Weekly Threat Briefing: JavaScript Web Apps And Servers Vulnerable To ReDoS Attacks
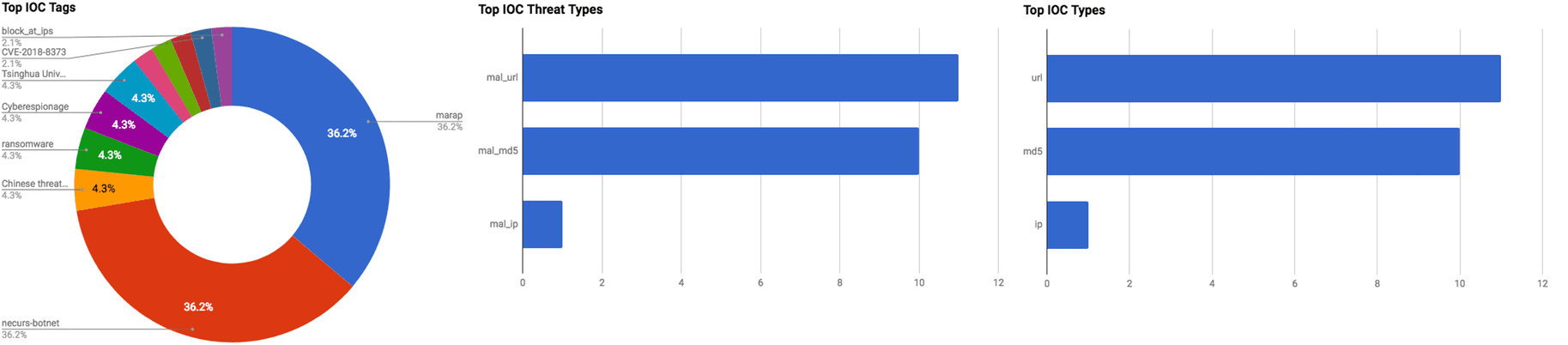

The intelligence in this week’s iteration discuss the following threats: APT, Credential theft, Cyberespionage, Malspam, Phishing, Ransomware, Remote access trojan, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
JavaScript Web Apps And Servers Vulnerable To ReDoS Attacks (August 20, 2018)
Web apps and web servers using JavaScript have been discovered to be vulnerable to a specific type of attack known as Regular Expression Denial-of-Service (ReDoS). This type of attack occurs when a threat actor sends large and complex pieces of text to the open input of a JavaScript-based web server or application. If the web page or application cannot handle various edge cases, the application or page is temporarily blocked whilst trying to process and pattern-match the input. ReDoS attacks are particularly detrimental with JavaScript-based applications and pages because every request is handled by the same thread since JavaScript only engages in single-threaded execution. ReDoS attacks then end up blocking the entire server with requests. Because ReDos vulnerabilities in JavaScript still have yet to be addressed, despite being known since 2012, it has begun to gain momentum with the threat actor community. At least 340 different sites are vulnerable to this type of attack. Several servers have addressed the problem and applied patches, but many still have yet to, making them susceptible to this threat still.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
Chinese Cyberespionage Originating From Tsinghua University Infrastructure (August 16, 2018)
Recorded Future researchers have published a report in which they discuss their findings of threat actors that are attributed to China’s “Tsinghua University,” which is an elite Chinese academic institution in Beijing. The threat actors were observed to target the Tibetan community with a Linux backdoor called “ext4.” In addition, researchers identified that the attacks also targeted U.S. entities such as Alaska’s Department of Natural Resources, and the State of Alaska Government. Other targeted entities include the United Nations office in Nairobi, and the Kenya Ports Authority, among others. Researchers conclude with medium confidence that these network reconnaissance activities were conducted by Chinese state-sponsored threat actors.
Click here for Anomali recommendation
New Modular Downloaders Fingerprint systems, Prepare for More - Part 1: Marap (August 16, 2018)
Proofpoint security researchers discovered a new malware strain, dubbed “Marap,” that is distributed by malspam with malicious email attachments. The emails pose as sales requests, major bank notices, or vague messages simply requesting the recipient open the attached file from a “Jane” or “John” that all contained malicious PDFs, Word documents, or ZIP file downloads. The malware infects a machine, copies the system, and then relays that information to the command and control (C2) server. This allows the Marap malware to later download specific modules on individual systems based on the threat actor’s instructions. According to researchers, this malware has many similarities to the Necurs botnet, so researchers are presuming that this malware is also from the same actors as Necurs.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204)
Severe Vulnerability Exposes WordPress Websites To Attack (August 16, 2018)
A significant vulnerability in WordPress has continually been observed for over a year without a patch being issued to fix it. This vulnerability could allow threat actors to exploit the WordPress PHP framework that results in a full system compromise. Threat actors can upload a crafted thumbnail file to trigger “eXternal Entity (XXE -- XML)” and Server Side Request Forgery (SSRF) flaws which therein causes unserialization of the platform’s code. This could allow for serious remote code execution attacks to occur. Researchers have yet to see this in the wild, and whilst the WordPress content management system has been made aware of the vulnerability since February 2017, they have yet to issue a patch.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
User-after-free (UAF) Vulnerability CVE-2018-8373 in VBScript Engine Affects Internet Explorer to Run Shellcode (August 15, 2018)
On July 11, 2018, Trend Micro researchers discovered a vulnerability that located in the Internet Explorer (IE) web browser. The vulnerability, registered as “CVE-2018-8373,” affects the VBScript engine in the most recent versions of Windows. IE 11 was found to not be vulnerable to CVE-2018-8373 because VBScript in Windows 10 Redstone 3 (RS3) is disabled by default. CVE-2018-8373 is a remote code execution vulnerability that is caused by the way the scripting engine handles objects in memory in IE.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
Revamped jRAT Uses New Anti-Parsing Techniques (August 15, 2018)
Security researchers at Symantec have discovered a new version of jRAT (remote access trojan) in the wild. The new version uses techniques to avoid detection and parsing, and prevent reverse-engineering. This version has seen over a 300% increase in use, but is utilized for targeted attacks against mainly the financial sector, though infections have been seen in communications, hospitality, energy, and government sectors as well. The jRAT’s initial attack vector is through financially-themed phishing emails, typically using the guise of “proof of payment,” “invoice,”, “wire instructions,” and others to manipulate the target into opening the JAR file attachment in the email. This particular version of jRAT contains a MZ header and two corrupt MZ files that help avoid MZ and Java parsers. This version of jRAT has the following capabilities: log keystrokes, take screenshots on the infected machine, play audio messages, access the webcam, read/write or delete files, and download and execute files.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204)
Cisco Releases Security Updates (August 15, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert concerning vulnerabilities that affect multiple Cisco products. One of the vulnerable products include “Cisco AsyncOS Software” for Cisco Web Security versions 9.1, 10.1, 10.5, and 11.0, and the vulnerability registered as “CVE-2018-0410.” Other vulnerable products include “Cisco Unified Communications Manager IM & Presence Service” (CUCM IM&P), “Cisco TelePresence Video Communication Server (VCS),” and “Expressway” with Unified Communications mode set to Mobile and Remote Access; the vulnerability affects all releases of said products prior their first fixed release and is registered as “CVE-2018-0409.” A remote threat actor could exploit these vulnerabilities to launch a Denial-of-Service (DoS) attack.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
India Cosmos Bank Loses $13.5 Million in Cyber Attack (August 14, 2018)
Unknown threat actors compromised the systems of India’s Cosmos Bank and were able to steal 944 million rupees (approximately $13.5 million USD). The bank has stated that the actors were able to steal the funds by first stealing customer information via a malware attack targeting the bank’s ATM server. Using the stolen credentials, the actors withdrew the funds with approximately 805 million rupees being withdrawn in 14,849 transactions in just over two hours on August 11. The remaining 139 million rupees were stolen via three unauthorized transactions through the Society for Worldwide Interbank Financial Telecommunication (SWIFT) network. The SWIFT transactions were approved via a proxy switch bypassing the fraudulent payment approvals through the proxy switching system.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Account Manipulation (T1098)
PhishPoint: New SharePoint Phishing Attack Affects an Estimated 10% of Office 365 Users (August 14, 2018)
A new phishing attack has been found to affect “Office 365” users, and Avanan researchers believe that this attack could potentially affect approximately 10% of the general “Office 365” users, as well. Threat actors are distributing emails that contain a link to a “SharePoint” document; SharePoint is a collaborative platform that is integrated with Microsoft Office. The actors were observed placing a malicious link inside of the SharePoint document to bypass Office 365 security because Office 365 only scans links in the email itself and not in attached files. If the SharePoint file is opened, a recipient will be presented with a fake “OneDrive for Business” prompt with an “Access Document” hyperlink that leads to a phishing page impersonating Microsoft’s login page. The objective of this campaign is to steal credentials by presenting email recipients with a fake login page.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] User Execution (T1204)
Brazilian Banking Customers Targeted By IoT DNS Hijacking Attacks (August 14, 2018)
Brazilian banks “Banco de Brasil” and “Itau Unibanco” have faced targeted DNS hijacking campaigns to obtain customer credentials through end-user Internet of Things (IoT) devices. Using modems and routers, threat actors have been able to remotely compromise the home devices and redirect users unknowingly to a phishing site instead of the intended financial site the user had attempted to reach. The malicious DNS server that controls the attack acts as the middleman that provides the threat actor the ability to bring up fake sites collect sensitive banking information from users whose routers were infected. The DNS servers try to reconfigure IoT devices using an unauthenticated remote configuration URL which changes the DNS settings and results in the users accessing the infected router or modem to be routed through the malicious DNS server, specifically when attempts to access the two banking websites are entered.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] User Execution (T1204)
Oracle Releases Security Alert (August 13, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding a vulnerability that affects “Oracle Database Server.” The affected versions include the following: 11.2.0.4, 12.1.0.2, 12.2.0.1, and 18. The vulnerability, registered as “CVE-2018-3110,” can result in the complete compromise of the Oracle Database and shell access to the underlying server, according to the Oracle Security Advisory.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
KeyPass Ransomware (August 13, 2018)
Security researchers have identified a new family of ransomware, dubbed “KeyPass,” that was first observed in the wild in August 2018. The ransomware, which is written in C++ and compiled in MS Visual Studio, is distributed by threat actors via fake installers that download the ransomware module. Once the fake installer is on a machine, it will copy its executable to “%LocalAppData%” and launches it; it will subsequently delete itself from the original location and begins its encryption process. The actors behind KeyPass demand $300 USD for the decryption key and threaten to increase the price if contact is not made via email within 72 hours.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise (T1195)
New Man-in-the-Disk Attack Leaves Millions of Android Phones Vulnerable (August 13, 2018)
A new attack vector has been found to affect Android devices that could result in code injection into the privileged context of a targeted application, according to Check Point researchers. The attack vector, dubbed “Man-in-the-Disk” (MitD), takes advantage of the Android operating system by intercepting and manipulating information that is exchanged between external storage and an application. This manipulation can occur when an application downloads the latest version on the external storage of a device prior to installing the update. This could cause an application’s data to be replaced with malicious code because the application does not validate the integrity of the data; an example of this was found in the “Xiaomi” web browser. Other applications tested and found to be vulnerable to a MitD attack include Google Translate, Google Text-to-Speech, Google Voice Typing, LG Application Manager, LG World, Xiaomi Browser, and Yandex Translate, among others.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE MOBILE-ATT&CK] Repackaged Application (MOB-T1047)
Report: “Faxploit” Hack Can Penetrate Networks with Just a Fax Number (August 13, 2018)
Check Point researchers have published a report in which they discuss an exploit, dubbed “Faxploit,” that affects all-in-one printer fax machines. Security researchers were able to exploit certain, multifunctional fax machines with the only prerequisite knowledge being the fax number. The researchers were able to take advantage of inherent vulnerabilities in the fax protocol in conjunction with an exploit such as “EternalBlue” to move laterally in a target network and execute arbitrary malware. Additionally, the all-in-one fax machine network does not have to be connected to the internet to be exploited because "Faxploit" exploits the fax protocol and leverages telephone lines instead of the internet itself.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts (T1078) | [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
FEATURED RESOURCES

The Deceptive Lull: Why the Iran Cyber Conflict's Real Threat Isn't the One Making Headlines



