Weekly Threat Briefing: Kansas Data Breach Exposes More than 5 Million Social Security Numbers
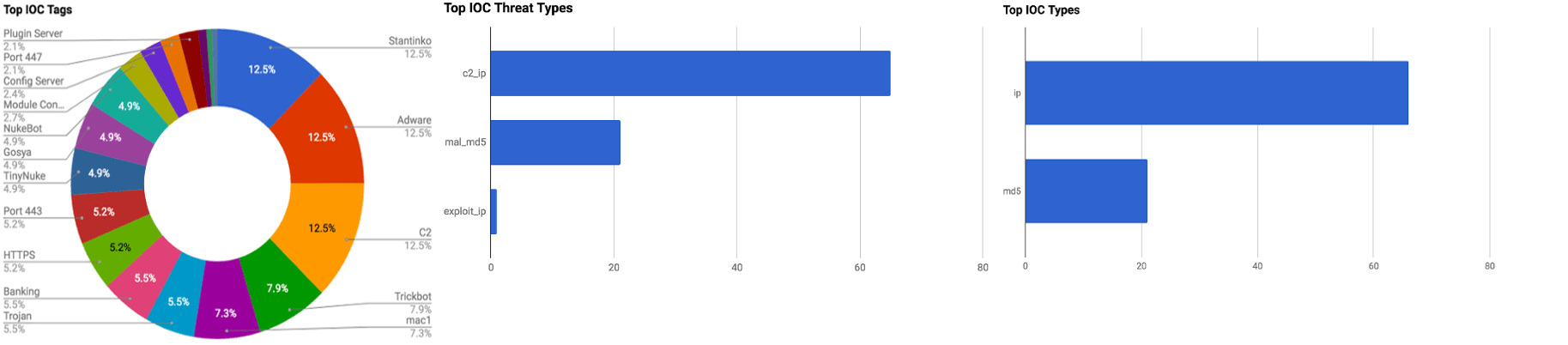

The intelligence in this week’s iteration discuss the following threats: Adware, Banking Trojans, Breaches, Internet of Things, NukeBot, SambaCry, Stantinko and TrickBot. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Kansas Data Breach Exposes More Than 5 Million Social Security Numbers (July 21, 2017)
After a Public Records request by the Kansas News Service, the full extent of a breach on a database operated by the Kansas Department of Commerce was revealed on the 19th July. More than 5.5 million social security numbers of Americans across 10 states were exposed. The data was kept to help members of the public find jobs. The largest amount of social security numbers stolen were citizens of Alabama, with approximately 1.3 million peoples details stolen. Kansas has agreed to pay for up to one year of credit monitoring, in 9 of the 10 affected states in response to the breach.
Recommendation: Personal information such as social security and credit card numbers should be protected with the utmost care, and only used with vendors that you trust to keep your information in compliance with the relevant standards. Regular monitoring of financial accounts in addition to identity protection and fraud prevention services can assist in identifying potential theft of data.
Tags: Breach, Kansas
Stantinko: A massive adware campaign operating covertly since 2012 (July 20, 2017)
ESET researchers have conducted investigations into a large adware campaign that has been operating secretly since 2017. The adware, called "Stantinko" has mainly targeted Russia and Ukraine. The initial infection vector was via executables disguised as torrents. It then installs malicious Chrome browser extensions that carry out ad injection and click fraud. It also tried to brute-force into Wordpress and Joomla admin panels in order to compromise and sell them. It also is able to avoid detection by antivirus and reverse engineering by having encrypted code that resides on disk or the Windows registry. A benign looking executable loads and decrypts the code. It is able to maintain persistence on the victim's system by installing two Windows services, which have the ability to reinstall the other, if one is deleted.
Recommendation: Malware authors are always innovating new methods of communicating back to the control servers. Always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). All software/torrents should be carefully researched prior to installing on a personal or work machine. Additionally, all software, especially free versions, should only be downloaded from trusted vendors.
Tags: Stantinko, Adware, C2
$30 million below Parity: Ethereum wallet bug fingered in mass heist (July 20, 2017)
A vulnerability in Parity Ethereum client allowed hackers to steal funds from multi-sig wallets. Over $30 Million of Ethereum was moved into one address. As a preventative measure to protect other vulnerable multi-sig wallets, White Hat hackers have used the same vulnerability to exfiltrate all other multi-sig wallets into a secure wallet. The vulnerability has been fixed and now the money is being returned to their owners from the White Hat wallet.
Recommendation: If you have a multi-sig wallet with Parity, check where your funds have gone. If they have been exfiltrated to the White Hat group, then you should be soon getting a new multi-sig wallet with the vulnerability removed. One of the best ways to secure your cryptocurrency against theft is by using hardware wallets. Hardware wallets are a type of cryptocurrency wallet that stores the owner's private keys on a hardware device that is secure from hacking attempts. Cold storage wallets could also be used to assist in cryptocurrency security. Cold wallets are placed on clean air-gapped computers and therefore protect all private keys from online threats. It is more tedious to use but increases the security.
Tags: Ethereum, Theft, Parity
The NukeBot banking Trojan: from rough drafts to real threats (July 19, 2017)
In Spring of 2017, the actor Gosya leaked the source code to the "NukeBot" banking Trojan. This was believed to be done in response to him being banned off forums for being a suspected scammer. The Trojan's main function was to make web injections into specific web pages to steal user data. Kaspersky researchers set up an imitation infected bot in order to collect web injections from Command and Control servers. They concluded that the main targets were French and United States banks.
Recommendation: Bank accounts and credit card numbers should be protected with the utmost care, and only used with vendors that you trust to keep your information in compliance with the relevant standards. Regular monitoring of financial accounts in addition to identity protection and fraud prevention services can assist in identifying potential theft of data.
Tags: NukeBot, TinyNuke, Gosya, Trojan
With a boost from Necurs, Trickbot expands its targeting to numerous U.S. financial institutions (July 19, 2017)
The Necurs botnet is well known for malware spam campaigns. One of the malwares that targets the financial sector is the "Trickbot" Trojan. Trickbot performs man-in-the-browser (MitB) attacks against customers of financial institutions. Tickbot traditionally only targeted financial institutions outside of the United States. On July 17th, Flashpoint researchers have observed them targeting various institutions both inside and outside the United States in a new wave of attacks. Emails are being sent which have an attachment with obfuscated JavaScript that downloads the Trickbot trojan.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and anti-virus protection, and avoid opening email from untrusted or unverified senders.
Tags: Trickbot, Necurs, Trojan, Banking
Devil's Ivy: Flaw in Widely Used Third-party Code Impacts Millions (July 18, 2017)
A stack overflow vulnerability has been discovered in gSOAP, a simple object access protocol web services toolkit developed by Genivia, which can lead to remote code execution. Researchers at Senrio discovered the vulnerability after analyzing an M3004 Axis Communications security camera. The vulnerability has been dubbed as "Devil's Ivy". When the vulnerability was exploited on the security camera, the researchers were able to access the video feed, and deny the owner access to that feed. The vulnerability affects any device that uses gSOAP to support their web services. Genivia claims that gSOAP has been downloaded over 1 million times.
Recommendation: Genivia has released a patch which fixes the vulnerability. It is recommended that users keep all services updated. If the device is IoT, it is recommended that it is placed behind a firewall or network address translation and placed within a Virtual Local Area Network (VLAN).
Tags: gSOAP, RCE, Buffer Overflow, IOT
Hacker steals $7.4 million in ethereum during CoinDash ICO launch (July 18, 2017)
On Monday 17th July, a hacker managed to steal approximately $7.4 million in Ethereum during CoinDash's Initial Coin Offering (ICO). CoinDash had posted the wallet address on their website in order for investors to send Ethereum to. But a hacker managed to compromise the website, and post their own wallet address instead. The hacker managed to gain millions of dollars worth of Ethereum before CoinDash stopped the token sale. CoinDash has promised that investors who gave money to the wrong address will still be given tokens reflecting their pledges.
Recommendation: Providing the funding wallet address in a single place is not very secure. Also, any important content on a web site that can be modified should be cryptographically signed.
Tags: Ethereum, ICO, Web Server
Linux Users Urged to Update as a New Threat Exploits SambaCry (July 18, 2017)
The open source re-implementation of the SMB/CIFS networking protocol for Windows, "Samba," is continuing to be exploited by threat actors, according to Trend Micro researchers. Additionally, the company issued a security advisory stating that Samba versions from 3.5.0 onwards are vulnerable to remote code execution. The vulnerability is being exploited by threat actors to distribute a modified version of the "SambaCry" malware.
Recommendation: The Samba vulnerability abused by actors in this story has already been patched in May 2016. The patch should be applied as soon as possible if it has not been already.
Tags: Linux, SambaCry
Two Iranians Charged in U.S. Over Hacking Defense Materials (July 18, 2017)
On Monday 17th July, two Iranians were indicted with hacking a defense contractor and theft of software that was being used to design bullets and warheads from a Vermont based company Arrow Tech Associates. The two Iranians indicted were Mohammed Saeed Ajily and Mohammed Reza Rezakhah. A third man involved in the case was Nima Golestaneh, who was arrested in Turkey in 2013 and extradited to the United States.
Recommendation: Company owners must take every step necessary to secure their data. Always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
Tags: Breach, Arrow Tech, Iran
751 Domains Hijacked to Redirect Traffic to Exploit Kits (July 17, 2017)
On Friday 7th July, the French domain registrar Gandi lost control of 751 domains after a technical partner was breached, and name servers modified. Gandi detailed in a report that the attacker was able to obtain a password for the backend of one of Gandi's technical partners. Traffic to these domains was redirected to servers hosting Neutrino and RIG exploit kits.
Recommendation: It is important that your company and employees use different passwords for the different accounts that are being used. Your company should implement security policies on accounts that store any sensitive information. Multi-factor authentication, and frequent password changes can help protect trade secrets and other forms of sensitive data.
Tags: Domain, Neutrino, RIG
Cisco WebEx Browser Extension Remote Code Execution Vulnerability (July 17, 2017)
A critical vulnerability in Cisco's WebEx extensions for Chrome and Firefox would allow an attacker to remotely execute malicious code. If an attacker sets up a webpage with malicious Javascript, the attacker is able to embed an iframe with a specific URL that loads the WebEx extension. Then the Javascript can pass a JSON message to the native app to roll back the sanitization component to an older version. With this, another JSON message can be sent to the app in order to execute arbitrary code. Over 20 million people use the extension on Chrome and over 700,000 use it on Firefox.
Recommendation: This vulnerability affects Cisco WebEx extensions for Google Chrome and Mozilla Firefox on Windows. Cisco has released an update which addresses the vulnerability. Users should ensure that their extensions are updated to the latest version.
Tags: RCE, Chrome, Firefox, WebEX
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
RIG exploit kit Tool Tip
The RIG exploit kit is a framework used to exploit client side vulnerabilities in web browsers. The RIG exploit kit takes advantage of vulnerabilities in Internet Explorer, Adobe flash, Java and Microsoft Silverlight. The RIG exploit kit was first observed in early 2014. The RIG exploit kit's objective is to upload malicious code to the target system. The RIG exploit kit is known to distribute ransomware, spambots and backdoors. Victims are redirected to the RIG exploit kit with a landing page coming from malvertising or compromised sites.
Tags: RIG, exploitkit
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



