Weekly Threat Briefing: GPON Exploit in the Wild (III) - Mettle, Hajime, Mirai, Omni, Imgay
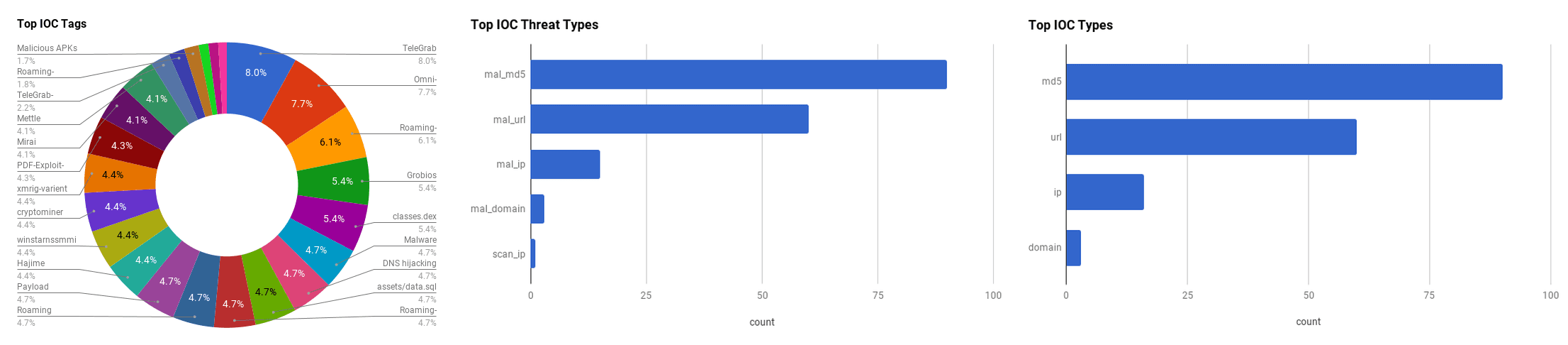

The intelligence in this week’s iteration discuss the following threats: Adobe Vulnerabilities, Cisco Digital Network Architecture Vulnerabilities, DDoS Amplification, GPON Router Exploits, Grobios Trojan, UPnP Router Vulnerabilities and WinstarNssmMiner. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
GPON Exploit in the Wild (III) - Mettle, Hajime, Mirai, Omni, Imgay (May 21, 2018)
Netlab researchers claim that at least five different botnets are using two GPON router vulnerabilities, registered as "CVE-2018-10561" and "CVE-2018-10562" to infect devices to expand the botnet. The botnets include "Mettle," "Hajime," "Mirai," "Omni," and "Imgay," among others. Some of the botnets patch the device to prevent intrusion from other competitors.
Click here for Anomali recommendation
Roaming Mantis dabbles in mining and phishing multilingually (May 18, 2018)
The "Roaming Mantis" Android malware also known as "MoqHao" and "XLoader," has been expanding its attack targets, according to Kaspersky Labs researchers. Roaming Mantis is distributed via trojanized APKs. The landing pages and APK files now support 27 different languages covering Europe and the Middle East. It is believed that the actor(s) behind the malware used an automatic translator to implement the different languages. The actor also targets iOS devices via phishing pages in addition to Android. A new feature of the malware also uses a cryptominer to generate extra revenue.
Click here for Anomali recommendation
Hardcoded Password Found in Cisco Enterprise Software, Again (May 17, 2018)
Cisco has released 16 security advisories, three of which are classified as "Critical". The three vulnerabilities include a hardcoded backdoor account (CVE-2018-0222) and two authentication bypasses for the Cisco Digital Network Architecture (DNA) Center (CVE-2018-0268,CVE-2018-0271). The vulnerability "CVE-2018-0222" is undocumented static user credentials for the default administrative account that grants an attacker root privileges on targeted systems.
Click here for Anomali recommendation
CryptoMiner, WinstarNssmMiner, Has Made a Fortune By Brutally Hijacking Computers (May 16, 2018)
Researchers from the security firm "Qihoo 360" have released information regarding a new cryptominer, dubbed "WinstarNssmMiner." that has been spreading quickly. The software when terminated crashes the victim machine. The malware is based off the "XMRIG" open source Monero miner project. It also tries to identify any running antivirus protection and deactivate the running processes.
Click here for Anomali recommendation
TeleGrab - Grizzly Attacks on Secure Messaging (May 16, 2018)
Researchers from the Cisco Talos team have been observing a malware that collects cache and key files from the end-to-end encrypted instant messaging chat service "Telegram." The malware is being distributed via various downloaders, only targets the desktop version of Telegram and mainly targets Russian-speaking individuals.. The collected information can be used to access a victim's current session, contacts and previous chats. The researchers believe the malware was created by a Russian speaking actor called "Racoon Hacker/Enot."
Click here for Anomali recommendation
A tale of two zero-days (May 15, 2018)
ESET researchers discovered a PDF file exploiting two zero-day vulnerabilities. The vulnerabilities include a remote-code execution in Adobe Reader followed by a privilege escalation vulnerability in Microsoft Windows that allowed code, embedded in the PDF, to be executed with the highest possible privileges on the target machine. The PDF exploited a remote code execution vulnerability, registered as "CVE-2018-4990," in Adobe Reader. If opened, JavaScript code is executed that manipulates an object containing a "JPEG2000" image that triggers a double-free vulnerability in Adobe Reader. Using heap-spray techniques that corrupt internal data structures that result in reading and writing memory access from their JavaScript code. The script then locates the memory address of the Adobe JavaScript engine and uses assembly instructions in a Return-oriented programming (ROP) chain to execute native shellcode that initializes an embedded executable file. The executable exploits a vulnerability, registered as "CVE-2018-8120," in "NtUserSetImeInfoEx" of the "win32k" Windows kernel component. The vulnerability allows the executable to write to an arbitrary address in the kernel space. Next a technique is used to rewrite the Global Descriptor Table (GDT) to execute code in the kernel, replaces the token of the current process with the system token to gain privilege escalation.
Click here for Anomali recommendation
CVE-2018-8174 and Forcing Internet Explorer Exploits (May 15, 2018)
A newly discovered zero-day exploit has been targeting trade agencies and other related organizations in China, according to Trustwave researchers. The zero-day, registered as CVE-2018-8174, is a "Use-After-Free" memory corruption bug in the Microsoft VBScript engine that could lead to arbitrary code execution. Attacks in the wild use a Rich Text Format (RTF) file in Microsoft Word for distribution. The file uses an OLE element that points to a link for data on a website, which is a malicious VBScript exploiting the vulnerability. The reason why the RTF file is used linking to an external source and not an embedded macro is because the vulnerability needs to exploit the VBScript engine in the "Internet Explorer" browser. If clicking a link in an email, the chances are that the default browser is not Internet Explorer, so the RTF file ensures that the correct browser is used for the exploit.
Click here for Anomali recommendation
New DDoS Attack Method Demands a Fresh Approach to Amplification Assault Mitigation (May 14, 2018)
Imperva researchers have discovered a new amplification attack vector for Distributed Denial-of-Service (DDoS) attacks after discovering new payloads in the wild with irregular source port data. The attack, a "UPnP (Universal Plug and Play) protocol exploit," uses UPnP to obfuscate source port information for any type of amplification payload. The attack works by finding open UPnP routers and changing the devices configuration XML file to reroute traffic to an external DNS server and switching ports. The threat actor spoofs the victims IP address and sends a DNS request to the UPnP device. This request is sent to the proxy DNS resolver which is sent back to the device which forwards the response to the victim via the port specified by the attacker in the XML file.
Click here for Anomali recommendation
A Deep Dive Into RIG Exploit Kit Delivering Grobios Trojan (May 14, 2018)
The RIG exploit kit has been observed delivering the "Grobios" Trojan, according to FireEye researchers. The attack starts from a compromised website that contains an injected malicious iframe which in turn loads a RIG landing page. RIG loads a malicious Flash file that drops the Grobios trojan. The trojan uses multiple techniques for anti-analysis and persistence on a victim machine such as a packer to evade static analysis. For persistence, Grobios drops a copy of itself into the "%APPDATA%" folder masquerading as legitimate software and creates a autorun registry key. The malware also drops a shortcut into the Windows startup folder and creates scheduled tasks. The trojan communicates with a command and control server to receive commands to execute.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



