Weekly Threat Briefing: LokiBot Android Banking Trojan Turns Into Ransomware When You Try to Remove It
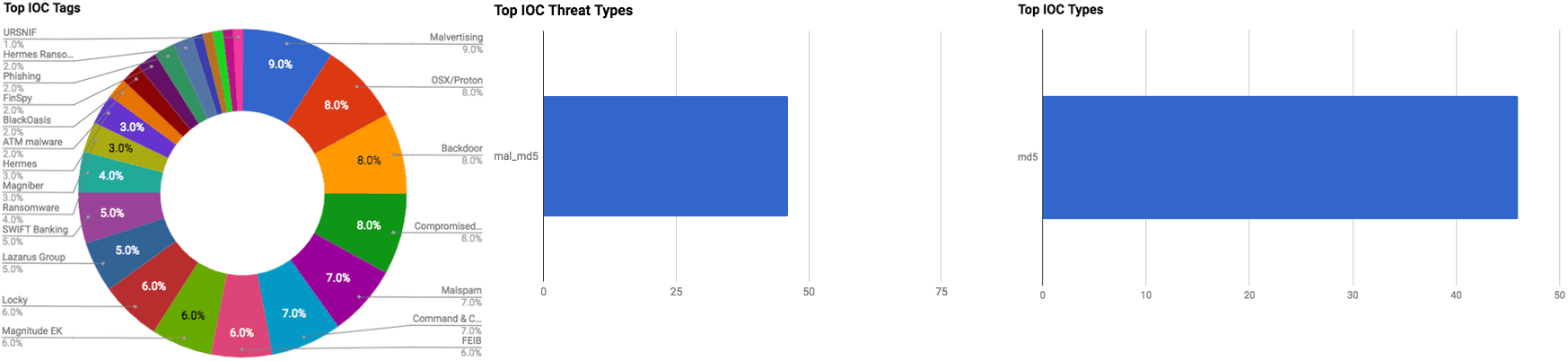

This section listed below contains summaries on various threat intelligence stories that occurred during the past week. The intelligence in this week's iteration discuss the following threats: Botnet, Exploit kit, Malicious Applications, Malspam, Phishing, Ransomware, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Evasive Sage 2.2 Ransomware Variant Targets More Countries (October 29, 2017)
Fortinet researchers have published information regarding a new variant of the "Sage" ransomware, dubbed "Sage 2.2." This variant is distributed via spam emails with malicious JavaScript attachments that will download Sage 2.2. The malware will still not infect some machines if certain languages are detected, however, this variant uses a new privilege escalation technique not seen in previous variants. The added privilege allows the malware to encrypt files located in a protected folder. The actors behind the campaign request $2,000 USD in bitcoins for the decryption key. Furthermore, this variant has added more languages to its ransom note in order to infected additional users in more countries.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, it is important to have a comprehensive and tested backup solution in place for the unfortunate case of ransomware infection.
Tags: Spam, Ransomware, Sage 2.2
Vulnerability Spotlight: Apache OpenOffice Vulnerabilities (October 26, 2017)
Three new vulnerabilities have been found in the open source office suite "Apache OpenOffice," according to Cisco Talos researchers. The first vulnerability is located within "OpenOffice Write," the second in the "Draw" application, and the third in the "Writer" application. The vulnerable version is Apache OpenOffice 4.1.3.
Recommendation: Your company should have policies in place to monitor all software that is used to ensure that the most current and secure version is implemented. It is critical that the latest security patches be applied as soon as possible to the web browser used by your company. Vulnerabilities are discovered relatively frequently, and it is paramount to install the security patches because the vulnerabilities are often posted to open sources where any malicious actor could attempt to mimic the techniques that are described.
Tags: Vulnerability, Apache OpenOffice
AmosConnect: Maritime Communications Security Has Its Flaws (October 26, 2017)
IOActive researchers have published information discussing two critical vulnerabilities found "AmosConnect" software. Specifically, AmosConnect 8, which is a platform designed to work in a maritime environment in combination with satellite equipment. The vulnerabilities include the ability to perform SQL injection to return passwords that were stored in plain text and the presence of a privileged backdoor account. If a maritime vessel did not segment their network configurations, a threat actor may find an exposed network via the internet scanning tool "Shodan," and access the systems via a satellite link.
Recommendation: Researchers state that these vulnerabilities pose a serious risk because they could potentially allow actors to steal sensitive data, take over a server completely, or even pivot within the vessel network. If the network is segmented, researchers state that the vulnerabilities can only be exploited by an actor with access to the IT systems network.
Tags: Vulnerabiltiy, AmosConnect 8
Malvertising Campaign Redirects Browser to Terror Exploit Kit (October 25, 2017)
Security researchers warn that some "Quit Smoking" and "20 Minute Fat Loss" advertisements are part of a malvertising campaign. Some of these advertisements, when clicked on, are directing users to landing pages that host the "Terror" exploit kit. Terror was first identified in early 2017, and this campaign was found to have increased in malicious activity beginning on September 1 and last through October 23, 2017. The Terror exploit kit is targeting two vulnerabilities in CVE-2016-0189 (scripting engine memory corruption vulnerability) and CVE-2014-6332 (flaw in Windows OLE that can lead to remote code execution). Researchers state that this campaign is currently attempting to infect user with the "Smoke Loader" malware that gives actors remote control over an infected machine.
Recommendation: Malvertising and exploit kits techniques are often updated by threat actors, therefore, keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: Malvertising, Exploit Kit, Malware
SnatchLoader Reloaded (October 25, 2017)
Arbor Networks researchers have published new information regarding the downloader malware called "SnatchLoader." The malware was first discovered in January 2017, but went dormant for a few months before recently being observed again. The malware is being delivered via spam emails. SnatchLoader is currently being used to distribute the "Ramnit" banking trojan. Researchers found that SnatchLoader is using "geo-IP blocking" to ensure that machines located only in certain regions will be infected. At the time of this writing, this campaign is at least targeting the U.K. and Italy.
Recommendation: Always be cautious while reading email, in particular when it has attachments or comes with an urgent label or poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: Malware, SnatchLoader
Multiple Ransomware Infections Reported (October 24, 2017)
The U.S. Computer Emergency Readiness Team (CERT) has issued an alert regarding numerous infections of a ransomware strain dubbed "Bad Rabbit." Bad Rabbit is suspected to be a variant of the "NotPetya" ransomware. The threat actors request 0.05 bitcoins (approximately $273 USD). As of this writing, the actors behind the campaign are unknown. The U.S. CERT discourages anyone from paying the ransom because it does not guarantee that access will be restored to an infected machine.
Recommendation: The U.S.-CERT states that using unpatched and unsupported software may increase the threat and risk of this ransomware. They also ask users to report ransomware incidents to the Internet Crime Complaint Center (IC3).
Tags: Alert, Ransomware, Bad Rabbit
New Ransomware "Bad Rabbit" Spreading Quickly Through Russia and Ukraine (October 24, 2017)
On October 24, 2017, media sources and security researchers began reporting about an active ransomware campaign. The ransomware, dubbed "Bad Rabbit," infected at least three Russian media outlets, the Kiev Metro, and others as the day progressed. The malware was spread via drive-by downloads from compromised Russian news websites which displayed fake Adobe Flash Player installers. If infected, a user will be presented with instructions in the command prompt to visit a ".onion" domain to receive further instructions. The threat actors request 0.05 bitcoins (approximately $273 USD) for the decryption key. As of the writing, the threat actors behind this campaign are unknown.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Ransomware, Bad Rabbit
LokiBot Android Banking Trojan Turns Into Ransomware When You Try to Remove It (October 24, 2017)
A newly discovered variant of the Android banking trojan "LokiBot" has the capability to turn into ransomware, according to SfyLabs researchers. This variant transitions from displaying fake login pages impersonating banking applications to steal credentials, to locking a user's phone when they attempt to remove the malware's administrator privileges. At the time of this writing, LokiBot is offered for purchase on underground markets for approximately $2,000 USD. Due to a flaw in the encryption implementation, researchers found that the ransomware feature does not actually encrypt a user's files with AES, but rather results in the renaming of the files. However, the screen locking feature does work, and the actors demand between $70 and $100 USD to unlock the device.
Recommendation: This LokiBot variant is capable of working on Android version 4.0. The malware must run with administrator privileges, which it requests upon installation, for example, by hiding in an application in the Google Play store or third-party store. Users should carefully read the permission an application will request prior to installation. It can also be useful to read the comments regarding the application to identify potential issues. Furthermore, trusted antivirus applications should also be run on mobile devices. The screen locking is able to be disabled by booting the device into "Safe Mode" and removing LokiBot's admin user and the infected application.
Tags: Android, Mobile, Malicious applications, Malware, LokiBot
Fake Cryptocurrency Trading Apps on Google Play (October 23, 2017)
ESET researchers have found that Android users are being targeted with malicious applications, specifically, users of the cryptocurrency exchange "Poloniex." Two malicious applications were identified in the Google Play store to be impersonating Poloniex, which is one of the world's leading cryptocurrency exchanges. One of the malicious applications, "POLONIEX," was downloaded approximately 5,000 times between August 28 and September 19, 2017. The second application, "POLONIEX COMPANY," was downloaded approximately 500 times after it first appeared on Google Play on October 15, 2017. When launched, the applications present a screen impersonating Poloniex to steal user credentials, and then will request the user to sign in with their Google account to steal more credentials.
Recommendation: Google has since removed the two applications mentioned in this story. Researchers note that if a user is using two-factor authentication, he/she will be unaffected if the malicious applications were downloaded. Additionally, always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Android, Mobile, Malicious applications
Reaper: Calm Before the IoT Security Storm (October 23, 2017)
Security experts have discovered a new Internet of Things (IoT) botnet, called "IoTroop" and/or "Reaper." Check Point researchers claim that this massive botnet, which already consists of millions of compromise IoT devices, may have the potential to take down the entire internet. Researchers note that this botnet is evolving and recruiting at a far greater pace than the Mirai botnet of 2016.
Recommendation: This botnet is actively infecting IoT devices such as IP Wireless Cameras to increase the impact of a possible Distributed Denial-of-Service (DDoS) attack. While the motives of threat actors behind IoTroop remains unclear as of this writing, this story serves as crucial evidence regarding the importance of securing IoT devices. All IoT devices, particularly IP wireless cameras in this case, should be secured by changing the default credentials. Actors are often able to create botnets, or compromise devices simply because a user did not change the default username and password.
Tags: Botnet, IoT, Reaper
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



