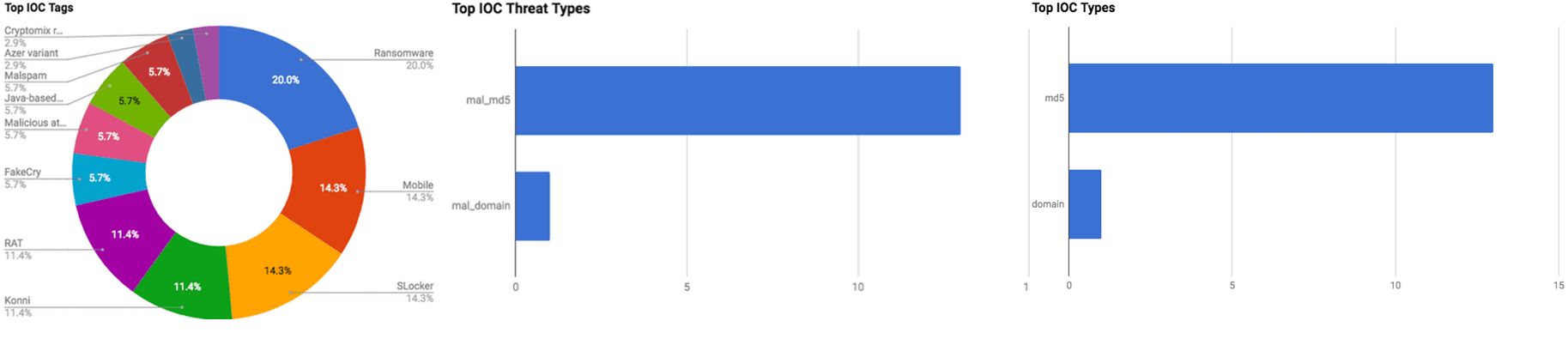

The intelligence in this week’s iteration discuss the following threats: Credit Card theft, Distributed Denial-of-Service, Mobile malware, Payment System breach, Point-of-Sale, Ransomware, Remote Access Trojan. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Hard Rock, Loews Hotels Admit Data Breach (July 10, 2017)
Hard Rock Hotels and Casinos and Loews Hotels have both released statements in which they confirmed that they had been breached with information-stealing malware. Unknown actors were able to gain access to card payment systems in multiple Hard Rock locations and steal unencrypted credit card data. The hotel company stated that the breach began on August 10, 2016, and the last access to credit card data was on March 9, 2017. Loews Hotels was also similarly affected and unknown actors were able to steal an unspecified amount of credit card information.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: Breach, POS, Credit card theft
Self-Service Food Kiosk Vendor Avanti Hacked (July 8, 2017)
A self-service payment kiosk company, Avanti, has had a breach of its networks that allowed hackers to push malware to their payment kiosks. Avanti have warned that the breach may have put customer credit card accounts and their biometric data at risk. The company has approximately 1.6 million customers. The kiosks were infected with the point-of-sale malware known as "PoSeidon."
Recommendation: POS networks should carefully be monitored for unusual activity, thus keeping logs of what typical network activity looks like is very important. In the case of strange activity, taking POS systems offline and repopulating them is a safe mediation step in order to avoid possible loss of reputation, or lawsuit by individuals who had their credit card information stolen, and possibly used by cybercriminals.
Tags: PoS, Breach, Malware
Broadpwn Bug Affects Millions of Android and iOS Devices (July 8, 2017)
Security researcher Nitay Artenstein has discovered that "BCM43xx" Wi-Fi chips made by Broadcom are vulnerable to a bug that allows an attacker to remotely execute code on a victim's device. The Broadcom chips are embedded in millions of iOS and Android devices.The vulnerability can be exploited when a user is within range an attacker's Wi-Fi network. The bug appears to be a heap overflow that can occur when the victim's device receives a special packet from a connected network.
Recommendation: Users should only connect to Wi-Fi networks that they trust. Users should also disable any Wi-Fi auto connect feature. Google has made a patch for this vulnerability for Android devices. It is recommended that users phones are always kept up to date. To check if your Android phone is updated, go to "Settings" -> "About Device" -> "Software info" and check to see if the "Android security patch level" is at least "2017-07-05." It is still unknown whether Apple have addressed this vulnerability.
Tags: Android, Remote Code Execution, iOS, wifi
How the CopyCat Malware Infected Android Devices Around the World (July 6, 2017)
Security researchers have identified a malware for Android, called "CopyCat," that has infected approximately 14 million Android devices primarily located in Southeast Asia. CopyCat is able to root devices and inject code into the Zygote daemon. This allows CopyCat to control any activity on the device. CopyCat uses control of the phone to generate illicit advertisement revenue by displaying fraudulent adverts and stealing the referrer IDs of applications that CopyCat installs from Google Play.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Android, Malware, CopyCat
M.E.Doc Software Was Backdoored 3 Times, Servers Left Without Updates Since 2013 (July 6, 2017)
On July 4, 2017, Ukrainian authorities seized update servers owned by the Ukrainian accounting service company, "M.E.Doc," that distributed malicious updates that contained the "NotPetya" ransomware. Researchers analyzed the servers and discovered that they had not been updated since 2013. Additionally, Cisco researchers believe that the group responsible for compromising the servers and distributing the malicious updates is a cyber espionage group called "TeleBots." It is believed the group infiltrated M.E.Doc by stealing employee credentials.
Recommendation: It is crucial that your company ensure that servers are always running the most current software version. In addition, your company should have policies in place in regards to the proper configurations needed for your servers in order to conduct your business needs safely. Furthermore, always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: Breach, Petya/NotPetya, Ransomware
New Konni Campaign References North Korean Missile Capabilities (July 6, 2017)
Talos researchers have identified a new campaign that is distributing the "Konni" Remote Access Trojan (RAT). The Konni malware has been distributed in three previous campaigns over the past three years. In this campaign, the malware is being distributed via a phishing campaign that began on July 3, 2017. The phishing campaign uses a malicious attachment titled "N.K. marks anniversary of strategic force, touting missile capabilities." If the attachment is opened, the Konni malware will begin its infection process by dropping executables.
Recommendation: All employees should be educated on the risks of phishing, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. It may also be useful for employees to stop using email attachments, in favor of a cloud file hosting service like Box or dropbox.
Tags: Konni, RAT, Phishing
New Azer CryptoMix Ransomware Variant Released (July 5, 2017)
The security researcher known as "MalwareHuntTeam" has discovered a new variant of the "Cryptomix" ransomware, called "Azer." The malware has no network communication processes and functions entirely offline. As of this writing, the ransom note that appears after infection does not specify a monetary amount needed to purchase the decryption tool. Instead, the note provides the email address for the user to contact for further instruction.
Recommendation: It is paramount to have a comprehensive and tested backup solution in place. If a reproducible backup is not available, there may a decryptor available that can assist in retrieving encrypted files. Additionally, educate your employees about the dangers of downloading applications when they are not offered from the website of the official provider/developer.
Tags: Cryptomix, Azer variant, Ransomware
AdGholas Malvertising Thrives in the Shadows of Ransomware Outbreaks (July 5, 2017)
Recently, the prolific Malvertising gang "AdGholas" has initiated a new wave of drive-by download attacks that push the "Astrum" exploit kit. AdGholas create fake websites, usually mirroring legitimate websites by changing the logo and acquiring a legitimate SSL certificate. This is done to fool ad agencies who distribute their malicious adverts on popular websites. The redirect tag hosted on their fake website loads a landing page for the Astrum exploit kit. New AdGholas/Astrum infection chains have been dropping ransomware.
Recommendation: Because many exploit kits use known vulnerabilities, it is imperative that users make sure all software is up to date. This makes it a lot harder for malicious actors to compromise systems. Another layer of protection can be to use an ad-blocker in order to stop adverts being served to the user's machine. But this does not fix the underlying vulnerabilities.
Tags: AdGholas, Malvertising,
SLocker Mobile Ransomware Starts Mimicking WannaCry (July 5, 2017)
The Android mobile ransomware, "SLocker," was observed to be using the same Graphical User Interface (GUI) of the "WannaCry" ransomware, according to Trend Micro researchers. The researchers released new information about a SLocker variant that was first identified in May 2017. The malware is distributed by impersonating guides and tools for legitimate games in addition to video players.
Recommendation: Always keep your mobile devices fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: SLocker, Mobile, Ransomware
In ExPetr/Petya's Shadow, FakeCry Ransomware Wave Hits Ukraine (July 4, 2017)
Kaspersky researchers have identified a new strain of ransomware, dubbed "FakeCry," that is targeting Ukrainian entities. As of this writing, approximately 90 Ukrainian organizations were attacked with FakeCry. Similar to the ExPetr/Patya outbreak on June 2017, 2017, FakeCry was also distributed via compromised MeDoc (Ukrainian accounting software) updates at the same time ExPetr/Petya was being distributed.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: FakeCry, Ransomware
Fourth Largest Cryptocurrency Exchange Was Hacked. Users Lose Ethereum & Bitcoin (July 4, 2017)
Around 3% of the user base (over 31,800 users) of "Bithumb," of the world's fourth largest cryptocurrency exchange, have had their details stolen. These details included customer names, email addresses, and mobile phone numbers. The company revealed that one of their employees had had their laptop hacked by an unknown attacker. Bithumb users have started complaining that their accounts were being drained. It is not clear how the attacker used the stolen details to compromise accounts. Bithumb promises to reimburse affected users.
Recommendation: One of the best ways to secure your Bitcoins against theft is by using hardware wallets. Hardware wallets are a type of Bitcoin wallet that stores the owner's private keys on a hardware device that is secure from hacking attempts. Cold storage wallets could also be used to assist in Bitcoin security. Cold wallets are placed on clean air-gapped computers and therefore protect all private keys from online threats. It is more tedious to use but increases the security.
Tags: Cryptocurrecny exchange, Breach
Malspam With Java-Based RAT (July 4, 2017)
Researchers have discovered a new malspam campaign that attempts to infect recipients with a Java-based Remote Access Trojan (RAT). The sender of the malicious email purports to be "Jees George Cherian," a Parts Sales Representative for "General Transportation & Equipment Co." The content of the email claims that a colleague is on leave and requests that the recipient to open that attachment in order to proceed with payment. The malicious attachment, titled "INVOICE LIST," is a .jar file that will infect the user's machine if opened.
Recommendation: Educate your employees on the risks of opening attachments from unknown senders. Additionally, maintain policies regarding what kind of requests and information your employees can expect to receive from colleagues and management. Anti-spam and antivirus applications provided from trusted vendors should also be employed.
Tags: Malspam, RAT
Android Vulnerabilities in Lenovo Vibe Allow Jailbreaking (July 3, 2017)
A vulnerability in Lenovo VIBE mobile phones allows a malicious user with physical possession of the device, without a secure lock screen, the ability to escalate privileges to root user (rooting/jailbreaking). The vulnerabilities use applications that allow private data to be backed up and restored via Android Debug Bridge, which allows for tampering.
Recommendation: Devices that have been upgraded to Android 6.0 Marshmallow and above are not affected. It is recommended that users upgrade their devices. If the user is not able to update, then the user should disable Android Development Bridge, via the Android Developer Options menu, when not in use. Also since the vulnerability requires the attacker to have access to the physical device, users should enable lock screen authentication mechanisms, such as a PIN or password protection.
Tags: Anroid, Mobile, Vulnerability
UK Teen Charged with Running DDoS Booter Service (July 3, 2017)
An 18-year-old resident of Manchester, UK, named Jack Chappell, has been arrested by UK authorities. Chappell has been accused of creating malware that he installed on devices around the world. The compromised devices were then used to create a Distributed Denial-of-Service (DDoS) botnet that he would allow access to for paying customers. The botnet was used to launch DDoS attacks against companies located around the globe.
Recommendation: Denial of service attacks can potentially cost your company loss in revenue because severe attacks can shut down online services for extended periods of time. With the leak of the Mirai botnet source code in October, the availability for threat actors to compromise vulnerable devices, and purchase DDoS for hire is a continually evolving threat. Mitigation technique can vary depending on the specifics of the attack. For example, in the case of BlackNurse, which can disrupt enterprise firewalls, ICMP type 3 traffic should be blocked, or at least rate limited.
Tags: Cybercriminal, DDoS
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



