Weekly Threat Briefing: Mexican Banks Hacked – Leading to Large Cash Withdrawals
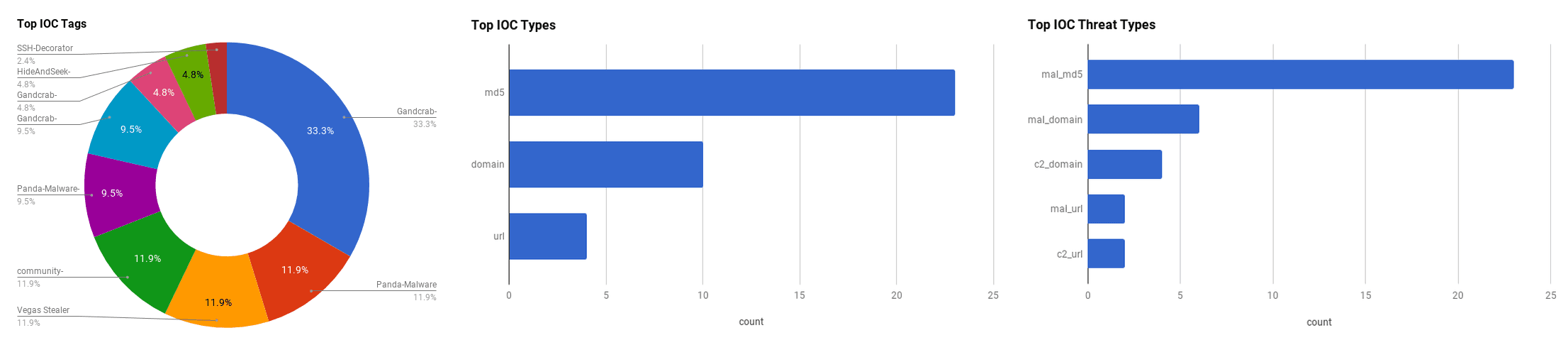

The intelligence in this week’s iteration discuss the following threats: baseStriker, Chili's Breach, Gandcrab Ransomware, Hide and Seek Botnet, New Vegas Stealer, SSH Decorator Credential Stealer and TreasureHunter malware. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Mexican Banks Hacked – Leading To Large Cash Withdrawals (May 13, 2018)
Multiple banks in Mexico have experienced large, unauthorized cash transfers after threat actors gained access to five financial institutions approximately two weeks ago. The affected financial institutions include: "Grupo Financiero Banorte," "Banco del Bajio SA," and "Banco del Ejercito," and two that have remained unnamed. The incidents were identified by the Banco de Mexico, who had observed large cash transfers involving other banks. According to the head of operations, Lorenza Martinez, of the Banco de Mexico, a vulnerability in the banks system led to a large amount money being withdrawn from "fake accounts" of five banks. The central bank is investigating whether the affected banks are complying with security regulations
Click here for Anomali recommendation
EFAIL: Vulnerabilities in OpenPGP and S/MIME that leak the plaintext of encrypted emails (May 13, 2018)
Researchers from the Munster University of Applied Sciences, Ruhr University Bochum, and KU Leuven claim to have discovered vulnerabilities in OpenPGP and S/MIME that reveal the plaintext of encrypted emails. The vulnerabilities, dubbed "EFAIL," exploit active content of HTML based emails to exfiltrate plaintext through requested URLs. An attacker would take PGP or S/MIME ciphertext and enclose them in a URL tag such as an image tag. The first part of the tag has no closing quotes. The closing parts of the tag are put after the ciphertext. When the email is sent to the target, the victim's client will decrypt the ciphertext, and stitches the three parts together, then the active HTML component will attempt to fetch the URL, resulting in the plaintext being sent to an attackers server.
Click here for Anomali recommendation
Notice Of Unauthorized Access To Chili's Grill & Bar Guest Data (May 11, 2018)
A number of "Chili's" restaurants have been affected by a data breach, resulting in the unauthorized access of customers payment card data. The breach was discovered on May 11. The incident was believed to have happened between March and April 2018. The leaked data involved credit/debit card numbers and cardholder names. Chili's are still working to determine the number of customers affected.
Click here for Anomali recommendation
New Vega Stealer Shines Brightly In Targeted Campaign (May 10, 2018)
Proofpoint researchers have observed a campaign that targets the Marketing/Advertising/Public Relations and Retail/Manufacturing sectors with a malware dubbed "Vega Stealer." The malware steals saved credentials and credit card information from Chrome and Firefox browsers. The malware is also capable of stealing sensitive documents from an infected machine. The malware is being delivered via spear phishing emails with a Microsoft Word document that contains a malicious macro to download the Vega Stealer payload. Researchers note that the malware appears to be a stripped down version of the "August Stealer" malware.
Click here for Anomali recommendation
CVE-2018-1000136 - Electron nodeIntegration Bypass (May 10, 2018)
A vulnerability has been discovered by Trustwave researchers in the "Electron" framework that could lead to remote code execution. Electron is a popular framework for creating native applications using web technologies, such as HTML, CSS, and JavaScript. The vulnerability, registered as "CVE-2018-1000136," lies in the method to apply restricted attributes to child windows in the "WebView" tag feature. If the default value for "webviewTag" feature is not explicitly declared in the applications "webPreferences," it will then take the value of "nodeIntegration." This allows the window opening function to pass "webviewTag" as an additional feature, allowing for potential remote code execution.
Click here for Anomali recommendation
TreasureHunter Point-of-Sale Malware and Builder Source Code Leaked (May 10, 2018)
The source code for the Point-of-Sale (PoS) malware "TreasureHunter" has been leaked onto a top-tier Russian-speaking forum. The TreasureHunter malware has been investigated since 2014, but now with the source code, analysts can gain new insight into the inner workings of the malware. On the other hand, the publicly available code lowers the bar for entry for new cybercriminals. It is unknown why the source code was leaked at this time. This source code leak can spawn many different variants in the near future.
Click here for Anomali recommendation
Panda Malware Broadens Targets To Cryptocurrency Exchanges And Social Media (May 9, 2018)
The "Panda" malware, a derivative of the "Zeus" Banking Trojan, has been targeting new sectors such as Cryptocurrency exchanges and social media in four campaigns between February and May, according to F5 researchers. However, the primary focus for the Panda malware is still financial services. Panda is distributed via phishing emails with malicious attachments and targets the Windows operating system. A campaign in February targeted Italian cryptocurrency sites and financial services. The other three campaigns beginning in May target United States, Canadian, Japanese and South American financial services and social media sites.
Click here for Anomali recommendation
Gandcrab Ransomware Walks its Way onto Compromised Sites (May 9, 2018)
Cisco Talos researchers have discovered a series of compromised websites delivering the "Gandcrab" ransomware. The attacks begin by sending phishing emails with attachments that download the malware from compromised websites. The compromised websites are being used because it saves threat actor's time and money by not having to set up their own infrastructure. It also allows the actors to "piggy back" off the good reputation of the compromised site, in order to bypass blacklisting technologies. Gandcrab uses Namecoin domains for Command and Control (C2) communication.
Click here for Anomali recommendation
Threat Actors Shift to Android-Based Carding, Struggle with iOS (May 9, 2018)
Cybercriminals on Russian-language underground forums are showing an increased interest in using the Android mobile operating system to evade detection whilst making fraudulent purchases using stolen card data, according to Flashpoint researchers. Cybercriminals believe that e-commerce retailers' anti-fraud systems on mobile operating systems are less likely to identify malicious activity. Android is also preferred because it is easily obtainable via an emulator, which eliminates the need for access to a physical Android device. Tutorials for abusing Android-based technology are prevalent on Russian-language forums, which lowers the bar among low-skilled fraudsters thus increasing the likelihood of malicious activity. Researchers have noted that threat actors are struggling to use iOS devices for the same malicious activity, due to the lack of open-source code, effective emulators and security measures put in place by Apple that makes it harder to "Jailbreak" iOS devices.
Click here for Anomali recommendation
Backdoored Python Library Caught Stealing SSH Credentials (May 9, 2018)
Recent versions of a popular Python module were found to have a backdoor that harvested users' Secure Shell (SSH) credentials and sent them to a remote server. The Python module, "SSH Decorator," was developed by an Israeli developer Uri Goren who claimed that the backdoor was not intentional and was the result of a hack. Goren has now removed the module from both GitHub and PyPI.
Click here for Anomali recommendation
Security updates available for Flash Player (May 8, 2018)
Adobe has released security updates for Flash Player. The updates address "critical" vulnerabilities in Adobe Flash Player 29.0.0.140 and earlier versions. Successful exploitation could lead to arbitrary code execution. The vulnerabilities lie in the Flash Player products for Desktop Runtime in Windows, Macintosh, and Linux, Adobe Flash Player for Google Chrome, and Adobe Flash Player for Microsoft Edge and Internet Explorer 11.
Click here for Anomali recommendation
baseStriker: Office 365 Security Fails To Secure 100 Million Email Users (May 8, 2018)
Researchers from Avanan have uncovered a security flaw in Microsoft Office 365. According to the researchers, the vulnerability, dubbed "baseStriker," can bypass all of Microsoft's security features. The attack works by sending a malicious link split up into two HTML tags: the "base" tag and the "anchor" tag. Normally a malicious link in an anchor tag would be blocked by Office 365. However, if the link is divided up between a base and anchor tag the base tag is only checked by Office 365, ignoring the relative part of the link, allowing a malicious email to get through security features. This technique has been observed in real-world attacks.
Click here for Anomali recommendation
Hide and Seek IoT Botnet resurfaces with new tricks, persistence (May 7, 2018)
Researchers from Bitdefender have discovered that the "Hide and Seek" Internet of Things (IoT) Botnet has been updated with new persistence capabilities. There have also been improvements to the propagation code. This includes targeting new devices by passing their default login credentials and leveraging two new vulnerabilities that allow it to infect IPTV camera models. The Botnet also has ten different binaries compiled for various architectures including x86, x64m ARM and SuperH. Researchers theorize that the Botnet is in the growth phase and is trying to infect as many devices as possible before adding weaponized features to the binary.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



