Weekly Threat Briefing: More Security Firms Confirm NotPetya Shoddy Code is Making Recovery Impossible
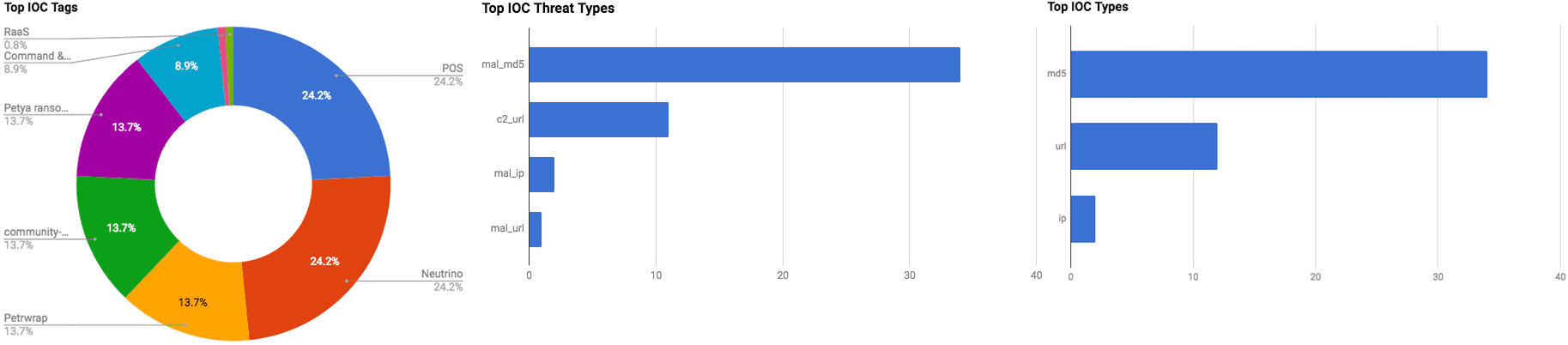

Figure 1: IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Threats
This section provides summaries and links to the top threat intelligence stories from this past week. All IOCs from these stories are attached to this threat briefing and can be used for indicator matching against your logs.
A New Service Offers Cybercriminals Automated Social Engineering as a Service (July 3, 2017)
An actor with the alias "Goldrose" has been identified to be advertising a new subscription-based service on the underground market, "AlphaBay." The actor claims that the service was created because there are a large amount of credit card dumps available for purchase, but they often do not come with Personal Identification Numbers (PINs) and mother's maiden names needed to steal funds. A user could subscribe for $250 USD per month to gain access to an automated calling service that impersonates a financial institution. The automated call attempts to trick the recipients into visiting a website and entering their financial data, or prompt the user to say confidential information over the call which is recorded.
Recommendation: The impersonation of legitimate services continues to be a tactic used by threat actors in attempts to steal sensitive information. All employees should be educated on the risk phishing poses, and how to identify such attempts. As this story portrays, it is important to understand your bank's policies, and how they will contact you if they need any information. Most banks will not call a customer and ask for authentication, it is usually reserved for when a customer must prove their identity for when they call the bank. Be wary of calls asking for sensitive information.
Tags: Underground market, Phishing phone calls
More Security Firms Confirm NotPetya Shoddy Code Is Making Recovery Impossible (June 30, 2017)
Researchers from multiple security firms believe that the "NotPetya" ransomware outbreak on June 27, 2017, was actually an attack meant to cause destruction rather than earn illicit revenue. Researchers point to the malware's defective encryption process in addition to the attack taking place prior to a Ukrainian national holiday, as evidence that the attack was designed to damage Ukrainian infrastructure and businesses. Furthermore, those who were infected by the malware also stopped making payments to the NotPetya Bitcoin wallet as of June 28.
Recommendation: Always run antivirus and endpoint protection software to assist in preventing ransomware infection. Maintain secure backups of all your important files to avoid the need to consider payment for the decryption key. Emails received from unknown sources should be carefully avoided, and attachments and links should not be followed or opened. Your company should sustain policies to consistently check for new system security patches. In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: NotPetya, Ransomware
Azure AD Connect Vulnerability Allows Attackers to Reset Admin Passwords (June 29, 2017)
A vulnerability in Azure Active Directory (AD) Connect could lead to elevation of privilege if Password Writeback is misconfigured during establishment. If Password Writeback is enabled, Azure AD Connect must be granted Reset Password permission over the AD user accounts on-premises. When this is set up, an AD Administrator may have unintentionally given Azure AD Connect the ability to reset passwords over on-premises AD privileged accounts, thus allowing an malicious Azure AD Administrator to reset the password of an on-premises AD user privileged account. Allowing the malicious Azure AD Administrator to gain privileged access to a on-premises Active Directory. This vulnerability has been registered as "CVE-2017-8613."
Recommendation: Microsoft has fixed this vulnerability by blocking Password Writeback requests for on-premises AD privileged accounts unless the requesting Azure AD Administrator is the owner of the on-premises AD account. This is in the latest version (1.1.553.0). It is recommended that Azure AD Connect is updated immediately.
Tags: Azure, Active Directory, Vulnerability, Privilege Escalation
Cerber Renames Itself as CRBR ENCRYPTOR (June 29, 2017)
Researchers have a identified a new "Cerber" ransomware campaign in which the actors behind the malware have renamed it "CRBR Encryptor." The ransomware is being distributed via compromised websites injected with the Magnitude Exploit Kit, or via spear phishing emails prompting the recipient to download an attachment. The attachment is a ZIP archive containing a JavaScript file that downloads the malicious executable. The actors demand 0.5 BTC ($1,249 USD), increasing to 1 BTC (approximately $2,564.49 USD) after five days, in order to decrypt their files.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Cerber, CRBR Encryptor, Ransomware
Don't panic, but Linux's Systemd Can be Pwned via an Evil DNS Query (June 28, 2017)
A security flaw in "Systemd" can lead to a crash or remote code execution by malicious Domain Name System (DNS) server. The malicious server is able to craft a TCP payload that can pass sizes to "dns_packet_new" which can cause "systemd-resolved" to allocate a buffer that is too small, resulting in arbitrary data being written beyond the end of the buffer. This can cause a crash or facilitate remote code execution. This vulnerability has been registered as "CVE-2017-9445."
Recommendation: This vulnerability is present in Systemd version 223 to 233. Multiple Linux Distros use Systemd. For Ubuntu, Canonical has released fixes for versions 17.04 and 16.10. It is advised that users check to see if any updates are available via package manager, and install them. For Debian, "systemd-resolved" is not enabled by default, but users are able to apply the patch manually.
Tags: DNS, Linux, TCP, Systemd
Massive Skype Zero-Day Enables Remote Crashes (June 27, 2017)
A Vulnerability Lab security researcher has discovered a zero-day vulnerability for Skype during a team video conference. The vulnerability, registered as "CVE-2017-9948," is located in Skype's "clipboard format" function and can cause a stack buffer overflow. An attacker is able to set up a Remote Desktop Protocol (RDP) connection to another system, and set up a shared clipboard. If an image is copied into the shared clipboard from the remote desktop, and pasted (Crtl+V) into the message box of Skype on the local client, this causes a stack overflow which can be exploited by attackers to execute their own code on both the local and connected computers via Skype.
Recommendation: This vulnerability occurs in Skype for Windows desktop versions 7.2, 7.35 and 7.36. Windows have addressed this problem in their 7.37 update. It is recommended that users check to make sure that their Skype version is always up to date.
Tags: Skype, Vulnerability
New Shiftr RaaS Lets Any Dummy Enter the Ransomware Business (June 27, 2017)
According to researchers, a new Ransomware-as-a-Service (RaaS) portal has been identified on an underground forum. A potential buyer of the services needs to only provide their Bitcoin address and the ransom amount they want possible victims to pay for the decryption to receive a Shiftr sample. Interestingly, this service does not require threat actors to purchase the malware, but the actor behind Shiftr does take a 10% cut of the ransom funds. Researchers contend that this service may be a scam because sometimes the payment location does work; in contrast, this may also indicate that Shiftr is still in development.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Shiftr, Ransomware
Neutrino Modification for POS-Terminals (June 27, 2017)
Kaspersky researchers have discovered a new variant of the Neutrino malware that specifically targets Point of Sale (POS) terminals. This version of Neutrino has multiple capabilities including: change registry keys, download and execute files, search file by name on host and send it to a C2, search processes by name, and a proxy feature. Neutrino will steal the CVV number, expiration date, Track 1 data, and Track 2 data by scanning memory pages and send it back to a C2.
Recommendation: POS networks should be carefully monitored for unusual activity, thus keeping logs of what typical network activity looks like is very important. In the case of strange activity, taking POS systems offline and repopulating them is a safe mediation step in order to avoid possible loss of reputation, or lawsuit by individuals who had their credit card information stolen, and possibly used by cybercriminals.
Tags: Neutrino, POS, Malware
New Ransomware, Old Techniques: Petya Adds Worm Capabilities (June 27, 2017)
In the early morning hours of June 27, 2017, a new strain of ransomware related to "Petya" began infecting business and government systems in Ukraine and Russia. The infections spread rapidly to affect entities in approximately 64 countries around the globe. Researchers believe that some of the initial infections began with a tainted update distributed by a compromised server that belonged to the Ukrainian tax accounting software company called MeDoc. The malware is capable of using multiple methods for propagation such as: stealing user credentials, using file-shares to transfer malicious files, using legitimate functionalities to execute payloads, and abusing Server Message Block (SMB) vulnerabilities for unpatched systems.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: NotPetya, Ransomware
Google Researcher Uncovers Another RCE in Microsoft Malware Protection Engine (June 27, 2017)
A Google security researcher, Tavis Ormandy, has uncovered a Remote Code Execution (RCE) vulnerability affecting the Microsoft Malware Protection Engine (MsMpEng) in early June. MsMpEng has a full system x86 emulator that runs as SYSTEM and is not sandboxed. It is utilized to execute files that do not seem like portable executables during a scan. This emulator defines an opcode called "apicall." This instruction can invoke a large number of internal APIs and is exposed to remote attackers by default. Tavis discovered that a threat actor can cause a heap corruption in the Virtual File System (VFS) API. The issue was acknowledged by Microsoft: "An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system."
Recommendation: Microsoft has already addressed this vulnerability in "CVE-2017-8558" and released an update for the Microsoft Malware Protection Engine (MsMpEng) in Version 1.1.13903.0. For enterprise deployments as well as end users, the default configuration for MsMpEng is that automatic updates are enabled. If automatic updates are not enabled, then it is recommended that they are re-enabled, in accordance with the product documentation. Users should also regularly verify that software distributions, such as automatic updates and malware definitions, are working as expected in their environment.
Tags: Vulnerability, Microsoft
Mobile Menace Monday: Fake WannaCry Scanner (June 26, 2017)
A fake antivirus scanner, purporting to be able to identify the "WannaCry" ransomware, was identified on the Google Play Store, according to Malwarebytes researchers. As of this writing, WannaCry does not exist for mobile devices. The fake scanner will show advertisements and install additional applications to acquire revenue for the malware creator. Google has since removed the application.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, WannaCry, Fake Scanner
$1 Million Ransomware Payment Has Spurred New DDoS (June 26, 2017)
Last week the South Korean web hosting company Nayana paid a ransom of approximately $1 million USD to recover encrypted files. Researchers believe that this was the largest ransom payment ever made, and the consequences of the payment are now being felt by other South Korean businesses. A threat group called "The Armada Collective" has begun to send ransom letters to South Korean banks demanding funds to prevent Distributed Denial-of-Service (DDoS) attacks.
Recommendation: Denial of service attacks can potentially cost your company loss in revenue because severe attacks can shut down online services for extended periods of time. With the leak of the Mirai botnet source code in October, the availability for threat actors to compromise vulnerable devices, and purchase DDoS for hire is a continually evolving threat. Mitigation technique can vary depending on the specifics of the attack. For example, in the case of BlackNurse, which can disrupt enterprise firewalls, ICMP type 3 traffic should be blocked, or at least rate limited.
Tags: Ransom, DDoS
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
Cerber Ransomware Tool Tip
Cerber is ransomware that surfaced in January of 2016. Cerber is sold on hacking forums and criminal bulletin board systems. Cerber has been in constant development with version 4 being released around the month of October of 2016. Cerber has been distributed through phishing lures, exploit kits and malvertisement.
Tags: Cerber, Ransomware
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



