Weekly Threat Briefing: Mastermind Behind EUR 1 Billion Cyber Bank Robbery Arrested in Spain
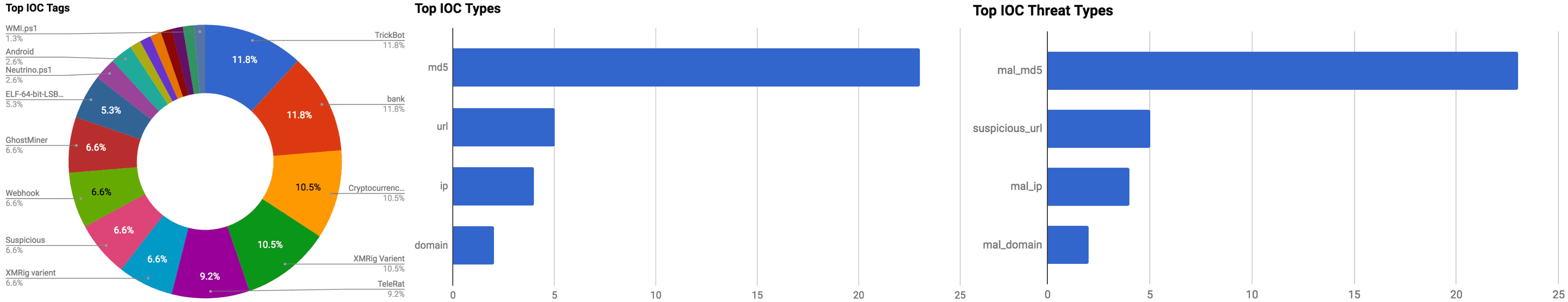

The intelligence in this week’s iteration discuss the following threats: 419 Scams, Cobalt Gang, GhostMiner, Guccifer 2.0, Orbitz Breach and TeleRat. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Mastermind Behind EUR 1 Billion Cyber Bank Robbery Arrested In Spain (March 26, 2018)
The leader of the group behind the "Carbanak" and "Cobalt" malware attacks has been arrested in Alicante, Spain. The arrest took place after a joint investigation was carried out by the Spanish National Police in conjunction with Europol, the United States FBI, authorities from Romanian, Belarus, and Taiwan, as well as private security companies. The group has been conducting operations since 2013, striking banks in more than 40 countries, resulting in cumulative losses of over one billion Euro for the financial industry. The group would typically target banking employees with spear phishing emails in attempts to gain access to the network.
Click here for Anomali recommendation
"Celebrating Stephen Hawking" with a 419 scam (March 23, 2018)
A new "419" scam is using the subject line "Celebrating Stephen Hawking," in an attempt to make some quick money. 419 scams, which refers to the section of Nigerian criminal code dealing with fraud, promise the target a large sum of money in return for a small advance fee, in this case, the fraudster was promising an $8 million USD prize for answering three questions about Stephen Hawking. When you send an email with the correct answers, the scammer asks for personal details including cell phone number, date of birth, and pictures of government-issued ID cards.
Click here for Anomali recommendation
GhostMiner: Cryptomining Malware Goes Fileless (March 22, 2018)
Minerva Labs researchers have conducted an analysis on "GhostMiner;" a cryptocurrency miner that is using fileless techniques in order to increase it's stealth capabilities. The miner spreads by exploiting vulnerable servers running Oracle WebLogic, MSSQL, and phpMyAdmin. The mining component, a modified "XMRig" miner, is launched directly from memory after stopping other miners running on the system by using PowerShell's "Stop-Process -force" command on blacklisted miners from a hardcoded list.
Click here for Anomali recommendation
Lone DNC Hacker' Guccifer 2.0 Slipped Up and Revealed He Was a Russian Intelligence Officer (March 22, 2018)
The "lone hacker" who took credit for passing stolen emails from the Democratic National Committee (DNC) to WikiLeaks has been exposed as an officer for the GRU, Russia's military intelligence directorate. The "Guccifer 2.0" persona was first reported on by Crowdstrike in 2016. Guccifer 2.0 built up an image as an independent Romanian hacktivist. On one occasion Guccifer 2.0 forgot to activate his VPN client which left the real Moscow-based IP address in the logs of a social media company. Which was identified as a particular GRU officer.
Click here for Anomali recommendation
Thousands of servers found leaking 750MB worth of passwords and keys (March 22, 2018)
The security researcher "Giovanni Collazo" has discovered almost 2,300 internet exposed servers running "etcd." etcd is a distributed key-value store database that is able to store data across a cluster. Using a simple script, Collazo was able to query the servers to return all the stored credentials. The queries fetched 8,781 passwords, 650 AWS access keys, 23 secret keys, and 8 private keys.
Click here for Anomali recommendation
Uh Oh! Unified Logs in High Sierra (10.13) Show Plaintext Password for APFS Encrypted External Volumes via Disk Utility.app (March 21, 2018)
Security researcher Sarah Edwards has discovered that plaintext passwords for APFS encrypted external volumes are visible in unified logs in High Sierra via the Disk Utility application. Starting from a "clean" flash drive, using the Disk Utility application to create an encrypted APFS volume on the drive. Monitoring the unified logs during this will reveal the plaintext password.
Click here for Anomali recommendation
TrickBot Banking Trojan Adapts with New Module (March 21, 2018)
The TrickBot banking trojan has incorporated multiple new modules according to Webroot researchers. One module, named "Spreader_x86.dll," is used by TrickBot to spread laterally through an infected network by leveraging "EternalRomance" (MS17-010:CVE-2017-0145). Another module still in development appears to be a "screenlocker." It appears that the developers are trying to adapt TrickBot to also target corporate networks, as evidenced by the fact that the screenlocking is only called after lateral movement. Prior to this new activity, Trickbot typically targeted individuals using their personal banking websites. In this context, this appears to be an attempt by Trickbot actors to generate more revenue in a corporate setting because users are less likely to be visiting targeted personal banking URLs from corporate networks.
Click here for Anomali recommendation
Cryptocurrency Miner Distributed via PHP Weathermap Vulnerability, Targets Linux Servers (March 21, 2018)
Trend Micro researchers have discovered a new cryptocurrency-mining campaign that is targeting Linux servers. The campaign delivers the miners by exploiting the vulnerability registered as "CVE-2013-2618." The vulnerability lies in Cacti's "Network Weathermap" plugin, which is used by network administrators to visualize network activity. A patch for this vulnerability has existed for five years. The delivered cryptominer is a modified "XMRig" miner that mines the "Monero" cryptocurrency.
Click here for Anomali recommendation
Expedia's Orbitz Says 880,000 Payment Cards Compromised in Security Breach (March 20, 2018)
An online travel booking subsidiary of Expedia, Orbitz, has revealed that one of its deprecated websites has been hacked, exposing the card payment numbers of approximately 880,000 customers. The breach likely took place between October 2016 and December 2017. Along with card numbers, other personal data of customers that were exposed included the following: name, address, date of birth, phone number, email address, and gender. Orbitz is working to notify the affected customers and is planning to offer one year of free credit monitoring and identity protection service.
Click here for Anomali recommendation
Windows Remote Assistance Tool Can Be Used for Targeted Attacks (March 20, 2018)
A utility that ships with all Windows distributions, called "Windows Remote Assistance Tool," is able to be used in targeted attacks. The vulnerability was discovered by a Belgian security researcher "Nabeel Ahmed." The vulnerability exists because Microsoft failed to sanitize an invitation file used by Windows Remote Assistance Tool. The invitation file, which is an XML file with configuration data, is able to embed an XML External Entity (XEE) exploit that can be sent to a target to take a local file and exfiltrate it to a remote server.
Click here for Anomali recommendation
TeleRAT: Another Android Trojan Leveraging Telegram's Bot API to Target Iranian Users (March 20, 2018)
Palo Alto Unit 42 researchers have discovered a new Android Trojan that is using Telegram's Bot API, targeting Iranian users. The malware, dubbed "TeleRat," uses the bot API for both Command and Control (C2) and data exfiltration. When first executed, the trojan steals contact information, details of Google accounts on the phone, SMS history, and pictures taken using both front and rear camera. TeleRat uses the API every 4.6 seconds to receive further commands from the Telegram Bot and can perform actions such as calling a number, getting GPS location, getting app list, recording audio, and taking pictures. It is believed that the trojan is being distributed via third party application stores.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
TrickBot Tool Tip
TrickBot is a modular Bot/Loader malware family which is primarily focused on harvesting banking credentials. It shares heavy code, targeting, and configuration data similarities with Dyreza. It was first observed in September 2016 and both the core bot and modules continue to be actively developed. Both x86 and x64 payloads exist. It has been distributed using traditional malvertising and phishing methods. [Flashpoint](https://www.flashpoint-intel.com/blog/trickbot-targets-us-financials/) recently (2017-07-19) observed TrickBot operators leveraging the NECURS Botnet for distribution. Previously, Anomali Labs released a [Threat Bulletin](https://ui.threatstream.com/tip/17137) detailing the unpacking of this malware family.
Tags: TrickBot, Family-Trickbot, victim-Financial-Services
FEATURED RESOURCES

Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more


