra 10.13.6, watchOS 4.3.2, tvOS 11.4.1, and iOS 11.4.1.
Click here for Anomali recommendation
AZORult Malware Finds a New Ride with Recent Stealer Phishing Campaign (July 9, 2018)
AZORult has resurfaced in a new phishing campaign that is delivered to targeted machines via email attachments. AZORult collects cookies, steals passwords, credit card information, and auto-complete data from most popular web browsers. It targets Bitcoin wallets, and credentials for FTP, email, and XMPP clients. In addition to stealing credentials, it can be configured to steal files from the Desktop with specific extensions. Upon execution, AZORult will use Process Hollowing to impersonate a legitimate Windows process to evade detection and is using CVE-2017-11882, CVE-2017-0199, and CVE-2017-8750 to deliver the malware to targeted machines.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
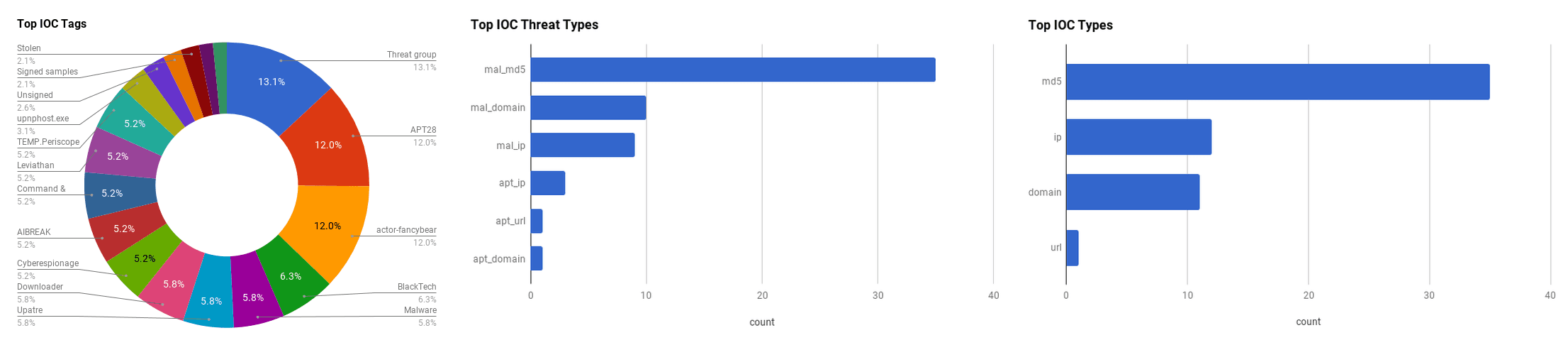
APT28
The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
Leviathan
The Cyber Espionage group “Leviathan” is believed to be a China-based group that has been active since at least 2013. Leviathan conducts cyber espionage operations primarily on maritime, naval defense contractors, and associated research targets across multiple industries. The group’s targets are mainly located in the United States and Western Europe.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



