Weekly Threat Briefing: Flawed Apple Mac Firmware Updates May Leave Them Vulnerable to Attack
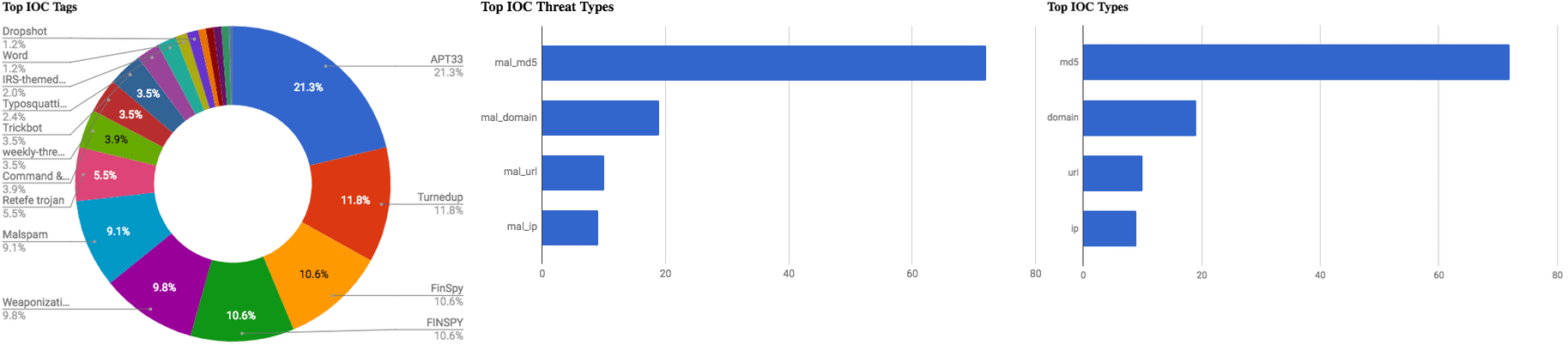

The intelligence in this week’s iteration discuss the following threats: Data breach, Data theft, Malspam, Phishing, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Flawed Apple Mac Firmware Updates May Leave Them Vulnerable to Attack (September 29, 2017)
Duo Labs researchers have discovered that some Mac systems' Extensible Firmware Interface (EFI) are vulnerable to sophisticated attacks. While Apple has addressed this vulnerability in a security update, researchers identified that some instances of Mac EFI's were not updated along with the security update. This led to researchers finding of approximately 73,000 machines that are affected by firmware vulnerabilities.
Recommendation: Mac users should update to the most recent version of Mac OS version 10.12.6 as soon as possible, if it has not been applied already. This update provides the latest EFI firmware and provides features that address known vulnerabilities.
Tags: Vulnerability, Mac firmware
Whole Food Investigates Payment Card Breach (September 29, 2017)
The U.S.-based supermarket chain "Whole Foods" has acknowledged that its Point of Sale (POS) systems at some locations were compromised by unknown actors. Whole Foods states that its primary store checkout systems were not infected, but instead the POS systems location in taprooms and full table-service restaurants located within some stores. As of this writing, it is unknown how many locations were compromised and how many individuals may be affected via stolen credit card information.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of FastPoS infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: Breach, Data theft, POS
Money-Making Machine: Monero-Mining Malware (September 28, 2017)
ESET researchers have discovered a malware campaign that has been ongoing since at least May 2017. Actors are targeting unpatched Windows webservers with a malicious "Monero" cryptocurrency mining malware. The malware is a modified version of the open source Monero mining software "xmrig" that exploits the known vulnerability "CVE-2017-7296" located in unpatched "Microsoft ISS 6.0" servers. As of this writing, researchers state that the actors behind this campaign have created a botnet that has mined Monero worth approximately $63,000 USD.
Recommendation: It is crucial that your company ensure that servers are always running the most current software version. In addition, your company should have policies in place in regards to the proper configurations needed for your servers in order to conduct your business needs safely. Furthermore, always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
Tags: Vulnerability, Unpatched webserver, Malicious cryptocurrency miner, Monero
Banking Trojan Attempts to Steal Brazillion$ (September 28, 2017)
Cisco Talos researchers have identified a new banking trojan campaign that is targeting South American banks, primarily those located in Brazil. The malware is being distributed via malspam. The emails purport that the recipient has received an invoice and to open the .html attachment to view. The attachment contains a link that will direct the recipient to a goo[.]gl URL shortener that will then redirect another location that will download the archived malware (RAR). If the file is decompressed and the JAR file (which masquerades as an invoice) is clicked on, the installation process of the banking Trojan will begin. The malware will use web injections to steal banking credentials.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: Malspam, Banking trojan
Tech Support Scammer Abuse Native Ad and Content Provider Taboola to Serve Malware (September 28, 2017)
Threat actors are taking advantage of native advertising to engage in malvertisement campaigns, according to Malwarebytes researchers. Rogue advertisement companies are displaying legitimate advertisements to increase their reputation, and then switch to displaying malvertisements at a later point in time. Researchers discovered this tactic has affected websites that use the services of the popular native advertising and content provider "Taboola". Taboola's content appears on websites that receive significant traffic such as msn[.]com. If the malvertisements are clicked, users will be redirected a tech support scam page. The warning on the website claims that the user's computer has crashed and requests that a provided number be called to receive assistance.
Recommendation: Users should be cautious when clicking on advertisements because as this story portrays, malicious advertisements can sometimes appear on legitimate online locations. If the advertised product is appealing, it would be safer to search for the product on the authentic website of the company who is selling the product, or other trusted online shopping locations. The same logic can be applied to advertised news stories, it would be safer to search for the story or headline on trusted media sources instead of following advertisements.
Tags: Malvertising, Tech support scam
Phish For The Future (September 27, 2017)
An advanced persistent spear phishing campaign has been found to have occurred between July 7 and August 8, 2017, according to the Electronic Frontier Foundation. The spear phishing campaign targeting employees of "Non-Governmental Organization (NGO) for the Future and Free Press." The actors' objective in the campaign is to steal credentials for business-related services such as Dropbox, Google, and LinkedIn. The actors used tabloid-style headlines, as well as scare tactics such as a notification for a work-related email that had subscribed to an adult content website. A recipient may then follow the link to a fake Google login page and enter their credentials to unsubscribe.
Recommendation: Spear phishing emails represent a significant security risk because the sending email will often appear legitimate to the target; sometimes a target company email is compromised and used for such emails. Education is the best defense, inform your employees on what to expect for information requests from their managers and colleagues. Employees should also be aware of whom to contact when they suspect they are the target of a possible spear phishing attack.
Tags: Spear phshing, Credential theft
Stored Cross-Site Scripting Vulnerability in WordPress 4.8.1 (September 26, 2017)
Sucuri researchers have found a Cross-Site Scripting (XSS) vulnerability that affects the open source content management system "WordPress," specifically, version 4.8.1. Researchers state that the vulnerability requires access to a "Contributor" account on the targeted site, or any account in a WordPress installation with the "bbPress" plugin that has posting abilities. The vulnerability can allow an actor to send a post or topic with a crafted XSS payload, which will execute when an administrator comes to review the post and clicks "Save" or "Preview." This can result in malicious actors remotely executing arbitrary code to send an authenticated request that can edit the website's PHP code that can lead to taking full control of the website.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Vulnerability, WordPress
Apple Releases Security Update for iOS (September 26, 2017)
The U.S. Computer Emergency Response Team (CERT) has issued an alert regarding Apple's latest security update in iOS 11.0.1. The update addresses vulnerabilities that a threat actor could exploit remotely. A successful exploitation could allow an actor to take full control of an affected device.
Recommendation: The U.S. CERT advises Apple customer to review the Apple security page located at "https://support.apple.com/en-us/HT208143" and apply the necessary update.
Tags: Vulnerability, iOS, Alert
Breach at Sonic Drive-In May Have Impacted Millions of Credit, Debit Cards (September 26, 2017)
The U.S. restaurant chain "Sonic Drive-In" has confirmed that it was the subject of a data breach that affects an unknown number of restaurant payment systems, according to KrebsOnSecurity. Researchers believe that ongoing breach has potentially resulted in in actors selling millions of stolen credit and debit card account on underground markets.
Recommendation: Bank accounts and credit card numbers should be protected with the utmost care, and only used with vendors that you trust to keep your information in compliance with the relevant standards. Regular monitoring of financial accounts in addition to identity protection and fraud prevention services can assist in identifying potential theft of data.
Tags: Breach, Data theft, Sonic, Credit and debit cards
Proof-of-Concept Exploit Code Published for Remote iPhone 7 Hack (September 26, 2017)
The Google Project Zero team has published proof-of-concept code for a vulnerability that affects iPhone 7 handsets. The researchers state that if the exploit is executed successfully, a threat actor could implant a backdoor into the firmware. This would allow a remote actor to be able to read and write commands "to be issued to the firmware via crafted action frames, thus allowing easy remote control over the Wi-Fi chip." Additionally, this exploit can be executed without the need of any user interaction. Apple has issued a security update to fix this vulnerability. This vulnerability is not limited to iPhone 7 but affects any device that Broadcom WiFi chips running the firmware version BCM4355C0.
Recommendation: This story portrays the potential risk that exists if security updates for devices are applied. Employees should be informed on the dangers of not applying security updates to personal and professional devices. Policies should be in place to apply security updates as soon as possible. Apple has released a security update for both iPhone's iOS and Apple TV'S tvOS. Google has also patched the vulnerability for Android. To check if your Android phone is updated, go to "Settings" -> "About Device" -> "Software info" and check to see if the "Android security patch level" is at least "2017-09-05."
Tags: Vulnerability, iPhone 7, Wi-Fi
XPCTRA Malware Stealing Banking and Digital Wallet User's Credentials (September 25, 2017)
Incident handler, Renato Marinho, has published his findings a new trojan dubbed, "XPCTRA" that is being distributed via a malspam campaign. The emails claim that the link in the body of the email leads to PDF form invoice, but will lead the recipient to download an executable file. The executable file (dropper) will download a zip file, which is subsequently unzipped and executes the malware payload. The malware is capable of multiple forms of malicious activity. It can monitor and intercept traffic to financial institution websites, as well as stealing banking and email credentials.
Recommendation: All employees should be educated on the risks of malspam, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. Emails that request that the recipient follow a link that then asks for credentials to be entered is often an indicator of a phishing attack.
Tags: Malware, Banking, XPCTRA
Deloitte Hit by Cyber-Attack Revealing Clients' Secret Emails (September 25, 2017)
The London registered and U.S.-based accounting firm "Deloitte" has confirmed that it was the target of a sophisticated attack that resulted in confidential information being stolen. The compromised resulted in sensitive information such as confidential emails, and plans of some of their blue-chip clients. Additionally, the unknown threat actors also had the potential to access to architectural diagrams for business and health information, IP addresses, usernames, and passwords. Deloitte discovered the breach in March 2017, however, it appears that the actors had access to Deloitte global email server since October or November 2016.
Recommendation: Ensure that your server is always running the most current software version. Additionally, maintaining secure passwords for RDP and other remote access systems is paramount, and passwords should be changed on a frequent basis. Intrusion detection systems and intrusion prevention systems can also assist in identifying and preventing attacks against your company's network. Furthermore, always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
Tags: Breach, Data theft
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



